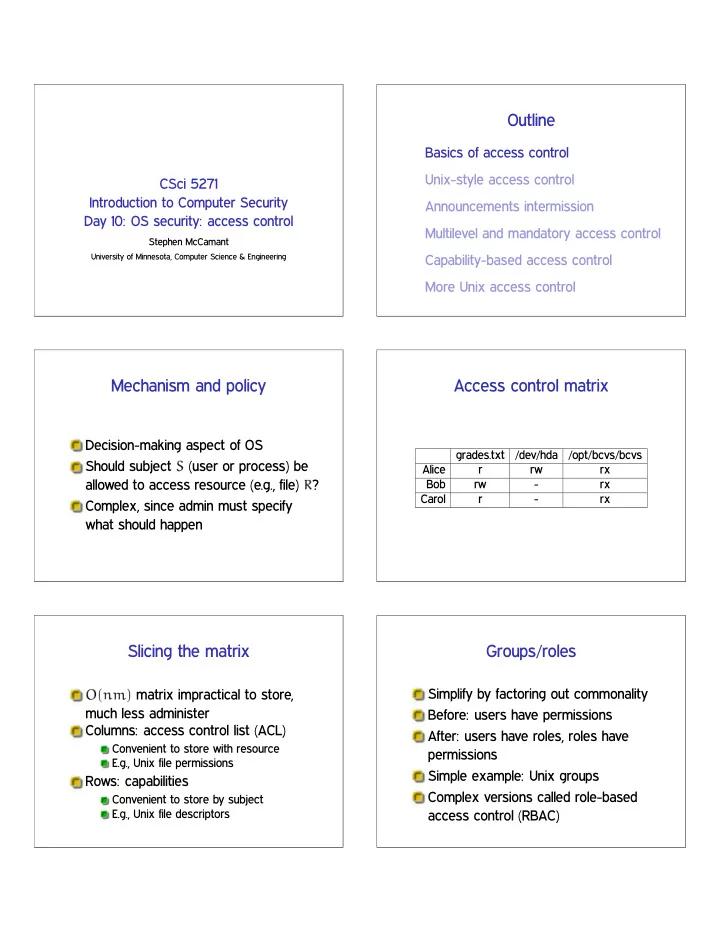

Outline Basics of access control Unix-style access control CSci 5271 Introduction to Computer Security Announcements intermission Day 10: OS security: access control Multilevel and mandatory access control Stephen McCamant University of Minnesota, Computer Science & Engineering Capability-based access control More Unix access control Mechanism and policy Access control matrix Decision-making aspect of OS grades.txt /dev/hda /opt/bcvs/bcvs Should subject ❙ (user or process) be Alice r rw rx allowed to access resource (e.g., file) ❘ ? Bob rw - rx Carol r - rx Complex, since admin must specify what should happen Slicing the matrix Groups/roles Simplify by factoring out commonality ❖ ✭ ♥♠ ✮ matrix impractical to store, much less administer Before: users have permissions Columns: access control list (ACL) After: users have roles, roles have Convenient to store with resource permissions E.g., Unix file permissions Simple example: Unix groups Rows: capabilities Complex versions called role-based Convenient to store by subject E.g., Unix file descriptors access control (RBAC)
Outline UIDs and GIDs Basics of access control To kernel, users and groups are just Unix-style access control numeric identifiers Names are a user-space nicety Announcements intermission E.g., ✴❡t❝✴♣❛ss✇❞ mapping Multilevel and mandatory access control Historically 16-bit, now 32 Capability-based access control User 0 is the special superuser r♦♦t Exempt from all access control checks More Unix access control File mode bits Interpretation of mode bits File also has one user and group ID Core permissions are 9 bits, three Choose one set of bits groups of three If users match, use user bits Read, write, execute for user, group, If subject is in the group, use group bits other Otherwise, use other bits ❧s format: r✇① r✲① r✲✲ Note no fallback, so can stop yourself or have negative groups Octal format: 0754 But usually, ❖ ✒ ● ✒ ❯ Directory mode bits Process UIDs and s❡t✉✐❞✭✷✮ Same bits, slightly different UID is inherited by child processes, and interpretation an unprivileged process can’t change it Read: list contents (e.g., ❧s ) But there are syscalls root can use to Write: add or delete files change the UID, starting with s❡t✉✐❞ Execute: traverse E.g., login program, SSH server X but not R means: have to know the names
Setuid programs, different UIDs More different UIDs Two mechanisms for temporary If 04000 “setuid” bit set, newly exec’d switching: process will take UID of its file owner Swap real UID and effective UID (BSD) Remember saved UID , allow switching to Other side conditions, like process not it (System V) traced Specifically the effective UID is changed, Modern systems support both while the real UID is unchanged mechanisms at the same time Shows who called you, allows switching Linux only: file-system UID back Once used for NFS servers, now mostly obsolete Setgid, games Other permission rules Only file owner or root can change Setgid bit 02000 mostly analogous to permissions setuid Only root can change file owner But note no supergroup, so UID 0 is still Former System V behavior: “give away special ❝❤♦✇♥ ” Classic application: setgid ❣❛♠❡s for Setuid/gid bits cleared on ❝❤♦✇♥ managing high-score files Set owner first, then enable setuid Non-checks Outline Basics of access control File permissions on st❛t Unix-style access control File permissions on link, unlink, rename Announcements intermission File permissions on read, write Parent directory permissions generally Multilevel and mandatory access control Except traversal Capability-based access control I.e., permissions not automatically recursive More Unix access control
Deadlines reminder Outline Basics of access control Exercise set 1: returned before midterm Unix-style access control Homework 1: today is last day for late Announcements intermission submission Exercise set 2: Thursday night Multilevel and mandatory access control Ask HW1 and Ex.2 questions before Capability-based access control midterm More Unix access control MAC vs. DAC Motivation: it’s classified Discretionary access control (DAC) Government defense and intelligence Users mostly decide permissions on their agencies user classification to restrict own files access to information If you have information, you can pass it on to anyone E.g.: Unclassified, Confidential, Secret, E.g., traditional Unix file permissions Top Secret Mandatory access control (MAC) Multilevel Secure (MLS) systems first Restrictions enforced regardless of developed to support mixing subject choices classification levels under timesharing Typically specified by an administrator Motivation: system integrity Bell-LaPadula, linear case State-machine-like model developed for Limit damage if a network server US DoD in 1970s application is compromised 1. A subject at one level may not read a Unix DAC is no help if server is root resource at a higher level Limit damage from Simple security property, “no read up” browser-downloaded malware 2. A subject at one level may not write a Windows DAC is no help if browser is resource at a lower level “administrator” user * property, “no write down”
High watermark property Biba and low watermark Inverting a confidentiality policy gives Dynamic implementation of BLP an integrity one Process has security level equal to Biba: no write up, no read down highest file read Low watermark policy Written files inherit this level BLP ❫ Biba ✮ levels are isolated Information-flow perspective Covert channels Problem: conspiring parties can misuse Confidentiality: secret data should not other mechanisms to transmit flow to public sinks information Integrity: untrusted data should not flow Storage channel: writable shared state to critical sinks E.g., screen brightness on mobile phone Timing channel: speed or ordering of Watermark policies are process-level events conservative abstractions E.g., deliberately consume CPU time Multilateral security / compartments Partial orders and lattices ✔ on integers is a total order In classification, want finer divisions Reflexive, antisymmetric, transitive, ❛ ✔ ❜ based on need-to-know or ❜ ✔ ❛ Also, selected wider sharing (e.g., with Dropping last gives a partial order allied nations) A lattice is a partial order plus Many other applications also have this operators for: character Least upper bound or join t Anderson’s example: medical data Greatest lower bound or meet ✉ How to adapt BLP-style MAC? Example: subsets with ✒ , ❬ , ❭
Subset lattice example Subset lattice example Lattice model Classification lattice example Generalize MLS levels to elements in a lattice BLP and Biba work analogously with lattice ordering No access to incomparable levels Potential problem: combinatorial explosion of compartments Lattice BLP example MLS operating systems 1970s timesharing, including Multics “Trusted” versions of commercial Unix (e.g. Solaris) SELinux (called “type enforcement”) Integrity protections in Windows Vista and later
Multi-VM systems Air gaps, pumps, and diodes The lack of a connection between One (e.g., Windows) VM for each networks of different levels is called an security level air gap More trustworthy OS underneath A pump transfers data securely from provides limited interaction one network to another E.g., NSA NetTop: VMWare on SELinux A data diode allows information flow in Downside: administrative overhead only one direction Chelsea Manning cables leak Outline Manning (n´ ee Bradley) was an Basics of access control intelligence analyst deployed to Iraq Unix-style access control PC in a T-SCIF connected to SIPRNet Announcements intermission (Secret), air gapped CD-RWs used for backup and software Multilevel and mandatory access control transfer Capability-based access control Contrary to policy: taking such a CD-RW home in your pocket More Unix access control ❤tt♣✿✴✴✇✇✇✳❢❛s✳♦r❣✴s❣♣✴❥✉❞✴♠❛♥♥✐♥❣✴✵✷✷✽✶✸✲st❛t❡♠❡♥t✳♣❞❢ ACLs: no fine-grained subjects ACLs: ambient authority Subjects are a list of usernames All authority exists by virtue of identity maintained by a sysadmin Kernel automatically applies all available Unusual to have a separate subject for authority an application Authority applied incorrectly leads to Cannot easily subset access (sandbox) attacks
Recommend
More recommend