
Material and some slide content from: Taylor et. al. http://queue.acm.org/detail.cfm?id=1556050 http://seclab.stanford.edu/websec/chromium/chromium-security-architecture.pdf OS-Level Sandbox OS/Runtime OS/Runtime Exploit Barriers Exploit Barriers JavaScript Sandbox Browser Kernel Web Content (trusted) (untrusted) IPC Channel Architecture in Practice: Chrome Reid Holmes
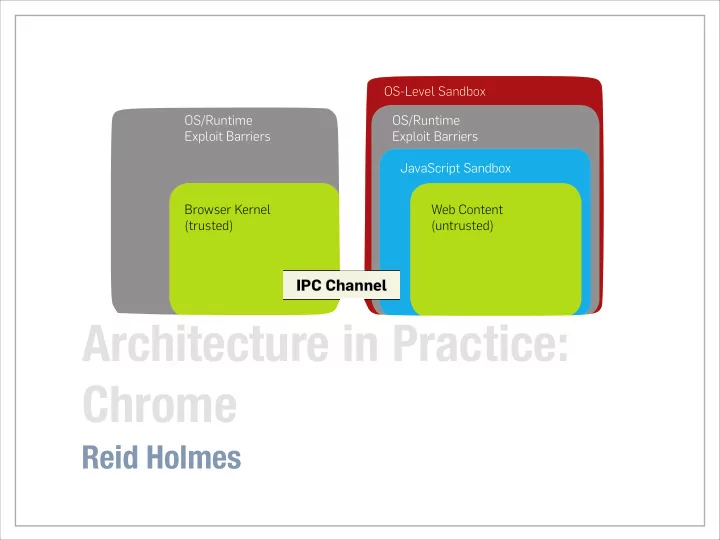
Chrome ‣ Online content is insecure and can compromise: ‣ Confidentiality: Leak user data ‣ Integrity: Read/write arbitrary data on disk ‣ Availability: Crash host application and/or OS Chrome relies on least privilege , separation of privilege, and defence in depth to securely parse and render insecure content. REID HOLMES - SE2: SOFTWARE DESIGN & ARCHITECTURE
Chrome architecture OS-Level Sandbox OS/Runtime OS/Runtime Exploit Barriers Exploit Barriers JavaScript Sandbox Browser Kernel Web Content (trusted) (untrusted) IPC Channel REID HOLMES - SE2: SOFTWARE DESIGN & ARCHITECTURE
Recommend
More recommend