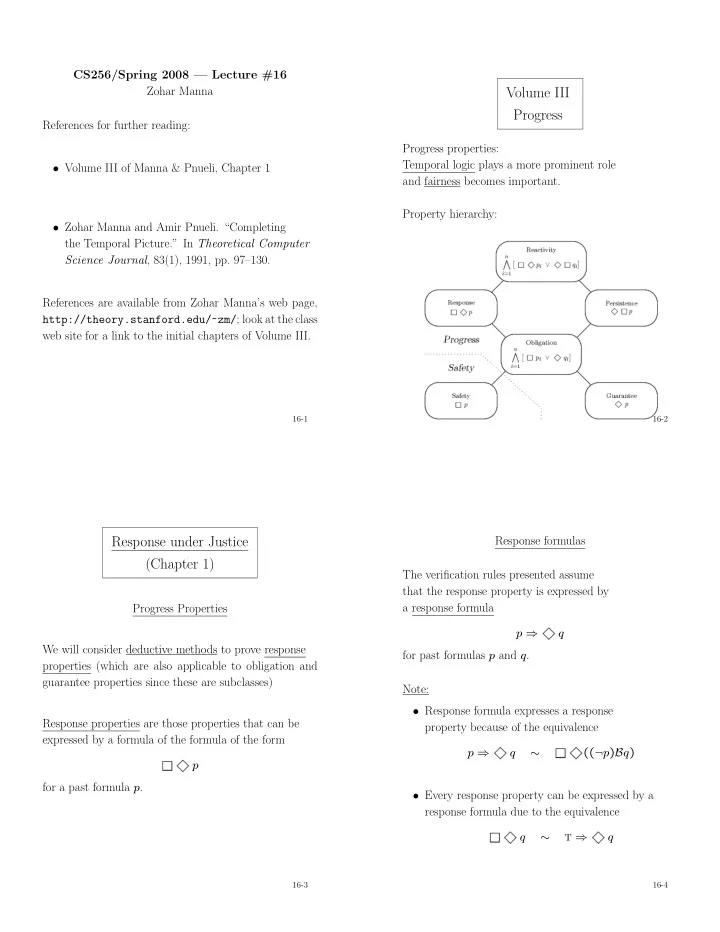

CS256/Spring 2008 — Lecture #16 Zohar Manna Volume III Progress References for further reading: Progress properties: Temporal logic plays a more prominent role • Volume III of Manna & Pnueli, Chapter 1 and fairness becomes important. Property hierarchy: • Zohar Manna and Amir Pnueli. “Completing the Temporal Picture.” In Theoretical Computer Science Journal , 83(1), 1991, pp. 97–130. References are available from Zohar Manna’s web page, http://theory.stanford.edu/~zm/ ; look at the class web site for a link to the initial chapters of Volume III. 16-1 16-2 1 Response under Justice Response formulas (Chapter 1) The verification rules presented assume that the response property is expressed by a response formula Progress Properties 1 0 1 0 1 p ⇒ q We will consider deductive methods to prove response for past formulas p and q . properties (which are also applicable to obligation and guarantee properties since these are subclasses) Note: 0 1 1 • Response formula expresses a response Response properties are those properties that can be property because of the equivalence expressed by a formula of the formula of the form p ⇒ q ∼ (( ¬ p ) B q ) p for a past formula p . • Every response property can be expressed by a response formula due to the equivalence q ∼ t ⇒ q 16-3 16-4
1 Overview Overview (Cont’d) We consider the simple case where p , q are assertions. 2. Rule chain-j (chain rule under justice) The proof of a response property A fixed number of helpful transitions p ⇒ q (independent of the value of variables) often relies on the identification of one or more so-called suffices to establish the property helpful transitions. We consider three cases: p 1. Rule resp-j τ h n (single-step response under justice) A single helpful transition τ h suffices ϕ n − 1 to establish the property τ h n − 1 p ϕ 1 τ h τ h 1 q q 16-5 16-6 Overview (Cont’d) Overview (Cont’d) In all cases we will be able to use 3. Rule well-j verification diagrams to represent the proof. (well-founded response under justice) The number of helpful transitions required to estab- In practice, verification diagrams are often the lish the property is unbounded preferred way to prove progress properties, because they represent the temporal structure p of the program relative to the property. q 16-7 16-8
1 1 Single-step rule (Motivation) Single-step rule p ⇒ q For assertions p , q , ϕ , and helpful transition τ h ∈ J , J1. p → q ∨ ϕ J2. { ϕ } T { q ∨ ϕ } En ( τ h ) J3. { ϕ } τ h { q } J4. ϕ → En ( τ h ) ϕ p ⇒ q τ h p q Premise J2 requires all transitions to preserve ϕ (or es- tablish q , in which case we are done). Premise J4 ensures that the helpful transition τ h will be continuously enabled. It ensures, by the justice requirement, that τ h will even- tually be taken. Premise J3 guarantees that it will establish q . Justice requirement: it is not the case that a just transi- tion is continuously enabled but never taken. 16-9 16-10 1 1 1 Single-step rule (Cont’d) Useful rules In practice, this rule is not very useful: • Monotonicity: Very few properties rely on just a single helpful transition. 1 1 p ⇒ q q ⇒ r r ⇒ t 1 p ⇒ t This leads to the chain rule, where we have several in- termediate properties. • Reflexivity: 1 1 p ⇒ p 1 • Transitivity: p ⇒ q q ⇒ r p ⇒ r • Case analysis: p ⇒ r q ⇒ r ( p ∨ q ) ⇒ r 16-11 16-12
1 Chain rule (Motivation) p ⇒ q Chain rule For assertions p, q = ϕ 0 and ϕ 1 , . . . , ϕ m ϕ m and helpful transitions τ h 1 , . . . , τ h m ∈ J τ h m s j ← rank m -1 m � J1. p → ϕ j ϕ m − 1 j =0 τ h m − 1 � 1 J2. { ϕ i }T ϕ j j ≤ i for i = 1 , . . . , m q � J3. { ϕ i } τ h i ϕ j ϕ 1 j<i τ h 1 J4. ϕ i → En ( τ h i ) ϕ 0 = q p ⇒ q J2: rank never increases For state s j : let ϕ i be the intermediate formula with the J3: rank decreases smallest i such that s j ϕ i . Then i is the rank of s j . 16-13 16-14 Chain rule (Cont’d) Verification Diagrams It is our task to find the intermediate assertions Nodes: labeled by assertions ϕ i ϕ m , . . . , ϕ 1 . Terminal node ϕ 0 Premise J2 ensures that all transitions either preserve the current assertion or move down to a lower-ranked assertion. Edges: labeled by transitions single-lined Premise J4 ensures that the helpful transition τ h i is enabled (represents a regular transition) for ϕ i , which makes it impossible to stay in ϕ i forever, by the justice requirement. double-lined (represents a helpful transition) Premise J3 guarantees that the helpful transition moves down to a strictly lower-ranked assertion. Since premises J2–J4 hold for every 1 ≤ i ≤ m , this ensures that ϕ 0 = q will be reached eventually. 16-15 16-16
Chain diagram: verification conditions Chain diagram 1. single τ -edges well-formedness conditions: ϕ • weakly acyclic in − → : τ τ if ϕ i − → ϕ j then i ≥ j • acyclic in = ⇒ : ϕ 1 ϕ n if = ⇒ ϕ j then i > j ϕ i { ϕ } τ { ϕ ∨ ϕ 1 ∨ . . . ∨ ϕ n } • every nonterminal node has a double edge departing nonterminal node with no outgoing τ -edges: from it • no transition can label both a single and a double ϕ edge departing from the same node. { ϕ } τ { ϕ } Note: No Verification Condition for terminal node. 16-17 16-18 1 Chain diagram verification conditions (Cont’d) Chain diagrams: validity A chain diagram is P -valid 2. double τ -edges if all the verification conditions associated with the dia- gram are P -valid. ϕ Claim: A P -valid chain diagram establishes that 1 m τ τ � ϕ j ⇒ ϕ 0 j =0 is P -valid. ϕ 1 ϕ n m � With p → ϕ j and ϕ 0 → q , j =0 { ϕ } τ { ϕ 1 ∨ . . . ∨ ϕ n } we can conclude the P -validity of p ⇒ q 3. enabling condition τ ϕ ϕ → En ( τ ) 16-19 16-20
Example: Program mux-pet1 (Fig. 3.4) (Peterson’s Algorithm for mutual exclusion) Example: Accessibility for mux-pet1 local y 1 , y 2 : boolean where y 1 = f , y 2 = f In Chapter 3 of the SAFETY book we s : integer where s = 1 established 1-bounded overtaking, expressed by ℓ 0 : loop forever do at − ℓ 3 ⇒ ¬ at − m 4 W at − m 4 W ¬ at − m 4 W at − ℓ 4 ℓ 1 : noncritical for mux-pet1 with the following wait -diagram ℓ 2 : ( y 1 , s ) := ( t , 1) P 1 :: ℓ 3 : await ( ¬ y 2 ) ∨ ( s � = 1) ✬ ✩ ℓ 4 : critical at − ℓ 3 ✤ ✜ ℓ 5 : y 1 := f ϕ 3 : at − m 3 ∧ s = 1 � � ✣ ✢ � � � � m 3 ✤ ✜ m 0 : loop forever do ❄ ϕ 2 : at − m 4 ✣ ✢ m 1 : noncritical m 4 ✤ ✜ m 2 : ( y 2 , s ) := ( t , 2) ❄ ϕ 1 : at − m 0 .. 2 , 5 ∨ ( at − m 3 ∧ s = 2) P 2 :: ✣ ✢ m 3 : await ( ¬ y 1 ) ∨ ( s � = 2) ✫ ✪ m 4 : critical ℓ 3 ✤ ✤ ✤ ✤ ✤ ✤ ✤ ✤ ✤ ✤ ✤ ✜ ✜ ✜ ✜ ✜ ✜ ✜ ✜ ✜ ✜ ✜ ❄ m 5 : y 2 := f ϕ 0 : at − ℓ 4 ✣ ✣ ✣ ✣ ✣ ✣ ✣ ✣ ✣ ✣ ✢ ✢ ✢ ✢ ✢ ✢ ✢ ✢ ✢ ✢ ✣ ✢ 16-21 16-22 1 Example (Cont’d) Example (Cont’d) The problem with We now want to establish accessibility, expressed by ϕ 1 : ( at − m 0 .. 2 , 5 ∨ ( at − m 3 ∧ s = 2)) ∧ at − ℓ 3 is the disjunct at − m 5 , because at − ℓ 3 ⇒ at − ℓ 4 at − m 5 → ¬ En ( ℓ 3 ) Since the two properties seem similar we would like to Therefore we separate this disjunct and create two new transform the wait diagram into a chain diagram. This assertions requires a double edge departing from every node. The ϕ ′ 1 : at − m 5 ∧ at − ℓ 3 edges labeled by m 3 and m 4 can be converted into double edges immediately since we have ϕ ′′ 1 : ( at − m 0 .. 2 ∨ ( at − m 3 ∧ s = 2)) ∧ at − ℓ 3 As helpful transition for ϕ ′ 1 we identify m 5 . Clearly ϕ 3 → En ( m 3 ) and ϕ 2 → En ( m 4 ) ϕ ′ 1 → En ( m 5 ) However, ϕ 1 �→ En ( ℓ 3 ) , so we have to do some more and m 5 leads from ϕ ′ 1 to ϕ ′′ 1 . Now we have work on ϕ 1 . ϕ ′′ 1 → En ( ℓ 3 ) and ℓ 3 leads from ϕ ′ 1 to ϕ 0 , as required. With some rearrangement of assertion numbers, and simplification of ϕ ′′ 1 , 16-23 16-24 this leads to the following chain diagram.
Recommend
More recommend