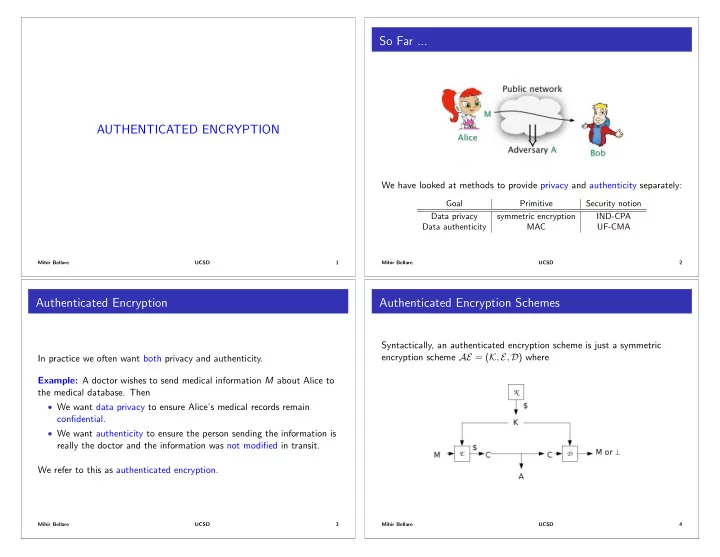

So Far ... AUTHENTICATED ENCRYPTION We have looked at methods to provide privacy and authenticity separately: Goal Primitive Security notion Data privacy symmetric encryption IND-CPA Data authenticity MAC UF-CMA Mihir Bellare UCSD 1 Mihir Bellare UCSD 2 Authenticated Encryption Authenticated Encryption Schemes Syntactically, an authenticated encryption scheme is just a symmetric encryption scheme AE = ( K , E , D ) where In practice we often want both privacy and authenticity. Example: A doctor wishes to send medical information M about Alice to the medical database. Then • We want data privacy to ensure Alice’s medical records remain confidential. • We want authenticity to ensure the person sending the information is really the doctor and the information was not modified in transit. We refer to this as authenticated encryption. Mihir Bellare UCSD 3 Mihir Bellare UCSD 4
Privacy of Authenticated Encryption Schemes Integrity of Authenticated Encryption Schemes Adversary’s goal is to get the receiver to accept a “non-authentic” ciphertext C . The notion of privacy for symmetric encryption carries over, namely we want IND-CPA. Integrity of ciphertexts: C is “non-authentic” if it was never transmitted by the sender. Mihir Bellare UCSD 5 Mihir Bellare UCSD 6 INT-CTXT Integrity with privacy Let AE = ( K , E , D ) be a symmetric encryption scheme and A an adversary. Game INTCTXT AE procedure Initialize procedure Finalize ( C ) $ K ← K ; S ← ∅ M ← D K ( C ) The goal of authenticated encryption is to provide both integrity and if ( C �∈ S ∧ M � = ⊥ ) then privacy. We will be interested in IND-CPA + INT-CTXT. procedure Enc ( M ) return true $ C ← E K ( M ) Else return false S ← S ∪ { C } Return C The int-ctxt advantage of A is Adv int - ctxt ( A ) = Pr[INTCTXT A AE ⇒ true] AE Mihir Bellare UCSD 7 Mihir Bellare UCSD 8
Plain Encryption Does Not Provide Integrity Plain Encryption Does Not Provide Integrity Alg E K ( M ) Alg E K ( M ) Alg D K ( C ) Alg D K ( C ) $ $ ← { 0 , 1 } n ← { 0 , 1 } n C [0] C [0] For i = 1 , . . . , m do For i = 1 , . . . , m do For i = 1 , . . . , m do For i = 1 , . . . , m do M [ i ] ← E − 1 M [ i ] ← E − 1 K ( C [ i ]) ⊕ C [ i − 1] K ( C [ i ]) ⊕ C [ i − 1] C [ i ] ← E K ( C [ i − 1] ⊕ M [ i ]) C [ i ] ← E K ( C [ i − 1] ⊕ M [ i ]) Return M Return M Return C Return C Question: Is CBC $ encryption INT-CTXT secure? Question: Is CBC $ encryption INT-CTXT secure? Answer: No, because any string C [0] C [1] . . . C [ m ] has a valid decryption. Plain Encryption Does Not Provide Integrity Encryption with Redundancy Alg E K ( M ) Alg D K ( C ) $ M [1] M [2] M [ m ] h ( M ) ← { 0 , 1 } n C [0] For i = 1 , . . . , m do ✐ ✐ ✐ ✐ For i = 1 , . . . , m do M [ i ] ← E − 1 K ( C [ i ]) ⊕ C [ i − 1] ❄ ❄ ❄ ❄ C [ i ] ← E K ( C [ i − 1] ⊕ M [ i ]) ... Return M E K E K E K E K Return C ❄ ❄ ❄ ❄ C [0] C [1] C [2] C [ m ] C [ m + 1] adversary A Here E : { 0 , 1 } k × { 0 , 1 } n → { 0 , 1 } n is our block cipher and h : { 0 , 1 } ∗ → ← { 0 , 1 } 3 n $ C [0] C [1] C [2] { 0 , 1 } n is a “redundancy” function, for example Return C [0] C [1] C [2] • h ( M [1] . . . M [ m ]) = 0 n Then • h ( M [1] . . . M [ m ]) = M [1] ⊕ · · · ⊕ M [ m ] Adv int - ctxt ( A ) = 1 SE • A CRC This violates INT-CTXT. • h ( M [1] . . . M [ m ]) is the first n bits of SHA1( M [1] . . . M [ m ]). A scheme whose decryption algorithm never outputs ⊥ cannot provide The redundancy is verified upon decryption. integrity! Mihir Bellare UCSD 11 Mihir Bellare UCSD 12
Encryption with Redundancy Arguments in Favor of Encryption with Redundancy M [1] M [2] M [ m ] h ( M ) ✐ ✐ ✐ ✐ ❄ ❄ ❄ ❄ ... E K E K E K E K M [1] M [2] M [ m ] h ( M ) ❄ ❄ ❄ ❄ ✐ ✐ ✐ ✐ C [0] C [1] C [2] C [ m ] C [ m + 1] ❄ ❄ ❄ ❄ ... E K E K E K E K Let E : { 0 , 1 } k × { 0 , 1 } n → { 0 , 1 } n be our block cipher and h : { 0 , 1 } ∗ → ❄ ❄ ❄ ❄ { 0 , 1 } n a redundancy function. Let SE = ( K , E ′ , D ′ ) be CBC$ encryption C [0] C [1] C [2] C [ m ] C [ m + 1] and define the encryption with redundancy scheme AE = ( K , E , D ) via The adversary will have a hard time producing the last enciphered block of Alg E K ( M ) Alg D K ( C ) a new message. M [1] . . . M [ m ] ← M M [1] . . . M [ m ] M [ m + 1] ← D ′ K ( C ) M [ m + 1] ← h ( M ) if ( M [ m + 1] = h ( M )) then $ return M [1] . . . M [ m ] C ← E ′ K ( M [1] . . . M [ m ] M [ m + 1]) else return ⊥ return C Mihir Bellare UCSD 13 Mihir Bellare UCSD 14 Encryption with Redundancy Fails WEP Attack adversary A ← { 0 , 1 } n ; M [2] ← h ( M [1]) $ M [1] $ C [0] C [1] C [2] C [3] ← Enc ( M [1] M [2]) A “real-life” rendition of this attack broke the 802.11 WEP protocol, which Return C [0] C [1] C [2] h ( M [1]) instantiated h as CRC and used a stream cipher for encryption [BGW]. ���� M [1] M [2] h ( M [1] M [2]) What makes the attack easy to see is having a clear, strong and formal ✐ ✐ ✐ security model. ❄ ❄ ❄ E K E K E K ❄ ❄ ❄ C [0] C [1] C [2] C [3] This attack succeeds for any (not secret-key dependent) redundancy function h . Mihir Bellare UCSD 15 Mihir Bellare UCSD 16
Generic Composition Generic Composition Build an authenticated encryption scheme AE = ( K , E , D ) by combining Build an authenticated encryption scheme AE = ( K , E , D ) by combining • a given IND-CPA symmetric encryption scheme SE = ( K ′ , E ′ , D ′ ) • a given PRF F : { 0 , 1 } k × { 0 , 1 } ∗ → { 0 , 1 } n • a given IND-CPA symmetric encryption scheme SE = ( K ′ , E ′ , D ′ ) • a given PRF F : { 0 , 1 } k × { 0 , 1 } ∗ → { 0 , 1 } n CBC$-AES CTR$-AES . . . A key K = K e || K m for AE always consists of a key K e for SE and a key K m for F : HMAC-SHA1 Alg K CMAC $ ← { 0 , 1 } k $ ← K ′ ; K m ECBC K e . Return K e || K m . . Mihir Bellare UCSD 17 Mihir Bellare UCSD 18 Generic Composition Methods Encrypt-and-MAC AE = ( K , E , D ) is defined by The order in which the primitives are applied is important. Can consider Alg E K e || K m ( M ) Alg D K e || K m ( C ′ || T ) Method Usage $ C ′ ← E ′ K e ( M ) M ← D ′ K e ( C ′ ) Encrypt-and-MAC (E&M) SSH T ← F K m ( M ) If ( T = F K m ( M )) then return M MAC-then-encrypt (MtE) SSL/TLS Return C ′ || T Else return ⊥ Encrypt-then-MAC (EtM) IPSec Security Achieved? We study these following [BN]. IND-CPA INT-CTXT Mihir Bellare UCSD 19 Mihir Bellare UCSD 20
Encrypt-and-MAC Encrypt-and-MAC AE = ( K , E , D ) is defined by AE = ( K , E , D ) is defined by Alg E K e || K m ( M ) Alg D K e || K m ( C ′ || T ) Alg E K e || K m ( M ) Alg D K e || K m ( C ′ || T ) $ C ′ ← E ′ K e ( M ) M ← D ′ K e ( C ′ ) $ T ← F K m ( M ) If ( T = F K m ( M )) then return M C ′ ← E ′ K e ( M ) M ← D ′ K e ( C ′ ) Return C ′ || T Else return ⊥ T ← F K m ( M ) If ( T = F K m ( M )) then return M Return C ′ || T Else return ⊥ Security Achieved? Security Achieved? IND-CPA NO INT-CTXT IND-CPA NO INT-CTXT Why? T = F K m ( M ) is a deterministic function of M and allows detection of repeats. Mihir Bellare UCSD 21 Mihir Bellare UCSD 22 Encrypt-and-MAC MAC-then-Encrypt AE = ( K , E , D ) is defined by AE = ( K , E , D ) is defined by Alg E K e || K m ( M ) Alg D K e || K m ( C ′ || T ) Alg E K e || K m ( M ) Alg D K e || K m ( C ) $ C ′ ← E ′ K e ( M ) M ← D ′ K e ( C ′ ) T ← F K m ( M ) If ( T = F K m ( M )) then return M T ← F K m ( M ) M || T ← D ′ K e ( C ) Return C ′ || T Else return ⊥ $ ← E ′ K e ( M || T ) If ( T = F K m ( M )) then return M C Return C Else return ⊥ Security Achieved? Security Achieved? IND-CPA NO IND-CPA INT-CTXT NO INT-CTXT Why? May be able to modify C ′ in such a way that its decryption is unchanged. Mihir Bellare UCSD 23 Mihir Bellare UCSD 24
MAC-then-Encrypt MAC-then-Encrypt AE = ( K , E , D ) is defined by AE = ( K , E , D ) is defined by Alg E K e || K m ( M ) Alg D K e || K m ( C ) Alg E K e || K m ( M ) Alg D K e || K m ( C ) T ← F K m ( M ) M || T ← D ′ K e ( C ) T ← F K m ( M ) M || T ← D ′ K e ( C ) $ C ← E ′ K e ( M || T ) If ( T = F K m ( M )) then return M $ ← E ′ K e ( M || T ) If ( T = F K m ( M )) then return M C Else return ⊥ Return C Return C Else return ⊥ Security Achieved? Security Achieved? IND-CPA YES IND-CPA YES INT-CTXT INT-CTXT Why? SE ′ = ( K ′ , E ′ , D ′ ) is IND-CPA secure. Mihir Bellare UCSD 25 Mihir Bellare UCSD 26 MAC-then-Encrypt Encrypt-then-MAC AE = ( K , E , D ) is defined by AE = ( K , E , D ) is defined by Alg E K e || K m ( M ) Alg D K e || K m ( C ) Alg E K e || K m ( M ) Alg D K e || K m ( C ′ || T ) T ← F K m ( M ) M || T ← D ′ K e ( C ) $ $ ← E ′ K e ( M || T ) If ( T = F K m ( M )) then return M C C ′ ← E ′ K e ( M ) M ← D ′ K e ( C ′ ) Else return ⊥ Return C T ← F K m ( C ′ ) If ( T = F K m ( C ′ )) then return M Return C ′ || T Else return ⊥ Security Achieved? IND-CPA YES Security Achieved? INT-CTXT NO IND-CPA INT-CTXT Why? May be able to modify C in such a way that its decryption is unchanged. Mihir Bellare UCSD 27 Mihir Bellare UCSD 28
Recommend
More recommend