Administrivia AdvancedTopicsin - PDF document
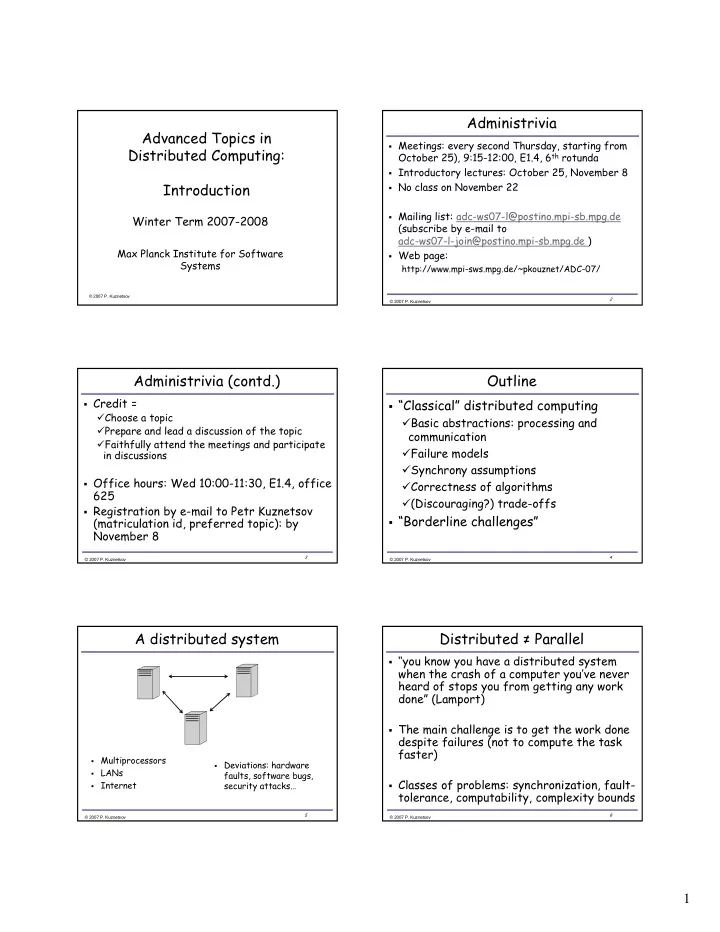
Administrivia AdvancedTopicsin Meetings:everysecondThursday,startingfrom DistributedComputing: October25),9:1512:00,E1.4,6 th rotunda
Administrivia Advanced�Topics�in� � Meetings:�every�second�Thursday,�starting�from� Distributed�Computing: October�25),�9:15�12:00,�E1.4,�6 th rotunda � Introductory�lectures:�October�25,�November�8�� Introduction � No�class�on�November�22 � Mailing�list:�adc�ws07�l@postino.mpi�sb.mpg.de� Winter�Term�2007�2008 (subscribe�by�e�mail�to���������������������������������������������� adc�ws07�l�join@postino.mpi�sb.mpg.de�) Max�Planck�Institute�for�Software� � Web�page:� Systems http://www.mpi�sws.mpg.de/~pkouznet/ADC�07/ � ����������������� � � ����������������� Administrivia (contd.) Outline � Credit�=� � “Classical” distributed�computing� � Choose�a�topic � Basic�abstractions:�processing�and� � Prepare�and�lead�a�discussion�of�the�topic� communication � Faithfully�attend�the�meetings�and�participate� � Failure�models in�discussions � Synchrony�assumptions � Office�hours:�Wed�10:00�11:30,�E1.4,�office� � Correctness�of�algorithms 625� � (Discouraging?)�trade�offs � Registration�by�e�mail�to�Petr�Kuznetsov � “Borderline�challenges” (matriculation�id,�preferred�topic):�by� November�8 � � � ����������������� � ����������������� A�distributed�system Distributed�≠ Parallel � ‘‘you�know�you�have�a�distributed�system� when�the�crash�of�a�computer�you’ve�never� heard�of�stops�you�from�getting�any�work� done” (Lamport) � The�main�challenge�is�to�get�the�work�done� despite�failures�(not�to�compute�the�task� faster) � Multiprocessors � Deviations:�hardware� � LANs faults,�software�bugs,� � Classes�of�problems:�synchronization,�fault� � Internet security�attacks… tolerance,�computability,�complexity�bounds � � � ����������������� � ����������������� 1
History Basic�abstractions � Process abstraction�– an�independent� � Dining�philosophers,�mutual�exclusion� (Dijkstra )~60’s thread�of�computation � Distributed�computing,�logical�clocks� (Lamport),�distributed�transactions�(Gray)� � Communication�abstractions� ~70’s � Message�passing:� channels � Consensus�(Lynch)�~80’s � Shared�memory:� objects � Distributed�programming�models,�systems,� since�~90’s � � � ����������������� � ����������������� Processes Failure�models:�processing � Automaton�Pi� Process�is� correct if�it�follows�its�algorithm� ����������� (i=1,...,N):� �������� ��������� � States � Processing�failures �� � Inputs � Byzantine � Outputs ��������� ������ � Omission � Sequential� �������������� � Crashes �������������� specification� ����� ����� � Crash�recoveries Algorithm�=�{P 1 ,…,P N } � �� � ����������������� � ����������������� Byzantine�failure�model Omission�failure�model � Arbitrary�deviations: � Viruses � A�process�fails�to�send�or�receive�a� message�(send/receive�omission) � Software�bugs � Unanticipated�malicious�attacks � Send/receive�buffer�overflows � Difficult�to�handle,�typical�assumptions: � Failures�not�correlated � Less�than�one�third�of�the�processes�can�fail �� �� � ����������������� � ����������������� 2
Crash�failure�model Failure�models:�communication A�process�crashes�=�prematurely�stops�taking� � Link�losses steps � Fair�loss�channels:��every�message�re�sent� sufficiently�many�times�is�eventually�delivered � Models�“benign” hardware�errors� � Reliable�channels:�every�message�sent�by�a� � Typically�an�upper�bound�f�on�the�number� correct�process�to�a�correct�process�is� of�crashes�is�assumed: eventually�delivered� � At�most�a�minority�of�the�processes�can�crash � Duplication/creation�in�links� � At�least�one�process�is�correct� � Faulty�shared�objects �� �� � ����������������� � ����������������� Synchrony�assumptions Synchronous�system Can�be�quantified�using� processing�bound Φ The�bounds�∆ and�Φ exist�and�are�known and� communication�bound ∆ (≈there�are� known� upper�and�lower�bounds�on� � While�a�process�takes�Φ local�steps ,�every� time�to�execute�a�step�and�to�transmit�a� correct�process�takes�at�least�one�step� message) � Every�sent�message�takes�at�most�∆ local� steps to�be�delivered To�model�systems�with�highly�predictable� stable�timing�bounds �� �� � ����������������� � ����������������� Partially�synchronous�system Asynchronous�system The�bounds�∆ and�Φ exist�but�are�not�known The�bounds�might�not�exist. (≈there�are� unknown� bounds�on�time�to� (≈ it�can�take�arbitrarily�long�to�take�a�step� execute�a�step�and�to�transmit�a�message) of�computation�and�to�communicate) To�model�systems�with�unpredictable�but� To�model�unpredictable�systems:�no�global� stable�timing�bounds time,�only�causality �� �� � ����������������� � ����������������� 3
Problem�specification Fundamental�trade�offs � Safety� properties�≈ nothing�bad�happens � Availability�vs.�Consistency � State�machine�replication:�strong�consistency,� Can�only�be�violated�in�a�finite�execution,�e.g.,�by� likely�unavailable producing�a�wrong�output�or�sending�an� � Distributed�Hash�Tables�(DHTs):��best�effort� incorrect�message consistency,�always�responsive� � Liveness properties�≈ something�good� � Time�vs.�space�complexity eventually�happens � Shared�memory�implementations Can�only�be�violated�in�an infinite� execution,�e.g., � Routing�at�a�scale by�never�producing�an�expected�output � … � Cost�vs.�benefit �� �� � ����������������� � ����������������� “Borderline” topics “Borderline” topics�(contd.) IV.�Multiprocessor�synchronization�with� I.�Security STMs (vs.�locks) � systems�should�not�“leak” information� � access�concurrent�objects�with�(light�weight)� II.�Games transactions � set�the�rules�and�prevent�deviations� � boost�progress�with�contention�managers III.�Networks V.�Formal�models � transmit�a�message�reliably�(and�securely)� � I/O�automata despite�node�and�link�failures � Temporal�logic � overcome�failures�in�wireless�networks VI.�Systems � compute�an�aggregate�value�from�a�large�group� � Byzantine�Fault�Tolerance of�“weak” sensors � P2P:�key�based�routing�and�DHTs �� �� � ����������������� � ����������������� Problem�statement I.1�Secure�multi�party�computation � n�players�p 0 ,…,�p n�1 ,�each�p i possessing�an� input�value�x i � How�to�compute�the�average�salary�in�a� � a�(probabilistic)�function�f(x 0 ,…,x n�1 ) group�without�anyone�learning�the�salary�of� anyone�else? � Every�player�computes�the�value�of� � Alice�and�Bob�want�to�know�who�is�older� f(x 0 ,…,x n�1 )�without�learning�any� without�revealing�their�ages information�on�the�inputs� extra�to�the� computed�value f(…)�can�be�defined�in�a�fault�tolerant�way �� �� � ����������������� � ����������������� 4
Recommend
More recommend
Explore More Topics
Stay informed with curated content and fresh updates.