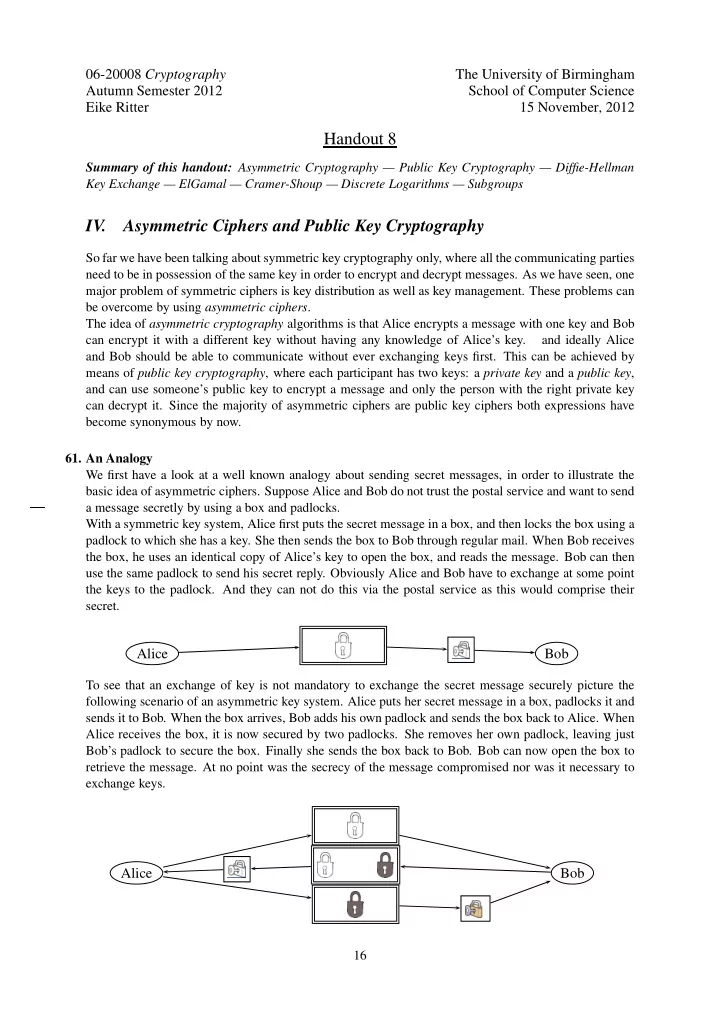

06-20008 Cryptography The University of Birmingham Autumn Semester 2012 School of Computer Science Eike Ritter 15 November, 2012 Handout 8 Summary of this handout: Asymmetric Cryptography — Public Key Cryptography — Diffie-Hellman Key Exchange — ElGamal — Cramer-Shoup — Discrete Logarithms — Subgroups IV. Asymmetric Ciphers and Public Key Cryptography So far we have been talking about symmetric key cryptography only, where all the communicating parties need to be in possession of the same key in order to encrypt and decrypt messages. As we have seen, one major problem of symmetric ciphers is key distribution as well as key management. These problems can be overcome by using asymmetric ciphers . The idea of asymmetric cryptography algorithms is that Alice encrypts a message with one key and Bob can encrypt it with a different key without having any knowledge of Alice’s key. and ideally Alice and Bob should be able to communicate without ever exchanging keys first. This can be achieved by means of public key cryptography , where each participant has two keys: a private key and a public key , and can use someone’s public key to encrypt a message and only the person with the right private key can decrypt it. Since the majority of asymmetric ciphers are public key ciphers both expressions have become synonymous by now. 61. An Analogy We first have a look at a well known analogy about sending secret messages, in order to illustrate the basic idea of asymmetric ciphers. Suppose Alice and Bob do not trust the postal service and want to send a message secretly by using a box and padlocks. With a symmetric key system, Alice first puts the secret message in a box, and then locks the box using a padlock to which she has a key. She then sends the box to Bob through regular mail. When Bob receives the box, he uses an identical copy of Alice’s key to open the box, and reads the message. Bob can then use the same padlock to send his secret reply. Obviously Alice and Bob have to exchange at some point the keys to the padlock. And they can not do this via the postal service as this would comprise their secret. Alice Bob To see that an exchange of key is not mandatory to exchange the secret message securely picture the following scenario of an asymmetric key system. Alice puts her secret message in a box, padlocks it and sends it to Bob. When the box arrives, Bob adds his own padlock and sends the box back to Alice. When Alice receives the box, it is now secured by two padlocks. She removes her own padlock, leaving just Bob’s padlock to secure the box. Finally she sends the box back to Bob. Bob can now open the box to retrieve the message. At no point was the secrecy of the message compromised nor was it necessary to exchange keys. Alice Bob 16
Finally in an public key system the exchange of messages is even easier. Again Bob and Alice have separate padlocks. Firstly, Alice asks Bob to send his open padlock to her through regular mail, keeping its key to himself. When Alice receives it she uses it to lock a box containing her message, and sends the locked box to Bob. Bob can then unlock the box with his key and read the message from Alice. To reply, Bob must similarly get Alice’s open padlock to lock the box before sending it back to her. Again no keys had to be exchanged. However, it is crucial now that nobody is able to forge a copy of Bob’s key given Bob’s padlock alone. Alice Bob 62. A Formal View Let us put the two last cases in the the above analogy into our formal cipher notation. The operations of padlocks and keys correspond to the operations of a cipher. I.e., closing the padlock is encryption and opening the padlock is decryption. We first consider the general asymmetric case with the two padlocks. We have two ciphers ( E A , D A ) and ( E B , D B ) , where A, B are Alice’s and Bob’s keys, respectively. We get the following chain of messages: E A ( M ) → E B ( E A ( M )) → D A ( E B ( E A ( M ))) = E B ( M ) → D B ( E B ( M )) = M The crucial point here is the equation D A ( E B ( E A ( M ))) = E B ( M ) . This will only hold if we have encryption functions E B and E A that commute (or if D A and E B commute). We know from our sym- metric ciphers, that this property does in general not hold. So in order to make the asymmetric scenario work, one has to carefully design the encryption functions. Now consider the public key scenario. Let � B be the key Bob sends to Alice (open padlock in our analogy). We will call � B a public key . Let B be the key he keeps secret (the actual key for the padlock in our analogy). We will call B Bob’s private key . Then Bob makes � B public and, upon receiving a message encrypted with � B decrypts it with B : � B → E � B ( M ) → D B ( E � B ( M )) Obviously it is important for the design of the encryption function that it can be inverted with a different key. Again this is in general not possible with the symmetric ciphers we have seen so far. Moreover, it is crucial that there is no way for Eve to infer B from � B , even though she knows the basic working of the encryption and decryption scheme. This is a complication that we did not have for symmetric ciphers. In a symmetric cipher we could use essentially any key (we preferred randomly generated ones of course) and en-/decryption would work. In a public key cipher, however, the right choice of public and private key are crucial and can not be left to chance, but have to be done systematically using a generation algorithm. Hence public key ciphers consist of three important components: • A key generator G . • An encryption function E . • A decryption function D . 63. Trapdoor One-way Functions When designing functions for public key ciphers it is important that they are easy to compute given the public key but that they are invertible alone when one has knowledge of the private key. In particular the inversion should be independent from the public key. 17
We have already discussed one-way functions in point 44 in handout 7. A one-way function is a function that is easy to compute but hard to invert. We have seen their uses as hash-functions, where inversion was not only not wanted, but also in general impossible to compute. (Recall that hash functions compress arbitrary length messages to a fixed length hash value.) Thus simple one-way functions are not useful for encryption, since their decryption is nearly always impossible to compute. However, there are certain types of one-way function that are hard to invert unless some secret information, a so called trapdoor , is known. This type of function is called trapdoor one-way function or trapdoor permutation . Here are some possible candidate functions: p find x ∈ N such that g x ≡ Discrete Logarithm Problem: Let g be a generator in Z ∗ p . For h ∈ Z ∗ h (mod p ) . [ g x can be computed efficiently.] p . Given a = g x and b = g y , find c ∈ Z ∗ Diffie-Hellman Problem: Let g be a generator in Z ∗ p such that c = g xy . [Again the exponentiations can be computed efficiently.] Integer Factorisation: Let n be a large integer number. Find the prime factors of n . [Multiplying primes together is easy.] 64. A Historical Note It was a long upheld paradigm that cryptography was only possible symmetrically, i.e. with some prior exchange of a key. However, in 1976 Whitfield Diffie and Martin Hellman from Stanford published a first asymmetric key cryptosystem. It was a method of public key agreement, which came to be known as Diffie-Hellman key exchange, and was the first published practical method for establishing a shared secret key over an unprotected communications channel without using a prior shared secret. The work was influenced by Ralph Merkle’s work on public key distribution, whose technique became known as Merkle’s Puzzles, and was published in 1978. Inspired by this work, Rivest, Shamir and Adleman from MIT, invented in 1977 the first public key cipher. The authors published their work in 1978, and the algorithm appropriately came to be known as RSA. In 1997 GCHQ in the UK publicly announced that they were aware of public key cryptography several years before Diffie and Hellman published their paper. Indeed the first invention of asymmetric key algorithms was by James H. Ellis, Clifford Cocks, and Malcolm Williamson at GCHQ in the early 1970s; they invented both the Diffie-Hellman key exchange, as well as a special case of RSA. We will follow the historical order and first have a look at the Diffie-Hellman key exchange protocol before having a look at some public key ciphers. IV.1 Diffie-Hellman Key Exchange The Diffie-Hellman key exchange was invented by Wittfield Diffie and Martin Hellman in 1976. Using this protocol it is possible for Alice and Bob to agree on a secret value in the presence of Eve observing their entire communication. It is an asymmetric algorithm since there is no need for a trusted third party Trent or for the exchange of any secret information anytime before the exchange. The main idea of the protocol is to agree on a key given as an integer by using discrete exponentiation. Thus its security is based on the hardness of the discrete logarithm problem. The algorithm was originally proposed for Z ∗ p for a large prime p but is today usually used in subgroups G q of Z ∗ p . The protocol has essentially 5 steps, where the first is a public initialisation: 1. Alice and Bob agree (publicly) on a prime number p (i.e., on Z ∗ p ) and on an element g ∈ Z ∗ p that generates the the finite group G q . 2. Alice picks a random positive integer a and sends g a to Bob. 3. Bob picks a random positive integer b and sends g b to Alice. 4. Alice computes the key K = ( g b ) a = g ba . 5. Bob computes the key K = ( g a ) b = g ab . 18
Recommend
More recommend