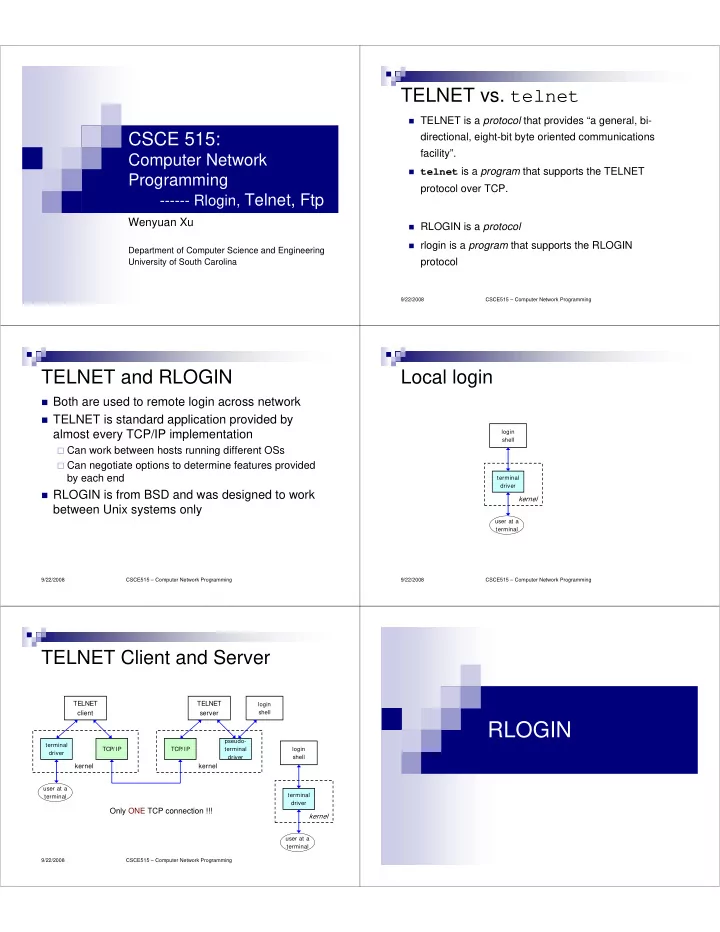

TELNET vs. telnet � TELNET is a protocol that provides “a general, bi- CSCE 515: directional, eight-bit byte oriented communications facility”. Computer Network � telnet is a program that supports the TELNET Programming protocol over TCP. ------ Rlogin, Telnet, Ftp Wenyuan Xu � RLOGIN is a protocol � rlogin is a program that supports the RLOGIN Department of Computer Science and Engineering protocol University of South Carolina 9/22/2008 CSCE515 – Computer Network Programming TELNET and RLOGIN Local login � Both are used to remote login across network � TELNET is standard application provided by almost every TCP/IP implementation login shell � Can work between hosts running different OSs � Can negotiate options to determine features provided by each end terminal driver � RLOGIN is from BSD and was designed to work kernel between Unix systems only user at a terminal 9/22/2008 CSCE515 – Computer Network Programming 9/22/2008 CSCE515 – Computer Network Programming TELNET Client and Server TELNET TELNET login client server shell RLOGIN pseudo- terminal TCP/IP TCP/IP terminal login driver driver shell kernel kernel user at a terminal terminal driver Only ONE TCP connection !!! kernel user at a terminal 9/22/2008 CSCE515 – Computer Network Programming
RLOGIN Protocol – Start up Interactive input � Specified in RFC 1282 Client Server � Use a single TCP connection � Protocol between client and server after connection is set up keystroke 1byte Date � Client writes 4 strings to server � a byte of 0 Server ACK = 1 WIN = xxx � login name of user on client, terminated by a byte of 0 � login name of user on server, terminated by a byte of 0 echo � name of user ’ s terminal type, a slash, terminal speed, terminated by a byte Date of 0 1byte display � (\0John\0John\0ibmpc3/9600\0) � Server responds with a byte of 0 ACK = 1 WIN = xxx � Optionally server can ask user for a password � Server sends a request to client asking for terminal ’ s window size 9/22/2008 CSCE515 – Computer Network Programming 9/22/2008 CSCE515 – Computer Network Programming Flow control Server to Client Commands � Need to mark command bytes because only one TCP connection is � Done by client used � Use TCP ’ s urgent mode to mark command bytes � User type Control-S, Control-Q, asking � To send a command to client, server enters urgent mode and makes SERVER to stop sending data, or start command byte the last byte of urgent data � Four command bytes sending data � 0x02: client flushes output � Control-S � stop writing to the network � 0x10: client stops performing flow control � 0x20: client resumes flow control � Control-Q � start writing to the network � 0x80: client sends current window size to server immediately and notifies server if changing window size � Out-of-band signaling � Control by Server 9/22/2008 CSCE515 – Computer Network Programming 9/22/2008 CSCE515 – Computer Network Programming TCP Segment Format Client to Server Command � When client receives command 0x80 from 0 15 16 31 server, client needs to send window size to source port number destination port number server sequence number � This command needs to be marked 20 bytes acknowledgment number � 2 bytes of 0xff U A P R S F header window size reserved R C S S Y I length � 2 flag bytes of ASCII char ‘ s ’ G K H T N N TCP checksum urgent pointer � 4 16-bit values: #rows, #chars per row, #pixels in X direction, #pixels in Y direction option (if any) � In-band signaling data (if any) 9/22/2008 CSCE515 – Computer Network Programming 9/22/2008 CSCE515 – Computer Network Programming
RLOGIN Client Escape � Talk to client directly instead of sending the input to server � Start with a tilde ‘ ~ ’ TELNET � Followed by one of four characters � ‘ . ’ : terminate client � EOF (Ctrl-D): terminate client � Job control suspend char (Ctrl-Z): suspend client � Job control delayed suspend char (Ctrl-Y): suspend only client input but keep server output 9/22/2008 CSCE515 – Computer Network Programming TELNET Protocol TELNET Client and Server � Specified in RFC 854 TELNET TELNET login client server shell � TCP connection � data and control over the same connection. pseudo- terminal TCP/IP TCP/IP terminal login driver driver shell � Network Virtual Terminal kernel kernel � Designed to work between any host and any user at a terminal terminal terminal driver Only ONE TCP connection !!! � Negotiated options kernel user at a terminal 9/22/2008 CSCE515 – Computer Network Programming 9/22/2008 CSCE515 – Computer Network Programming Network Virtual Terminal Network Virtual Terminal � intermediate representation of a generic terminal. � provides a standard language for communication of terminal control functions. Server Server � Client maps user ’ s terminal type to NVT Process Process � Server maps NVT into its terminal type � Use NVT ASCII, the 7-bit US variant of ASCII NVT NVT NVT NVT character set, but also allow 8-bit data TCP TCP transmission TCP TCP 9/22/2008 CSCE515 – Computer Network Programming 9/22/2008 CSCE515 – Computer Network Programming
Negotiated Options Negotiated Options � All NVTs support a minimal set of � The protocol for requesting optional capabilities. features is well defined and includes rules for eliminating possible negotiation “loops”. � Some terminals have more capabilities than the minimal set. � The set of options is not part of the TELNET protocol, so that new terminal � The 2 endpoints negotiate a set of features can be incorporated without mutually acceptable options (character set, changing the TELNET protocol. echo mode, etc). 9/22/2008 CSCE515 – Computer Network Programming 9/22/2008 CSCE515 – Computer Network Programming Option examples Command Structure � In-band signaling for both directions � Four operation modes � All TELNET commands and data flow through the � Half-duplex same TCP connection. � Character at a time � Commands start with a special character called � Line at a time the Interpret as Command (IAC) escape character. � Linemode � The IAC code is 255 (0xff). � Next byte is command byte � character set (EBCDIC vs. ASCII) � <IAC COMMAND XX > � If a 0xff is sent as data - it must be followed by another 0xff. 9/22/2008 CSCE515 – Computer Network Programming 9/22/2008 CSCE515 – Computer Network Programming Looking for Commands Command Codes � Each receiver must look at each byte that � IP 243 0xf3 arrives and look for IAC. � WILL WILL 251 0xfb 251 0xfb � AO 244 0xf4 � � WON WON’ ’T T 252 252 0xfc 0xfc � � AYT 245 0xf5 � If IAC is found and the next byte is IAC - a � DO DO 253 0xfd 0xfd � 253 � EC 246 0xf6 single byte is presented to the � DON DON’ ’T T 254 254 0xfe 0xfe application/terminal (a 0xff). � EL 247 0xf7 � � IAC IAC 255 0xff 255 0xff � � If IAC is followed by any other code - the TELNET layer interprets this as a command. 9/22/2008 CSCE515 – Computer Network Programming 9/22/2008 CSCE515 – Computer Network Programming
TELNET Option Negotiation TELNET Options � Either side can send request to other side Option ID Name � <IAC COMMANDID OPTIONID > 1 echo 3 suppress go ahead � Four different requests for any given option 5 status � WILL: sender wants to enable option 6 timing mark � DO: receiver says OK 24 terminal type � DONT: receiver says NO 31 window size � DO: sender wants receiver to enable option 32 terminal speed � WILL: receiver says OK 33 remote flow control � WONT: NO 34 linemode � WONT: sender wants to disable option 36 environment variables � DONT: receiver must say OK � DONT: sender wants receiver to disable option � WONT receiver must say OK 9/22/2008 CSCE515 – Computer Network Programming 9/22/2008 CSCE515 – Computer Network Programming TELNET Suboption Negotiation Control Functions � Used for options that require more information � TELNET includes support for a series of than just “ enable ” or “ disable ” control functions commonly supported by � For example, servers. client: <IAC, WILL, 24> server: <IAC, DO, 24> � This provides a uniform mechanism for server: <IAC, SB, 24, 1, IAC, SE> communication of (the supported) control client: <IAC, SB, 24, 0, ‘ I ’ , ‘ B ’ , ‘ M ’ , ‘ P ’ , ‘ C ’ , IAC, SE> functions. 9/22/2008 CSCE515 – Computer Network Programming 9/22/2008 CSCE515 – Computer Network Programming Control Functions More Control Functions � Interrupt Process (IP) � Erase Character (EC) � suspend/abort process. � delete last character sent � Abort Output (AO) � typically used to edit keyboard input. � process can complete, but send no more output to user’s terminal. � Erase Line (EL) � Are You There (AYT) � delete all input in current line. � check to see if system is still running. 9/22/2008 CSCE515 – Computer Network Programming 9/22/2008 CSCE515 – Computer Network Programming
Recommend
More recommend