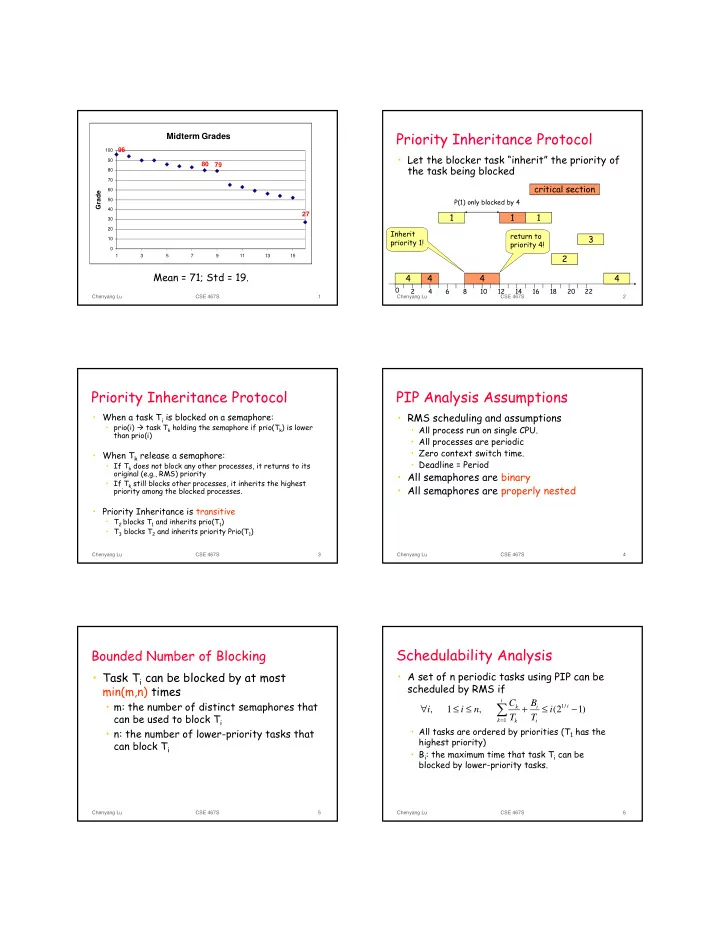

Priority Inheritance Protocol Midterm Grades 96 100 • Let the blocker task “inherit” the priority of 90 80 79 the task being blocked 80 70 critical section 60 Grade P(1) only blocked by 4 50 40 27 1 1 1 30 20 Inherit return to 3 10 priority 1! priority 4! 0 2 1 3 5 7 9 11 13 15 Mean = 71; Std = 19. 4 4 4 4 0 2 4 6 8 10 12 14 16 18 20 22 Chenyang Lu CSE 467S 1 Chenyang Lu CSE 467S 2 Priority Inheritance Protocol PIP Analysis Assumptions • RMS scheduling and assumptions • When a task T i is blocked on a semaphore: • prio(i) � task T k holding the semaphore if prio(T k ) is lower • All process run on single CPU. than prio(i) • All processes are periodic • Zero context switch time. • When T k release a semaphore: • Deadline = Period • If T k does not block any other processes, it returns to its original (e.g., RMS) priority • All semaphores are binary • If T k still blocks other processes, it inherits the highest • All semaphores are properly nested priority among the blocked processes. • Priority Inheritance is transitive • T 2 blocks T 1 and inherits prio(T 1 ) • T 3 blocks T 2 and inherits priority Prio(T 1 ) Chenyang Lu CSE 467S 3 Chenyang Lu CSE 467S 4 Schedulability Analysis Bounded Number of Blocking • Task T i can be blocked by at most • A set of n periodic tasks using PIP can be scheduled by RMS if min(m,n) times i • m: the number of distinct semaphores that ∑ C B ∀ ≤ ≤ + ≤ − k i 1 / i i , 1 i n , i ( 2 1 ) can be used to block T i T T = k 1 k i • All tasks are ordered by priorities (T 1 has the • n: the number of lower-priority tasks that highest priority) can block T i • B i : the maximum time that task T i can be blocked by lower-priority tasks. Chenyang Lu CSE 467S 5 Chenyang Lu CSE 467S 6
Compute B i Priority Ceiling /* potential blocking by other jobs */ • Priority ceiling C(S k ) of a semaphore S k B1=0; for each T j with priority lower than T i { • Highest priority among tasks requesting S k . b1 = longest critical section in T j that can block T i B1 = B1 + b1 • A critical region guarded by S k may lock } a task T i only if C(S k ) ≥ T i ’s priority /* potential blocking by semaphores */ B2=0; for each semaphore S k that can block T i { b2 = longest critical section guarded by S k in lower priority tasks B2 = B2 + b2 } Return min(B1, B2) Chenyang Lu CSE 467S 7 Chenyang Lu CSE 467S 8 Scheduling Review Priority Ceiling Protocol Assumptions RMS DMS EDF RMS/PIP • Priority ceiling of system: The highest priority ceiling among resources currently in use Single CPU √ √ √ √ • A task can acquire a resource only if Periodic • the resource is free, AND √ √ √ √ • it has a higher priority than the priority ceiling of the context switch system √ √ √ √ time = 0 • Improvements from PIP: Deadline = • Guarantees there is no deadlock X X √ √ Period • Each task is blocked for at most the duration of ONE critical section No blocking X √ √ √ • Downside: more run-time overhead than PIP Fixed Fixed Dynamic Optimality No Priority priority Priority Chenyang Lu CSE 467S 9 Chenyang Lu CSE 467S 10 Context-switching time Fixing scheduling problems • In practice, OS context switch • Change periods in requirements. overhead is small. • Reduce execution times of tasks. • Non-zero context switch time can push • Reduce blocking factors. limits of a tight schedule. • Get a faster CPU. • Leave margin in your schedule. • Multi-processor systems. • Techniques exist to reduce number of • Replace with software components with context switches. hardware (ASIC, FPGA) components Chenyang Lu CSE 467S 11 Chenyang Lu CSE 467S 12
Multi-processor system Distributed system • Tight coupling among processors • Loose coupling among processors • E.g., Dual-processor Sun workstations • Each processor has its own scheduler • Communicate through shared memory and on- • Costly to acquire states of other processors board buses • Broad range of systems • Scheduled by a common scheduler/OS • Processor boards mounted on a VME bus • Global scheduling • Automobile: hundreds of processors connected • Partitioned scheduling through a Control Area Network (CAN) • States of all processors available to each • Air traffic control system on a wide area network other Chenyang Lu CSE 467S 13 Chenyang Lu CSE 467S 14 End-to-End Task Model Notation • An (end-to-end) task is composed of multiple • T i = {T i,1 , T i,2 , … , T i,n(i) } subtasks running on multiple processors • n(i): the number of subtasks of T i • Message • Precedence constraint: Job J i,j cannot • Event be released until J i,j-1 is completed. • Remote method invocation • Subtasks are subject to precedence constraints • Task = a chain/tree/graph of subtasks Chenyang Lu CSE 467S 15 Chenyang Lu CSE 467S 16 End-to-End Deadline End-to-End Scheduling Framework • A task is subject to an end-to-end 1. Task allocation: bind tasks to processors deadline 2. Synchronization protocol: enforce precedence constraints • Does not care about the response time of a particular subtask 3. Subdeadline assignment 4. Schedulability analysis • How to guarantee end-to-end deadlines on a distributed system? Chenyang Lu CSE 467S 17 Chenyang Lu CSE 467S 18
Bin-packing formulation Task Allocation • Load code (e.g., objects) to processors • Pack subtasks to bins (processors) with limited capacity • Strategies • Size of a subtask T i,j : u i,j = e i,j /p i • Offline, static allocation • Capacity of each bin is its utilization bound • Allocate a task when it arrives • e.g., 0.69 (RMS) or 1 (EDF) under certain assumptions • Re-allocate (migrate) a task after it starts • Goal: minimize the number of bins subject to the capacity constraints • NP-hard: heuristics needed • Ignore communication cost • Assume every subtask is periodic Chenyang Lu CSE 467S 19 Chenyang Lu CSE 467S 20 Bin-Packing Heuristics: First- Fit Performance limit of First-Fit • Subtasks assigned in arbitrary order • Number of processors needed: m/m 0 -> 1.7 as m 0 -> ∞ • To allocate a new subtask T i,j • m: number of processors needed under First-Fit • If T i,j can be added to an existing processor P l • m 0 : minimum number of processors needed (1 ≤ l ≤ k) without exceeding its capacity, allocate T i,j to P k • First-Fit can always find a feasible allocation • Else add a new processor P k+1 and allocate T i,j to it. on m processors if total subtask utilization is no greater than m(2 1/2 -1) = 0.414m • Assuming fixed-priority scheduling, identical processors Chenyang Lu CSE 467S 21 Chenyang Lu CSE 467S 22
Recommend
More recommend