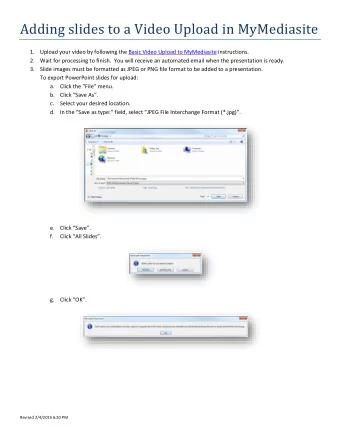
FUSE: Finding File Upload Bugs via Penetration Testing Taekjin Lee, - PowerPoint PPT Presentation
FUSE: Finding File Upload Bugs via Penetration Testing Taekjin Lee, Seongil Wi , Suyoung Lee, Sooel Son KAIST Upload Functionality Sharing user-provided content has become a de facto standard feature of modern web applications 2 File
FUSE: Finding File Upload Bugs via Penetration Testing Taekjin Lee, Seongil Wi , Suyoung Lee, Sooel Son KAIST
Upload Functionality • Sharing user-provided content has become a de facto standard feature of modern web applications 2
File Uploading Procedure Web server PHP interpreter Web application File Content-filtering Extractor checks Disable uploading NDSS.png specified file types NDSS.png Upload request [HTTP(S) POST] User A 3
File Uploading Procedure Web server PHP interpreter Web application File Content-filtering Extractor https://wsplab.com/NDSS.png checks NDSS.png Download NDSS.png Upload Access request https://wsplab.com/NDSS.png User A User B 4
Disable Uploading Malicious Files Web server PHP interpreter Web application File Content-filtering Discard Extractor checks webshell.php <?php system(‘ls’); ?> webshell.php Upload request Attacker 5 5
Content-filtering Checks Content-filtering checks php <?php $black_list = array(‘js’,‘php’,‘html’,...) if (!in_array(ext($file_name), $black_list)) { <?php Error: move($file_name, $upload_path); system(‘ ls ’); forbidden } ?> file type else { PHP interpreter webshell.php message(' Error: forbidden file type '); } ?> 6
File Upload Vulnerabilities - Server Side What will be happening? Web server PHP interpreter Web application File Content-filtering Discard Extractor checks webshell.php <?php Unrestricted File Upload Potential code system(‘ls’); <?php ?> execution (UFU) system(‘ls’); webshell.php ?> webshell.php Upload request Attacker 7 7
File Upload Vulnerabilities - Server Side Arbitrary code execution Unrestricted Executable via a URL Web server File Upload (UEFU) PHP interpreter Web application File Content-filtering Extractor checks Unrestricted File Upload Potential code <?php execution (UFU) system(‘ls’); ?> webshell.php Access https://wsplab.com/webshell.php Attacker 8
File Upload Vulnerabilities - Client Side Arbitrary code execution Unrestricted Executable Web server File Upload (UEFU) via a URL PHP interpreter Web application File Content-filtering Extractor <html> https://wsplab.com/xss.html checks <script> alert(‘xss’); Unrestricted File Upload </script> < html > < script > </html> (UFU) alert(‘xss’); xss.html </ script > </ html > xss.html Upload Access request https://wsplab.com/xss.html Attacker Victim 9
How to Find UEFU Vulnerabilities? Web server PHP interpreter Web application File Content-filtering Extractor checks #1: Bypassing application-specific checks Executable Upload request Attacker 10 10
How to Find UEFU Vulnerabilities? #2: Preserving the Web server execution semantic PHP interpreter Web application File Content-filtering Extractor https://wsplab.com/Executable checks #1: Bypassing application-specific checks Executable Upload request Attacker Victim 11 11
#2: Preserving the Execution Semantic Web server PHP interpreter Web application File Content-filtering Extractor checks <?php #1: Bypassing system(‘ls’); <?php ?> application-specific checks system(‘ls’); webshell.foo ?> php → foo webshell.foo Upload request Attacker 12 12
#2: Preserving the Execution Semantic A web server does not #2: Preserving the execute webshell.foo execution semantic Web server (Not a php-style extension) PHP interpreter Web application File Content-filtering Extractor checks Potential code #1: Bypassing <?php application-specific checks execution system(‘ls’); ?> webshell.foo Access https://wsplab.com/webshell.foo Attacker 13 13 13
Summary #2: Preserving the Web server execution semantic PHP interpreter Web application File Content-filtering Extractor https://wsplab.com/Executable checks #1: Bypassing application-specific checks Executable Upload request Attacker Victim 14 14
Previous Studies • Static analysis − Pixy, Oakland ’06 − Merlin, PLDI ’09 Few studies have addressed • Dynamic analysis finding U(E)FU vulnerabilities ! − Saner, Oakland ’08 − Riding out DOMsday, NDSS ’18 • Symbolic execution − NAVEX, USENIX ’18 − SAFERPHP, PLAS ’11 15
How we address all the challenges? 16
We propose FUSE 17
Our Approach Web server PHP interpreter Web application File Content-filtering Rejected Extractor checks Initial upload FUSE request 18 18
Our Approach - Mutate Upload Request Web server PHP interpreter Web application File Content-filtering Rejected Extractor checks UEFU vulnerability Mutated upload FUSE request 19 19
Our Approach Analyze web servers #2: Preserving the Web server execution semantic and browsers PHP interpreter Web application File Content-filtering Extractor https://wsplab.com/Executable checks Investigate root causes #1: Bypassing application-specific checks of U(E)FU bugs Executable Initial upload FUSE request Victim 20 20
Our Approach Analyze web servers Analyze web servers Web server and browsers and browsers PHP interpreter Web application File Content-filtering Extractor https://wsplab.com/Executable checks Investigate root causes of U(E)FU bugs Web server Executable Initial upload FUSE request Victim 21 21
Mutate Upload Request Analyze web servers Investigate root causes and browsers of U(E)FU bugs Web server Design 13 Mutate Initial upload FUSE mutation operations request 22 22
Our Goal: Finding U(E)FU Bugs Mutator Uploader Mutated upload request 23
Our Goal: Finding U(E)FU Bugs Mutator Uploader Validator Mutated Upload upload request information UFU and UEFU vulnerabilities 24
Upload Request filename content-type content Web server Upload FUSE request 25
Upload Request filename xss.html content-type <html> text/html <script> content alert(‘xss’); </script> <html><script>al </html> ert(‘xss’)</scri xss.html pt></html> Upload request 26
Five objectives that trigger Mutation Objectives common mistakes in implementing checks filename Content-filtering checks xss.html if (finfo_file( content ) not in expected_type) content-type reject(file); text/html if (ext( file_name ) not in expected_ext) content reject(file); if (expected_keyword in content ) <html><script>al reject(file); ert(‘xss’)</scri if ( content_type not in expected_type) pt></html> reject(file); accept(file) Upload request 27
Mutation Objectives #1 filename Content-filtering checks xss.html if (finfo_file( content ) == ‘text/html’) content-type reject(file); text/html Exploiting the absence of if (ext( file_name ) == ‘php’) content reject(file); content-filtering checks if ( ‘ <?php ’ in content ) <html><script>al reject(file); ert(‘xss’)</scri if ( content_type == ‘text/html’) pt></html> reject(file); accept(file) Upload No mutation request 28
Mutation Objectives #2 ‘image/png’ filename Content-filtering checks xss.html if (finfo_file( content ) == ‘text/html’) content-type reject(file); text/html if (ext( file_name ) == ‘php’) content \x89\x50\x4e\x47 reject(file); Causing incorrect type if ( ‘ <?php ’ in content ) \x0d\x0a\x1a... <html><script>al inferences based on reject(file); ert(‘xss’)</scri <html><script>al PNG header if ( content_type == ‘text/html’) pt></html> ert(‘xss’)</scri content reject(file); pt></html> accept(file) Upload M1: Prepending a resource header request 29
Mutation Objectives #3 filename Content-filtering checks ‘php5’ webshell.php5 webshell.php if (finfo_file( content ) == ‘text/html’) content-type reject(file); application/x-php if (ext( file_name ) == ‘php’) content reject(file); if ( ‘ <?php ’ in content ) <?php Exploiting incomplete reject(file); system(‘ls’); if ( content_type == ‘text/html’) blacklist based on ?> reject(file); extension accept(file) Upload M4: Changing a file extension request 30
Mutation Objectives #4 filename Content-filtering checks webshell.php Bypassing keyword if (finfo_file( content ) == ‘text/html’) content-type checks based on content reject(file); application/x-php if (ext( file_name ) == ‘php’) content reject(file); if ( ‘ <?php ’ in content ) <? <?php reject(file); system(‘ls’); system(‘ls’); ‘<?’ if ( content_type == ‘text/html’) ?> ?> reject(file); accept(file) Upload M5: Replace PHP tags with short tags request 31
Mutation Objectives #5 filename Content-filtering checks xss.html if (finfo_file( content ) == ‘text/html’) content-type Bypassing filtering logic reject(file); image/png text/html if (ext( file_name ) == ‘php’) based on content-type content reject(file); ‘image/png’ if ( ‘ <?php ’ in content ) <html><script>al reject(file); ert(‘xss’)</scri if ( content_type == ‘text/html’) pt></html> reject(file); accept(file) Upload M3: Changing the content-type of an upload request request 32
Recommend
More recommend
Explore More Topics
Stay informed with curated content and fresh updates.