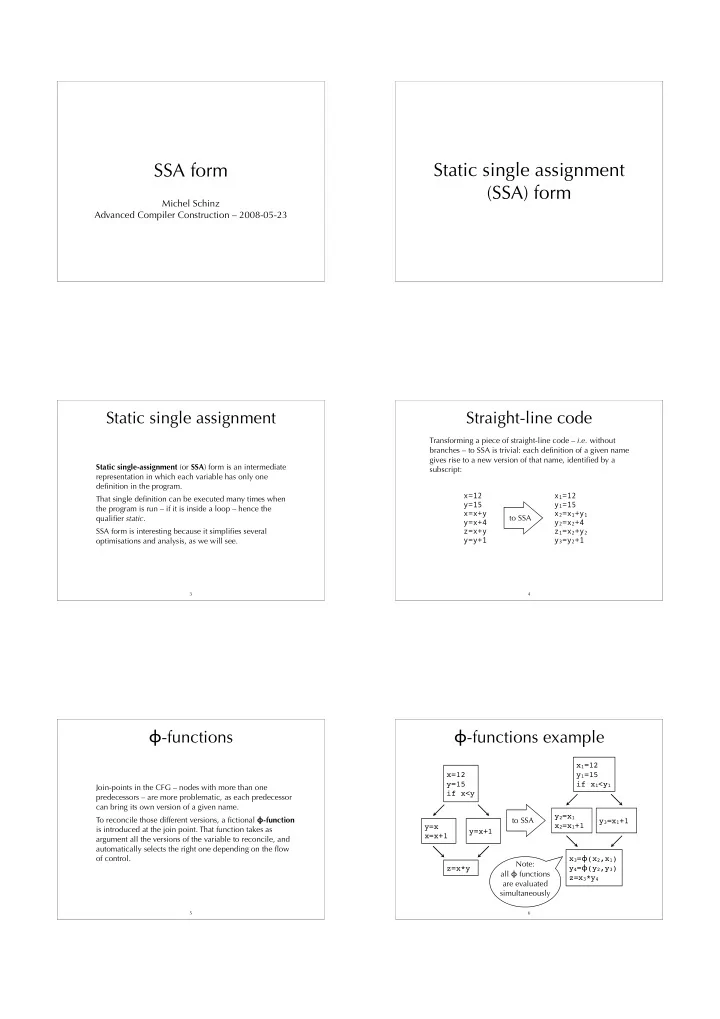

SSA form Static single assignment (SSA) form Michel Schinz Advanced Compiler Construction – 2008-05-23 Static single assignment Straight-line code Transforming a piece of straight-line code – i.e. without branches – to SSA is trivial: each definition of a given name gives rise to a new version of that name, identified by a Static single-assignment (or SSA ) form is an intermediate subscript: representation in which each variable has only one definition in the program. x=12 x 1 =12 That single definition can be executed many times when y=15 y 1 =15 the program is run – if it is inside a loop – hence the x=x+y x 2 =x 1 +y 1 qualifier static . to SSA y=x+4 y 2 =x 2 +4 SSA form is interesting because it simplifies several z=x+y z 1 =x 2 +y 2 y=y+1 y 3 =y 2 +1 optimisations and analysis, as we will see. 3 4 � -functions � -functions example x 1 =12 x=12 y 1 =15 y=15 if x 1 <y 1 Join-points in the CFG – nodes with more than one if x<y predecessors – are more problematic, as each predecessor can bring its own version of a given name. y 2 =x 1 To reconcile those different versions, a fictional � -function to SSA y 3 =x 1 +1 x 2 =x 1 +1 y=x is introduced at the join point. That function takes as y=x+1 x=x+1 argument all the versions of the variable to reconcile, and automatically selects the right one depending on the flow of control. x 3 = � (x 2 ,x 1 ) Note: y 4 = � (y 2 ,y 3 ) z=x*y all � functions z=x 3 *y 4 are evaluated simultaneously 5 6
(Naïve) building of SSA form (Naïve) building of SSA form CFG After phase 1 After phase 2 x=1 x=1 x 1 =1 Naïve technique to build SSA form: y=2 y=2 y 1 =2 z=x+y z=x+y z 1 =x 1 +y 1 • for each variable x of the CFG, at each join point n , insert a � -function of the form x = � ( x ,…, x ) with as many parameters as n has predecessors, y=y-1 y=y+1 y=y-1 y=y+1 y 2 =y 1 -1 y 3 =y 1 +1 • compute reaching definitions, and use that information x=x+y x=y x=x+y x=y x 2 =x 1 +y 2 x 3 =y 3 to rename any use of a variable according to the – now unique – definition reaching it. y=x*2 x= � (x,x) x 4 = � (x 2 ,x 3 ) dead z=z+x y= � (y,y) y 4 = � (y 2 ,y 3 ) redundant z= � (z,z) z 2 = � (z 1 ,z 1 ) y=x*2 y 5 =x 4 *2 z=z+x z 3 =z 2 +x 4 7 8 Smarter techniques The naïve technique just presented works, in the sense that the resulting program is in SSA form and is equivalent to the original one. However, it introduces too many � -functions – some dead, Dominance some redundant – to be useful in practice. It builds the maximal SSA form. We will examine better techniques later, but to understand them we must first introduce the notion of dominance in a CFG. 9 Dominance Dominance example CFG Dominance Node Dominators 0 In a control-flow graph, a node n 1 dominates a node n 2 if 0 { 0 } 1 all paths from the start node to n 2 pass through n 1 . 1 { 0 , 1 } By definition, the domination relation is reflexive, that is a 2 3 2 { 0, 1 , 2 } node n always dominates itself. We then say that node n 1 3 { 0, 1 , 3 } 4 5 strictly dominates n 2 if n 1 dominates n 2 and n 1 � n 2 . 4 { 0, 1, 3 , 4 } The immediate dominator of a node n is the strict 6 5 { 0, 1, 3 , 5 } dominator of n closest to n . 7 6 { 0, 1, 3 , 6 } 7 { 0, 1 , 7 } (immediate dominator in bold) 11 12
Dominator tree Dominator tree example CFG Dominator tree 0 0 The dominator tree is a tree representing the dominance 1 1 relation. 2 3 2 3 The nodes of the tree are the nodes of the CFG, and a node n 1 is a parent of a node n 2 if and only if n 1 is the immediate 4 5 4 5 dominator of n 2 . 6 6 7 7 13 14 Computing dominance Dominance frontier Dominance can be computed using data-flow analysis. The dominance frontier of a node n – written To each node n of the CFG we attach a variable v n giving DF( n ) – is the set of all nodes m such that n dominates a the set of nodes that dominate n . The value of v n is given by predecessor of m , but does not strictly dominates m itself. the following equation: Informally, the dominance frontier of n contains the first v n = { n } � ( v p1 � v p2 � … � v pk ) nodes which are reachable from n but which are not strictly dominated by n . where p 1 , …, p k are the predecessors of n . 15 16 Dominance frontier example CFG Dominance frontier 0 0 nodes dominated by 3 1 1 Building SSA form 2 3 2 3 4 5 4 5 6 6 7 7 dominance frontier of 3={7} 17
Minimal SSA form Improving on minimal SSA The naïve technique to build SSA form presented earlier Reminder: the naïve technique to build SSA form presented inserts � -functions for every variable at the beginning of at the beginning computes maximal SSA form. every join point. The better technique just presented computes minimal SSA Using dominance information, it is possible to do better, form. and compute minimal SSA form: for each definition of a Unfortunately, minimal SSA form is not necessarily optimal, variable x in a node n , insert a � -function for x in all nodes and can contain dead � -functions. To solve that problem, of DF( n ). improved techniques have been developed to build semi- Notice that the inserted � -functions are definitions, and pruned – which is still not optimal – and pruned SSA form. can therefore force the insertion of more � -functions. 19 20 Semi-pruned SSA form Building semi-pruned SSA form Observation: a variable that is only live in a single node Like the naïve technique to build maximal SSA form, the can never have a live � -function. algorithm to build semi-pruned SSA form is composed of Therefore, the minimal technique can be further refined by two phases: first computing the set of global names – defined as the 1. � -functions are inserted for global names, according names that are live across more than one node – and to dominance information, producing � -functions for these names only. 2. variables are renamed. This is called semi-pruned SSA form . 21 22 Phase 1: inserting � -functions Phase 2: renaming variables Before inserting � -functions, the set G of global names must be computed. Once this is done, insertion of � - Renaming is done by a pre-order traversal of the dominator functions is done as follows: tree, as follows: for each name x in G for each node n in the dominator tree work list = all nodes in which x is defined rename definitions and uses of variables in n for each node n in work list rename � -functions parameters corresponding to n in all for each node m in DF( n ) successors of n in the CFG. insert a � -function for x in m work list = work list � { m } 23 24
Example: phase 1 Example: phase 2 CFG Algorithm (phase 1) CFG Algorithm (phase 2) for each name x in { x , y , z } a a x=1 x 1 =1 x=1 work list = all nodes in which x is defined for each node n in the dominator tree (pre-order) y=2 y 1 =2 y=2 rename definitions and uses of variables in n for each node n in work list z=x+y z 1 =x 1 +y 1 z=x+y rename � -functions parameters corresponding for each node m in DF( n ) insert a � -function for x in m to n in all successors of n in the CFG. work list = work list � { m } b c b c y=y-1 y=y+1 y 2 =y 1 -1 y=y-1 y 5 =y 1 +1 y=y+1 Dominator tree x=x+y x=y x 2 =x 1 +y 2 x=x+y x 4 =y 1 x=y Result a name x name y name z d x= � (x,x) wrk lst � -fun. d x 3 = � (x 2 ,x 4 ) x= � (x 2 ,x) x 3 = � (x 2 ,x) x= � (x,x) wrk lst � -fun. wrk lst � -fun. y= � (y,y) b c d [ a , b , c ] [ a , b , c , d ] [ a , d ] y 3 = � (y 2 ,y) y= � (y 2 ,y) y 3 = � (y 2 ,y 5 ) y= � (y,y) y=x*2 [ b , c ] for x in d [ b , c , d ] for y in d [ d ] y=x*2 y 4 =x 3 *2 y 4 =x 3 *2 y=x*2 chosen pre-order: z=z+x z 2 =z 1 +x 3 z 2 =z 1 +x 3 z=z+x z=z+x [ c , d ] for x in d [ c , d ] for y in d [] a , b , d , c [ d ] [ d ] DF( a ) = DF( d ) = {} [] [] DF( b ) = DF( c ) = { d } 25 26 Generating code from SSA After the program has been turned into SSA form and the Generating code from SSA various optimisations performed on that representation, it must be transformed into executable form. form This implies in particular that � -functions must be removed, as they cannot be implemented on standard machines. 28 Removing � -functions Removing � -functions x 1 =12 x 1 =12 y 1 =15 y 1 =15 if x 1 <a 1 if x 1 <a 1 A � -function of the form x i = � ( x 1 ,…, x n ) can be removed by inserting appropriate assignments to x i in all predecessors of the node containing that function. � -function y 2 =x 1 y 2 =x 1 y 3 =x 1 +1 y 3 =x 1 +1 This will introduce many assignments of the form x i = x j (that removal x 2 =x 1 +1 x 2 =x 1 +1 x 3 =x 1 is, move instructions), but most of them will be removed x 3 =x 2 y 4 =y 3 later during register allocation, thanks to coalescing. y 4 =y 2 x 3 = � (x 2 ,x 1 ) y 4 = � (y 2 ,y 3 ) z=x 3 *y 4 z=x 3 *y 4 29 30
Recommend
More recommend