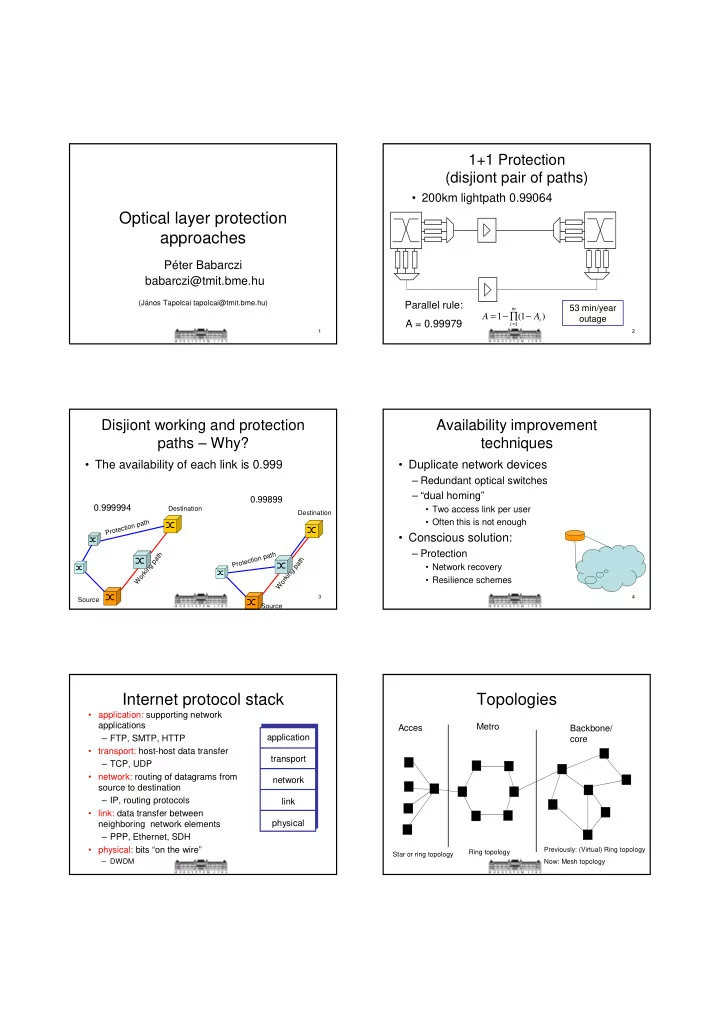

1+1 Protection (disjiont pair of paths) • 200km lightpath 0.99064 Optical layer protection approaches Péter Babarczi babarczi@tmit.bme.hu (János Tapolcai tapolcai@tmit.bme.hu) Parallel rule: m 53 min/year = 1 − ∏ ( 1 − ) A A outage i A = 0.99979 i = 1 1 2 Disjiont working and protection Availability improvement paths – Why? techniques • The availability of each link is 0.999 • Duplicate network devices – Redundant optical switches – “dual homing” 0.99899 0.999994 Destination • Two access link per user Destination Protection path • Often this is not enough • Conscious solution: – Protection Working path Protection path Working path • Network recovery • Resilience schemes 3 4 Source Source Internet protocol stack Topologies • application: supporting network applications Metro Acces Backbone/ – FTP, SMTP, HTTP application core • transport: host-host data transfer transport – TCP, UDP • network: routing of datagrams from network source to destination – IP, routing protocols link • link: data transfer between neighboring network elements physical – PPP, Ethernet, SDH • physical: bits “on the wire” Previously: (Virtual) Ring topology Ring topology Star or ring topology – DWDM Now: Mesh topology
source Encapsulation Layer 5 - Application layer message M application segment H t M transport datagram H n H t network M • Supporting network frame H l H n H t M link host or host or applications physical server server – Process-to-process H l H n H t M link H l H n H t M Which layer communication using controlled by physical sockets (by exchanging should we use app developer messages) switch process process to reach higher – Berkeley Socket is a socket socket widely used API availability? (Application Programming TCP with TCP with Internet Interface) buffers, buffers, destination H n H t M network H n H t M variables • socket() – creates an variables endpoint for H l H n H t M link H l H n H t M M application communication physical H t M transport • connect() – connects a H n H t M network socket router • listen() - waiting for H l H n H t M link incoming connection physical 8 Layer 4 – Transport Layer Layer 3 – Network Layer • Routing of datagrams from source to destination • host-host data transfer • Transport segment from sending to receiving • Responsible for sending data between end host nodes – Efficiently – Transmission Control Protocol (TCP) • As much packets as possible • Best effort • Reliable end-to-end connection – Self adaptive • TCP sent in IP packets • to the changing topology fast (link state protocols like OSPF) – Error correction, congestion control, flow control – Fully distributed manner – User Datagram Protocol (UDP) • 1981: “end-to-end principle” – No intelligence in network core, only on the edges • Unreliable, but fast 9 10 Layer 2 – Data link layer Layer 1 – Physical layer • Data transfer between neighboring network • Optical channels in the core/backbone elements – DWDM – Dense wavelength division – has responsibility of transferring datagram from one node to adjacent node over a link multiplexing – Aggregated traffic – Deploy lightpaths between users • State-dependent • Finer routing • Dynamically configured – Traditionally network are statically configured – Reserve flows on the links • Reliable infrastructure – Error detection, error correction, flow control 11 12
Optical layer protection Recovery in multi-layer networks • Protect connections in lower layers (1-2) Traffic – Waiting for upper layer protocols (e.g. OSPF in layer 3) to adapt Refresh the routing table Refresh the routing table to the failure introduce high latency in the network (link is failed) (link is operating) • A network recovery mechanism, which Detect, that the link is – Detects the failure ALARM operational again – Reroute the traffic on an operating path Switching node The link is protected by the optical layer Working path Link failure Recovered segment Protection path Destination 100 ms 10 sec 10 sec • Rapid reaction in the upper layer cause redundant Sorce recovery action Swithing or splitting node 13 14 Source: RHK Recovery cycle of a protection Protection and restoration method 100%, fast No guarantee, slower Different protection Sending fault Data flow arrives at the approaches from down to after failure event occures notification pre-planned destination node top (e.g. Dedicated Path (restoration) Hold-Off time (protection) protection or Failure Traffic Recovery time Dependent Shared Link Recovery time Protection) link path link path segment segment Recovery operation (switching) time Fault detection Fault notification time time time dedicated dedicated shared notification shared failure dedicated Failure dependent shared The service is Failure detected by the The protection path is The service is Faiure independent operational nearast node deployed operational (the faied element is unknown) Failure dependent After failure is repaired: reversion cycle to optimize the Faiure independent usage of network resources (the faied element is unknown) 15 16 Link, segment and path protection Dedicated protection 1 2 3 1 2 3 Failure 4 5 6 4 5 6 7 8 9 7 8 9 Back 1 1 hauling 1 Link The working and 2 1 2 3 1 2 3 protection paths Failure Failure 1 operate during 4 5 6 1 4 5 6 the whole 7 8 1 9 8 7 9 holding time of Path Segment the connection Protection resources (hot stand-by) 17 18 are additional
Shared protection for single link Dedicated 1+1 protection failures • Signal is sent parallel on two disjoint paths – Both configured and signaled at connection setup • If the destination node sense the degradation of the 1 signal on the working path, switches over the protection 1 path (single end switching) 1 • Simple (thus widely deployed) but capacity consuming (hot stand-by) 1 • Recovery time: • If two working Shared 1 1 paths are link Fault Detection Splitter Switch bandwidth Path 1 Fault notification time Time 1 disjoint, their time Source Backup resources are protection Destination Path 2 failure not additional, their capacity is Hold-Off Switching time 1+1 maximum need to be Time shareable. 19 20 reserved Dedicated 1:1 protection Dedicated m:n protection • Common pool m of protection paths are given • Two disjoint paths are reserved for a set of working paths n – Data is sent only on the working path – Protection resources can be used for route low priority traffic • Consumes less resources • If the working path failes, switching is needed both in • Lower availability source and destinaiton node – Low priotity traffic is preempted • Calculate the availabilty of 1:1 protection: • Recovery time: – A w , A p Switch Fault n working paths Switch A=1-(1-A w )(1-A p )=A w +A p -A w A p Fault notification time Detection Time ... Working path • And for 1:2 protection: Source time Source protection – A w1 , A w2 , A p Destination failure path Destination Protection Path Hold-Off Switching time A=A w1 A w2 +(1-A w1 )A w2 A p +A w1 (1-A w2 )A p 1:1 1:n Time 21 22 Dedicated m:n protection Topologies Metro Acces Backbone/ core n working paths ... Source ... Destination m protection paths m:n Previously: (Virtual) Ring topology Ring topology Star or ring topology Now: Mesh topology 23
Mesh topology Shared Risk (Link) Group • Disjoint working and protection paths • Set of network elements which share a common risk of failure (and fail together) – The problem is more complex than in ring topology – physical devices SRLGs – protocols Working path – links – nodes Assumption: SRLG failures are independent! Protection path 25 26 Suurballe’s algorithm – finding link SRG disjoint pair of paths disjoint paths (1) • Given: • Shortest path finding algorithm used (e.g. – Graph representation of the topology G=(V,E) Dijkstra’s algorithm) – list of SRGs, • Objective: 2 1 – Find SRG disjoint working and protection path 1 – SRGs result an s-d cut in the topology are not considered in the routing problem 1 Dst Src 1 1 2 27 28 Védelmi út Suurballe’s algorithm – finding link Suurballe’s algorithm – finding link disjoint paths (2) disjoint paths (3) • Direct edges in the opposite direction and • Get the pair of disjoint paths (first the red find shortest path in the modified graph one) Use the other shortest path if needed 2 1 -1 -1 Dst Dst Src Src -1 1 2 29 30
Recommend
More recommend