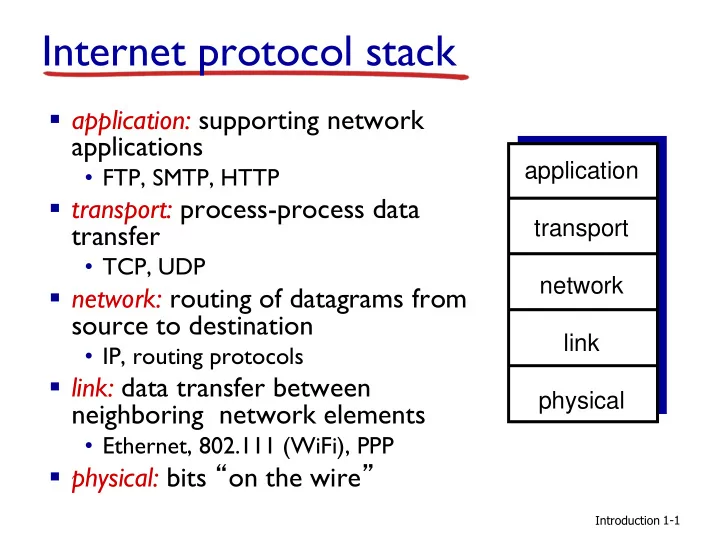

Internet protocol stack ▪ application: supporting network applications application • FTP, SMTP, HTTP ▪ transport: process-process data transfer transport • TCP, UDP network ▪ network: routing of datagrams from source to destination link • IP, routing protocols ▪ link: data transfer between physical neighboring network elements • Ethernet, 802.111 (WiFi), PPP ▪ physical: bits “ on the wire ” Introduction 1-1
Encapsulation source message M application segment transport H t H t M network datagram H n H n H t M link frame H l H n H t M physical link physical switch destination network H n H t M link H l H n H t M M application H n H t M physical transport H t M network H n H t M router link H l H n H t M physical Introduction 1-2
What ’ s the Internet: “ nuts and bolts ” view ▪ billions of connected PC mobile network computing devices: server • hosts = end systems global ISP wireless laptop • running network apps smartphone home ▪ communication links network regional ISP • fiber, copper, radio, wireless satellite links • transmission rate: wired links bandwidth ▪ packet switches: forward packets (chunks of data) router institutional • routers and switches network Introduction 1-3
Four sources of packet delay (1 of 2) transmission A propagation B nodal queueing processing d nodal = d proc + d queue + d trans + d prop d proc : nodal processing d queue : queueing delay ▪ check bit errors ▪ time waiting at output link for transmission ▪ determine output link ▪ depends on congestion ▪ typically < msec level of router Introduction 1-4
Four sources of packet delay (2 of 2) transmission A propagation B nodal queueing processing d nodal = d proc + d queue + d trans + d prop d trans : transmission delay: d prop : propagation delay: ▪ L : packet length (bits) ▪ d : length of physical link ▪ s : propagation speed (~2x10 8 m/sec) ▪ R : link bandwidth (bps) ▪ d trans = L/R ▪ d prop = d / s d trans and d prop very different * Check out the online interactive exercises for more examples: h ttp://gaia.cs.umass.edu/kurose_ross/interactive/ * Check out the Java applet for an interactive animation on trans vs. prop delay Introduction 1-5
Sockets ▪ process sends/receives messages to/from its socket ▪ socket analogous to door • sending process shoves message out door • sending process relies on transport infrastructure on other side of door to deliver message to socket at receiving process application application socket controlled by process process app developer transport transport network controlled network by OS link link Internet physical physical Application Layer 2-6
Internet transport protocols services TCP service: UDP service: ▪ reliable transport between ▪ unreliable data transfer sending and receiving between sending and process receiving process ▪ flow control: sender won ’ t ▪ does not provide: reliability, overwhelm receiver flow control, congestion ▪ congestion control: throttle control, timing, sender when network throughput guarantee, overloaded security, or connection setup, ▪ does not provide: timing, minimum throughput guarantee, security Q: why bother? Why is ▪ connection-oriented: setup there a UDP? required between client and server processes Application Layer 2-7
Chapter 2: summary our study of network apps now complete! ▪ application architectures ▪ specific protocols: • HTTP • client-server • SMTP, POP, IMAP • P2P • DNS ▪ application service requirements: • P2P: BitTorrent ▪ video streaming, CDNs • reliability, bandwidth, delay ▪ socket programming: ▪ Internet transport service model TCP , UDP sockets • connection-oriented, reliable: TCP • unreliable, datagrams: UDP Application Layer 2-8
Principles of reliable data transfer ▪ important in application, transport, link layers • top-10 list of important networking topics! ▪ characteristics of unreliable channel will determine complexity of reliable data transfer protocol (rdt) Transport Layer 3-9
TCP: Overview RFCs: 793,1122,1323, 2018, 2581 ▪ point-to-point: ▪ full duplex data: • one sender, one • bi-directional data flow receiver in same connection ▪ reliable, in-order byte • MSS: maximum segment size stream: ▪ connection-oriented: • no “ message boundaries ” • handshaking (exchange of control msgs) inits ▪ pipelined: sender, receiver state • TCP congestion and before data exchange flow control set window ▪ flow controlled: size • sender will not overwhelm receiver Transport Layer 3-10
TCP segment structure 32 bits URG: urgent data counting source port # dest port # (generally not used) by bytes sequence number of data ACK: ACK # (not segments!) acknowledgement number valid head not receive window U A P R S F PSH: push data now len used # bytes (generally not used) checksum Urg data pointer rcvr willing to accept RST, SYN, FIN: options (variable length) connection estab (setup, teardown commands) application data Internet (variable length) checksum (as in UDP) Transport Layer 3-11
TCP congestion control: additive increase multiplicative decrease ▪ approach: sender increases transmission rate (window size), probing for usable bandwidth, until loss occurs • additive increase: increase cwnd by 1 MSS every RTT until loss detected • multiplicative decrease : cut cwnd in half after loss additively increase window size … …. until loss occurs (then cut window in half) congestion window size cwnd: TCP sender AIMD saw tooth behavior: probing for bandwidth time Transport Layer 3-12
Recommend
More recommend