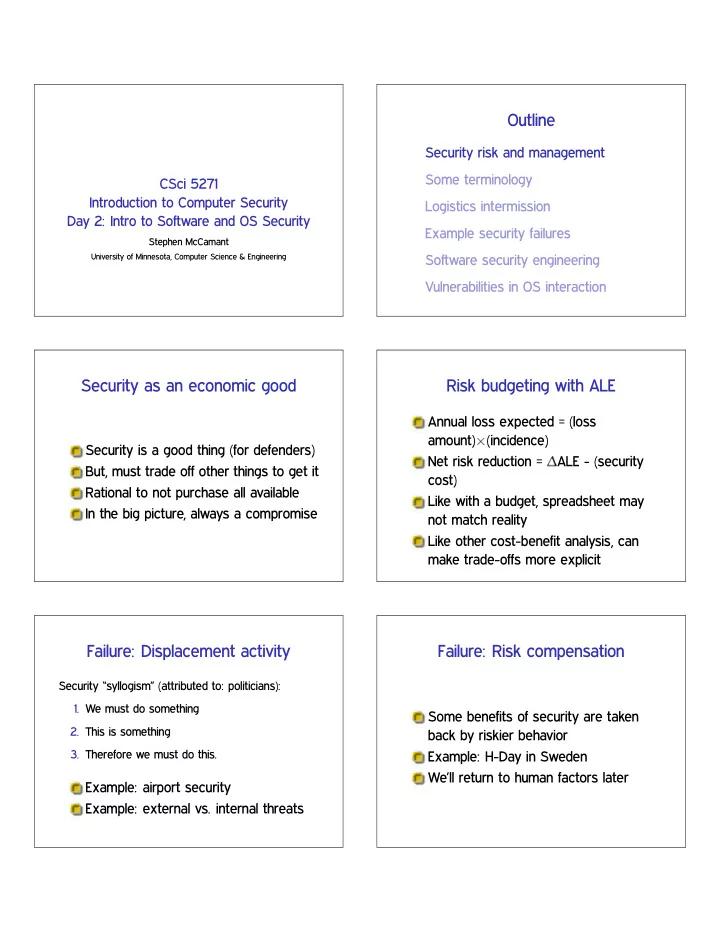

Outline Security risk and management Some terminology CSci 5271 Introduction to Computer Security Logistics intermission Day 2: Intro to Software and OS Security Example security failures Stephen McCamant University of Minnesota, Computer Science & Engineering Software security engineering Vulnerabilities in OS interaction Security as an economic good Risk budgeting with ALE Annual loss expected = (loss amount) ✂ (incidence) Security is a good thing (for defenders) Net risk reduction = ✁ ALE - (security But, must trade off other things to get it cost) Rational to not purchase all available Like with a budget, spreadsheet may In the big picture, always a compromise not match reality Like other cost-benefit analysis, can make trade-offs more explicit Failure: Displacement activity Failure: Risk compensation Security “syllogism” (attributed to: politicians): 1. We must do something Some benefits of security are taken 2. This is something back by riskier behavior 3. Therefore we must do this. Example: H-Day in Sweden We’ll return to human factors later Example: airport security Example: external vs. internal threats
This class’s perspective Outline Security risk and management Some terminology We’ll mostly ignore management issues Logistics intermission For this class, maximize security at all Example security failures costs Software security engineering Vulnerabilities in OS interaction “Trusted” “Trusted” vs. “trustworthy” In security, “trusted” is a bad word Something you actually should trust is ❳ is trusted: ❳ can break your security “trustworthy” “Untrusted” = okay if it’s evil Concise definition of security failure: Trusted Computing Base (TCB): something trusted is not trustworthy minimize “Privilege” 3 common privilege levels Privilege is the power to take 1. Administrator/root/OS kernel security-relevant actions 2. Regular user of system Concise definition of security failure: the 3. Evil people on the Internet adversary gets privilege they shouldn’t
3 common privilege levels Outline Security risk and management 1. Administrator/root/OS kernel Some terminology ✯ Local exploit Logistics intermission 2. Regular user of system Example security failures ✯ Remote exploit Software security engineering 3. Evil people on the Internet Vulnerabilities in OS interaction Posting slides before lecture Outline Security risk and management Some terminology I’ll try for 11:59pm on the night before, not guaranteed Logistics intermission Announcements are most likely to Example security failures change, recheck after Software security engineering Vulnerabilities in OS interaction Classic buffer overflow Buffer overflow classification ❝❤❛r ❜✉❢❬✷✵❪❀ Bug: stack buffer overflow ❣❡ts✭❜✉❢✮❀ Attack: return address overwrite Consequence: (binary) code injection Vulnerability in ❢✐♥❣❡r daemon Morris worm brought down 1988 Internet (4.3BSD VAXes)
Read It Twice (WOOT’12) Confused deputy compiler Smart TV (running Linux) only accepts Compiler writes to billing database signed apps on USB sticks Compiler can produce debug output to 1. Check signature on file user-specified file 2. Install file Specify debug output to billing file, Malicious USB device replaces app disrupt billing between steps How to write policy preventing this? TV “rooted”/“jailbroken” Leaky intelligence analysts Outline Security risk and management 1000s of analysts need to view 1000s Some terminology of classified documents to do their job Logistics intermission Can we prevent it if one wants to send them to the Washington Post? Example security failures More than regular access control Software security engineering (Reality: many non-technical problems) Vulnerabilities in OS interaction Vulnerabilities are bugs Security and quality Security bugs “just a special case” of bugs Security correlated with other software quality: Like regular bugs, only obscure ones Developers understand code well make it through testing Interactions between modules controlled Key difference: Well tested Rare regular bug has limited impact Attackers seek out vulnerability circumstances
Security and other features Contracts and checks Requirement: check ❳ before doing ❨ Security would be much easier if What function’s responsibility is the systems were less complex check? But, very few users want that trade-off Answer embodied in contracts, aka Risk compensation with improvements specifications, preconditions and to development process postconditions Defensive programming Outline Security risk and management Analogy: defensive driving Some terminology Don’t assume things are right, check Logistics intermission Inbound: preconditions on arguments Outbound: error conditions Example security failures Within reason: some things can’t be Software security engineering checked at some places Vulnerabilities in OS interaction Shell code injection Shell code injection example Don’t pass untrusted strings to a Benign: s②st❡♠✭✧❝♣ ✩❛r❣✶ ✩❛r❣✷✧✮ , command shell arg1 = ✧❢✐❧❡✶✳t①t✧ In C: s②st❡♠ , ♣♦♣❡♥ Attack: arg1 = ✧❛ ❜❀ ❡❝❤♦ ●♦t❝❤❛✧ s②st❡♠✭✧❝♠❞ ✩❛r❣✶ ✩❛r❣✷✧✮ Command: ✧❝♣ ❛ ❜❀ ❡❝❤♦ ●♦t❝❤❛ ❢✐❧❡✷✳t①t✧ Fix 1: avoid shell Not a complete solution: blacklist ‘ ❀ ’ Fix 2: sanitize data (preferably whitelist)
Bad/missing error handling Race conditions Under what circumstances could each Two actions in parallel; result depends system call fail? on which happens first Careful about rolling back after an error Usually attacker racing with you in the middle of a complex operation 1. Write secret data to file Fail to drop privileges ✮ run untrusted 2. Restrict read permissions on file code anyway Many other examples Update file when disk full ✮ truncate Classic races: files in ✴t♠♣ TOCTTOU gaps Time-of-check (to) time-of-use races Temp filenames must already be unique 1. Check it’s OK to write to file But “unguessable” is a stronger 2. Write to file requirement Attacker changes the file between Unsafe design ( ♠❦t❡♠♣✭✸✮ ): function to steps 1 and 2 return unused name Just get lucky, or use tricks to slow Must use ❖ ❊❳❈▲ for real atomicity you down TOCTTOU example TOCTTOU example ✐♥t s❛❢❡❴♦♣❡♥❴❢✐❧❡✭❝❤❛r ✯♣❛t❤✮ ❢ ✐♥t s❛❢❡❴♦♣❡♥❴❢✐❧❡✭❝❤❛r ✯♣❛t❤✮ ❢ ✐♥t ❢❞ ❂ ✲✶❀ ✐♥t ❢❞ ❂ ✲✶✱ r❡s❀ str✉❝t st❛t s❀ str✉❝t st❛t s❀ st❛t✭♣❛t❤✱ ✫s✮ r❡s ❂ st❛t✭♣❛t❤✱ ✫s✮ ✐❢ ✭✦❙ ■❙❘❊●✭s✳st ♠♦❞❡✮✮ ✐❢ ✭r❡s ⑤⑤ ✦❙ ■❙❘❊●✭s✳st ♠♦❞❡✮✮ ❡rr♦r✭✧♦♥❧② r❡❣✉❧❛r ❢✐❧❡s ❛❧❧♦✇❡❞✧✮❀ ❡rr♦r✭✧♦♥❧② r❡❣✉❧❛r ❢✐❧❡s ❛❧❧♦✇❡❞✧✮❀ ❡❧s❡ ❢❞ ❂ ♦♣❡♥✭♣❛t❤✱ ❖ ❘❉❖◆▲❨✮❀ ❡❧s❡ ❢❞ ❂ ♦♣❡♥✭♣❛t❤✱ ❖ ❘❉❖◆▲❨✮❀ r❡t✉r♥ ❢❞❀ r❡t✉r♥ ❢❞❀ ❣ ❣
TOCTTOU example Changing file references ✐♥t s❛❢❡❴♦♣❡♥❴❢✐❧❡✭❝❤❛r ✯♣❛t❤✮ ❢ ✐♥t ❢❞ ❂ ✲✶✱ r❡s❀ With symbolic links str✉❝t st❛t s❀ r❡s ❂ st❛t✭♣❛t❤✱ ✫s✮ With hard links ✐❢ ✭r❡s ⑤⑤ ✦❙ ■❙❘❊●✭s✳st ♠♦❞❡✮✮ With changing parent directories ❡rr♦r✭✧♦♥❧② r❡❣✉❧❛r ❢✐❧❡s ❛❧❧♦✇❡❞✧✮❀ ❡❧s❡ ❢❞ ❂ ♦♣❡♥✭♣❛t❤✱ ❖ ❘❉❖◆▲❨✮❀ r❡t✉r♥ ❢❞❀ ❣ Directory traversal with ✳✳ Environment variables Can influence behavior in unexpected ways Program argument specifies file, found P❆❚❍ in directory ❢✐❧❡s ▲❉ ▲■❇❘❆❘❨ P❆❚❍ ■❋❙ What about . . . ❢✐❧❡s✴✳✳✴✳✳✴✳✳✴✳✳✴❡t❝✴♣❛ss✇❞ ? Also umask, resource limits, current directory IFS and why it’s a problem Next time In Unix, splitting a command line into words is the shell’s job String ✦ argv array Bugs particular to low-level (e.g., C) ❣r❡♣ ❛ ❜ ❝ vs. ❣r❡♣ ✬❛ ❜✬ ❝ programs Choice of separator characters (default space, tab, newline) is configurable Exploit s②st❡♠✭✧✴❜✐♥✴✉♥❛♠❡✧✮
Recommend
More recommend