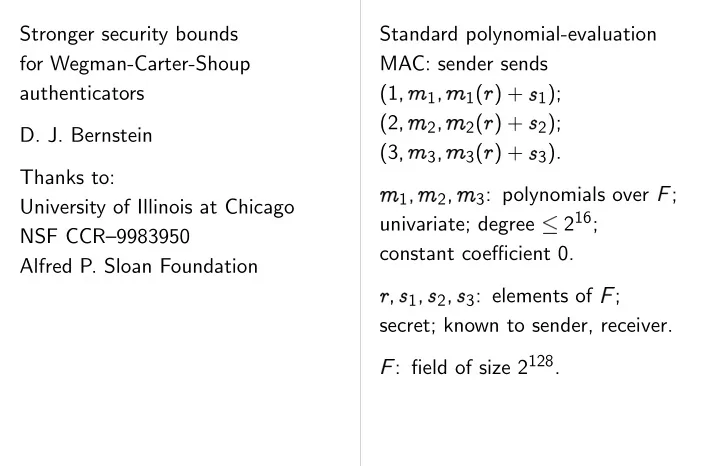

� � � � � ✁ � � � � � � Stronger security bounds Standard polynomial-evaluation for Wegman-Carter-Shoup MAC: sender sends ✁ ) + authenticators (1 1 ( ✂ 1 ); 1 ✁ ) + (2 2 ( ✂ 2 ); 2 D. J. Bernstein ✁ ) + (3 3 ( ✂ 3 ). 3 Thanks to: 3 : polynomials over ; 1 2 University of Illinois at Chicago 2 16 ; univariate; degree NSF CCR–9983950 constant coefficient 0. Alfred P. Sloan Foundation ✂ 3 : elements of ; ✂ 1 ✂ 2 secret; known to sender, receiver. : field of size 2 128 .
� � � � � � � ✁ � � � � � ✂ � ✂ � � � ✁ bounds Standard polynomial-evaluation Wegman-Carter version: rter-Shoup MAC: sender sends ( ✂ 3 ) is a unifo ✂ 1 ✂ 2 ✁ ) + (1 1 ( ✂ 1 ); random element of 1 ✁ ) + 2 512 possibilities, (2 2 ( ✂ 2 ); 2 ✁ ) + (3 3 ( ✂ 3 ). each equally likely. 3 3 : polynomials over ; Wegman-Carter-Shoup 1 2 Illinois at Chicago 2 16 ; univariate; degree ✂ 1 = ✂ 2 ; ✂ 1 = ✂ 3 ; CCR–9983950 constant coefficient 0. otherwise uniform. Foundation 2 256 (2 128 1)(2 128 ✂ 3 : elements of ; ✂ 1 ✂ 2 possibilities, each equally secret; known to sender, receiver. How secure are these : field of size 2 128 .
� � � � ✁ � � � ✁ � � � � � � � � � Standard polynomial-evaluation Wegman-Carter version: MAC: sender sends ( ✂ 3 ) is a uniform ✂ 1 ✂ 2 ✁ ) + 4 . (1 1 ( ✂ 1 ); random element of 1 ✁ ) + 2 512 possibilities, (2 2 ( ✂ 2 ); 2 ✁ ) + (3 3 ( ✂ 3 ). each equally likely. 3 3 : polynomials over ; Wegman-Carter-Shoup version: 1 2 2 16 ; univariate; degree ✂ 1 = ✂ 2 ; ✂ 1 = ✂ 3 ; ✂ 2 = ✂ 3 ; constant coefficient 0. otherwise uniform. 2 256 (2 128 1)(2 128 2) ✂ 3 : elements of ; ✂ 1 ✂ 2 possibilities, each equally likely. secret; known to sender, receiver. How secure are these MACs? : field of size 2 128 .
✁ � � ✂ � ✂ ✁ � � � � � ✁ � � � � � ✁ ✁ ✂ ✁ � � � � ✁ � � � ✁ � � ✂ ✁ ✂ � � � ✁ � � � olynomial-evaluation Wegman-Carter version: Standard security b sends ( ✂ 3 ) is a uniform for Wegman-Carter: ✂ 1 ✂ 2 4 . ✂ 1 ); random element of “Authenticators reveal 2 512 possibilities, ✂ 2 ); no information about ✂ 3 ). each equally likely. Conditional distribution olynomials over ; Wegman-Carter-Shoup version: � 1 ), (2 given (1 1 2 16 ; degree ✂ 1 = ✂ 2 ; ✂ 1 = ✂ 3 ; ✂ 2 = ✂ 3 ; � 3 ), is unifo (3 3 efficient 0. otherwise uniform. There are 2 128 possible 2 256 (2 128 1)(2 128 2) elements of ; each consistent with possibilities, each equally likely. sender, receiver. unique choice of How secure are these MACs? ✁ ), � 2 128 . ✂ 2 = 2 (
� � ✁ � � � � � � � � � � � � Wegman-Carter version: Standard security bounds ( ✂ 3 ) is a uniform for Wegman-Carter: ✂ 1 ✂ 2 4 . random element of “Authenticators reveal 2 512 possibilities, ✁ .” no information about each equally likely. ✁ , Conditional distribution of Wegman-Carter-Shoup version: � 1 ), (2 � 2 ), given (1 1 2 ✂ 1 = ✂ 2 ; ✂ 1 = ✂ 3 ; ✂ 2 = ✂ 3 ; � 3 ), is uniform. (3 3 otherwise uniform. ✁ ’s, There are 2 128 possible 2 256 (2 128 1)(2 128 2) each consistent with a possibilities, each equally likely. ✁ ), � 1 unique choice of ✂ 1 = 1 ( How secure are these MACs? ✁ ), ✁ ). � 2 � 3 ✂ 2 = 2 ( ✂ 3 = 3 (
� ✁ � � � � � � � � � � � � ✁ � ✂ � � � ✂ � ✂ � ✂ � ✂ � � � ✁ ✂ ✂ � version: Standard security bounds Say attacker attempts � ) with a uniform for Wegman-Carter: (1 = 4 . of (0) = 0; degree “Authenticators reveal ossibilities, ✁ .” no information about Forgery is successful ely. � = ✁ ) + ( ✁ , ✂ 1 Conditional distribution of � = ✁ ) + � 1 rter-Shoup version: ( � 1 ), (2 � 2 ), given (1 1 2 ; ✂ 2 = ✂ 3 ; is a root of � 3 ), is uniform. (3 3 rm. � 1 1 + ✁ ’s, There are 2 128 possible 128 2) polynomial of degree each consistent with a each equally likely. 2 16 roots. so it has ✁ ), � 1 unique choice of ✂ 1 = 1 ( these MACs? ✁ ), ✁ ). � 2 � 3 ✂ 2 = 2 ( ✂ 3 = 3 ( Attempted forgery 2 16 2 128 chance
� � � � � � � � � � � � ✁ � � � � � Standard security bounds Say attacker attempts forgery � ) with for Wegman-Carter: (1 = 1 ; 2 16 . (0) = 0; degree “Authenticators reveal ✁ .” no information about Forgery is successful � = ✁ ) + ( ✁ , ✂ 1 Conditional distribution of � = ✁ ) + ✁ ) � 1 ( 1 ( � 1 ), (2 � 2 ), given (1 � . 1 2 � 1 is a root of 1 + � 3 ), is uniform. (3 3 � 1 1 + is a nonzero ✁ ’s, There are 2 128 possible 2 16 polynomial of degree each consistent with a 2 16 roots. so it has ✁ ), � 1 unique choice of ✂ 1 = 1 ( ✁ ), ✁ ). � 2 � 3 ✂ 2 = 2 ( ✂ 3 = 3 ( Attempted forgery has 2 16 2 128 chance of success.
� � � � � ✂ � � ✁ � � � � � � � � � � � ✁ � � y bounds Say attacker attempts forgery Original security bounds � ) with rter: (1 = 1 ; for Wegman-Carter-Shoup: 2 16 . (0) = 0; degree “Authenticators reveal reveal very little information ✁ .” about Forgery is successful (1996 Shoup) � = ✁ ) + ( ✁ , ✂ 1 distribution of � = ✁ ) + ✁ ) � 1 ( 1 ( Stronger security b � 2 ), ), (2 � . 2 � 1 is a root of 1 + for Wegman-Carter-Shoup: uniform. “Wegman-Carter-Shoup � 1 1 + is a nonzero ✁ ’s, ossible identical to Wegman-Ca 2 16 polynomial of degree with a (bounds, 2004.10 Bernstein; 2 16 roots. so it has ✁ ), � 1 ✂ 1 = 1 ( this proof, 2005.03 ✁ ), ✁ ). � 3 ✂ 3 = 3 ( Attempted forgery has Warning: carelessness 2 16 2 128 chance of success. weaker (“game-pla
� � � � � � � ✁ � Say attacker attempts forgery Original security bounds � ) with (1 = 1 ; for Wegman-Carter-Shoup: 2 16 . (0) = 0; degree “Authenticators reveal ✁ .” very little information about Forgery is successful (1996 Shoup) � = ✁ ) + ( ✂ 1 � = ✁ ) + ✁ ) � 1 ( 1 ( Stronger security bounds � . � 1 is a root of 1 + for Wegman-Carter-Shoup: “Wegman-Carter-Shoup is almost � 1 1 + is a nonzero identical to Wegman-Carter.” 2 16 polynomial of degree (bounds, 2004.10 Bernstein; 2 16 roots. so it has this proof, 2005.03 Bernstein) Attempted forgery has Warning: carelessness leads to 2 16 2 128 chance of success. weaker (“game-playing”) bounds.
� � � � � � � � ✂ � � ✁ � � � ✁ ✁ � ✂ ✁ � � ✁ ✂ � ✁ � � ✂ attempts forgery Original security bounds Fix a deterministic = 1 ; for Wegman-Carter-Shoup: generates 1 ; sees 2 16 . degree “Authenticators reveal generates 2 ; sees ✁ .” very little information about generates 3 ; sees successful (1996 Shoup) generates forgery attempt � ) with ( ✁ ) 1 ( Stronger security bounds = ✁ , (0) = � . � 1 1 + for Wegman-Carter-Shoup: “Wegman-Carter-Shoup is almost (Generalizations: randomized is a nonzero identical to Wegman-Carter.” variable # of chosen 2 16 degree (bounds, 2004.10 Bernstein; arbitrary order of nonces; roots. this proof, 2005.03 Bernstein) variable # of forgery rgery has Warning: carelessness leads to chance of success. weaker (“game-playing”) bounds.
� � � � Original security bounds Fix a deterministic attack that ✁ ) + for Wegman-Carter-Shoup: generates 1 ; sees 1 ( ✂ 1 ; ✁ ) + “Authenticators reveal generates 2 ; sees 2 ( ✂ 2 ; ✁ .” ✁ ) + very little information about generates 3 ; sees 3 ( ✂ 3 ; (1996 Shoup) generates forgery attempt � ) with � 2 � 3 , ( 1 Stronger security bounds 2 16 . = ✁ , (0) = 0, deg for Wegman-Carter-Shoup: “Wegman-Carter-Shoup is almost (Generalizations: randomized ; identical to Wegman-Carter.” variable # of chosen messages; (bounds, 2004.10 Bernstein; arbitrary order of nonces; this proof, 2005.03 Bernstein) variable # of forgery attempts.) Warning: carelessness leads to weaker (“game-playing”) bounds.
✂ � � ✂ ✂ � � ✁ ✂ � � ✂ � � bounds Fix a deterministic attack that Apply to Wegman-Ca ✁ ) + rter-Shoup: generates 1 ; sees 1 ( ✂ 1 ; � = ✁ ) + Pr[ ( ✁ ] ✁ ) + reveal generates 2 ; sees 2 ( ✂ 2 ; Proved this earlier. ✁ .” ✁ ) + rmation about generates 3 ; sees 3 ( ✂ 3 ; 3 : For each generates forgery attempt � ) with conditional probabilit � 2 � 3 , ( 1 bounds � = ✁ ) + that ( 2 16 . = ✁ , (0) = 0, deg rter-Shoup: given that ( ✂ 1 ✂ 2 rter-Shoup is almost (Generalizations: randomized ; � = ✁ ) + Pr[ ( ✁ ] egman-Carter.” variable # of chosen messages; = Pr[( 2004.10 Bernstein; arbitrary order of nonces; ✂ 1 ✂ 2 � 384 ( ). = 2 2005.03 Bernstein) variable # of forgery attempts.) � 384 ( Thus 2 relessness leads to (“game-playing”) bounds.
Recommend
More recommend