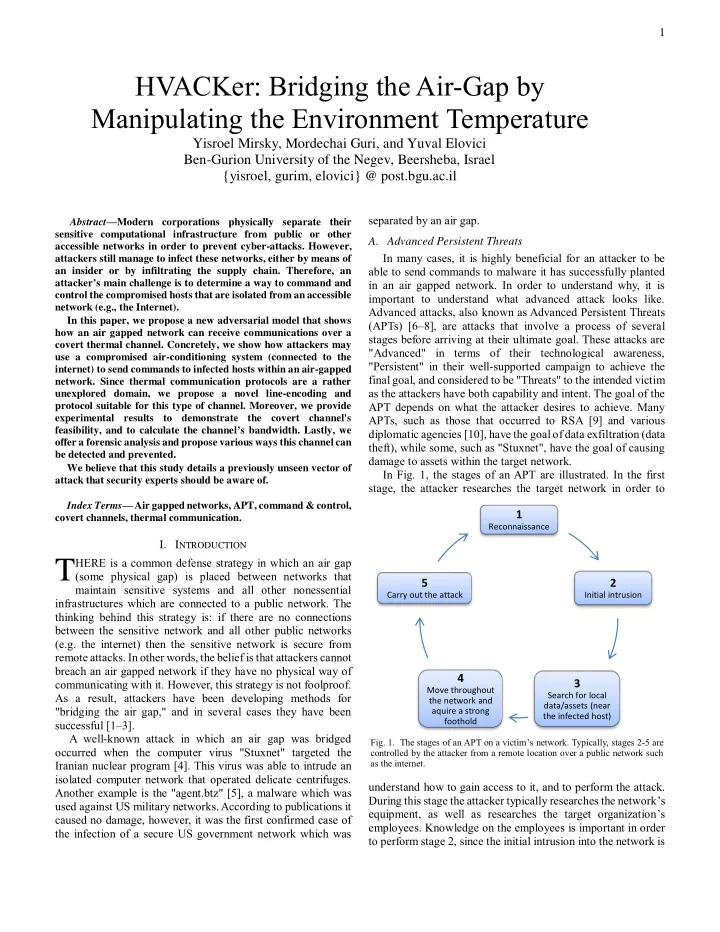

1 HVACKer: Bridging the Air-Gap by Manipulating the Environment Temperature Yisroel Mirsky, Mordechai Guri, and Yuval Elovici Ben-Gurion University of the Negev, Beersheba, Israel {yisroel, gurim, elovici} @ post.bgu.ac.il separated by an air gap. Abstract — Modern corporations physically separate their sensitive computational infrastructure from public or other A. Advanced Persistent Threats accessible networks in order to prevent cyber-attacks. However, In many cases, it is highly beneficial for an attacker to be attackers still manage to infect these networks, either by means of able to send commands to malware it has successfully planted an insider or by infiltrating the supply chain. Therefore, an attacker ’ s main challenge is to determine a way to command and in an air gapped network. In order to understand why, it is control the compromised hosts that are isolated from an accessible important to understand what advanced attack looks like. network (e.g., the Internet). Advanced attacks, also known as Advanced Persistent Threats In this paper, we propose a new adversarial model that shows (APTs) [6–8], are attacks that involve a process of several how an air gapped network can receive communications over a stages before arriving at their ultimate goal. These attacks are covert thermal channel. Concretely, we show how attackers may "Advanced" in terms of their technological awareness, use a compromised air-conditioning system (connected to the "Persistent" in their well-supported campaign to achieve the internet) to send commands to infected hosts within an air-gapped final goal, and considered to be "Threats" to the intended victim network. Since thermal communication protocols are a rather as the attackers have both capability and intent. The goal of the unexplored domain, we propose a novel line-encoding and APT depends on what the attacker desires to achieve. Many protocol suitable for this type of channel. Moreover, we provide experimental results to demonstrate the covert channel's APTs, such as those that occurred to RSA [9] and various feasibility, and to calculate the channel ’ s bandwidth. Lastly, we diplomatic agencies [10], have the goal of data exfiltration (data offer a forensic analysis and propose various ways this channel can theft), while some, such as "Stuxnet", have the goal of causing be detected and prevented. damage to assets within the target network. We believe that this study details a previously unseen vector of In Fig. 1, the stages of an APT are illustrated. In the first attack that security experts should be aware of. stage, the attacker researches the target network in order to Index Terms — Air gapped networks, APT, command & control, 1 covert channels, thermal communication. Reconnaissance I. I NTRODUCTION HERE is a common defense strategy in which an air gap T (some physical gap) is placed between networks that 5 2 maintain sensitive systems and all other nonessential Carry out the attack Initial intrusion infrastructures which are connected to a public network. The thinking behind this strategy is: if there are no connections between the sensitive network and all other public networks (e.g. the internet) then the sensitive network is secure from remote attacks. In other words, the belief is that attackers cannot breach an air gapped network if they have no physical way of 4 communicating with it. However, this strategy is not foolproof. 3 Move throughout As a result, attackers have been developing methods for Search for local the network and data/assets (near "bridging the air gap," and in several cases they have been aquire a strong the infected host) foothold successful [1–3]. A well-known attack in which an air gap was bridged Fig. 1. The stages of an APT on a victim’s network. Typically, stages 2-5 are occurred when the computer virus "Stuxnet" targeted the controlled by the attacker from a remote location over a public network such as the internet. Iranian nuclear program [4]. This virus was able to intrude an isolated computer network that operated delicate centrifuges. understand how to gain access to it, and to perform the attack. Another example is the "agent.btz" [5], a malware which was During this stage the attacker typically researches the network’s used against US military networks. According to publications it equipment, as well as researches the target organization’s caused no damage, however, it was the first confirmed case of employees. Knowledge on the employees is important in order the infection of a secure US government network which was to perform stage 2, since the initial intrusion into the network is
Recommend
More recommend