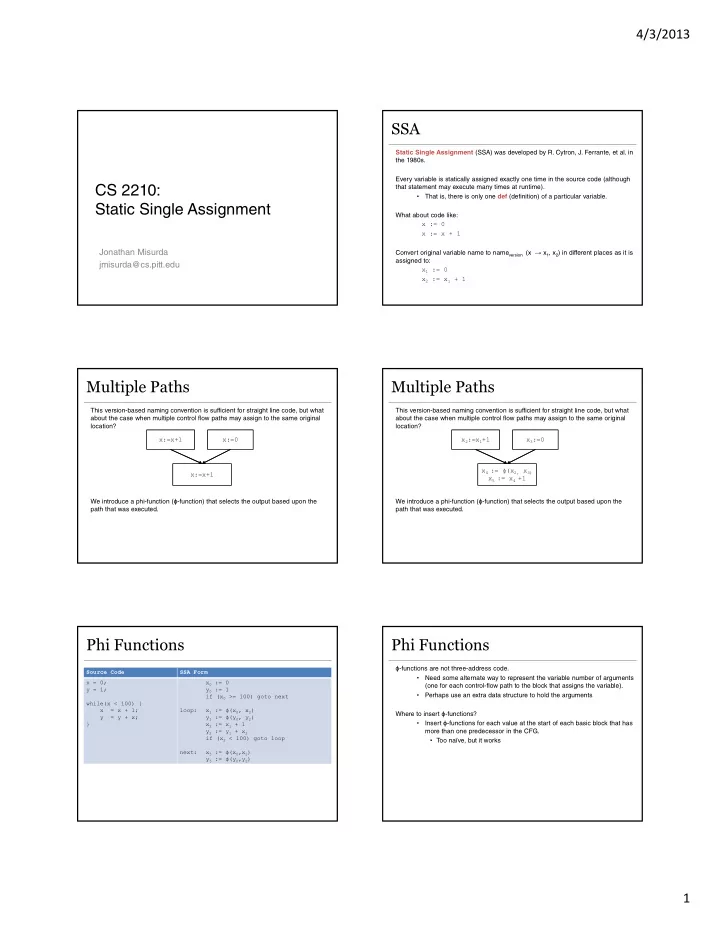

4/3/2013 SSA Static Single Assignment (SSA) was developed by R. Cytron, J. Ferrante, et al. in the 1980s. Every variable is statically assigned exactly one time in the source code (although CS 2210: that statement may execute many times at runtime). • That is, there is only one def (definition) of a particular variable. Static Single Assignment What about code like: x := 0 x := x + 1 Jonathan Misurda Convert original variable name to name version (x → x 1 , x 2 ) in different places as it is assigned to: jmisurda@cs.pitt.edu x 1 := 0 x 2 := x 1 + 1 Multiple Paths Multiple Paths This version-based naming convention is sufficient for straight line code, but what This version-based naming convention is sufficient for straight line code, but what about the case when multiple control flow paths may assign to the same original about the case when multiple control flow paths may assign to the same original location? location? x:=x+1 x:=0 x 2 :=x 1 +1 x 3 :=0 x 4 := ϕ (x 2, x 3) x:=x+1 x 5 := x 4 +1 We introduce a phi-function ( ϕ -function) that selects the output based upon the We introduce a phi-function ( ϕ -function) that selects the output based upon the path that was executed. path that was executed. Phi Functions Phi Functions ϕ -functions are not three-address code. Source Code SSA Form • Need some alternate way to represent the variable number of arguments x = 0; x 0 := 0 (one for each control-flow path to the block that assigns the variable). y = 1; y 0 := 1 • Perhaps use an extra data structure to hold the arguments if (x 0 >= 100) goto next while(x < 100) { x = x + 1; loop: x 1 := ϕ (x 0 , x 2 ) Where to insert ϕ -functions? y = y + x; y 1 := ϕ (y 0 , y 2 ) • Insert ϕ -functions for each value at the start of each basic block that has } x 2 := x 1 + 1 y 2 := y 1 + x 2 more than one predecessor in the CFG. if (x 2 < 100) goto loop • Too naïve, but it works next: x 3 := ϕ (x 0 ,x 2 ) y 3 := ϕ (y 0 ,y 2 ) 1
4/3/2013 Path-Convergence Criterion Iterated Path-Convergence There should be a ϕ -function for variable a at node z of the flow graph exactly The start node contains an implicit definition of every variable when all of the following are true: • formal parameters • a ← uninitialized 1. There is a block x containing a definition of a , 2. There is a block y (with y ≠ x ) containing a definition of a , A ϕ -function also counts as a definition of a , so the path-convergence criterion 3. There is a nonempty path P xz of edges from x to z , must be considered as a set of equations to be solved by iteration. 4. There is a nonempty path P yz of edges from y to z , while there are nodes x, y, z satisfying conditions 1–5 5. Paths P xz and P yz do not have any node in common other than z , and and z does not contain a ϕ -function for a 6. The node z does not appear within both P xz and P yz prior to the end, though it may appear in one or the other. do insert a ← ϕ (a, a, . . ., a) at node Z where the ϕ -function has as many a arguments as there are predecessors of node z . Iterated Path-Convergence Dominators The iterated path-convergence algorithm for placing ϕ -functions is not practical Certain blocks dominate other blocks in control flow graphs • • Must examine every triple of nodes x, y, z and All paths from the root to a given basic block must go through the • dominator Every path leading from x and y . 1 A much more efficient algorithm uses the dominator tree of the control flow graph. Example: Block 1 dominates blocks 2 and 3 2 3 If a block A dominates another block B, then we do not need a ϕ -function as we know one of two things: • The definitions of variables in A reach into B, unless • A redefinition of a variable happens in the path between A and B Basic Dominator Algorithm Sample CFG Dominators[r] = {r} Input: long evenSum=0; N = set of nodes in CFG int i=0; foreach node n ∈ (N - r) long evenSum=0; r = root of CFG Dominators[n] = N int i=0; while(i<1000000) { Output: if(i%2 == 0){ do Set of Dominator sets for changed = false evenSum+=i; while(i<1000000) each CFG node foreach node n ∈ (N - r) } T = N i++; } foreach node p in Predecessors (n) { return; if(i%2 == 0) T = T ∩ Dominators[p] return; D = T ∪ n evenSum+=i; if ( D != Dominators[n] ) changed = true Dominators[n] = D i++; until (!changed) 2
4/3/2013 Dominators Strict & Immediate Dominance a strictly dominates b if The root dominates itself. 1. a dom b and long evenSum=0; 1 Dom(1) = {1} int i=0; 2. a ≠ b . Dom(2) = {1, 2} For a ≠ b , a immediately dominates b if and only if: 2 while(i<1000000) Dom(3) = {1, 2, 3} 1. a dom b , and 2. there does not exist a node c such that: Dom(4) = {1, 2, 3, 4} a. c ≠ a and c ≠ b 6 return; 3 if(i%2 == 0) Not all paths to 5 go through 4, so: b. a dom c and c dom b. Dom(5) = {1, 2, 3, 5} 4 evenSum+=i; Thus, a idom b means that the closest dominator of b to the root (travelling Dom(6) = {1, 2, 6} backwards from b along the reverse control flow edges) is a. 5 i++; The immediate dominator of a node is unique. Immediate Dominator Algorithm Dominators temp = {} Input: long evenSum=0; 1 N = set of nodes in CFG idom(1) = {} int i=0; foreach node n ∈ N Dominators[x] = Dominators temp[n] = Dominators[n] - {n} idom(2) = {1} of x 2 while(i<1000000) r = root of CFG foreach node n ∈ (N - {r}) idom(3) = {2} foreach node s ∈ temp[n] 6 return; 3 if(i%2 == 0) Output: foreach node t ∈ (temp[n] - {s}) idom(4) = {3} if (t ∈ temp[s]) { Immediate dominator for each 4 evenSum+=i; temp[n] -= {t} CFG node idom(5) = {3} 5 i++; idom(6) = {2} foreach node n ∈ (N - {r}) idom[n] = temp[n] Dom(1) = {1} Dom(2) = {1, 2} Dom(3) = {1, 2, 3} Dom(4) = {1, 2, 3, 4} Dom(5) = {1, 2, 3, 5} Dom(6) = {1, 2, 6} Dominator Tree Dominance Frontier The immediate dominance relation forms a tree of the nodes of a flowgraph where: The dominance frontier of a node a is the set of all nodes s such that a 1. The root is the entry node, dominates a predecessor of s , but does not strictly dominate s . 2. The edges are immediate dominances, and 3. The paths display all of the dominance relationships. It is the “border” between dominated and undominated nodes. 1 idom(1) = {} 1 long evenSum=0; 1 int i=0; idom(2) = {1} Node 5 dominates the idom(3) = {2} 2 2 5 9 shaded nodes. idom(4) = {3} 2 while(i<1000000) idom(5) = {3} idom(6) = {2} 6 3 The dominance frontier is 6 return; 3 if(i%2 == 0) those nodes who are not 3 6 7 10 11 strictly dominated by 5. 4 5 4 evenSum+=i; DF[5] = {4, 5, 12, 13} 4 8 12 5 i++; 13 3
4/3/2013 Dominance Frontier Dominance Frontier Criterion A definition in node n forces a φ -function at join points that lie just outside Whenever node x contains a definition of some variable a , then any node z in the dominance frontier of x needs a φ -function for a . the region of the CFG that n dominates. Since a φ -function itself is a definition, we must iterate the dominance-frontier A definition in node n forces a corresponding φ -function at any join point m where: criterion until there are no nodes that need φ -functions. 1. n dominates a predecessor of m ( q ∈ preds ( m ) and n ∈ Dom( q )), and 2. n does not strictly dominate m . The iterated dominance frontier criterion and the iterated path convergence criterion specify exactly the same set of nodes at which to put φ -functions. (Using strict dominance rather than dominance allows a φ -function at the start of a single-block loop. In that case, n = m , and m ∉ Dom( n ) – { n }.) We call the collection of nodes m that have this property with respect to n the dominance frontier of n , denoted DF( n ). Computing the Dominance Frontier Dominance Frontier Alternative Algorithm: Block n=1: Has No Predecessors long evenSum=0; 1 DF(1) = {} int i=0; foreach node n in the CFG Block n=2: Has multiple predecessors (1,5) DF(n) = {} 2 while(i<1000000) Runner = 1 IDom(2) = 1 # Done with 1 foreach node n in the CFG 6 return; 3 if(i%2 == 0) if ( n has multiple predecessors) Runner = 5 foreach predecessor p of n 4 evenSum+=i; IDom(2) = 1 runner = p DF(5) = {} + {2} = {2} 5 while (runner ≠ IDom(n)) i++; Runner = IDom(Runner) = 3 DF(runner) = DF(runner) ∪ {n} DF(3) = {} + {2} = {2} 1 runner = IDom(runner) Runner = IDom(Runner) = 2 DF(2) = {} + {2} = {2} 2 Runner = IDom(Runner) = 1 # Done 6 3 4 5 Dominance Frontier Inserting φ -Functions Starting with a program not in SSA form, we need to insert just enough φ -functions Block n=3: Has 1 predecessor long evenSum=0; DF(1)={} 1 DF(3) = {2} to satisfy the iterated dominance frontier criterion. int i=0; Block n=4: Has 1 predecessor 2 while(i<1000000) DF(2)={2} Start with a set V of variables, a graph G of control-flow nodes, and for each node DF(4) = {} n a set A orig [ n ] of variables defined in node n . 6 3 DF(3)={2} return; if(i%2 == 0) Block n=5: Has 2 predecessors (3,4) DF(6)={} Compute A φ [ a ], the set of nodes that must have φ -functions for variable a . Runner = 3 4 evenSum+=i; DF(4)={5} IDom(5) = 3 # Done with 3 Use a work list W of nodes that might violate the dominance-frontier criterion. 5 i++; DF(5)={2} Runner = 4 IDom(5) = 3 1 DF(4) = {} + {5} Runner = IDom(Runner) = 3 2 IDom(5) = 3 # Done with 4 6 3 Block n=6: Has 1 predecessor DF(6) = {} 4 5 4
Recommend
More recommend