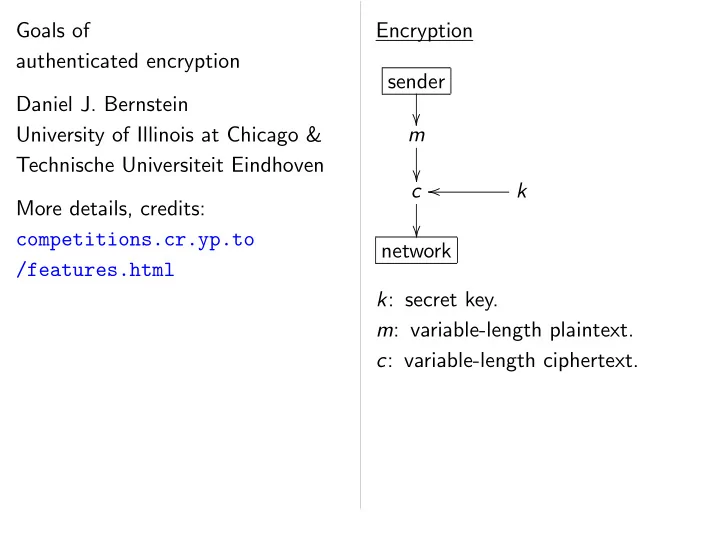

� � � � � � � � � Secret message numbers What is the attack Plaintext corruption, sender associated-data co � a n m a message-number Forge ( n; m; a ) that k c k receiver accepts but legitimate sender never network “INT-PTXT” k : secret key. (integrity of plaintexts) message number. n : secret message number. protection against riable-length associated data. a : variable-length associated data. Stronger goal: riable-length plaintext. m : variable-length plaintext. Forge at least f messages. riable-length ciphertext. c : variable-length ciphertext. eating a .
� � � � � � � � � Secret message numbers What is the attacker’s goal? Plaintext corruption, sender associated-data corruption, n m a message-number corruption. Forge ( n; m; a ) that c k receiver accepts but that legitimate sender never encrypted. network “INT-PTXT” k : secret key. (integrity of plaintexts) means er. n : secret message number. protection against such attacks. ciated data. a : variable-length associated data. Stronger goal: plaintext. m : variable-length plaintext. Forge at least f messages. ciphertext. c : variable-length ciphertext.
� � � � � � � � � Secret message numbers What is the attacker’s goal? Plaintext corruption, sender associated-data corruption, n m a message-number corruption. Forge ( n; m; a ) that c k receiver accepts but that legitimate sender never encrypted. network “INT-PTXT” k : secret key. (integrity of plaintexts) means n : secret message number. protection against such attacks. a : variable-length associated data. Stronger goal: m : variable-length plaintext. Forge at least f messages. c : variable-length ciphertext.
� � � � � � � � message numbers What is the attacker’s goal? Ciphertext Forge c Plaintext corruption, sender receiver associated-data corruption, legitimate m a message-number corruption. Forge ( n; m; a ) that “INT-CTXT” c k receiver accepts but that (integrity legitimate sender never encrypted. protection network “INT-PTXT” secret key. (integrity of plaintexts) means secret message number. protection against such attacks. riable-length associated data. Stronger goal: riable-length plaintext. Forge at least f messages. riable-length ciphertext.
numbers What is the attacker’s goal? Ciphertext corruption. Forge c that Plaintext corruption, receiver accepts but associated-data corruption, legitimate sender never � a message-number corruption. Forge ( n; m; a ) that “INT-CTXT” k receiver accepts but that (integrity of ciphertexts) legitimate sender never encrypted. protection against “INT-PTXT” (integrity of plaintexts) means ssage number. protection against such attacks. riable-length associated data. Stronger goal: riable-length plaintext. Forge at least f messages. riable-length ciphertext.
What is the attacker’s goal? Ciphertext corruption. Forge c that Plaintext corruption, receiver accepts but that associated-data corruption, legitimate sender never produced. message-number corruption. Forge ( n; m; a ) that “INT-CTXT” receiver accepts but that (integrity of ciphertexts) means legitimate sender never encrypted. protection against such attacks. “INT-PTXT” (integrity of plaintexts) means er. protection against such attacks. ciated data. Stronger goal: plaintext. Forge at least f messages. ciphertext.
What is the attacker’s goal? Ciphertext corruption. Forge c that Plaintext corruption, receiver accepts but that associated-data corruption, legitimate sender never produced. message-number corruption. Forge ( n; m; a ) that “INT-CTXT” receiver accepts but that (integrity of ciphertexts) means legitimate sender never encrypted. protection against such attacks. “INT-PTXT” (integrity of plaintexts) means protection against such attacks. Stronger goal: Forge at least f messages.
What is the attacker’s goal? Ciphertext corruption. Forge c that Plaintext corruption, receiver accepts but that associated-data corruption, legitimate sender never produced. message-number corruption. Forge ( n; m; a ) that “INT-CTXT” receiver accepts but that (integrity of ciphertexts) means legitimate sender never encrypted. protection against such attacks. “INT-PTXT” Ciphertext prediction. (integrity of plaintexts) means Distinguish c from protection against such attacks. uniform random string. Stronger goal: Forge at least f messages.
What is the attacker’s goal? Ciphertext corruption. Forge c that Plaintext corruption, receiver accepts but that associated-data corruption, legitimate sender never produced. message-number corruption. Forge ( n; m; a ) that “INT-CTXT” receiver accepts but that (integrity of ciphertexts) means legitimate sender never encrypted. protection against such attacks. “INT-PTXT” Ciphertext prediction. (integrity of plaintexts) means Distinguish c from protection against such attacks. uniform random string. Stronger goal: Is it better to Forge at least f messages. randomly pad or zero-pad a strong 112-bit MAC to 128 bits?
is the attacker’s goal? Ciphertext corruption. Replay. Forge c that Convince Plaintext corruption, receiver accepts but that legitimate ciated-data corruption, legitimate sender never produced. than legitimate message-number corruption. ( n; m; a ) that “INT-CTXT” receiver accepts but that (integrity of ciphertexts) means legitimate sender never encrypted. protection against such attacks. “INT-PTXT” Ciphertext prediction. (integrity of plaintexts) means Distinguish c from rotection against such attacks. uniform random string. Stronger goal: Is it better to at least f messages. randomly pad or zero-pad a strong 112-bit MAC to 128 bits?
attacker’s goal? Ciphertext corruption. Replay. Forge c that Convince receiver to rruption, receiver accepts but that legitimate ( n; m; a ) data corruption, legitimate sender never produced. than legitimate sender er corruption. that “INT-CTXT” but that (integrity of ciphertexts) means der never encrypted. protection against such attacks. Ciphertext prediction. plaintexts) means Distinguish c from nst such attacks. uniform random string. Is it better to messages. randomly pad or zero-pad a strong 112-bit MAC to 128 bits?
goal? Ciphertext corruption. Replay. Forge c that Convince receiver to accept receiver accepts but that legitimate ( n; m; a ) more times rruption, legitimate sender never produced. than legitimate sender sent it. rruption. “INT-CTXT” (integrity of ciphertexts) means encrypted. protection against such attacks. Ciphertext prediction. means Distinguish c from attacks. uniform random string. Is it better to randomly pad or zero-pad a strong 112-bit MAC to 128 bits?
Ciphertext corruption. Replay. Forge c that Convince receiver to accept receiver accepts but that legitimate ( n; m; a ) more times legitimate sender never produced. than legitimate sender sent it. “INT-CTXT” (integrity of ciphertexts) means protection against such attacks. Ciphertext prediction. Distinguish c from uniform random string. Is it better to randomly pad or zero-pad a strong 112-bit MAC to 128 bits?
Ciphertext corruption. Replay. Forge c that Convince receiver to accept receiver accepts but that legitimate ( n; m; a ) more times legitimate sender never produced. than legitimate sender sent it. “INT-CTXT” Reordering. (integrity of ciphertexts) means Convince receiver to accept protection against such attacks. legitimate messages out of order. Ciphertext prediction. Distinguish c from uniform random string. Is it better to randomly pad or zero-pad a strong 112-bit MAC to 128 bits?
Ciphertext corruption. Replay. Forge c that Convince receiver to accept receiver accepts but that legitimate ( n; m; a ) more times legitimate sender never produced. than legitimate sender sent it. “INT-CTXT” Reordering. (integrity of ciphertexts) means Convince receiver to accept protection against such attacks. legitimate messages out of order. Ciphertext prediction. Sabotage. Distinguish c from Prevent receiver from seeing uniform random string. ( n; m; a ) as often as sender sent it: flood radio, switch, CPU, etc. Is it better to randomly pad or zero-pad a strong 112-bit MAC to 128 bits?
Ciphertext corruption. Replay. Forge c that Convince receiver to accept receiver accepts but that legitimate ( n; m; a ) more times legitimate sender never produced. than legitimate sender sent it. “INT-CTXT” Reordering. (integrity of ciphertexts) means Convince receiver to accept protection against such attacks. legitimate messages out of order. Ciphertext prediction. Sabotage. Distinguish c from Prevent receiver from seeing uniform random string. ( n; m; a ) as often as sender sent it: flood radio, switch, CPU, etc. Is it better to randomly pad or zero-pad a Typically delegate solutions strong 112-bit MAC to 128 bits? to higher-level protocols, but is this optimal?
Ciphertext corruption. Replay. Plaintext c that Convince receiver to accept Figure out receiver accepts but that legitimate ( n; m; a ) more times legitimate sender never produced. than legitimate sender sent it. “INT-CTXT” Reordering. (integrity of ciphertexts) means Convince receiver to accept rotection against such attacks. legitimate messages out of order. Ciphertext prediction. Sabotage. Distinguish c from Prevent receiver from seeing random string. ( n; m; a ) as often as sender sent it: flood radio, switch, CPU, etc. etter to randomly pad or zero-pad a Typically delegate solutions 112-bit MAC to 128 bits? to higher-level protocols, but is this optimal?
rruption. Replay. Plaintext espionage. Convince receiver to accept Figure out user’s secret but that legitimate ( n; m; a ) more times der never produced. than legitimate sender sent it. Reordering. ciphertexts) means Convince receiver to accept nst such attacks. legitimate messages out of order. rediction. Sabotage. from Prevent receiver from seeing string. ( n; m; a ) as often as sender sent it: flood radio, switch, CPU, etc. r zero-pad a Typically delegate solutions MAC to 128 bits? to higher-level protocols, but is this optimal?
Replay. Plaintext espionage. Convince receiver to accept Figure out user’s secret message. legitimate ( n; m; a ) more times roduced. than legitimate sender sent it. Reordering. means Convince receiver to accept attacks. legitimate messages out of order. Sabotage. Prevent receiver from seeing ( n; m; a ) as often as sender sent it: flood radio, switch, CPU, etc. a Typically delegate solutions 128 bits? to higher-level protocols, but is this optimal?
Replay. Plaintext espionage. Convince receiver to accept Figure out user’s secret message. legitimate ( n; m; a ) more times than legitimate sender sent it. Reordering. Convince receiver to accept legitimate messages out of order. Sabotage. Prevent receiver from seeing ( n; m; a ) as often as sender sent it: flood radio, switch, CPU, etc. Typically delegate solutions to higher-level protocols, but is this optimal?
Replay. Plaintext espionage. Convince receiver to accept Figure out user’s secret message. legitimate ( n; m; a ) more times Message-number espionage. than legitimate sender sent it. Figure out user’s secret message number. Reordering. Convince receiver to accept legitimate messages out of order. Sabotage. Prevent receiver from seeing ( n; m; a ) as often as sender sent it: flood radio, switch, CPU, etc. Typically delegate solutions to higher-level protocols, but is this optimal?
Replay. Plaintext espionage. Convince receiver to accept Figure out user’s secret message. legitimate ( n; m; a ) more times Message-number espionage. than legitimate sender sent it. Figure out user’s secret message number. Reordering. Convince receiver to accept Traditional crypto view: legitimate messages out of order. It’s okay to use a counter as a message number. Sabotage. Prevent receiver from seeing Count is public anyway. ( n; m; a ) as often as sender sent it: flood radio, switch, CPU, etc. Typically delegate solutions to higher-level protocols, but is this optimal?
Replay. Plaintext espionage. Convince receiver to accept Figure out user’s secret message. legitimate ( n; m; a ) more times Message-number espionage. than legitimate sender sent it. Figure out user’s secret message number. Reordering. Convince receiver to accept Traditional crypto view: legitimate messages out of order. It’s okay to use a counter as a message number. Sabotage. Prevent receiver from seeing Count is public anyway. ( n; m; a ) as often as sender sent Counterarguments: it: flood radio, switch, CPU, etc. Did attacker see everything? Typically delegate solutions Maybe timestamp is better, to higher-level protocols, but how much does it leak? but is this optimal? Should encrypt by default.
What are y. Plaintext espionage. Convince receiver to accept Figure out user’s secret message. Extensive legitimate ( n; m; a ) more times Are 80-bit Message-number espionage. legitimate sender sent it. Figure out user’s secret Are 128-bit message number. dering. Convince receiver to accept Traditional crypto view: legitimate messages out of order. It’s okay to use a counter as a message number. otage. Prevent receiver from seeing Count is public anyway. a ) as often as sender sent Counterarguments: od radio, switch, CPU, etc. Did attacker see everything? ypically delegate solutions Maybe timestamp is better, higher-level protocols, but how much does it leak? this optimal? Should encrypt by default.
What are the attack Plaintext espionage. r to accept Figure out user’s secret message. Extensive computation. ; a ) more times Are 80-bit keys adequate? Message-number espionage. sender sent it. Figure out user’s secret Are 128-bit keys adequate? message number. r to accept Traditional crypto view: ssages out of order. It’s okay to use a counter as a message number. from seeing Count is public anyway. often as sender sent Counterarguments: switch, CPU, etc. Did attacker see everything? delegate solutions Maybe timestamp is better, rotocols, but how much does it leak? optimal? Should encrypt by default.
What are the attacker’s resources? Plaintext espionage. accept Figure out user’s secret message. Extensive computation. times Are 80-bit keys adequate? Message-number espionage. sent it. Figure out user’s secret Are 128-bit keys adequate? message number. accept Traditional crypto view: of order. It’s okay to use a counter as a message number. seeing Count is public anyway. sender sent Counterarguments: CPU, etc. Did attacker see everything? solutions Maybe timestamp is better, but how much does it leak? Should encrypt by default.
What are the attacker’s resources? Plaintext espionage. Figure out user’s secret message. Extensive computation. Are 80-bit keys adequate? Message-number espionage. Figure out user’s secret Are 128-bit keys adequate? message number. Traditional crypto view: It’s okay to use a counter as a message number. Count is public anyway. Counterarguments: Did attacker see everything? Maybe timestamp is better, but how much does it leak? Should encrypt by default.
What are the attacker’s resources? Plaintext espionage. Figure out user’s secret message. Extensive computation. Are 80-bit keys adequate? Message-number espionage. Figure out user’s secret Are 128-bit keys adequate? message number. Main arguments for small keys: Traditional crypto view: 1. Smaller keys are cheaper. It’s okay to use a counter as a message number. Count is public anyway. Counterarguments: Did attacker see everything? Maybe timestamp is better, but how much does it leak? Should encrypt by default.
What are the attacker’s resources? Plaintext espionage. Figure out user’s secret message. Extensive computation. Are 80-bit keys adequate? Message-number espionage. Figure out user’s secret Are 128-bit keys adequate? message number. Main arguments for small keys: Traditional crypto view: 1. Smaller keys are cheaper. It’s okay to use a counter 2. Attack cost outweighs as a message number. economic benefit of breaking key, Count is public anyway. so no sensible attacker will Counterarguments: carry out a 2 80 attack. Did attacker see everything? Maybe 64-bit keys are enough. Maybe timestamp is better, but how much does it leak? Should encrypt by default.
What are the attacker’s resources? Main countera Plaintext espionage. out user’s secret message. 1. Larger Extensive computation. Are 80-bit keys adequate? User doesn’t Message-number espionage. out user’s secret Are 128-bit keys adequate? better perfo message number. Main arguments for small keys: raditional crypto view: 1. Smaller keys are cheaper. ay to use a counter 2. Attack cost outweighs message number. economic benefit of breaking key, is public anyway. so no sensible attacker will Counterarguments: carry out a 2 80 attack. attacker see everything? Maybe 64-bit keys are enough. timestamp is better, w much does it leak? encrypt by default.
What are the attacker’s resources? Main counterarguments espionage. user’s secret message. 1. Larger keys are Extensive computation. Are 80-bit keys adequate? User doesn’t actually er espionage. user’s secret Are 128-bit keys adequate? better performance. er. Main arguments for small keys: crypto view: 1. Smaller keys are cheaper. a counter 2. Attack cost outweighs number. economic benefit of breaking key, anyway. so no sensible attacker will rguments: carry out a 2 80 attack. everything? Maybe 64-bit keys are enough. timestamp is better, does it leak? by default.
What are the attacker’s resources? Main counterarguments: message. 1. Larger keys are cheap enough. Extensive computation. Are 80-bit keys adequate? User doesn’t actually need espionage. Are 128-bit keys adequate? better performance. Main arguments for small keys: 1. Smaller keys are cheaper. 2. Attack cost outweighs economic benefit of breaking key, so no sensible attacker will carry out a 2 80 attack. everything? Maybe 64-bit keys are enough. etter, leak? default.
What are the attacker’s resources? Main counterarguments: 1. Larger keys are cheap enough. Extensive computation. Are 80-bit keys adequate? User doesn’t actually need Are 128-bit keys adequate? better performance. Main arguments for small keys: 1. Smaller keys are cheaper. 2. Attack cost outweighs economic benefit of breaking key, so no sensible attacker will carry out a 2 80 attack. Maybe 64-bit keys are enough.
What are the attacker’s resources? Main counterarguments: 1. Larger keys are cheap enough. Extensive computation. Are 80-bit keys adequate? User doesn’t actually need Are 128-bit keys adequate? better performance. Main arguments for small keys: 2. Attacker’s cost-benefit ratio is improved by 1. Smaller keys are cheaper. multiple-user attacks, 2. Attack cost outweighs multiple forgeries, etc. economic benefit of breaking key, so no sensible attacker will carry out a 2 80 attack. Maybe 64-bit keys are enough.
What are the attacker’s resources? Main counterarguments: 1. Larger keys are cheap enough. Extensive computation. Are 80-bit keys adequate? User doesn’t actually need Are 128-bit keys adequate? better performance. Main arguments for small keys: 2. Attacker’s cost-benefit ratio is improved by 1. Smaller keys are cheaper. multiple-user attacks, 2. Attack cost outweighs multiple forgeries, etc. economic benefit of breaking key, 3. Some attackers carry out so no sensible attacker will attacks that are feasible carry out a 2 80 attack. but not economically rational. Maybe 64-bit keys are enough. What attacks are feasible?
are the attacker’s resources? Main counterarguments: Back-of-the-envelop 2 57 watts: 1. Larger keys are cheap enough. Extensive computation. 80-bit keys adequate? User doesn’t actually need atmosphere 128-bit keys adequate? better performance. 2 44 watts: arguments for small keys: 2. Attacker’s cost-benefit ratio 2 26 watts: is improved by Smaller keys are cheaper. costing 2 multiple-user attacks, ttack cost outweighs 1 watt: p multiple forgeries, etc. 2 68 bit op economic benefit of breaking key, 3. Some attackers carry out sensible attacker will using mass-ma attacks that are feasible out a 2 80 attack. but not economically rational. 64-bit keys are enough. What attacks are feasible?
attacker’s resources? Main counterarguments: Back-of-the-envelop 2 57 watts: received 1. Larger keys are cheap enough. computation. adequate? User doesn’t actually need atmosphere from the adequate? better performance. 2 44 watts: world p for small keys: 2. Attacker’s cost-benefit ratio 2 26 watts: one computer is improved by costing 2 30 dollars. are cheaper. multiple-user attacks, outweighs 1 watt: power for multiple forgeries, etc. 2 68 bit operations enefit of breaking key, 3. Some attackers carry out attacker will using mass-market attacks that are feasible attack. but not economically rational. eys are enough. What attacks are feasible?
resources? Main counterarguments: Back-of-the-envelope figures: 2 57 watts: received by Earth’s 1. Larger keys are cheap enough. User doesn’t actually need atmosphere from the Sun. adequate? better performance. 2 44 watts: world power usage. keys: 2. Attacker’s cost-benefit ratio 2 26 watts: one computer center is improved by costing 2 30 dollars. er. multiple-user attacks, 1 watt: power for multiple forgeries, etc. 2 68 bit operations per year reaking key, 3. Some attackers carry out will using mass-market GPUs. attacks that are feasible but not economically rational. enough. What attacks are feasible?
Main counterarguments: Back-of-the-envelope figures: 2 57 watts: received by Earth’s 1. Larger keys are cheap enough. User doesn’t actually need atmosphere from the Sun. better performance. 2 44 watts: world power usage. 2. Attacker’s cost-benefit ratio 2 26 watts: one computer center is improved by costing 2 30 dollars. multiple-user attacks, 1 watt: power for multiple forgeries, etc. 2 68 bit operations per year 3. Some attackers carry out using mass-market GPUs. attacks that are feasible but not economically rational. What attacks are feasible?
Main counterarguments: Back-of-the-envelope figures: 2 57 watts: received by Earth’s 1. Larger keys are cheap enough. User doesn’t actually need atmosphere from the Sun. better performance. 2 44 watts: world power usage. 2. Attacker’s cost-benefit ratio 2 26 watts: one computer center is improved by costing 2 30 dollars. multiple-user attacks, 1 watt: power for multiple forgeries, etc. 2 68 bit operations per year 3. Some attackers carry out using mass-market GPUs. attacks that are feasible Scalable quantum computers. but not economically rational. 2 64 simple quantum operations What attacks are feasible? to find a 128-bit key using Grover’s algorithm.
counterarguments: Back-of-the-envelope figures: Many messages. Some designers 2 57 watts: received by Earth’s rger keys are cheap enough. “switch k doesn’t actually need atmosphere from the Sun. Other designers performance. 2 44 watts: world power usage. eliminating ttacker’s cost-benefit ratio adds robustness. 2 26 watts: one computer center roved by costing 2 30 dollars. multiple-user attacks, 1 watt: power for multiple forgeries, etc. 2 68 bit operations per year Some attackers carry out using mass-market GPUs. attacks that are feasible Scalable quantum computers. not economically rational. 2 64 simple quantum operations attacks are feasible? to find a 128-bit key using Grover’s algorithm.
rguments: Back-of-the-envelope figures: Many messages. Some designers blame 2 57 watts: received by Earth’s re cheap enough. “switch keys after actually need atmosphere from the Sun. Other designers argue rmance. 2 44 watts: world power usage. eliminating such requirements cost-benefit ratio adds robustness. 2 26 watts: one computer center costing 2 30 dollars. attacks, 1 watt: power for rgeries, etc. 2 68 bit operations per year ers carry out using mass-market GPUs. feasible Scalable quantum computers. economically rational. 2 64 simple quantum operations re feasible? to find a 128-bit key using Grover’s algorithm.
Back-of-the-envelope figures: Many messages. Some designers blame the user: 2 57 watts: received by Earth’s enough. “switch keys after 2 20 messages”. atmosphere from the Sun. Other designers argue that 2 44 watts: world power usage. eliminating such requirements ratio adds robustness. 2 26 watts: one computer center costing 2 30 dollars. 1 watt: power for 2 68 bit operations per year out using mass-market GPUs. Scalable quantum computers. rational. 2 64 simple quantum operations to find a 128-bit key using Grover’s algorithm.
Back-of-the-envelope figures: Many messages. Some designers blame the user: 2 57 watts: received by Earth’s “switch keys after 2 20 messages”. atmosphere from the Sun. Other designers argue that 2 44 watts: world power usage. eliminating such requirements adds robustness. 2 26 watts: one computer center costing 2 30 dollars. 1 watt: power for 2 68 bit operations per year using mass-market GPUs. Scalable quantum computers. 2 64 simple quantum operations to find a 128-bit key using Grover’s algorithm.
Back-of-the-envelope figures: Many messages. Some designers blame the user: 2 57 watts: received by Earth’s “switch keys after 2 20 messages”. atmosphere from the Sun. Other designers argue that 2 44 watts: world power usage. eliminating such requirements adds robustness. 2 26 watts: one computer center costing 2 30 dollars. Chosen plaintexts, chosen ciphertexts, 1 watt: power for 2 68 bit operations per year chosen message numbers. Consensus: using mass-market GPUs. Unacceptable to blame the user. Scalable quantum computers. All ciphers must be safe against 2 64 simple quantum operations chosen-plaintext attacks and to find a 128-bit key against chosen-ciphertext attacks. using Grover’s algorithm.
Back-of-the-envelope figures: Many messages. Many users. Some designers blame the user: degrade atts: received by Earth’s “switch keys after 2 20 messages”. atmosphere from the Sun. Other designers argue that atts: world power usage. eliminating such requirements adds robustness. atts: one computer center costing 2 30 dollars. Chosen plaintexts, chosen ciphertexts, att: power for chosen message numbers. bit operations per year Consensus: mass-market GPUs. Unacceptable to blame the user. Scalable quantum computers. All ciphers must be safe against simple quantum operations chosen-plaintext attacks and a 128-bit key against chosen-ciphertext attacks. Grover’s algorithm.
Back-of-the-envelope figures: Many users. How Many messages. Some designers blame the user: degrade with numb received by Earth’s “switch keys after 2 20 messages”. the Sun. Other designers argue that power usage. eliminating such requirements adds robustness. computer center rs. Chosen plaintexts, chosen ciphertexts, r chosen message numbers. erations per year Consensus: et GPUs. Unacceptable to blame the user. quantum computers. All ciphers must be safe against quantum operations chosen-plaintext attacks and key against chosen-ciphertext attacks. algorithm.
figures: Many users. How does securit Many messages. Some designers blame the user: degrade with number of keys? rth’s “switch keys after 2 20 messages”. Other designers argue that usage. eliminating such requirements adds robustness. center Chosen plaintexts, chosen ciphertexts, chosen message numbers. r Consensus: Unacceptable to blame the user. computers. All ciphers must be safe against erations chosen-plaintext attacks and against chosen-ciphertext attacks.
Many users. How does security Many messages. Some designers blame the user: degrade with number of keys? “switch keys after 2 20 messages”. Other designers argue that eliminating such requirements adds robustness. Chosen plaintexts, chosen ciphertexts, chosen message numbers. Consensus: Unacceptable to blame the user. All ciphers must be safe against chosen-plaintext attacks and against chosen-ciphertext attacks.
Many users. How does security Many messages. Some designers blame the user: degrade with number of keys? “switch keys after 2 20 messages”. Repeated message numbers. Other designers argue that Minimum impact: Attacker sees eliminating such requirements whether ( n; m; a ) is repeated. adds robustness. Examples of larger impact Chosen plaintexts, for many ciphers: chosen ciphertexts, Leak number of shared initial chosen message numbers. blocks of plaintext. Consensus: Unacceptable to blame the user. Leak xor of first non-shared block. All ciphers must be safe against Allow forgery under this n . chosen-plaintext attacks and against chosen-ciphertext attacks. Allow forgery under any n ′ .
Many users. How does security messages. Software designers blame the user: degrade with number of keys? Typical culp “switch keys after 2 20 messages”. secret branches, Repeated message numbers. designers argue that secret m Minimum impact: Attacker sees eliminating such requirements Also, on whether ( n; m; a ) is repeated. robustness. secret m Examples of larger impact Chosen plaintexts, for many ciphers: chosen ciphertexts, Leak number of shared initial chosen message numbers. blocks of plaintext. Consensus: Unacceptable to blame the user. Leak xor of first non-shared block. ciphers must be safe against Allow forgery under this n . chosen-plaintext attacks and against chosen-ciphertext attacks. Allow forgery under any n ′ .
Many users. How does security messages. Software side channels. blame the user: degrade with number of keys? Typical culprits: after 2 20 messages”. secret branches, Repeated message numbers. argue that secret memory addresses. Minimum impact: Attacker sees requirements Also, on some CPUs, whether ( n; m; a ) is repeated. robustness. secret multiplication Examples of larger impact plaintexts, for many ciphers: ciphertexts, Leak number of shared initial message numbers. blocks of plaintext. blame the user. Leak xor of first non-shared block. be safe against Allow forgery under this n . attacks and chosen-ciphertext attacks. Allow forgery under any n ′ .
Many users. How does security Software side channels. user: degrade with number of keys? Typical culprits: messages”. secret branches, Repeated message numbers. that secret memory addresses. Minimum impact: Attacker sees requirements Also, on some CPUs, whether ( n; m; a ) is repeated. secret multiplication inputs. Examples of larger impact for many ciphers: Leak number of shared initial ers. blocks of plaintext. the user. Leak xor of first non-shared block. against Allow forgery under this n . and attacks. Allow forgery under any n ′ .
Many users. How does security Software side channels. degrade with number of keys? Typical culprits: secret branches, Repeated message numbers. secret memory addresses. Minimum impact: Attacker sees Also, on some CPUs, whether ( n; m; a ) is repeated. secret multiplication inputs. Examples of larger impact for many ciphers: Leak number of shared initial blocks of plaintext. Leak xor of first non-shared block. Allow forgery under this n . Allow forgery under any n ′ .
Many users. How does security Software side channels. degrade with number of keys? Typical culprits: secret branches, Repeated message numbers. secret memory addresses. Minimum impact: Attacker sees Also, on some CPUs, whether ( n; m; a ) is repeated. secret multiplication inputs. Examples of larger impact Hardware side channels. for many ciphers: Power consumption, Leak number of shared initial electromagnetic radiation, etc. blocks of plaintext. Leak xor of first non-shared block. Allow forgery under this n . Allow forgery under any n ′ .
Many users. How does security Software side channels. degrade with number of keys? Typical culprits: secret branches, Repeated message numbers. secret memory addresses. Minimum impact: Attacker sees Also, on some CPUs, whether ( n; m; a ) is repeated. secret multiplication inputs. Examples of larger impact Hardware side channels. for many ciphers: Power consumption, Leak number of shared initial electromagnetic radiation, etc. blocks of plaintext. Faults. Flip bits in computation. Leak xor of first non-shared block. Allow forgery under this n . Allow forgery under any n ′ .
Many users. How does security Software side channels. degrade with number of keys? Typical culprits: secret branches, Repeated message numbers. secret memory addresses. Minimum impact: Attacker sees Also, on some CPUs, whether ( n; m; a ) is repeated. secret multiplication inputs. Examples of larger impact Hardware side channels. for many ciphers: Power consumption, Leak number of shared initial electromagnetic radiation, etc. blocks of plaintext. Faults. Flip bits in computation. Leak xor of first non-shared block. Thefts and monitors. Allow forgery under this n . Attacker steals secret keys. Can we still protect Allow forgery under any n ′ . past communication?
users. How does security What perfo Software side channels. degrade with number of keys? Typical culprits: Typical p secret branches, for ASICs: eated message numbers. secret memory addresses. Minimum impact: Attacker sees Low energy Also, on some CPUs, whether ( n; m; a ) is repeated. secret multiplication inputs. Low pow Examples of larger impact Hardware side channels. Low area ny ciphers: Power consumption, loosely p number of shared initial electromagnetic radiation, etc. “gate equivalents”). of plaintext. Faults. Flip bits in computation. High throughput xor of first non-shared block. (bytes per Thefts and monitors. forgery under this n . Attacker steals secret keys. Low latency Can we still protect forgery under any n ′ . very loosely past communication?
How does security What performance Software side channels. number of keys? Typical culprits: Typical performance secret branches, for ASICs: message numbers. secret memory addresses. impact: Attacker sees Low energy (joules) Also, on some CPUs, ) is repeated. secret multiplication inputs. Low power (watts). rger impact Hardware side channels. Low area (square m ciphers: Power consumption, loosely predicted b shared initial electromagnetic radiation, etc. “gate equivalents”). plaintext. Faults. Flip bits in computation. High throughput non-shared block. (bytes per second). Thefts and monitors. under this n . Attacker steals secret keys. Low latency (seconds; Can we still protect under any n ′ . very loosely predicted past communication?
security What performance is measured? Software side channels. eys? Typical culprits: Typical performance metrics secret branches, for ASICs: numbers. secret memory addresses. er sees Low energy (joules) per byte Also, on some CPUs, eated. secret multiplication inputs. Low power (watts). Hardware side channels. Low area (square micrometers; Power consumption, loosely predicted by initial electromagnetic radiation, etc. “gate equivalents”). Faults. Flip bits in computation. High throughput red block. (bytes per second). Thefts and monitors. . Attacker steals secret keys. Low latency (seconds; Can we still protect . very loosely predicted by cycles). past communication?
What performance is measured? Software side channels. Typical culprits: Typical performance metrics secret branches, for ASICs: secret memory addresses. Low energy (joules) per byte. Also, on some CPUs, secret multiplication inputs. Low power (watts). Hardware side channels. Low area (square micrometers; Power consumption, loosely predicted by electromagnetic radiation, etc. “gate equivalents”). Faults. Flip bits in computation. High throughput (bytes per second). Thefts and monitors. Attacker steals secret keys. Low latency (seconds; Can we still protect very loosely predicted by cycles). past communication?
What performance is measured? Similar m are side channels. ypical culprits: FPGAs and Typical performance metrics branches, for ASICs: For ASICs memory addresses. throughput Low energy (joules) per byte. on some CPUs, is not a useful multiplication inputs. Low power (watts). without are side channels. Low area (square micrometers; Parallelize consumption, loosely predicted by or across electromagnetic radiation, etc. “gate equivalents”). for arbitra ts. Flip bits in computation. High throughput (bytes per second). Thefts and monitors. er steals secret keys. Low latency (seconds; e still protect very loosely predicted by cycles). communication?
What performance is measured? Similar metrics for channels. FPGAs and softwa Typical performance metrics for ASICs: For ASICs and FPGAs, addresses. throughput per se Low energy (joules) per byte. CPUs, is not a useful metric plication inputs. Low power (watts). without limit on area channels. Low area (square micrometers; Parallelize across blo consumption, loosely predicted by or across independent radiation, etc. “gate equivalents”). for arbitrarily high in computation. High throughput (bytes per second). monitors. secret keys. Low latency (seconds; rotect very loosely predicted by cycles). communication?
What performance is measured? Similar metrics for FPGAs and software. Typical performance metrics for ASICs: For ASICs and FPGAs, throughput per se Low energy (joules) per byte. is not a useful metric inputs. Low power (watts). without limit on area (or pow Low area (square micrometers; Parallelize across blocks loosely predicted by or across independent messages etc. “gate equivalents”). for arbitrarily high throughput. computation. High throughput (bytes per second). eys. Low latency (seconds; very loosely predicted by cycles).
What performance is measured? Similar metrics for FPGAs and software. Typical performance metrics for ASICs: For ASICs and FPGAs, throughput per se Low energy (joules) per byte. is not a useful metric Low power (watts). without limit on area (or power). Low area (square micrometers; Parallelize across blocks loosely predicted by or across independent messages “gate equivalents”). for arbitrarily high throughput. High throughput (bytes per second). Low latency (seconds; very loosely predicted by cycles).
What performance is measured? Similar metrics for FPGAs and software. Typical performance metrics for ASICs: For ASICs and FPGAs, throughput per se Low energy (joules) per byte. is not a useful metric Low power (watts). without limit on area (or power). Low area (square micrometers; Parallelize across blocks loosely predicted by or across independent messages “gate equivalents”). for arbitrarily high throughput. High throughput Fix: measure (bytes per second). ratio of area and throughput, i.e., product of area and time per byte. Low latency (seconds; very loosely predicted by cycles).
performance is measured? Similar metrics for What op FPGAs and software. ypical performance metrics Authenticate ASICs: For ASICs and FPGAs, encrypt throughput per se Cost per energy (joules) per byte. is not a useful metric far below ower (watts). without limit on area (or power). Send valid rea (square micrometers; Parallelize across blocks data, or predicted by or across independent messages “Encrypt equivalents”). for arbitrarily high throughput. cost of decryption throughput Fix: measure per second). ratio of area and throughput, i.e., product of area and time per byte. latency (seconds; osely predicted by cycles).
rmance is measured? Similar metrics for What operations a FPGAs and software. rmance metrics Authenticate only For ASICs and FPGAs, encrypt and authenticate? throughput per se Cost per byte of a (joules) per byte. is not a useful metric far below cost per atts). without limit on area (or power). Send valid data, re micrometers; Parallelize across blocks data, or receive invalid by or across independent messages “Encrypt then MA equivalents”). for arbitrarily high throughput. cost of decryption throughput Fix: measure second). ratio of area and throughput, i.e., product of area and time per byte. (seconds; redicted by cycles).
measured? Similar metrics for What operations are measured? FPGAs and software. metrics Authenticate only, or For ASICs and FPGAs, encrypt and authenticate? throughput per se Cost per byte of a can be yte. is not a useful metric far below cost per byte of m without limit on area (or power). Send valid data, receive valid icrometers; Parallelize across blocks data, or receive invalid data? or across independent messages “Encrypt then MAC” skips for arbitrarily high throughput. cost of decryption for forgeries. Fix: measure ratio of area and throughput, i.e., product of area and time per byte. cycles).
Similar metrics for What operations are measured? FPGAs and software. Authenticate only, or For ASICs and FPGAs, encrypt and authenticate? throughput per se Cost per byte of a can be is not a useful metric far below cost per byte of m . without limit on area (or power). Send valid data, receive valid Parallelize across blocks data, or receive invalid data? or across independent messages “Encrypt then MAC” skips for arbitrarily high throughput. cost of decryption for forgeries. Fix: measure ratio of area and throughput, i.e., product of area and time per byte.
Similar metrics for What operations are measured? FPGAs and software. Authenticate only, or For ASICs and FPGAs, encrypt and authenticate? throughput per se Cost per byte of a can be is not a useful metric far below cost per byte of m . without limit on area (or power). Send valid data, receive valid Parallelize across blocks data, or receive invalid data? or across independent messages “Encrypt then MAC” skips for arbitrarily high throughput. cost of decryption for forgeries. Fix: measure Different area targets: ratio of area and throughput, i.e., encryption/authentication circuit; product of area and time per byte. verification/decryption circuit; circuit that can dynamically select either operation.
r metrics for What operations are measured? Plaintext FPGAs and software. and asso Authenticate only, or Huge impact ASICs and FPGAs, encrypt and authenticate? throughput per se Cost per byte of a can be Warning: a useful metric far below cost per byte of m . “overhead” without limit on area (or power). Cipher with Send valid data, receive valid can be consiste rallelize across blocks data, or receive invalid data? ross independent messages “Encrypt then MAC” skips rbitrarily high throughput. cost of decryption for forgeries. measure Different area targets: of area and throughput, i.e., encryption/authentication circuit; duct of area and time per byte. verification/decryption circuit; circuit that can dynamically select either operation.
for What operations are measured? Plaintext length ware. and associated-data Authenticate only, or Huge impact on perfo FPGAs, encrypt and authenticate? se Cost per byte of a can be Warning: Do not solely metric far below cost per byte of m . “overhead” of two area (or power). Cipher with larger Send valid data, receive valid can be consistently across blocks data, or receive invalid data? endent messages “Encrypt then MAC” skips high throughput. cost of decryption for forgeries. Different area targets: throughput, i.e., encryption/authentication circuit; and time per byte. verification/decryption circuit; circuit that can dynamically select either operation.
What operations are measured? Plaintext length and associated-data length. Authenticate only, or Huge impact on performance. encrypt and authenticate? Cost per byte of a can be Warning: Do not solely compa far below cost per byte of m . “overhead” of two ciphers. ower). Cipher with larger “overhead” Send valid data, receive valid can be consistently faster. data, or receive invalid data? messages “Encrypt then MAC” skips throughput. cost of decryption for forgeries. Different area targets: throughput, i.e., encryption/authentication circuit; per byte. verification/decryption circuit; circuit that can dynamically select either operation.
What operations are measured? Plaintext length and associated-data length. Authenticate only, or Huge impact on performance. encrypt and authenticate? Cost per byte of a can be Warning: Do not solely compare far below cost per byte of m . “overhead” of two ciphers. Cipher with larger “overhead” Send valid data, receive valid can be consistently faster. data, or receive invalid data? “Encrypt then MAC” skips cost of decryption for forgeries. Different area targets: encryption/authentication circuit; verification/decryption circuit; circuit that can dynamically select either operation.
What operations are measured? Plaintext length and associated-data length. Authenticate only, or Huge impact on performance. encrypt and authenticate? Cost per byte of a can be Warning: Do not solely compare far below cost per byte of m . “overhead” of two ciphers. Cipher with larger “overhead” Send valid data, receive valid can be consistently faster. data, or receive invalid data? “Encrypt then MAC” skips Number of inputs. cost of decryption for forgeries. e.g. reduce latency by processing several AES-CBC Different area targets: messages in parallel. encryption/authentication circuit; Simplest if many messages verification/decryption circuit; have the same length. circuit that can dynamically select either operation.
operations are measured? Plaintext length Number Most (not and associated-data length. Authenticate only, or Huge impact on performance. expect p encrypt and authenticate? “expanded er byte of a can be Warning: Do not solely compare elow cost per byte of m . “overhead” of two ciphers. Warning: Cipher with larger “overhead” “agility” valid data, receive valid can be consistently faster. Cipher with or receive invalid data? can be consiste “Encrypt then MAC” skips Number of inputs. of decryption for forgeries. e.g. reduce latency by processing several AES-CBC Different area targets: messages in parallel. encryption/authentication circuit; Simplest if many messages verification/decryption circuit; have the same length. that can dynamically select operation.
are measured? Plaintext length Number of times Most (not all) ciphers and associated-data length. only, or Huge impact on performance. expect precomputation authenticate? “expanded keys”. a can be Warning: Do not solely compare er byte of m . “overhead” of two ciphers. Warning: Do not solely Cipher with larger “overhead” “agility” of two ciphers. data, receive valid can be consistently faster. Cipher with better receive invalid data? can be consistently MAC” skips Number of inputs. decryption for forgeries. e.g. reduce latency by processing several AES-CBC rgets: messages in parallel. encryption/authentication circuit; Simplest if many messages verification/decryption circuit; have the same length. dynamically select eration.
measured? Plaintext length Number of times a key is used. Most (not all) ciphers and associated-data length. Huge impact on performance. expect precomputation of authenticate? “expanded keys”. Warning: Do not solely compare m . “overhead” of two ciphers. Warning: Do not solely compa Cipher with larger “overhead” “agility” of two ciphers. valid can be consistently faster. Cipher with better “agility” data? can be consistently slower. skips Number of inputs. rgeries. e.g. reduce latency by processing several AES-CBC messages in parallel. circuit; Simplest if many messages circuit; have the same length. dynamically select
Plaintext length Number of times a key is used. Most (not all) ciphers and associated-data length. Huge impact on performance. expect precomputation of “expanded keys”. Warning: Do not solely compare “overhead” of two ciphers. Warning: Do not solely compare Cipher with larger “overhead” “agility” of two ciphers. can be consistently faster. Cipher with better “agility” can be consistently slower. Number of inputs. e.g. reduce latency by processing several AES-CBC messages in parallel. Simplest if many messages have the same length.
Recommend
More recommend