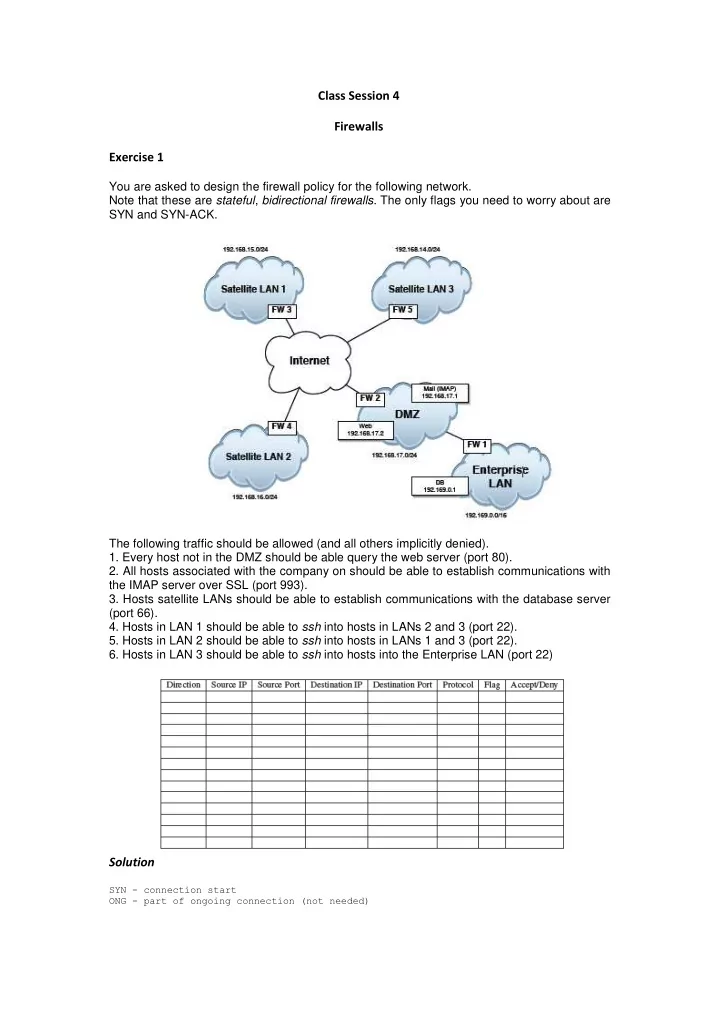

Class Session 4 Firewalls Exercise 1 You are asked to design the firewall policy for the following network. Note that these are stateful , bidirectional firewalls . The only flags you need to worry about are SYN and SYN-ACK. The following traffic should be allowed (and all others implicitly denied). 1. Every host not in the DMZ should be able query the web server (port 80). 2. All hosts associated with the company on should be able to establish communications with the IMAP server over SSL (port 993). 3. Hosts satellite LANs should be able to establish communications with the database server (port 66). 4. Hosts in LAN 1 should be able to ssh into hosts in LANs 2 and 3 (port 22). 5. Hosts in LAN 2 should be able to ssh into hosts in LANs 1 and 3 (port 22). 6. Hosts in LAN 3 should be able to ssh into hosts into the Enterprise LAN (port 22) Solution SYN - connection start ONG - part of ongoing connection (not needed)
Firewall 1: SRC IP SRC PT DST IP DST PT PROT FLAG ACCEPT/DENY 192.169.* * 192.168.17.2 80 TCP SYN Accept (1) 192.169.* * 192.168.17.2 80 TCP ONG Accept (1) 192.168.17.2 80 192.169.* * TCP Accept (1) 192.169.* * 192.168.17.1 993 TCP SYN Accept (2) 192.169.* * 192.168.17.1 993 TCP ONG Accept (2) 192.168.17.1 993 192.169.* * TCP Accept (2) 192.168.14.* * 192.169.0.1 66 TCP SYN ACCEPT (3) 192.168.14.* * 192.169.0.1 66 TCP ONG ACCEPT (3) 192.169.0.1 66 192.168.14.* * TCP ACCEPT (3) 192.168.15.* * 192.169.0.1 66 TCP SYN ACCEPT (3) 192.168.15.* * 192.169.0.1 66 TCP ONG ACCEPT (3) 192.169.0.1 66 192.168.15.* * TCP ACCEPT (3) 192.168.16.* * 192.169.0.1 66 TCP SYN ACCEPT (3) 192.168.16.* * 192.169.0.1 66 TCP ONG ACCEPT (3) 192.169.0.1 66 192.168.16.* * TCP ACCEPT (3) 192.168.14.* * 192.169.* 22 TCP SYN ACCEPT (6) 192.168.14.* * 192.169.* 22 TCP ONG ACCEPT (6) 192.169.* 22 192.168.14.* * TCP ACCEPT (6) Firewall 2: * * 192.168.17.2 80 TCP SYN ACCEPT (1) * * 192.168.17.2 80 TCP ONG ACCEPT (1) 192.168.17.2 80 * * TCP ACCEPT (1) 192.168.14.* * 192.168.17.1 993 TCP SYN ACCEPT (2) 192.168.14.* * 192.168.17.1 993 TCP ONG ACCEPT (2) 192.168.17.1 993 192.168.14.* * TCP ACCEPT (2) 192.168.15.* * 192.168.17.1 993 TCP SYN ACCEPT (2) 192.168.15.* * 192.168.17.1 993 TCP ONG ACCEPT (2) 192.168.17.1 993 192.168.15.* * TCP ACCEPT (2) 192.168.16.* * 192.168.17.1 993 TCP SYN ACCEPT (2) 192.168.16.* * 192.168.17.1 993 TCP ONG ACCEPT (2) 192.168.17.1 993 192.168.16.* * TCP ACCEPT (2) 192.169.* * 192.168.17.1 993 TCP SYN ACCEPT (2) 192.169.* * 192.168.17.1 993 TCP ONG ACCEPT (2) 192.168.17.1 993 192.169.* * TCP ACCEPT (2) 192.168.14.* * 192.169.0.1 66 TCP SYN ACCEPT (3) 192.168.14.* * 192.169.0.1 66 TCP ONG ACCEPT (3) 192.169.0.1 66 192.168.14.* * TCP ACCEPT (3) 192.168.15.* * 192.169.0.1 66 TCP SYN ACCEPT (3) 192.168.15.* * 192.169.0.1 66 TCP ONG ACCEPT (3) 192.169.0.1 66 192.168.15.* * TCP ACCEPT (3) 192.168.16.* * 192.169.0.1 66 TCP SYN ACCEPT (3) 192.168.16.* * 192.169.0.1 66 TCP ONG ACCEPT (3) 192.169.0.1 66 192.168.16.* * TCP ACCEPT (3) 192.168.14.* * 192.169.* 22 TCP SYN ACCEPT (6) 192.168.14.* * 192.169.* 22 TCP ONG ACCEPT (6) 192.169.* 22 192.168.14.* * TCP ACCEPT (6) Firewall 3: SRC IP SRC PT DST IP DST PT PROT FLAG ACCEPT/DENY 192.168.15.* * 192.168.17.2 80 TCP SYN ACCEPT (1) 192.168.15.* * 192.168.17.2 80 TCP ONG ACCEPT (1) 192.168.17.2 80 192.168.15.* * TCP ACCEPT (1) 192.168.15.* * 192.168.17.1 993 TCP SYN ACCEPT (2)
192.168.15.* * 192.168.17.1 993 TCP ONG ACCEPT (2) 192.168.17.1 993 192.168.15.* * TCP ACCEPT (2) 192.168.15.* * 192.169.0.1 66 TCP SYN ACCEPT (3) 192.168.15.* * 192.169.0.1 66 TCP ONG ACCEPT (3) 192.169.0.1 66 192.168.15.* * TCP ACCEPT (3) 192.168.15.* * 192.168.14.* 22 TCP SYN ACCEPT (4) 192.168.15.* * 192.168.14.* 22 TCP ONG ACCEPT (4) 192.168.14.* 22 192.168.15.* * TCP ACCEPT (4) 192.168.15.* * 192.168.16.* 22 TCP SYN ACCEPT (4) 192.168.15.* * 192.168.16.* 22 TCP ONG ACCEPT (4) 192.168.16.* 22 192.168.15.* * TCP ACCEPT (4) 192.168.16.* * 192.168.15.* 22 TCP SYN ACCEPT (5) 192.168.16.* * 192.168.15.* 22 TCP ONG ACCEPT (5) 192.168.15.* 22 192.168.16.* * TCP ACCEPT (5) Firewall 4: SRC IP SRC PT DST IP DST PT PROT FLAG ACCEPT/DENY 192.168.16.* * 192.168.17.2 80 TCP SYN ACCEPT (1) 192.168.16.* * 192.168.17.2 80 TCP ONG ACCEPT (1) 192.168.17.2 80 192.168.15.* * TCP ACCEPT (1) 192.168.16.* * 192.168.17.1 993 TCP SYN ACCEPT (2) 192.168.16.* * 192.168.17.1 993 TCP ONG ACCEPT (2) 192.168.17.1 993 192.168.15.* * TCP ACCEPT (2) 192.168.16.* * 192.169.0.1 66 TCP SYN ACCEPT (3) 192.168.16.* * 192.169.0.1 66 TCP ONG ACCEPT (3) 192.169.0.1 66 192.168.16.* * TCP ACCEPT (3) 192.168.15.* * 192.168.16.* 22 TCP SYN ACCEPT (4) 192.168.15.* * 192.168.16.* 22 TCP ONG ACCEPT (4) 192.168.16.* 22 192.168.15.* * TCP ACCEPT (4) 192.168.16.* * 192.168.14.* 22 TCP SYN ACCEPT (5) 192.168.16.* * 192.168.14.* 22 TCP ONG ACCEPT (5) 192.168.14.* 22 192.168.16.* * TCP ACCEPT (5) 192.168.16.* * 192.168.15.* 22 TCP SYN ACCEPT (5) 192.168.16.* * 192.168.15.* 22 TCP ONG ACCEPT (5) 192.168.15.* 22 192.168.16.* * TCP ACCEPT (5) Firewall 5: SRC IP SRC PT DST IP DST PT PROT FLAG ACCEPT/DENY 192.168.14.* * 192.168.17.2 80 TCP SYN ACCEPT (1) 192.168.14.* * 192.168.17.2 80 TCP ONG ACCEPT (1) 192.168.17.2 80 192.168.15.* * TCP ACCEPT (1) 192.168.14.* * 192.168.17.1 993 TCP SYN ACCEPT (2) 192.168.14.* * 192.168.17.1 993 TCP ONG ACCEPT (2) 192.168.17.1 993 192.168.15.* * TCP ACCEPT (2) 192.168.14.* * 192.169.0.1 66 TCP SYN ACCEPT (3) 192.168.14.* * 192.169.0.1 66 TCP ONG ACCEPT (3) 192.169.0.1 66 192.168.13.* * TCP ACCEPT (3) 192.168.15.* * 192.168.14.* 22 TCP SYN ACCEPT (4) 192.168.15.* * 192.168.14.* 22 TCP ONG ACCEPT (4) 192.168.14.* 22 192.168.15.* * TCP ACCEPT (4) 192.168.16.* * 192.168.16.* 22 TCP SYN ACCEPT (5) 192.168.16.* * 192.168.16.* 22 TCP ONG ACCEPT (5) 192.168.14.* 22 192.168.15.* * TCP ACCEPT (5) 192.168.14.* * 192.169.* 22 TCP SYN ACCEPT (6) 192.168.14.* * 192.169.* 22 TCP ONG ACCEPT (6) 192.169.* 22 192.168.14.* * TCP ACCEPT (6)
Recommend
More recommend