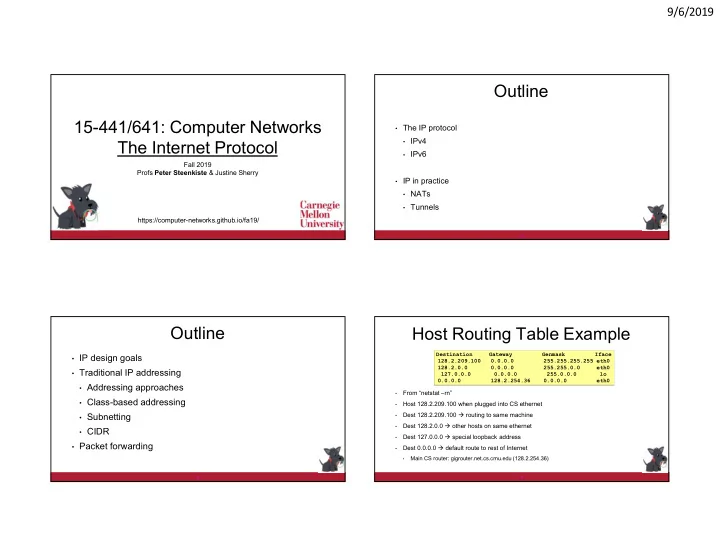

9/6/2019 Outline 15-441/641: Computer Networks • The IP protocol • IPv4 The Internet Protocol • IPv6 Fall 2019 Profs Peter Steenkiste & Justine Sherry • IP in practice • NATs • Tunnels https://computer-networks.github.io/fa19/ 2 Outline Host Routing Table Example Destination Gateway Genmask Iface • IP design goals 128.2.209.100 0.0.0.0 255.255.255.255 eth0 128.2.0.0 0.0.0.0 255.255.0.0 eth0 • Traditional IP addressing 127.0.0.0 0.0.0.0 255.0.0.0 lo 0.0.0.0 128.2.254.36 0.0.0.0 eth0 • Addressing approaches From “netstat –rn” • • Class-based addressing Host 128.2.209.100 when plugged into CS ethernet • • Subnetting Dest 128.2.209.100 routing to same machine • Dest 128.2.0.0 other hosts on same ethernet • • CIDR Dest 127.0.0.0 special loopback address • • Packet forwarding Dest 0.0.0.0 default route to rest of Internet • Main CS router: gigrouter.net.cs.cmu.edu (128.2.254.36) • 3 4 1
9/6/2019 Routing Within the Subnet Routing to the Network • Five subnets (yellow) Each router port has •Packet to 10.1.1.3 10.1.1.2 10.1.1.3 10.1.1.2 10.1.1.3 an IP address: 10.1.8/24 1. 5 5 H1 H2 H1 H2 •Matches 10.1.0.0/23 10.1.1.4 10.1.2/23 10.1.1.4 2. 10.1.1/24 10.1.1/24 4 4 10.1.0.2 Routing table at R2 10.1.0.2 10.1.0/24 3. 10.1.0.1 10.1.0.1 10.1.1.1 R1 H3 10.1.1.1 R1 H3 10.1.2.2 10.1.2.2 10.1.0/24 Destination Next Hop Egress Port 4. 10.1.0/24 10.1.0/24 3 2 3 2 127.0.0.1 - lo0 10.1.2/23 10.1.2/23 10.1.1.3/31 5. Default or 0/0 provider 10.1.16.1 10.1/16 10.1.8/24 10.1.8/24 1 Provider R2 R2 1 1 10.1.8.0/24 - 10.1.8.1 • Packet to 10.1.1.3 arrives from Internet 10.1/16 10.1.8.1 10.1.8.1 2 10.1.2.0/23 - 10.1.2.1 10.1.2.1 H4 10.1.2.1 H4 10.1.16.1 • Path is R2 – R1 – H1 – H2 10.1.16.1 3 4 5 10.1.0.0/23 10.1.2.2 10.1.2.1 10.1.8.4 10.1.8.4 • H1 serves as a router for the 10.1.1.2/31 network (2 IP addresses) 5 6 Routing Within the Subnet Routing Within the Subnet •Packet to 10.1.1.3 •Packet to 10.1.1.3 10.1.1.2 10.1.1.3 10.1.1.2 10.1.1.3 •Matches 10.1.1.2/31 5 5 H1 H2 H1 H2 •Direct route 10.1.1.4 10.1.1.4 10.1.1/24 10.1.1/24 •Longest prefix match 4 4 •Longest prefix match 10.1.0.2 10.1.0.2 10.1.0.1 10.1.0.1 10.1.1.1 R1 H3 10.1.1.1 R1 H3 Routing table at R1 10.1.2.2 10.1.2.2 Routing table at H1 10.1.0/24 10.1.0/24 Destination Next Hop Egress Port 3 3 2 2 10.1.2/23, 10.1.2/23 Destination Next Hop Egress Port 127.0.0.1 - lo0 10.1/16 127.0.0.1 - lo0 10.1/16 10.1.8/24 10.1.8/24 R2 1 R2 1 Default or 0/0 10.1.2.1 10.1.2.2 1 1 2 3 Default or 0/0 10.1.1.1 10.1.1.4 10.1.8.1 2 10.1.2.0/23 - 10.1.2.2 10.1.8.1 10.1.2.1 10.1.2.1 4 10.1.1.0/24 - 10.1.1.2 H4 H4 10.1.16.1 3 10.1.0.0/24 - 10.1.0.1 10.1.16.1 10.1.8.4 5 10.1.1.2/31 - 10.1.1.2 10.1.8.4 4 10.1.1.0/24 - 10.1.1.1 5 10.1.1.2/31 10.1.1.4 10.1.1.1 7 8 2
9/6/2019 Important Concepts IP Addresses: How to Get One? • How does an ISP get block of addresses? • From Regional Internet Registries (RIRs) • Hierarchical addressing critical for scalable system ARIN (North America, Southern Africa), APNIC (Asia-Pacific), RIPE (Europe, • Northern Africa), LACNIC (South America) • Don’t require everyone to know everyone else • How about a single host? • Reduces number of updates when something changes • Assigned by sys admin (static or dynamic) • Classless inter-domain routing supports more efficient use of address • DHCP: Dynamic Host Configuration Protocol: dynamically get address: “plug- space and-play” • Adds complexity to routing, forwarding, … Host broadcasts “DHCP discover” msg • • But it is Scalable! DHCP server responds with “DHCP offer” msg • Host requests IP address: “DHCP request” msg • DHCP server sends address: “DHCP ack” msg • 9 10 IP Address Availability Remains IP Service Model a Major Challenge IPv4 Packet Format • Low-level communication model provided by 0 4 8 12 16 19 24 28 31 • Some are in big trouble! version HLen TOS Length Internet • APNIC: Asia Identifier Flag Offset • Datagram: each packet is • AFRINIC: Africa TTL Protocol Checksum self-contained Source Address • ARIN: North America • All information needed to get Destination Address • LACNIC: Latin America to destination Options (if any) • RIPE NCC: Europe, Middle • No advance setup or Data East, parts of central Asia connection maintenance • Analogous to letter or telegram 12 11 3
9/6/2019 IP Delivery Model Designing the IP header • Best effort service • Think of the IP header as an interface • Network will do its best to get packet to destination • Between the source and destination IP modules on end-systems • Does NOT guarantee: • Between the source and network (routers) • Any maximum latency or even ultimate success • Contains the information routers need to forward a packet • Informing the sender if packet does not make it • Delivery of packets in same order as they were sent • Designing an interface • Just one copy of packet will arrive • What task(s) are we trying to accomplish? • Implications • What information is needed to do it? • Scales very well (really, it does) • Higher level protocols must make up for shortcomings, e.g., TCP • Header reflects information needed for basic tasks • Some services not feasible (or hard), e.g., l atency or bandwidth guarantees 13 5 What information do we need? What are these tasks? (in network) • Parse packet • Parse packet • Carry packet to the destination • IP version number (4 bits), packet length (16 bits) • Deal with problems along the way • Carry packet to the destination • Routing loops • Destination’s IP address (32 bits) • Corruption • Deal with problems along the way • Packet too large • Loops: • Accommodate evolution • Corruption: • Specify any special handling • Packet too large: 6 8 4
9/6/2019 What information do we need? Preventing Loops (TTL) • Forwarding loops cause packets to cycle for a very looong time • Parse packet • Would accumulate to consume all capacity if left unchecked • IP version number (4 bits), packet length (16 bits) • Carry packet to the destination • Destination’s IP address (32 bits) • Deal with problems along the way • Loops: TTL (8 bits) • Time-to-Live (TTL) Field (8 bits) • Corruption: checksum (16 bits) • Decremented at each hop, packet discarded if reaches 0 • Packet too large: fragmentation fields (32 bits) • … and “time exceeded” message is sent to the source 9 10 Header Corruption (Checksum) Fragmentation • Checksum (16 bits) • Every link has a “Maximum Transmission Unit” (MTU) • Particular form of checksum over packet header • Largest number of bits it can carry as one unit • If not correct, router discards packets • A router can split a packet into multiple “fragments” if the packet size exceeds the link’s MTU • So it doesn’t act on bogus information • Must reassemble to recover original packet • Checksum recalculated at every router • Why? • Will return to fragmentation shortly… 11 12 5
9/6/2019 What information do we need? Special handling • Parse packet • IP version number (4 bits), packet length (16 bits) • “Type of Service” (8 bits) • Carry packet to the destination • Destination’s IP address (32 bits) • allow packets to be treated differently based on needs • Deal with problems along the way • e.g., indicate priority, congestion notification • TTL (8 bits) , checksum (16 bits), fragmentation (32 bits) • has been redefined several times • Accommodate evolution • Now called “Differentiated Services Code Point (DSCP)” • Version number (4 bits) (+ fields for special handling) • Specify any special handling 13 122 IP Router Implementation: Options Fast Path versus Slow Path • Optional directives to the network • Common case: Switched in silicon (“fast path”) • Not used very often Almost everything • • 16 bits of metadata + option-specific data • Weird cases: Handed to a CPU (“slow path”, or “process switched”) • Examples of options Fragmentation • • Record Route Bottom Line: TTL expiration (traceroute) • Not Used! • Strict Source Route IP option handling • • Slow path is evil in today’s environment • Loose Source Route “Christmas Tree” attack sets weird IP options, bits, and overloads router • • Timestamp Developers cannot (really) use things on the slow path • • Various experimental options Slows down their traffic – not good for business • • … If it became popular, they are in trouble! • 16 24 6
Recommend
More recommend