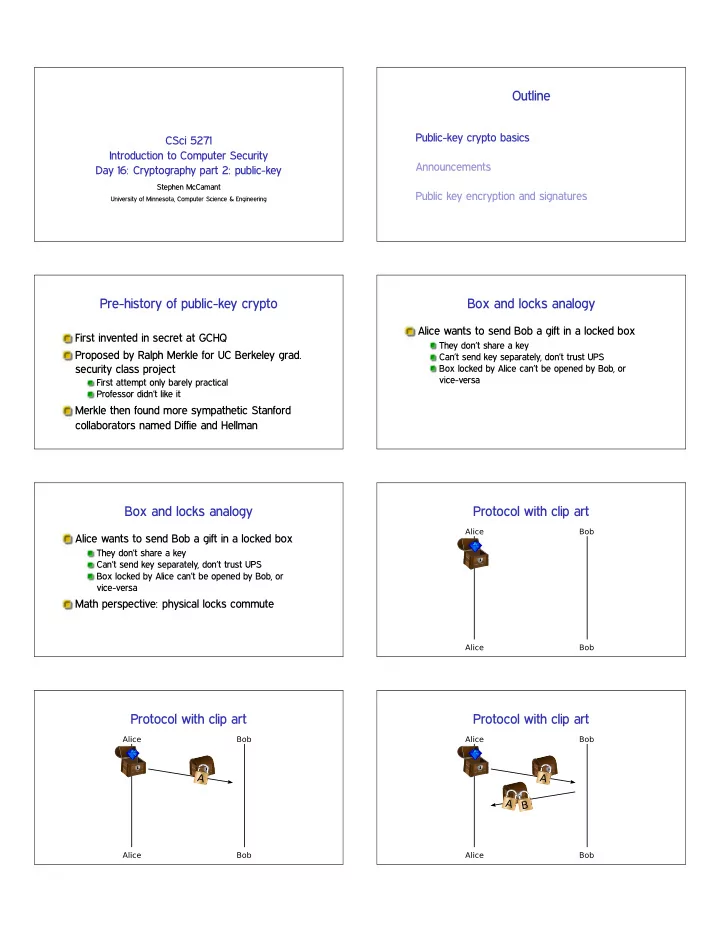

Outline Public-key crypto basics CSci 5271 Introduction to Computer Security Announcements Day 16: Cryptography part 2: public-key Stephen McCamant Public key encryption and signatures University of Minnesota, Computer Science & Engineering Pre-history of public-key crypto Box and locks analogy Alice wants to send Bob a gift in a locked box First invented in secret at GCHQ They don’t share a key Proposed by Ralph Merkle for UC Berkeley grad. Can’t send key separately, don’t trust UPS security class project Box locked by Alice can’t be opened by Bob, or vice-versa First attempt only barely practical Professor didn’t like it Merkle then found more sympathetic Stanford collaborators named Diffie and Hellman Box and locks analogy Protocol with clip art Alice wants to send Bob a gift in a locked box They don’t share a key Can’t send key separately, don’t trust UPS Box locked by Alice can’t be opened by Bob, or vice-versa Math perspective: physical locks commute Protocol with clip art Protocol with clip art
Protocol with clip art Public key primitives Public-key encryption (generalizes block cipher) Separate encryption key EK (public) and decryption key DK (secret) Signature scheme (generalizes MAC) Separate signing key SK (secret) and verification key VK (public) Modular arithmetic Generators and discrete log Modulo a prime ♣ , non-zero values and ✂ have a Fix modulus ♥ , keep only remainders mod ♥ nice (“group”) structure mod 12: clock face; mod ✷ ✸✷ : ✉♥s✐❣♥❡❞ ✐♥t ❣ is a generator if ❣ ✵ ❀ ❣❀ ❣ ✷ ❀ ❣ ✸ ❀ ✿ ✿ ✿ cover all ✰ , ✲ , and ✂ work mostly the same elements Division: see Exercise Set 1 Easy to compute ① ✼ ✦ ❣ ① Exponentiation: efficient by square and multiply Inverse, discrete logarithm , hard for large ♣ Diffie-Hellman key exchange Relationship to a hard problem Goal: anonymous key exchange We’re not sure discrete log is hard (likely not even Public parameters ♣ , ❣ ; Alice and Bob have resp. NP-complete), but it’s been unsolved for a long time secrets ❛ , ❜ Alice ✦ Bob: ❆ ❂ ❣ ❛ If discrete log is easy (e.g., in P), DH is insecure ✭ mod ♣ ✮ Bob ✦ Alice: ❇ ❂ ❣ ❜ Converse might not be true: DH might have other ✭ mod ♣ ✮ Alice computes ❇ ❛ ❂ ❣ ❜❛ ❂ ❦ problems Bob computes ❆ ❜ ❂ ❣ ❛❜ ❂ ❦ Categorizing assumptions Key size, elliptic curves Need key sizes ✘ 10 times larger then security level Math assumptions unavoidable, but can categorize Attacks shown up to about 768 bits E.g., build more complex scheme, shows it’s “as Elliptic curves: objects from higher math with secure” as DH because it has the same underlying analogous group structure assumption (Only tenuously connected to ellipses) Commonly “decisional” (DDH) and “computational” Elliptic curve algorithms have smaller keys, about 2 ✂ (CDH) variants security level
Outline Note to early readers Public-key crypto basics This is the section of the slides most likely to change in the final version Announcements If class has already happened, make sure you have the latest slides for announcements Public key encryption and signatures Outline General description Public-key encryption (generalizes block cipher) Public-key crypto basics Separate encryption key EK (public) and decryption key DK (secret) Announcements Signature scheme (generalizes MAC) Separate signing key SK (secret) and verification key VK Public key encryption and signatures (public) RSA setup RSA encryption Choose ♥ ❂ ♣q , product of two large primes, as modulus Public key is ✭ ♥❀ ❡ ✮ ♥ is public, but ♣ and q are secret Encryption of ▼ is ❈ ❂ ▼ ❡ ✭ mod ♥ ✮ Compute encryption and decryption exponents ❡ Private key is ✭ ♥❀ ❞ ✮ and ❞ such that Decryption of ❈ is ❈ ❞ ❂ ▼ ❡❞ ❂ ▼ ✭ mod ♥ ✮ ▼ ❡❞ ❂ ▼ ✭ mod ♥ ✮ RSA signature RSA and factoring Signing key is ✭ ♥❀ ❞ ✮ We’re not sure factoring is hard (likely not even Signature of ▼ is ❙ ❂ ▼ ❞ ✭ mod ♥ ✮ NP-complete), but it’s been unsolved for a long time Verification key is ✭ ♥❀ ❡ ✮ If factoring is easy (e.g., in P), RSA is insecure Check signature by ❙ ❡ ❂ ▼ ❞❡ ❂ ▼ ✭ mod ♥ ✮ Converse might not be true: RSA might have other Note: symmetry is a nice feature of RSA, not shared problems by other systems
Homomorphism Problems with vanilla RSA Multiply RSA ciphertexts ✮ multiply plaintexts Homomorphism leads to chosen-ciphertext attacks This homomorphism is useful for some interesting If message and ❡ are both small compared to ♥ , can applications compute ▼ ✶❂❡ over the integers Even more powerful: fully homomorphic encryption Many more complex attacks too (e.g., both ✰ and ✂ ) First demonstrated in 2009; still very inefficient Hybrid encryption Padding, try #1 Need to expand message (e.g., AES key) size to Public-key operations are slow match modulus In practice, use them just to set up symmetric PKCS#1 v. 1.5 scheme: prepend 00 01 FF FF .. FF session keys Surprising discovery (Bleichenbacher’98): allows ✰ Only pay RSA costs at setup time adaptive chosen ciphertext attacks on SSL ✲ Breaks at either level are fatal Variants recurred later (c.f. “ROBOT” 2018) Modern “padding” Simpler padding alternative “Key encapsulation mechanism” (KEM) Much more complicated encoding schemes using For common case of public-key crypto used for hashing, random salts, Feistel-like structures, etc. symmetric-key setup Common examples: OAEP for encryption, PSS for Also applies to DH signing Choose RSA message r at random mod ♥ , Progress driven largely by improvement in random symmetric key is ❍ ✭ r ✮ oracle proofs ✲ Hard to retrofit, RSA-KEM insecure if ❡ and r reused with different ♥ Post-quantum cryptography Box and locks revisited One thing quantum computers would be good for is breaking crypto Alice and Bob’s box scheme fails if an intermediary can set up two sets of boxes Square root speedup of general search Man-in-the-middle (or middleperson) attack Countermeasure: double symmetric security level Factoring and discrete log become poly-time Real world analogue: challenges of protocol design and public key distribution DH, RSA, DSA, elliptic curves totally broken Totally new primitives needed (lattices, etc.) Not a problem yet, but getting ready
Next time Building crypto into more complex protocols Failures of cryptosystems Toward more paranoid crypto design
Recommend
More recommend