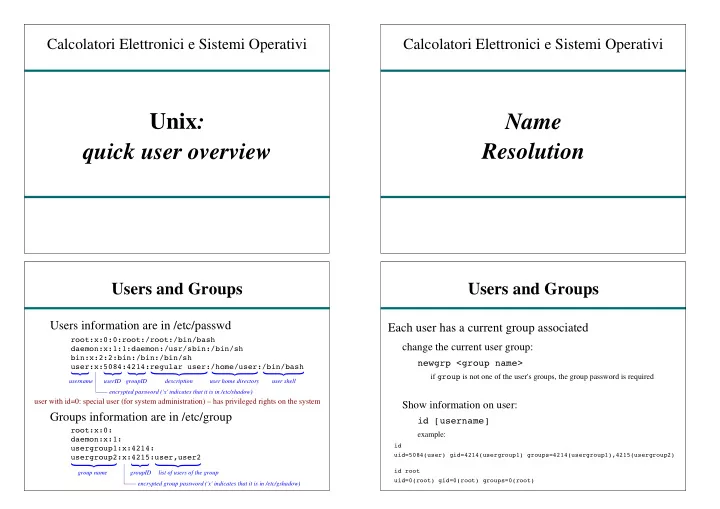

Calcolatori Elettronici e Sistemi Operativi Calcolatori Elettronici e Sistemi Operativi Unix : Name Resolution quick user overview Users and Groups Users and Groups Users information are in /etc/passwd Each user has a current group associated root:x:0:0:root:/root:/bin/bash change the current user group: daemon:x:1:1:daemon:/usr/sbin:/bin/sh bin:x:2:2:bin:/bin:/bin/sh newgrp <group name> user:x:5084:4214:regular user:/home/user:/bin/bash if group is not one of the user's groups, the group password is required username userID groupID description user home directory user shell encrypted password ('x' indicates that it is in /etc/shadow) user with id=0: special user (for system administration) – has privileged rights on the system Show information on user: Groups information are in /etc/group id [username] root:x:0: example: daemon:x:1: id usergroup1:x:4214: uid=5084(user) gid=4214(usergroup1) groups=4214(usergroup1),4215(usergroup2) usergroup2:x:4215:user,user2 id root group name groupID list of users of the group uid=0(root) gid=0(root) groups=0(root) encrypted group password ('x' indicates that it is in /etc/gshadow)
Users and Groups Users and Groups Passwords can be in /etc/shadow Passwords can be in /etc/shadow not readable by regular users not readable by regular users salt data = crypt (salt, password) based on MD5 algorithm root:$1$abcdefgh$sftjbP9Enm3qjnYVfbhrW.:15432:0:99999:7::: root:$1$abcdefgh$sftjbP9Enm3qjnYVfbhrW.:15432:0:99999:7::: daemon:*:15223:0:99999:7::: daemon:*:15223:0:99999:7::: bin:*:15223:0:99999:7::: bin:*:15223:0:99999:7::: user:abfdATwZM2ZO6:15551:0:79:7::: user:abfdATwZM2ZO6:15551:0:79:7::: username reserved field salt data = crypt (salt, password) based on DES algorithm days since Jan 1, 1970 that account is disabled days after password expires that account is disabled days before password is to expire that user is warned Salt is used to mitigate dictionary attacks days after which password must be changed days before password may be changed days since Jan 1, 1970 that password was last changed encrypted password Hostnames Networks � /etc/hosts � /etc/networks � format (plain text): � format (plain text): <ip address> <hostname> [aliases] <network name> <ip number> [aliases] � example � example 127.0.0.1 localhost default 0.0.0.0 loopback 127.0.0.0 10.0.2.21 host1.localnet.org host1 link-local 169.254.0.0 localnet 10.0.2.0 10.0.2.22 host2.localnet.org h2 159.65.34.8 www.opensource.org 147.75.44.153 www.kernel.org
Internet network services list Name Service Switch � configuration file : /etc/nsswitch.conf � /etc/services � format (plain text): � format (plain text): <database> <sources list> <service name> <port/protocol> [aliases] � database: passwd | group | shadow | hosts | networks | services | rpc | initgroups | netgroup | protocols | � example ftp 21/tcp publickey ssh 22/tcp ssh 22/udp � examples: telnet 23/tcp � passwd : User passwords � shadow : Shadow user passwords entr � group : Groups of users entr = getservbyname ("ftp", "tcp"); s_name ftp s_aliases � hosts : Host names and numbers s_port: 21 � more info : man nsswitch.conf s_proto s_proto Name Service Switch Name Service Switch � format (plain text): � /etc/nsswitch.conf example: � sources list: <source> <source> <source> ... � source: files | nis | db | dns | ... passwd: compat group: compat shadow: compat � examples: hosts: files dns � files : read from file (/etc/passwd, /etc/shadow, /etc/group, /etc/hosts, ...) networks: files � nis : query a NIS (Network Information Service) server ethers: db files gethostbyname ("www.host.dom"); protocols: files � db : read from file (/var/db/passwd.db, ...) in "Berkeley Databases" format rpc: files � dns : 1. Search in /etc/hosts (for hosts) query a DNS (Domain Name System) server services: files � compat : similar to files, but some information is read from a NIS server netgroup: nis 2. Query a DNS server (for passwd, group, shadow)
Calcolatori Elettronici e Sistemi Operativi File information Show file info: number of hard links ls -l owner group size mtime } } } drwxr-xr-x 4 root root 4096 2010-06-08 20:20 apt Files -rw-r--r-- 1 root root 351 2008-03-25 09:38 arpwatch.conf -rw-r--r-- 1 root root 2286 2011-12-11 12:57 asound.names -rw-r----- 1 root daemon 144 2008-10-20 07:34 at.deny } } } permissions for others Type: permissions for group - regular file permissions for owner d directory l symbolic link type b block special file c character special file p FIFO (named pipe) s socket ? some other file type Unix file ownership Unix file permissions Each file has: r w x r – x r - x file owner : an user of the system } } } group : a group of users (each user is part of one or more groups) permissions for others permissions for group permissions for owner Changing file ownership (only root): Permissions are three flags: chown <new_owner>:<new_group> <file> change both owner and group r : can read w : can write chown <new_owner> <file> change only owner x : can execute (for directories: can search) chown :<new_group> <file> change only group Permissions can be expressed as three octal digits (each octal digit is 3-bit) Examples: new_owner and new_group can be names or numeric ids rwx r-x r-x � 0755 rw- r-- r-- � 0644 only root can change a file's owner r-x --- --- � 0500 r-- r-- r-- � 0444 a regular user can assign the file's group only to one of its own groups
Unix file permissions Access Control List Other flags (globals): � ACL set user id : if executed, the effective user id of the process becomes the id of the file owner set group id : if executed, the effective group id of the process becomes the id of the file group sticky : for directory, files contained can be deleted only by the directory's or the file's owner (or by root) � each file has a list of users and their related permissions � getfacl : get file access control lists Changing file permissions (only the owner or root): � setfacl : set file access control lists chmod <new_permissions> <file> <new_permissions>: user1 user: group1 group: octal representation rw-r----- perms: users[+-]permission ACL Examples: u+r : add read permission for owner (user) u-w : remove write permission for owner (user) user2 user3 user4 user: user: user: og+x : add executable permission for group and others r-- rw- r-x perms: perms: perms: u+s : add set user id flag g-s : remove set group id flag Access Control List Sparse files $ ls -l /dev/kvm #include <sys/types.h> On some filesystems, unused space is not allocated #include <sys/stat.h> crw-rw----+ 1 root kvm 10, 232 Oct 19 16:59 /dev/kvm #include <fcntl.h> #include <unistd.h> ls -ls sparsefile #include <string.h> there is some other info #include <errno.h> 8 -rw-r--r-- 1 user usergrp 1000001 May 11 21:52 sparsefile #include <stdio.h> $ getfacl /dev/kvm main() # file: dev/kvm used blocks size { # owner: root from standard permissions int fd; # group: kvm char c = 'A'; user::rw- fd = open ("sparsefile", user:user123:rw- O_RDWR | O_CREAT | O_EXCL, group::rw- S_IRUSR|S_IWUSR | S_IRGRP | S_IROTH); mask::rw- other::--- from ACL records if ( fd <0 ) { printf("Error: cannot open file. Error code is %d (%s)\n", errno, strerror(errno)); return 1; } Only move the file pointer if ( lseek (fd, 1000000, SEEK_SET) < 0 ) { printf("Error: cannot perform lseek. Error code is %d (%s)\n", errno, strerror(errno)); return 2; } write (fd, &c, 1); Write only one byte close(fd); return 0; }
Process I/O and redirections Process I/O and redirections � on creation, each process has 3 open file descriptors: � I/O redirection � 0 ( stdin ), 1 ( stdout ), 2 ( stderr ) � standard input � command1 < inputfile.txt � read ( 0 , buf, n); For command1 input data for file descriptor 0 comes � Read n bytes from standard input to buf from file inputfile.txt � write ( 2 , buf, n); � Write n bytes from buf to standard error � fprintf ( stderr , "Error message\n"); Process I/O and redirections Process I/O and redirections � I/O redirection � I/O redirection � standard output � standard error � command1 > outfile.txt � command1 2> outerrfile.txt Data written by command1 on file descriptor 1 is (bash) � command1 &> outerrfile.txt stored in file outfile.txt � command1 >& outerrfile.txt (csh and bash) � command1 >> outfile.txt Data written by command1 on file descriptor 1 is Data written by command1 on file descriptor 2 is stored (appended) in file outfile.txt stored in file outfile.txt
Process I/O and redirections Process I/O and redirections � I/O redirection � I/O redirection � standard error � pipeline � command1 2>> outerrfile.txt � command1 | command2 (bash) Data written by command1 on file descriptor 1 is sent � command1 &>> outerrfile.txt as input to command2 � command1 >>& outerrfile.txt � command1 |& command2 (csh) Data written by command1 on file descriptor 2 is sent Data written by command1 on file descriptor 2 is as input to command2 stored (appended) in file outfile.txt
Recommend
More recommend