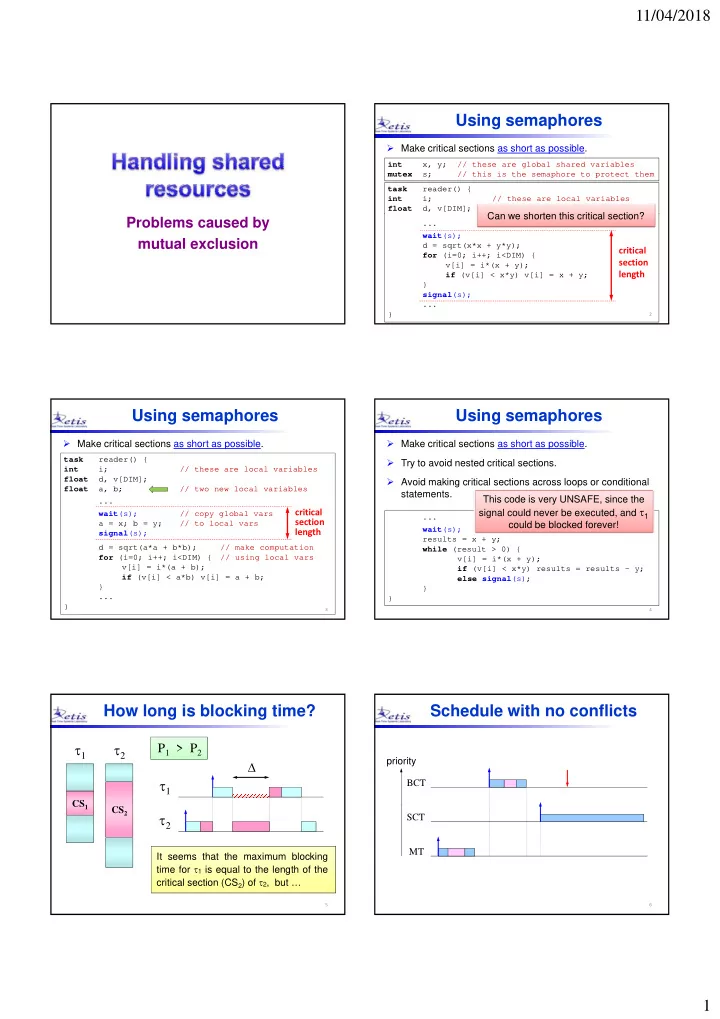

11/04/2018 Using semaphores Make critical sections as short as possible. int x, y; // these are global shared variables mutex s; // this is the semaphore to protect them task reader() { i; // these are local variables int d, v[DIM]; float Can we shorten this critical section? C h t thi iti l ti ? Problems caused by ... wait (s); mutual exclusion d = sqrt(x*x + y*y); critical for (i=0; i++; i<DIM) { section v[i] = i*(x + y); length if (v[i] < x*y) v[i] = x + y; } signal (s); ... } 2 Using semaphores Using semaphores Make critical sections as short as possible. Make critical sections as short as possible. task reader() { Try to avoid nested critical sections. int i; // these are local variables float d, v[DIM]; Avoid making critical sections across loops or conditional a, b; // two new local variables float statements. This code is very UNSAFE, since the ... signal could never be executed, and 1 critical i i l i l ld b t d d wait (s); // copy global vars ... section a = x; b = y; // to local vars could be blocked forever! wait (s); length signal (s); results = x + y; d = sqrt(a*a + b*b); // make computation while (result > 0) { for (i=0; i++; i<DIM) { // using local vars v[i] = i*(x + y); v[i] = i*(a + b); if (v[i] < x*y) results = results - y; if (v[i] < a*b) v[i] = a + b; else signal (s); } } ... } } 3 4 How long is blocking time? Schedule with no conflicts 1 2 P 1 > P 2 priority 1 BCT CS 1 CS CS 2 2 SCT MT It seems that the maximum blocking time for 1 is equal to the length of the critical section (CS 2 ) of 2 , but … 5 6 1
11/04/2018 Conflict on a critical section Conflict on a critical section priority priority B B BCT BCT SCT SCT MT MT 7 8 Priority Inversion Protocol key aspects Access Rule: Decides whether to block and when. A high priority task is blocked by a lower priority Progress Rule: Decides how to execute inside a critical task a for an unbounded interval of time section. Release Rule: R l R l D Decides id how h to t order d the th pending di Solution requests of the blocked tasks. Introduce a concurrency control protocol for Other aspects accessing critical sections. Analysis: estimates the worst-case blocking times. Implementation: finds the simplest way to encode the protocol rules. 9 10 Rules for classical semaphores Resource Access Protocols The following rules are normally used for classical semaphores: Classical semaphores (No protocol) Access Rule (Decides whether to block and when): Non Preemptive Protocol ( NPP ) Enter a critical section if the resource is free, block if the resource is locked. Highest Locker Priority ( HLP ) Progress Rule (Decides how to execute in a critical section): Priority Inheritance Protocol ( PIP ) Execute the critical section with the nominal priority. Priority Ceiling Protocol ( PCP ) Release Rule (Decides how to order pending requests): Stack Resource Policy ( SRP ) Wake up the blocked task in FIFO order. Wake up the blocked task with the highest priority. 11 12 2
11/04/2018 Assumption Non Preemptive Protocol Critical sections are correctly accessed by tasks: Access Rule: A task never blocks at the entrance of a critical section, but at its activation time. wait(S A ) wait(S A ) Progress Rule: Disable preemption when executing inside wait(S B ) wait(S ) a critical section. a critical section wait(S B ) signal(S A ) Release Rule: At exit, enable preemption so that the resource is assigned to the pending task signal(S B ) with the highest priority. signal(S B ) signal(S A ) 13 14 Conflict on a critical section NPP: example (using classical semaphores) B priority priority B 1 1 2 2 3 3 15 16 NPP: implementation notes NPP: pro & cons Each task i must be assigned two priorities: ADVANTAGES: simplicity and efficiency. Semaphores queues are not needed, because tasks a nominal priority P i (fixed) assigned by the application developer; never block on a wait(s). Each task can block at most on a single critical section. a dynamic priority p i (initialized to P i ) used to schedule the It prevents deadlocks and allows stack sharing. It prevents deadlocks and allows stack sharing task and affected by the protocol. task and affected by the protocol It is transparent to the programmer. Then, the protocol can be implemented by changing the behavior of the wait and signal primitives: PROBLEMS: 1. Tasks may block even if they do not use resources. wait(s): p i = max( P 1 , …, P n ) 2. Since tasks are blocked at activation, blocking could be signal(s): p i = P i unnecessary (pessimistic assumption). 17 18 3
11/04/2018 NPP: problem 1 NPP: problem 2 Long critical sections delay all high priority tasks: A task could block even if not accessing a critical section: B 1 B 1 is useless: 2 1 1 blocks just in case ... priority 1 cannot preempt, 1 although it could! 1 test B B 2 2 2 CS CS 3 p 2 P max Priority assigned to i p i = P max = max( P 1 , …, P n ) P 2 inside critical sections: 19 20 Highest Locker Priority HLP: example 2 is blocked, but priority 1 can preempt 1 Access Rule: A task never blocks at the entrance of a critical section, but at its activation time. B 2 2 Progress Rule: Inside resource R, a task executes at the highest priority of the tasks that use R. 3 p 3 Release Rule: At exit, the dynamic priority of the task is P 2 reset to its nominal priority P i . P 3 Priority assigned to i p i (R) = max { P j | j uses R } inside a resource R: 21 22 HLP: implementation notes HLP: pro & cons Each task i is assigned a nominal priority P i and a ADVANTAGES: simplicity and efficiency. dynamic priority p i . Semaphores queues are not needed, because tasks Each semaphore S is assigned a resource ceiling C(S) : never block on a wait(s). C(S) = max { P i | i uses S } Each task can block at most on a single critical section. It prevents deadlocks It prevents deadlocks. Then, the protocol can be implemented by changing the It allows stack sharing. behavior of the wait and signal primitives: wait(S): p i = C(S) PROBLEMS: signal(S): p i = P i Since tasks are blocked at activation, blocking could be unnecessary (same pessimism as for NPP). Note : HLP is also known as Immediate Priority Ceiling ( IPC ). It is not transparent to programmers (due to ceilings). 23 24 4
11/04/2018 Priority Inheritance Protocol PIP: example priority Access Rule: A task blocks at the entrance of a critical direct blocking 1 section if the resource is locked. push-through blocking Progress Rule: Inside resource R, a task executes with the 2 highest priority of the tasks blocked on R. 3 inherits the priority of 1 3 Release Rule: At exit, the dynamic priority of the task is reset to its nominal priority P i . P 1 P 3 26 25 PIP: types of blocking PIP: implementation notes Inside a resource R the dynamic priority p i is set as Direct blocking p i (R) = max { P h | h blocked on R } A task blocks on a locked semaphore wait(s): if (s == 0) { Indirect blocking (Push-through blocking) <suspend the calling task exe in the semaphore queue> <find the task k that is locking the semaphore s> A task blocks because a lower priority task inherited A task blocks because a lower priority task inherited p = P p k = P exe // priority inheritance // priority inheritance a higher priority. <call the scheduler> } else s = 0; BLOCKING: signal(s): if (there are blocked tasks) { <awake the highest priority task in the semaphore queue> a delay caused by lower priority tasks p exe = P exe <call the scheduler> } else s = 1; 27 28 Identifying blocking resources Identifying blocking resources Under PIP, a task i can be blocked on a semaphore Lemma 1: A task i can be blocked at most S k only if: once by a lower priority task. 1. S k is directly shared between i and lower priority tasks (direct blocking) If there are n i tasks with priority lower than i , OR then i can be blocked at most at most n i times, 2. S k is shared between tasks with priority lower independently of the number of critical sections than i and tasks having priority higher than i that can block i . (push-through blocking). 29 30 5
Recommend
More recommend