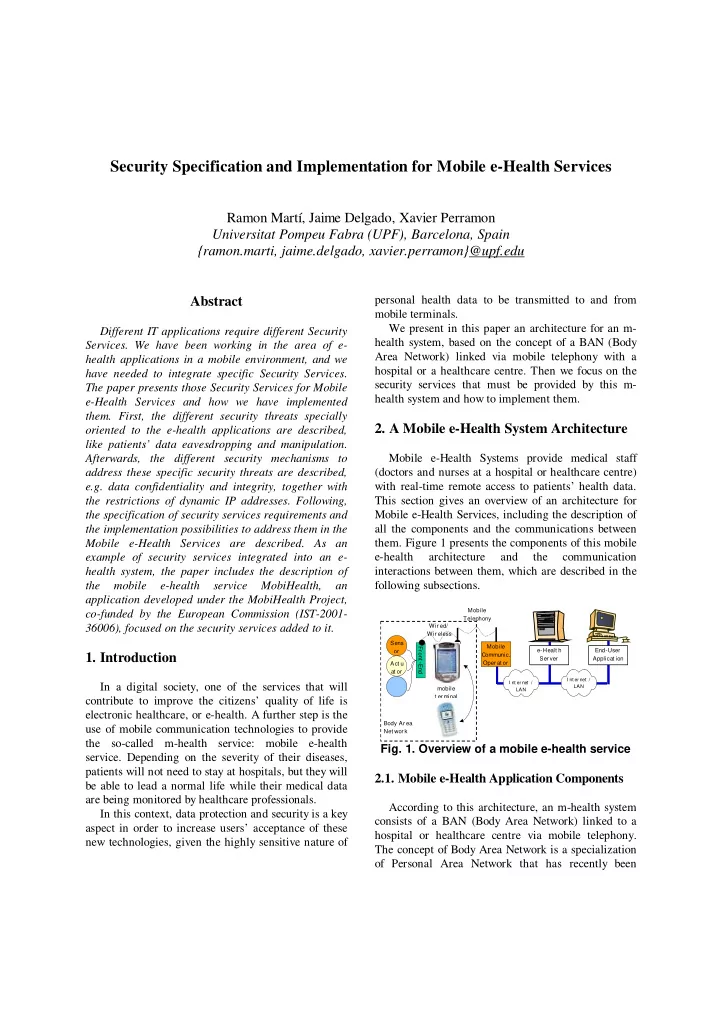

Security Specification and Implementation for Mobile e-Health Services Ramon Martí, Jaime Delgado, Xavier Perramon Universitat Pompeu Fabra (UPF), Barcelona, Spain {ramon.marti, jaime.delgado, xavier.perramon}@upf.edu personal health data to be transmitted to and from Abstract mobile terminals. We present in this paper an architecture for an m- Different IT applications require different Security health system, based on the concept of a BAN (Body Services. We have been working in the area of e- Area Network) linked via mobile telephony with a health applications in a mobile environment, and we hospital or a healthcare centre. Then we focus on the have needed to integrate specific Security Services. security services that must be provided by this m- The paper presents those Security Services for Mobile health system and how to implement them. e-Health Services and how we have implemented them. First, the different security threats specially 2. A Mobile e-Health System Architecture oriented to the e-health applications are described, like patients’ data eavesdropping and manipulation. Mobile e-Health Systems provide medical staff Afterwards, the different security mechanisms to (doctors and nurses at a hospital or healthcare centre) address these specific security threats are described, with real-time remote access to patients’ health data. e.g. data confidentiality and integrity, together with This section gives an overview of an architecture for the restrictions of dynamic IP addresses. Following, Mobile e-Health Services, including the description of the specification of security services requirements and all the components and the communications between the implementation possibilities to address them in the them. Figure 1 presents the components of this mobile Mobile e-Health Services are described. As an e-health architecture and the communication example of security services integrated into an e- interactions between them, which are described in the health system, the paper includes the description of following subsections. the mobile e-health service MobiHealth, an application developed under the MobiHealth Project, Mobile co-funded by the European Commission (IST-2001- Telephony 36006), focused on the security services added to it. Wir ed/ Wir eless Sens Mobile Fr ont -End e-Healt h End-User or 1. Introduction Communic. Ser ver Applicat ion Oper at or Act u at or I nt ernet / I nt ernet / In a digital society, one of the services that will LAN mobile LAN t er minal contribute to improve the citizens’ quality of life is electronic healthcare, or e-health. A further step is the Body Ar ea use of mobile communication technologies to provide Net wor k the so-called m-health service: mobile e-health Fig. 1. Overview of a mobile e-health service service. Depending on the severity of their diseases, patients will not need to stay at hospitals, but they will 2.1. Mobile e-Health Application Components be able to lead a normal life while their medical data are being monitored by healthcare professionals. According to this architecture, an m-health system In this context, data protection and security is a key consists of a BAN (Body Area Network) linked to a aspect in order to increase users’ acceptance of these hospital or healthcare centre via mobile telephony. new technologies, given the highly sensitive nature of The concept of Body Area Network is a specialization of Personal Area Network that has recently been
introduced in the literature [1][2][3]. For our the e-HS stored information, both from inside or purposes, the BAN is a network of sensors (e.g. a outside the Hospital. pulse meter or a glucose meter) and/or actuators (e.g. an insulin pump) attached to the patient’s body, and 2.2. Mobile e-Health Application interconnected in a star topology to a hub or Communication concentrator, where all data are collected. This interconnection can be through wires, but also through Different communication interactions exist in a short-range wireless techniques, such as IEEE mobile e-health service. These communications can be 802.15.1/Bluetooth or the more recently developed done in two ways: from the BAN to the End-User IEEE 802.15.4/ZigBee [4]. The hub is a device Application, but also from the End-User Application directly connected to a mobile communications to the BAN. The following hop-to-hop interactions are terminal, typically a cellular phone, through which considered: data can be transmitted virtually anywhere using - Sensor ↔ Front-End: Wired communication, or Internet protocols, and in particular to the hospital or wireless e.g. Bluetooth. healthcare centre where the patient is being - Actuator ↔ Front-End: Wired communication, or monitored. wireless e.g. Bluetooth. In this architecture, a mobile e-health service is ↔ - Front-End Mobile terminal: Wired composed of the following components: communication, or wireless e.g. Bluetooth. - Sensor: A device, such as a photoelectric cell, that - Mobile terminal ↔ Network Operator: TCP/IP receives and responds to a signal or stimulus. Sensors communication through mobile telephony. in the BAN can measure pulse, blood pressure, oxygen - Network Operator ↔ e-Health Server: TCP/IP level, glucose level, etc. communication. This communication is through local - Actuator: A device responsible for actuating a LAN, when the e-HS is in the same location as the mechanical device, such as one connected to a Network Operator, or through Internet when it is in a computer by a sensor link. In an e-health system, an different location. actuator can be an insulin pump for patients with - e-Health Server ↔ End-User Application: Remote diabetes. access of the client to the e-HS data. The access is - Front-End: Hub for all the sensors and actuators through application layer protocol and application in the BAN. It records all the data from all the sensors data, and the communication through TCP/IP in and actuators, and can send them to the mobile Internet or LAN. terminal. - Mobile terminal: A Mobile Phone or, The communication path between the Mobile alternatively, some device with mobile communication terminal and the e-Health Server is used to transport capabilities, e.g. a PDA. application data through application layer protocols. - Body Area Network (BAN): Patients network, composed of Sensors, Actuators, a Front-End and a 3. Security Threats in e-Health Mobile Mobile terminal. Personal Area Network Communications - Mobile communications Operator: Network operator with wireless telephony access to Internet. A mobile e-health service, like all information - e-Health Server (e-HS): Main server, where technology systems, is subject to different kinds of medical data is received and distributed. It can be security threats. We will not consider here threats of installed in the mobile communications service environmental origin (fire, etc.) or accidental ones provider, or at the Hospital. (user errors, software malfunction, etc.). The - End-User Application (EUA): Computers in the deliberate threats that we will consider can be Hospital (or Healthcare centre), used to access the categorized into 4 groups: information from the Sensors and Actuators and to - threats to confidentiality, send new configuration parameters to the BAN, - threats to integrity, through the access to the e-HS. It can be either a main - threats to authenticity (including non- server in the Hospital, that accesses the e-HS data and repudiation), stores them in the already existing patients database, - threats to system performance (availability, or authorized employees user computers, that access reliability and accountability).
Recommend
More recommend