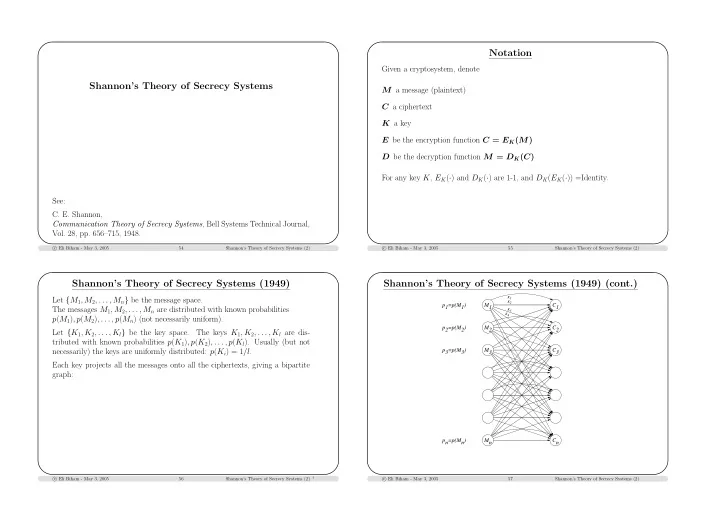

Notation Given a cryptosystem, denote Shannon’s Theory of Secrecy Systems M a message (plaintext) C a ciphertext K a key E be the encryption function C = E K ( M ) D be the decryption function M = D K ( C ) For any key K , E K ( · ) and D K ( · ) are 1-1, and D K ( E K ( · )) =Identity. See: C. E. Shannon, Communication Theory of Secrecy Systems , Bell Systems Technical Journal, Vol. 28, pp. 656–715, 1948. � Eli Biham - May 3, 2005 c 54 Shannon’s Theory of Secrecy Systems (2) � Eli Biham - May 3, 2005 c 55 Shannon’s Theory of Secrecy Systems (2) Shannon’s Theory of Secrecy Systems (1949) Shannon’s Theory of Secrecy Systems (1949) (cont.) K1 Let { M 1 , M 2 , . . . , M n } be the message space. K2 p1=p(M1) M1 C1 The messages M 1 , M 2 , . . . , M n are distributed with known probabilities K3 K4 p ( M 1 ) , p ( M 2 ) , . . . , p ( M n ) (not necessarily uniform). p2=p(M2) M2 C2 Let { K 1 , K 2 , . . . , K l } be the key space. The keys K 1 , K 2 , . . . , K l are dis- tributed with known probabilities p ( K 1 ) , p ( K 2 ) , . . . , p ( K l ). Usually (but not p3=p(M3) M3 C3 necessarily) the keys are uniformly distributed: p ( K i ) = 1 /l . Each key projects all the messages onto all the ciphertexts, giving a bipartite graph: pn=p(Mn) Mn Cn � Eli Biham - May 3, 2005 c 56 Shannon’s Theory of Secrecy Systems (2) † � Eli Biham - May 3, 2005 c 57 Shannon’s Theory of Secrecy Systems (2)
� ✁ ✂✄ ☎ Perfect Ciphers Perfect Ciphers (cont.) and thus it follows that Definition : A cipher is perfect ( ) if for any M, C Theorem : A cipher is perfect iff p ( M | C ) = p ( M ) ∀ M, C p ( C ) = p ( C | M ) . (i.e., the ciphertext does not reveal any information on the plaintext). By this definition, a perfect cipher is immune against ciphertext only attacks, even if the attacker has infinite computational power (unconditional security in Note that context of ciphertext only attacks). p ( C | M ) = p ( K ) . � K Note that E K ( M )= C p ( M ) p ( C | M ) = p ( M, C ) = p ( C ) p ( M | C ) . Therefore, a cipher is perfect iff ∀ C p ( K ) is independent of M � K E K ( M )= C � Eli Biham - May 3, 2005 c 58 Shannon’s Theory of Secrecy Systems (2) � Eli Biham - May 3, 2005 c 59 Shannon’s Theory of Secrecy Systems (2) Perfect Ciphers (cont.) Perfect Ciphers (cont.) Theorem : A perfect cipher satisfies l ≥ n (#keys ≥ #messages). Example : Encrypting only one letter by Caesar cipher: l = n = 26, p ( C ) = p ( C | M ) = 1 / 26. Proof : Assume the contrary: l < n . Let C 0 be such that p ( C 0 ) > 0. There exist l 0 (1 ≤ l 0 ≤ l ) messages M such that M = D K ( C 0 ) for some K . Let M 0 But: be a message not of the form D K ( C 0 ) (there exist n − l 0 such messages). Thus, When encrypting two letters: l = 26, n = 26 2 , p ( C ) = 1 / 26 2 . p ( C 0 | M 0 ) = p ( K ) = K ∈∅ p ( K ) = 0 Each M has only 26 possible values for C , and thus for those C ’s: p ( C | M ) = � � K 1 / 26, while for the others C ’s p ( C | M ) = 0. E K ( M 0 )= C 0 but in a perfect cipher In particular, p ( C = XY | M = aa ) = 0 for any X � = Y . p ( C 0 | M 0 ) = p ( C 0 ) > 0 . Contradiction. QED � Eli Biham - May 3, 2005 c 60 Shannon’s Theory of Secrecy Systems (2) � Eli Biham - May 3, 2005 c 61 Shannon’s Theory of Secrecy Systems (2)
✂ ✁✂ ☎ ✄✝ ✆ ☎ ✄ � ✄ Vernam is a Perfect Cipher Long Message Encryption Theorem : Vernam is a perfect cipher. To encrypt a long message M = M 1 M 2 . . . M N ( M is the full message, the M i ’s are the various letters) we encrypt each block M i to C i = E K ( M i ) under Vernam is a Vigenere with keys as long as the message. Clearly, if the keys are the same key K , and concatenate the results C = C 1 C 2 . . . C N . even slightly shorter, the cipher is not perfect. This cipher is not perfect since there is N such that #keys < #messages of Informally, in Vernam cipher, for each possible ciphertext, all the messages are length N (and since p ( XY | aa ) = 0 � = p ( XY ) when X � = Y ). still possible, as given P and C , there is a unique key that encrypts P to C . As we do not have any information on the key (and the keys are selected with Thus, we can gain information on the key or the message given the cipher- uniform distribution), we cannot discard any possible message-key pairs. text only (for a given C there are only #keys possible messages, rather than #messages). Proof : Clearly, in Vernam l = n . Given that the keys are uniformly selected at random, p ( K ) = 1 /l = 1 /n . p ( C | M ) = p ( K = C − M ) = 1 n = 1 l . Since p ( C | M ) = 1 /l for any M and C , clearly also p ( C | M ) = p ( C ). QED This proof hold also in the binary (XOR) case of one-time-pad. � Eli Biham - May 3, 2005 c 62 Shannon’s Theory of Secrecy Systems (2) � Eli Biham - May 3, 2005 c 63 Shannon’s Theory of Secrecy Systems (2) Unicity Distance Unicity Distance (cont.) How long should M and C be so we can identify the message M uniquely given Definition : the unicity distance N ( ) is the ciphertext C ? N = key length in bits We will instead ask the question: How long should M and C be so we can D identify the key K uniquely given the ciphertext C ? We will assume appropriate randomness and independence assumptions on the If D = 0 an attacker cannot identify the message uniquely. In this case we say cipher (i.e., all keys generate different and independent permutations, etc.) that N = ∞ . Let H be the average entropy of a plaintext character. It is known that in Conclusion : Compression of a message before encrypting reduces D (because English H = 1 . 5, i.e., it is possible in theory to compress each character in 1.5 the same text is compressed to a shorter length), and thus increases the unicity bits, and the approximate number of legal English texts of length m characters is (2 1 . 5 ) m . distance. Let D be the number of bits of redundancy that each character contains in the plaintext. In English D = log 26 − H = 4 . 7 − 1 . 5 = 3 . 2, i.e., 3.2 bits are redundant in each character. In an ASCII byte, D = log 256 − H = 8 − H . � Eli Biham - May 3, 2005 c 64 Shannon’s Theory of Secrecy Systems (2) � Eli Biham - May 3, 2005 c 65 Shannon’s Theory of Secrecy Systems (2)
Random Ciphers Random Ciphers (cont.) Assume that the message space and the ciphertext space are of size n (i.e., there Example : In English D = log 26 − H . log 26 = 4 . 7, H = 1 . 5 (as letters are are n different messages of size N ). dependent in English). D = log 26 − H = 4 . 7 − 1 . 5 = 3 . 2. The messages are redundant , i.e., not all the n messages are legal, or not all In Caesar’s cipher (26 possible shifts), the unicity distance is thus have the same probabilities. N = H ( K ) = log 26 Each key represents a random permutation of the letters, each with probability = 1 . 5 3 . 2 3 . 2 1 /n !. where H ( K ) represents the key size in bits. In a substitution cipher N = H ( K ) = log 26! = 88 . 4 3 . 2 = 27 . 6 3 . 2 3 . 2 In a uniformly random letter distribution, whose frequencies are as in English, D = 4 . 7 − 4 = 0 . 7 and the unicity distances would be 7 and 126, respectively. � Eli Biham - May 3, 2005 c 66 Shannon’s Theory of Secrecy Systems (2) � Eli Biham - May 3, 2005 c 67 Shannon’s Theory of Secrecy Systems (2) †•
Recommend
More recommend