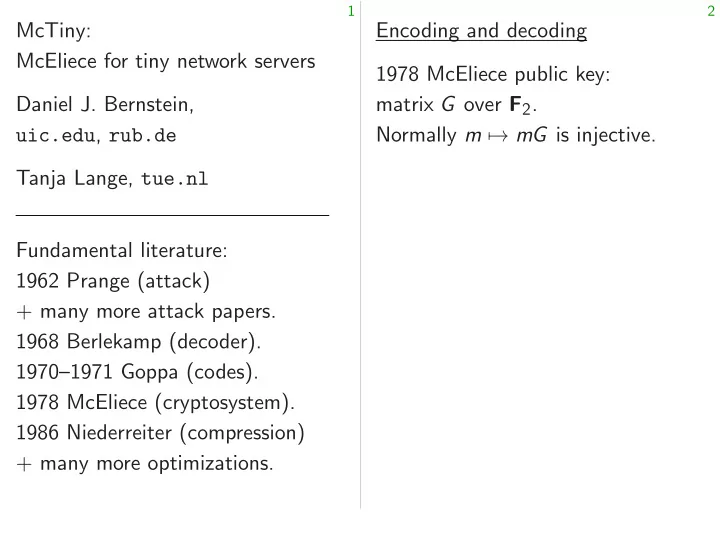

3 4 Binary Goppa codes One-wayness (“OW-Passive”) Parameters: q ∈ { 8 ; 16 ; 32 ; : : : } ; Fundamental security question: w ∈ { 2 ; 3 ; : : : ; ⌊ ( q − 1) = lg q ⌋} ; Can attacker efficiently find n ∈ { w lg q + 1 ; : : : ; q − 1 ; q } . random m; e given random public key G and ciphertext mG + e ? Secrets: distinct ¸ 1 ; : : : ; ¸ n ∈ F q ; monic irreducible degree- w polynomial g ∈ F q [ x ]. Goppa code: kernel of the map v �→ P i v i = ( x − ¸ i ) from F n 2 to F q [ x ] =g . Normally dimension n − w lg q . McEliece uses random G ∈ F k × n 2 whose image is this code.
3 4 Binary Goppa codes One-wayness (“OW-Passive”) Parameters: q ∈ { 8 ; 16 ; 32 ; : : : } ; Fundamental security question: w ∈ { 2 ; 3 ; : : : ; ⌊ ( q − 1) = lg q ⌋} ; Can attacker efficiently find n ∈ { w lg q + 1 ; : : : ; q − 1 ; q } . random m; e given random public key G and ciphertext mG + e ? Secrets: distinct ¸ 1 ; : : : ; ¸ n ∈ F q ; monic irreducible degree- w 1962 Prange: simple attack idea polynomial g ∈ F q [ x ]. guiding sizes in 1978 McEliece. Goppa code: kernel of the map v �→ P i v i = ( x − ¸ i ) from F n 2 to F q [ x ] =g . Normally dimension n − w lg q . McEliece uses random G ∈ F k × n 2 whose image is this code.
3 4 Binary Goppa codes One-wayness (“OW-Passive”) Parameters: q ∈ { 8 ; 16 ; 32 ; : : : } ; Fundamental security question: w ∈ { 2 ; 3 ; : : : ; ⌊ ( q − 1) = lg q ⌋} ; Can attacker efficiently find n ∈ { w lg q + 1 ; : : : ; q − 1 ; q } . random m; e given random public key G and ciphertext mG + e ? Secrets: distinct ¸ 1 ; : : : ; ¸ n ∈ F q ; monic irreducible degree- w 1962 Prange: simple attack idea polynomial g ∈ F q [ x ]. guiding sizes in 1978 McEliece. Goppa code: kernel of The McEliece system the map v �→ P i v i = ( x − ¸ i ) (with later key-size optimizations) from F n uses ( c 0 + o (1)) – 2 (lg – ) 2 -bit keys 2 to F q [ x ] =g . as – → ∞ to achieve 2 – security Normally dimension n − w lg q . against Prange’s attack. McEliece uses random G ∈ F k × n 2 Here c 0 ≈ 0 : 7418860694. whose image is this code.
3 4 Goppa codes One-wayness (“OW-Passive”) ≥ 26 subsequent analyzing rameters: q ∈ { 8 ; 16 ; 32 ; : : : } ; Fundamental security question: 2 ; 3 ; : : : ; ⌊ ( q − 1) = lg q ⌋} ; Can attacker efficiently find 1981 Cla lg q + 1 ; : : : ; q − 1 ; q } . random m; e given random public crediting key G and ciphertext mG + e ? 1988 Lee–Brick Secrets: distinct ¸ 1 ; : : : ; ¸ n ∈ F q ; 1988 Leon. irreducible degree- w 1962 Prange: simple attack idea 1989 Krouk. olynomial g ∈ F q [ x ]. guiding sizes in 1978 McEliece. 1989 Stern. code: kernel of The McEliece system 1989 Dumer. map v �→ P i v i = ( x − ¸ i ) (with later key-size optimizations) 1990 Coffey–Go n uses ( c 0 + o (1)) – 2 (lg – ) 2 -bit keys 2 to F q [ x ] =g . 1990 van as – → ∞ to achieve 2 – security rmally dimension n − w lg q . 1991 Dumer. against Prange’s attack. 1991 Coffey–Go McEliece uses random G ∈ F k × n 2 Here c 0 ≈ 0 : 7418860694. 1993 Chabanne–Courteau. image is this code. 1993 Chabaud.
3 4 des One-wayness (“OW-Passive”) ≥ 26 subsequent publication analyzing one-wayness { 8 ; 16 ; 32 ; : : : } ; Fundamental security question: ( q − 1) = lg q ⌋} ; Can attacker efficiently find 1981 Clark–Cain, : : : ; q − 1 ; q } . random m; e given random public crediting Omura. key G and ciphertext mG + e ? 1988 Lee–Brickell. ¸ 1 ; : : : ; ¸ n ∈ F q ; 1988 Leon. irreducible degree- w 1962 Prange: simple attack idea 1989 Krouk. F q [ x ]. guiding sizes in 1978 McEliece. 1989 Stern. ernel of The McEliece system 1989 Dumer. i v i = ( x − ¸ i ) (with later key-size optimizations) 1990 Coffey–Goodman. uses ( c 0 + o (1)) – 2 (lg – ) 2 -bit keys ] =g . 1990 van Tilburg. as – → ∞ to achieve 2 – security dimension n − w lg q . 1991 Dumer. against Prange’s attack. 1991 Coffey–Goodman–F random G ∈ F k × n 2 Here c 0 ≈ 0 : 7418860694. 1993 Chabanne–Courteau. this code. 1993 Chabaud.
3 4 One-wayness (“OW-Passive”) ≥ 26 subsequent publications analyzing one-wayness of system ; : : : } ; Fundamental security question: q ⌋} ; Can attacker efficiently find 1981 Clark–Cain, ; q } . random m; e given random public crediting Omura. key G and ciphertext mG + e ? 1988 Lee–Brickell. n ∈ F q ; 1988 Leon. 1962 Prange: simple attack idea 1989 Krouk. guiding sizes in 1978 McEliece. 1989 Stern. The McEliece system 1989 Dumer. ¸ i ) (with later key-size optimizations) 1990 Coffey–Goodman. uses ( c 0 + o (1)) – 2 (lg – ) 2 -bit keys 1990 van Tilburg. as – → ∞ to achieve 2 – security lg q . 1991 Dumer. against Prange’s attack. 1991 Coffey–Goodman–Farrell. ∈ F k × n 2 Here c 0 ≈ 0 : 7418860694. 1993 Chabanne–Courteau. 1993 Chabaud.
4 5 One-wayness (“OW-Passive”) ≥ 26 subsequent publications analyzing one-wayness of system: Fundamental security question: Can attacker efficiently find 1981 Clark–Cain, random m; e given random public crediting Omura. key G and ciphertext mG + e ? 1988 Lee–Brickell. 1988 Leon. 1962 Prange: simple attack idea 1989 Krouk. guiding sizes in 1978 McEliece. 1989 Stern. The McEliece system 1989 Dumer. (with later key-size optimizations) 1990 Coffey–Goodman. uses ( c 0 + o (1)) – 2 (lg – ) 2 -bit keys 1990 van Tilburg. as – → ∞ to achieve 2 – security 1991 Dumer. against Prange’s attack. 1991 Coffey–Goodman–Farrell. Here c 0 ≈ 0 : 7418860694. 1993 Chabanne–Courteau. 1993 Chabaud.
4 5 ayness (“OW-Passive”) ≥ 26 subsequent publications 1994 van analyzing one-wayness of system: 1994 Canteaut–Chabanne. undamental security question: 1998 Canteaut–Chabaud. attacker efficiently find 1981 Clark–Cain, 1998 Canteaut–Sendrier. m; e given random public crediting Omura. 2008 Bernstein–Lange–P and ciphertext mG + e ? 1988 Lee–Brickell. 2009 Bernstein–Lange–P 1988 Leon. Prange: simple attack idea van 1989 Krouk. guiding sizes in 1978 McEliece. 2009 Finiasz–Sendrier. 1989 Stern. 2011 Bernstein–Lange–P McEliece system 1989 Dumer. 2011 Ma later key-size optimizations) 1990 Coffey–Goodman. 2012 Beck 0 + o (1)) – 2 (lg – ) 2 -bit keys 1990 van Tilburg. 2013 Hamdaoui–Sendrier. ∞ to achieve 2 – security 1991 Dumer. 2015 Ma against Prange’s attack. 1991 Coffey–Goodman–Farrell. 2016 Canto 0 ≈ 0 : 7418860694. 1993 Chabanne–Courteau. 2017 Both–Ma 1993 Chabaud.
4 5 W-Passive”) ≥ 26 subsequent publications 1994 van Tilburg. analyzing one-wayness of system: 1994 Canteaut–Chabanne. security question: 1998 Canteaut–Chabaud. efficiently find 1981 Clark–Cain, 1998 Canteaut–Sendrier. given random public crediting Omura. 2008 Bernstein–Lange–P ciphertext mG + e ? 1988 Lee–Brickell. 2009 Bernstein–Lange–P 1988 Leon. simple attack idea van Tilborg. 1989 Krouk. 1978 McEliece. 2009 Finiasz–Sendrier. 1989 Stern. 2011 Bernstein–Lange–P system 1989 Dumer. 2011 May–Meurer–Th ey-size optimizations) 1990 Coffey–Goodman. 2012 Becker–Joux–Ma – 2 (lg – ) 2 -bit keys 1990 van Tilburg. 2013 Hamdaoui–Sendrier. achieve 2 – security 1991 Dumer. 2015 May–Ozerov. attack. 1991 Coffey–Goodman–Farrell. 2016 Canto Torres–Sendrier. 7418860694. 1993 Chabanne–Courteau. 2017 Both–May. 1993 Chabaud.
4 5 assive”) ≥ 26 subsequent publications 1994 van Tilburg. analyzing one-wayness of system: 1994 Canteaut–Chabanne. question: 1998 Canteaut–Chabaud. find 1981 Clark–Cain, 1998 Canteaut–Sendrier. public crediting Omura. 2008 Bernstein–Lange–Peters. e ? 1988 Lee–Brickell. 2009 Bernstein–Lange–Peters– 1988 Leon. attack idea van Tilborg. 1989 Krouk. McEliece. 2009 Finiasz–Sendrier. 1989 Stern. 2011 Bernstein–Lange–Peters. 1989 Dumer. 2011 May–Meurer–Thomae. optimizations) 1990 Coffey–Goodman. 2012 Becker–Joux–May–Meurer. -bit keys 1990 van Tilburg. 2013 Hamdaoui–Sendrier. security 1991 Dumer. 2015 May–Ozerov. 1991 Coffey–Goodman–Farrell. 2016 Canto Torres–Sendrier. 1993 Chabanne–Courteau. 2017 Both–May. 1993 Chabaud.
5 6 ≥ 26 subsequent publications 1994 van Tilburg. analyzing one-wayness of system: 1994 Canteaut–Chabanne. 1998 Canteaut–Chabaud. 1981 Clark–Cain, 1998 Canteaut–Sendrier. crediting Omura. 2008 Bernstein–Lange–Peters. 1988 Lee–Brickell. 2009 Bernstein–Lange–Peters– 1988 Leon. van Tilborg. 1989 Krouk. 2009 Finiasz–Sendrier. 1989 Stern. 2011 Bernstein–Lange–Peters. 1989 Dumer. 2011 May–Meurer–Thomae. 1990 Coffey–Goodman. 2012 Becker–Joux–May–Meurer. 1990 van Tilburg. 2013 Hamdaoui–Sendrier. 1991 Dumer. 2015 May–Ozerov. 1991 Coffey–Goodman–Farrell. 2016 Canto Torres–Sendrier. 1993 Chabanne–Courteau. 2017 Both–May. 1993 Chabaud.
5 6 subsequent publications 1994 van Tilburg. The McEliece analyzing one-wayness of system: 1994 Canteaut–Chabanne. uses ( c 0 1998 Canteaut–Chabaud. as – → ∞ Clark–Cain, 1998 Canteaut–Sendrier. against all crediting Omura. 2008 Bernstein–Lange–Peters. Same c 0 Lee–Brickell. 2009 Bernstein–Lange–Peters– Leon. van Tilborg. Krouk. 2009 Finiasz–Sendrier. Stern. 2011 Bernstein–Lange–Peters. Dumer. 2011 May–Meurer–Thomae. Coffey–Goodman. 2012 Becker–Joux–May–Meurer. van Tilburg. 2013 Hamdaoui–Sendrier. Dumer. 2015 May–Ozerov. Coffey–Goodman–Farrell. 2016 Canto Torres–Sendrier. Chabanne–Courteau. 2017 Both–May. Chabaud.
5 6 publications 1994 van Tilburg. The McEliece system uses ( c 0 + o (1)) – 2 ayness of system: 1994 Canteaut–Chabanne. 1998 Canteaut–Chabaud. as – → ∞ to achieve k–Cain, 1998 Canteaut–Sendrier. against all attacks Omura. 2008 Bernstein–Lange–Peters. Same c 0 ≈ 0 : 7418860694. ell. 2009 Bernstein–Lange–Peters– van Tilborg. 2009 Finiasz–Sendrier. 2011 Bernstein–Lange–Peters. 2011 May–Meurer–Thomae. odman. 2012 Becker–Joux–May–Meurer. urg. 2013 Hamdaoui–Sendrier. 2015 May–Ozerov. odman–Farrell. 2016 Canto Torres–Sendrier. Chabanne–Courteau. 2017 Both–May.
5 6 publications 1994 van Tilburg. The McEliece system uses ( c 0 + o (1)) – 2 (lg – ) 2 -bit system: 1994 Canteaut–Chabanne. as – → ∞ to achieve 2 – securit 1998 Canteaut–Chabaud. 1998 Canteaut–Sendrier. against all attacks known to 2008 Bernstein–Lange–Peters. Same c 0 ≈ 0 : 7418860694. 2009 Bernstein–Lange–Peters– van Tilborg. 2009 Finiasz–Sendrier. 2011 Bernstein–Lange–Peters. 2011 May–Meurer–Thomae. 2012 Becker–Joux–May–Meurer. 2013 Hamdaoui–Sendrier. 2015 May–Ozerov. rrell. 2016 Canto Torres–Sendrier. Chabanne–Courteau. 2017 Both–May.
6 7 1994 van Tilburg. The McEliece system uses ( c 0 + o (1)) – 2 (lg – ) 2 -bit keys 1994 Canteaut–Chabanne. as – → ∞ to achieve 2 – security 1998 Canteaut–Chabaud. 1998 Canteaut–Sendrier. against all attacks known today. 2008 Bernstein–Lange–Peters. Same c 0 ≈ 0 : 7418860694. 2009 Bernstein–Lange–Peters– van Tilborg. 2009 Finiasz–Sendrier. 2011 Bernstein–Lange–Peters. 2011 May–Meurer–Thomae. 2012 Becker–Joux–May–Meurer. 2013 Hamdaoui–Sendrier. 2015 May–Ozerov. 2016 Canto Torres–Sendrier. 2017 Both–May.
6 7 1994 van Tilburg. The McEliece system uses ( c 0 + o (1)) – 2 (lg – ) 2 -bit keys 1994 Canteaut–Chabanne. as – → ∞ to achieve 2 – security 1998 Canteaut–Chabaud. 1998 Canteaut–Sendrier. against all attacks known today. 2008 Bernstein–Lange–Peters. Same c 0 ≈ 0 : 7418860694. 2009 Bernstein–Lange–Peters– Replacing – with 2 – van Tilborg. stops all known quantum attacks: 2009 Finiasz–Sendrier. 2008 Bernstein, 2017 Kachigar– 2011 Bernstein–Lange–Peters. Tillich, 2018 Kirshanova. 2011 May–Meurer–Thomae. 2012 Becker–Joux–May–Meurer. 2013 Hamdaoui–Sendrier. 2015 May–Ozerov. 2016 Canto Torres–Sendrier. 2017 Both–May.
6 7 1994 van Tilburg. The McEliece system uses ( c 0 + o (1)) – 2 (lg – ) 2 -bit keys 1994 Canteaut–Chabanne. as – → ∞ to achieve 2 – security 1998 Canteaut–Chabaud. 1998 Canteaut–Sendrier. against all attacks known today. 2008 Bernstein–Lange–Peters. Same c 0 ≈ 0 : 7418860694. 2009 Bernstein–Lange–Peters– Replacing – with 2 – van Tilborg. stops all known quantum attacks: 2009 Finiasz–Sendrier. 2008 Bernstein, 2017 Kachigar– 2011 Bernstein–Lange–Peters. Tillich, 2018 Kirshanova. 2011 May–Meurer–Thomae. Modern example, 2012 Becker–Joux–May–Meurer. mceliece6960119 parameter set 2013 Hamdaoui–Sendrier. (2008 Bernstein–Lange–Peters): 2015 May–Ozerov. q = 8192, n = 6960, w = 119. 2016 Canto Torres–Sendrier. 2017 Both–May.
6 7 van Tilburg. The McEliece system NIST comp uses ( c 0 + o (1)) – 2 (lg – ) 2 -bit keys Canteaut–Chabanne. 2016: U.S. as – → ∞ to achieve 2 – security Canteaut–Chabaud. Standards Canteaut–Sendrier. against all attacks known today. “post-quantum” Bernstein–Lange–Peters. Same c 0 ≈ 0 : 7418860694. 2017: 69 Bernstein–Lange–Peters– Replacing – with 2 – van Tilborg. 2019: NIST stops all known quantum attacks: Finiasz–Sendrier. 26 submissions 2008 Bernstein, 2017 Kachigar– Bernstein–Lange–Peters. Tillich, 2018 Kirshanova. May–Meurer–Thomae. Modern example, Becker–Joux–May–Meurer. mceliece6960119 parameter set Hamdaoui–Sendrier. (2008 Bernstein–Lange–Peters): May–Ozerov. q = 8192, n = 6960, w = 119. Canto Torres–Sendrier. Both–May.
6 7 rg. The McEliece system NIST competition uses ( c 0 + o (1)) – 2 (lg – ) 2 -bit keys Canteaut–Chabanne. 2016: U.S. National as – → ∞ to achieve 2 – security Canteaut–Chabaud. Standards and Technology Canteaut–Sendrier. against all attacks known today. “post-quantum” comp Bernstein–Lange–Peters. Same c 0 ≈ 0 : 7418860694. 2017: 69 complete Bernstein–Lange–Peters– Replacing – with 2 – rg. 2019: NIST selects stops all known quantum attacks: Finiasz–Sendrier. 26 submissions for 2008 Bernstein, 2017 Kachigar– Bernstein–Lange–Peters. Tillich, 2018 Kirshanova. y–Meurer–Thomae. Modern example, er–Joux–May–Meurer. mceliece6960119 parameter set Hamdaoui–Sendrier. (2008 Bernstein–Lange–Peters): y–Ozerov. q = 8192, n = 6960, w = 119. rres–Sendrier. .
6 7 The McEliece system NIST competition uses ( c 0 + o (1)) – 2 (lg – ) 2 -bit keys Canteaut–Chabanne. 2016: U.S. National Institute as – → ∞ to achieve 2 – security Standards and Technology sta against all attacks known today. “post-quantum” competition. eters. Same c 0 ≈ 0 : 7418860694. 2017: 69 complete submissions. eters– Replacing – with 2 – 2019: NIST selects stops all known quantum attacks: 26 submissions for round 2. 2008 Bernstein, 2017 Kachigar– eters. Tillich, 2018 Kirshanova. ae. Modern example, y–Meurer. mceliece6960119 parameter set (2008 Bernstein–Lange–Peters): q = 8192, n = 6960, w = 119. rres–Sendrier.
7 8 The McEliece system NIST competition uses ( c 0 + o (1)) – 2 (lg – ) 2 -bit keys 2016: U.S. National Institute of as – → ∞ to achieve 2 – security Standards and Technology starts against all attacks known today. “post-quantum” competition. Same c 0 ≈ 0 : 7418860694. 2017: 69 complete submissions. Replacing – with 2 – 2019: NIST selects stops all known quantum attacks: 26 submissions for round 2. 2008 Bernstein, 2017 Kachigar– Tillich, 2018 Kirshanova. Modern example, mceliece6960119 parameter set (2008 Bernstein–Lange–Peters): q = 8192, n = 6960, w = 119.
7 8 The McEliece system NIST competition uses ( c 0 + o (1)) – 2 (lg – ) 2 -bit keys 2016: U.S. National Institute of as – → ∞ to achieve 2 – security Standards and Technology starts against all attacks known today. “post-quantum” competition. Same c 0 ≈ 0 : 7418860694. 2017: 69 complete submissions. Replacing – with 2 – 2019: NIST selects stops all known quantum attacks: 26 submissions for round 2. 2008 Bernstein, 2017 Kachigar– Tillich, 2018 Kirshanova. “Classic McEliece”: submission from team of 12 people. Modern example, mceliece6960119 parameter set Round-2 options: (2008 Bernstein–Lange–Peters): 8192128 , 6960119 , 6688128 , q = 8192, n = 6960, w = 119. 460896 , 348864 .
7 8 McEliece system NIST competition Is Classic 0 + o (1)) – 2 (lg – ) 2 -bit keys 1978 McEliece 2016: U.S. National Institute of ∞ to achieve 2 – security Standards and Technology starts 1978 McEliece against all attacks known today. “post-quantum” competition. huge amount c 0 ≈ 0 : 7418860694. 2017: 69 complete submissions. Some wo Replacing – with 2 – while clea 2019: NIST selects all known quantum attacks: e.g., Niederreiter 26 submissions for round 2. Bernstein, 2017 Kachigar– e.g., many Tillich, 2018 Kirshanova. “Classic McEliece”: submission Classic McEliec from team of 12 people. dern example, Classic McEliec mceliece6960119 parameter set Round-2 options: more than Bernstein–Lange–Peters): 8192128 , 6960119 , 6688128 , 8192, n = 6960, w = 119. 460896 , 348864 .
7 8 system NIST competition Is Classic McEliece – 2 (lg – ) 2 -bit keys 1978 McEliece? Not 2016: U.S. National Institute of achieve 2 – security Standards and Technology starts 1978 McEliece prompted attacks known today. “post-quantum” competition. huge amount of follo 7418860694. 2017: 69 complete submissions. Some work improves 2 – while clearly preserving 2019: NIST selects quantum attacks: e.g., Niederreiter comp 26 submissions for round 2. 2017 Kachigar– e.g., many decoding Kirshanova. “Classic McEliece”: submission Classic McEliece uses from team of 12 people. example, Classic McEliece also mceliece6960119 parameter set Round-2 options: more than OW-Passive Bernstein–Lange–Peters): 8192128 , 6960119 , 6688128 , 6960, w = 119. 460896 , 348864 .
7 8 NIST competition Is Classic McEliece same as -bit keys 1978 McEliece? Not exactly. 2016: U.S. National Institute of security Standards and Technology starts 1978 McEliece prompted a today. “post-quantum” competition. huge amount of followup wo 2017: 69 complete submissions. Some work improves efficiency while clearly preserving secur 2019: NIST selects attacks: e.g., Niederreiter compression; 26 submissions for round 2. Kachigar– e.g., many decoding speedups. “Classic McEliece”: submission Classic McEliece uses all this. from team of 12 people. Classic McEliece also aims fo rameter set Round-2 options: more than OW-Passive securit eters): 8192128 , 6960119 , 6688128 , 119. 460896 , 348864 .
8 9 NIST competition Is Classic McEliece same as 1978 McEliece? Not exactly. 2016: U.S. National Institute of Standards and Technology starts 1978 McEliece prompted a “post-quantum” competition. huge amount of followup work. 2017: 69 complete submissions. Some work improves efficiency while clearly preserving security: 2019: NIST selects e.g., Niederreiter compression; 26 submissions for round 2. e.g., many decoding speedups. “Classic McEliece”: submission Classic McEliece uses all this. from team of 12 people. Classic McEliece also aims for Round-2 options: more than OW-Passive security. 8192128 , 6960119 , 6688128 , 460896 , 348864 .
8 9 competition Is Classic McEliece same as Niederreiter 1978 McEliece? Not exactly. U.S. National Institute of Generato Standards and Technology starts 1978 McEliece prompted a of length G ′ ∈ F k × ost-quantum” competition. huge amount of followup work. 2 69 complete submissions. Some work improves efficiency McEliece while clearly preserving security: random invertible NIST selects e.g., Niederreiter compression; submissions for round 2. e.g., many decoding speedups. “Classic McEliece”: submission Classic McEliece uses all this. team of 12 people. Classic McEliece also aims for Round-2 options: more than OW-Passive security. 8192128 , 6960119 , 6688128 , , 348864 .
8 9 etition Is Classic McEliece same as Niederreiter key comp 1978 McEliece? Not exactly. National Institute of Generator matrix fo echnology starts 1978 McEliece prompted a of length n and dimension G ′ ∈ F k × n competition. huge amount of followup work. with Γ 2 complete submissions. Some work improves efficiency McEliece public key: while clearly preserving security: random invertible S selects e.g., Niederreiter compression; for round 2. e.g., many decoding speedups. e”: submission Classic McEliece uses all this. people. Classic McEliece also aims for options: more than OW-Passive security. 6960119 , 6688128 , .
8 9 Is Classic McEliece same as Niederreiter key compression 1978 McEliece? Not exactly. Institute of Generator matrix for code Γ starts 1978 McEliece prompted a of length n and dimension k G ′ ∈ F k × n 2 · G ′ . with Γ = F k etition. huge amount of followup work. 2 submissions. Some work improves efficiency McEliece public key: G = SG random invertible S ∈ F k × k while clearly preserving security: . 2 e.g., Niederreiter compression; 2. e.g., many decoding speedups. submission Classic McEliece uses all this. Classic McEliece also aims for more than OW-Passive security. 6688128 ,
9 10 Is Classic McEliece same as Niederreiter key compression 1978 McEliece? Not exactly. Generator matrix for code Γ 1978 McEliece prompted a of length n and dimension k : G ′ ∈ F k × n 2 · G ′ . with Γ = F k huge amount of followup work. 2 McEliece public key: G = SG ′ for Some work improves efficiency random invertible S ∈ F k × k while clearly preserving security: . 2 e.g., Niederreiter compression; e.g., many decoding speedups. Classic McEliece uses all this. Classic McEliece also aims for more than OW-Passive security.
9 10 Is Classic McEliece same as Niederreiter key compression 1978 McEliece? Not exactly. Generator matrix for code Γ 1978 McEliece prompted a of length n and dimension k : G ′ ∈ F k × n 2 · G ′ . with Γ = F k huge amount of followup work. 2 McEliece public key: G = SG ′ for Some work improves efficiency random invertible S ∈ F k × k while clearly preserving security: . 2 e.g., Niederreiter compression; Niederreiter instead reduces G ′ e.g., many decoding speedups. to the unique generator matrix in Classic McEliece uses all this. systematic form: G = ( I k | R ). Classic McEliece also aims for more than OW-Passive security.
9 10 Is Classic McEliece same as Niederreiter key compression 1978 McEliece? Not exactly. Generator matrix for code Γ 1978 McEliece prompted a of length n and dimension k : G ′ ∈ F k × n 2 · G ′ . with Γ = F k huge amount of followup work. 2 McEliece public key: G = SG ′ for Some work improves efficiency random invertible S ∈ F k × k while clearly preserving security: . 2 e.g., Niederreiter compression; Niederreiter instead reduces G ′ e.g., many decoding speedups. to the unique generator matrix in Classic McEliece uses all this. systematic form: G = ( I k | R ). Classic McEliece also aims for Pr ≈ 29% that systematic form more than OW-Passive security. exists. Security loss: < 2 bits.
9 10 Classic McEliece same as Niederreiter key compression Niederreiter McEliece? Not exactly. Generator matrix for code Γ Use Niede McEliece prompted a of length n and dimension k : McEliece G ′ ∈ F k × n 2 · G ′ . with Γ = F k amount of followup work. 2 McEliece public key: G = SG ′ for work improves efficiency random invertible S ∈ F k × k clearly preserving security: . 2 Niederreiter compression; Niederreiter instead reduces G ′ many decoding speedups. to the unique generator matrix in McEliece uses all this. systematic form: G = ( I k | R ). McEliece also aims for Pr ≈ 29% that systematic form than OW-Passive security. exists. Security loss: < 2 bits.
9 10 McEliece same as Niederreiter key compression Niederreiter ciphertext Not exactly. Generator matrix for code Γ Use Niederreiter key rompted a of length n and dimension k : McEliece ciphertext: G ′ ∈ F k × n 2 · G ′ . with Γ = F k followup work. 2 McEliece public key: G = SG ′ for roves efficiency random invertible S ∈ F k × k reserving security: . 2 Niederreiter compression; Niederreiter instead reduces G ′ ding speedups. to the unique generator matrix in uses all this. systematic form: G = ( I k | R ). also aims for Pr ≈ 29% that systematic form W-Passive security. exists. Security loss: < 2 bits.
9 10 as Niederreiter key compression Niederreiter ciphertext comp exactly. Generator matrix for code Γ Use Niederreiter key G = ( I k of length n and dimension k : McEliece ciphertext: mG + e G ′ ∈ F k × n 2 · G ′ . with Γ = F k work. 2 McEliece public key: G = SG ′ for efficiency random invertible S ∈ F k × k curity: . 2 ression; Niederreiter instead reduces G ′ edups. to the unique generator matrix in this. systematic form: G = ( I k | R ). for Pr ≈ 29% that systematic form security. exists. Security loss: < 2 bits.
10 11 Niederreiter key compression Niederreiter ciphertext compression Generator matrix for code Γ Use Niederreiter key G = ( I k | R ). of length n and dimension k : McEliece ciphertext: mG + e ∈ F n 2 . G ′ ∈ F k × n 2 · G ′ . with Γ = F k 2 McEliece public key: G = SG ′ for random invertible S ∈ F k × k . 2 Niederreiter instead reduces G ′ to the unique generator matrix in systematic form: G = ( I k | R ). Pr ≈ 29% that systematic form exists. Security loss: < 2 bits.
10 11 Niederreiter key compression Niederreiter ciphertext compression Generator matrix for code Γ Use Niederreiter key G = ( I k | R ). of length n and dimension k : McEliece ciphertext: mG + e ∈ F n 2 . G ′ ∈ F k × n 2 · G ′ . with Γ = F k 2 Niederreiter ciphertext, shorter: McEliece public key: G = SG ′ for He ⊤ ∈ F ( n − k ) × 1 2 random invertible S ∈ F k × k . where H = ( R ⊤ | I n − k ). 2 Niederreiter instead reduces G ′ to the unique generator matrix in systematic form: G = ( I k | R ). Pr ≈ 29% that systematic form exists. Security loss: < 2 bits.
10 11 Niederreiter key compression Niederreiter ciphertext compression Generator matrix for code Γ Use Niederreiter key G = ( I k | R ). of length n and dimension k : McEliece ciphertext: mG + e ∈ F n 2 . G ′ ∈ F k × n 2 · G ′ . with Γ = F k 2 Niederreiter ciphertext, shorter: McEliece public key: G = SG ′ for He ⊤ ∈ F ( n − k ) × 1 2 random invertible S ∈ F k × k . where H = ( R ⊤ | I n − k ). 2 Niederreiter instead reduces G ′ Given H and Niederreiter’s He ⊤ , to the unique generator matrix in can attacker efficiently find e ? systematic form: G = ( I k | R ). Pr ≈ 29% that systematic form exists. Security loss: < 2 bits.
10 11 Niederreiter key compression Niederreiter ciphertext compression Generator matrix for code Γ Use Niederreiter key G = ( I k | R ). of length n and dimension k : McEliece ciphertext: mG + e ∈ F n 2 . G ′ ∈ F k × n 2 · G ′ . with Γ = F k 2 Niederreiter ciphertext, shorter: McEliece public key: G = SG ′ for He ⊤ ∈ F ( n − k ) × 1 2 random invertible S ∈ F k × k . where H = ( R ⊤ | I n − k ). 2 Niederreiter instead reduces G ′ Given H and Niederreiter’s He ⊤ , to the unique generator matrix in can attacker efficiently find e ? systematic form: G = ( I k | R ). If so, attacker can efficiently Pr ≈ 29% that systematic form find m; e given G and mG + e : exists. Security loss: < 2 bits.
10 11 Niederreiter key compression Niederreiter ciphertext compression Generator matrix for code Γ Use Niederreiter key G = ( I k | R ). of length n and dimension k : McEliece ciphertext: mG + e ∈ F n 2 . G ′ ∈ F k × n 2 · G ′ . with Γ = F k 2 Niederreiter ciphertext, shorter: McEliece public key: G = SG ′ for He ⊤ ∈ F ( n − k ) × 1 2 random invertible S ∈ F k × k . where H = ( R ⊤ | I n − k ). 2 Niederreiter instead reduces G ′ Given H and Niederreiter’s He ⊤ , to the unique generator matrix in can attacker efficiently find e ? systematic form: G = ( I k | R ). If so, attacker can efficiently Pr ≈ 29% that systematic form find m; e given G and mG + e : exists. Security loss: < 2 bits. compute H ( mG + e ) ⊤ = He ⊤ ; find e ; compute m from mG .
10 11 Niederreiter key compression Niederreiter ciphertext compression Other choices Generator matrix for code Γ Use Niederreiter key G = ( I k | R ). Niederreiter length n and dimension k : Solomon McEliece ciphertext: mG + e ∈ F n 2 . k × n 2 · G ′ . with Γ = F k by Sidelnik 2 Niederreiter ciphertext, shorter: McEliece public key: G = SG ′ for More corpses: He ⊤ ∈ F ( n − k ) × 1 2 invertible S ∈ F k × k . codes, Reed–Muller where H = ( R ⊤ | I n − k ). 2 AG codes, Niederreiter instead reduces G ′ Given H and Niederreiter’s He ⊤ , several LDPC unique generator matrix in can attacker efficiently find e ? systematic form: G = ( I k | R ). If so, attacker can efficiently 29% that systematic form find m; e given G and mG + e : Security loss: < 2 bits. compute H ( mG + e ) ⊤ = He ⊤ ; find e ; compute m from mG .
10 11 compression Niederreiter ciphertext compression Other choices of co ix for code Γ Use Niederreiter key G = ( I k | R ). Niederreiter sugges dimension k : Solomon codes. Brok McEliece ciphertext: mG + e ∈ F n 2 . 2 · G ′ . Γ = F k by Sidelnikov and Shestak Niederreiter ciphertext, shorter: key: G = SG ′ for More corpses: e.g., He ⊤ ∈ F ( n − k ) × 1 2 invertible S ∈ F k × k . codes, Reed–Muller where H = ( R ⊤ | I n − k ). 2 AG codes, Gabidulin instead reduces G ′ Given H and Niederreiter’s He ⊤ , several LDPC code generator matrix in can attacker efficiently find e ? rm: G = ( I k | R ). If so, attacker can efficiently systematic form find m; e given G and mG + e : loss: < 2 bits. compute H ( mG + e ) ⊤ = He ⊤ ; find e ; compute m from mG .
10 11 ression Niederreiter ciphertext compression Other choices of codes Γ Use Niederreiter key G = ( I k | R ). Niederreiter suggested Reed– k : Solomon codes. Broken in 1992 McEliece ciphertext: mG + e ∈ F n 2 . ′ . by Sidelnikov and Shestakov. Niederreiter ciphertext, shorter: SG ′ for More corpses: e.g., concatenated He ⊤ ∈ F ( n − k ) × 1 2 k . codes, Reed–Muller codes, several where H = ( R ⊤ | I n − k ). AG codes, Gabidulin codes, reduces G ′ Given H and Niederreiter’s He ⊤ , several LDPC codes. matrix in can attacker efficiently find e ? | R ). If so, attacker can efficiently form find m; e given G and mG + e : bits. compute H ( mG + e ) ⊤ = He ⊤ ; find e ; compute m from mG .
11 12 Niederreiter ciphertext compression Other choices of codes Use Niederreiter key G = ( I k | R ). Niederreiter suggested Reed– Solomon codes. Broken in 1992 McEliece ciphertext: mG + e ∈ F n 2 . by Sidelnikov and Shestakov. Niederreiter ciphertext, shorter: More corpses: e.g., concatenated He ⊤ ∈ F ( n − k ) × 1 2 codes, Reed–Muller codes, several where H = ( R ⊤ | I n − k ). AG codes, Gabidulin codes, Given H and Niederreiter’s He ⊤ , several LDPC codes. can attacker efficiently find e ? If so, attacker can efficiently find m; e given G and mG + e : compute H ( mG + e ) ⊤ = He ⊤ ; find e ; compute m from mG .
11 12 Niederreiter ciphertext compression Other choices of codes Use Niederreiter key G = ( I k | R ). Niederreiter suggested Reed– Solomon codes. Broken in 1992 McEliece ciphertext: mG + e ∈ F n 2 . by Sidelnikov and Shestakov. Niederreiter ciphertext, shorter: More corpses: e.g., concatenated He ⊤ ∈ F ( n − k ) × 1 2 codes, Reed–Muller codes, several where H = ( R ⊤ | I n − k ). AG codes, Gabidulin codes, Given H and Niederreiter’s He ⊤ , several LDPC codes. can attacker efficiently find e ? No proof that changing codes If so, attacker can efficiently preserves security level. find m; e given G and mG + e : Classic McEliece: binary Goppa. compute H ( mG + e ) ⊤ = He ⊤ ; find e ; compute m from mG .
11 12 Niederreiter ciphertext compression Other choices of codes IND-CCA2 Niederreiter key G = ( I k | R ). Niederreiter suggested Reed– OW-Pass Solomon codes. Broken in 1992 Messages McEliece ciphertext: mG + e ∈ F n 2 . by Sidelnikov and Shestakov. Attacker Niederreiter ciphertext, shorter: and observe More corpses: e.g., concatenated F ( n − k ) × 1 2 codes, Reed–Muller codes, several H = ( R ⊤ | I n − k ). AG codes, Gabidulin codes, H and Niederreiter’s He ⊤ , several LDPC codes. attacker efficiently find e ? No proof that changing codes attacker can efficiently preserves security level. ; e given G and mG + e : Classic McEliece: binary Goppa. compute H ( mG + e ) ⊤ = He ⊤ ; compute m from mG .
11 12 ciphertext compression Other choices of codes IND-CCA2 security key G = ( I k | R ). Niederreiter suggested Reed– OW-Passive securit Solomon codes. Broken in 1992 Messages are not random. ciphertext: mG + e ∈ F n 2 . by Sidelnikov and Shestakov. Attackers choose ciphertexts ciphertext, shorter: and observe reactions. More corpses: e.g., concatenated codes, Reed–Muller codes, several | I n − k ). AG codes, Gabidulin codes, Niederreiter’s He ⊤ , several LDPC codes. efficiently find e ? No proof that changing codes can efficiently preserves security level. and mG + e : Classic McEliece: binary Goppa. + e ) ⊤ = He ⊤ ; m from mG .
11 12 compression Other choices of codes IND-CCA2 security ( I k | R ). Niederreiter suggested Reed– OW-Passive security is too w Solomon codes. Broken in 1992 Messages are not random. e ∈ F n 2 . by Sidelnikov and Shestakov. Attackers choose ciphertexts shorter: and observe reactions. More corpses: e.g., concatenated codes, Reed–Muller codes, several AG codes, Gabidulin codes, Niederreiter’s He ⊤ , several LDPC codes. find e ? No proof that changing codes efficiently preserves security level. + e : Classic McEliece: binary Goppa. e ⊤ ; G .
12 13 Other choices of codes IND-CCA2 security Niederreiter suggested Reed– OW-Passive security is too weak. Solomon codes. Broken in 1992 Messages are not random. by Sidelnikov and Shestakov. Attackers choose ciphertexts and observe reactions. More corpses: e.g., concatenated codes, Reed–Muller codes, several AG codes, Gabidulin codes, several LDPC codes. No proof that changing codes preserves security level. Classic McEliece: binary Goppa.
12 13 Other choices of codes IND-CCA2 security Niederreiter suggested Reed– OW-Passive security is too weak. Solomon codes. Broken in 1992 Messages are not random. by Sidelnikov and Shestakov. Attackers choose ciphertexts and observe reactions. More corpses: e.g., concatenated codes, Reed–Muller codes, several Classic McEliece does more work AG codes, Gabidulin codes, for “IND-CCA2 security”. several LDPC codes. Combines coding theory with No proof that changing codes AES-GCM “authenticated cipher” preserves security level. and SHA-3 “hash function”. Classic McEliece: binary Goppa. All messages are safe. Reusing keys is safe.
12 13 choices of codes IND-CCA2 security Time Niederreiter suggested Reed– OW-Passive security is too weak. Cycles on Solomon codes. Broken in 1992 Messages are not random. params delnikov and Shestakov. Attackers choose ciphertexts 348864 and observe reactions. corpses: e.g., concatenated 460896 Reed–Muller codes, several Classic McEliece does more work 6688128 des, Gabidulin codes, for “IND-CCA2 security”. 6960119 several LDPC codes. 8192128 Combines coding theory with of that changing codes AES-GCM “authenticated cipher” 348864 reserves security level. and SHA-3 “hash function”. 460896 6688128 McEliece: binary Goppa. All messages are safe. 6960119 Reusing keys is safe. 8192128
12 13 codes IND-CCA2 security Time suggested Reed– OW-Passive security is too weak. Cycles on Intel Hasw Broken in 1992 Messages are not random. params op cycles and Shestakov. Attackers choose ciphertexts 45888 348864 enc and observe reactions. e.g., concatenated 82684 460896 enc Reed–Muller codes, several Classic McEliece does more work 6688128 enc 153372 Gabidulin codes, for “IND-CCA2 security”. 6960119 enc 154972 des. 8192128 enc 183892 Combines coding theory with changing codes AES-GCM “authenticated cipher” dec 136840 348864 y level. and SHA-3 “hash function”. dec 273872 460896 6688128 dec 320428 e: binary Goppa. All messages are safe. 6960119 dec 302460 Reusing keys is safe. 8192128 dec 324008
12 13 IND-CCA2 security Time Reed– OW-Passive security is too weak. Cycles on Intel Haswell CPU 1992 Messages are not random. params op cycles ov. Attackers choose ciphertexts 45888 348864 enc and observe reactions. concatenated 82684 460896 enc des, several Classic McEliece does more work 6688128 enc 153372 des, for “IND-CCA2 security”. 6960119 enc 154972 8192128 enc 183892 Combines coding theory with des AES-GCM “authenticated cipher” dec 136840 348864 and SHA-3 “hash function”. dec 273872 460896 6688128 dec 320428 Goppa. All messages are safe. 6960119 dec 302460 Reusing keys is safe. 8192128 dec 324008
13 14 IND-CCA2 security Time OW-Passive security is too weak. Cycles on Intel Haswell CPU core: Messages are not random. params op cycles Attackers choose ciphertexts 45888 348864 enc and observe reactions. 82684 460896 enc Classic McEliece does more work 6688128 enc 153372 for “IND-CCA2 security”. 6960119 enc 154972 8192128 enc 183892 Combines coding theory with AES-GCM “authenticated cipher” dec 136840 348864 and SHA-3 “hash function”. dec 273872 460896 6688128 dec 320428 All messages are safe. 6960119 dec 302460 Reusing keys is safe. 8192128 dec 324008
13 14 IND-CCA2 security Time “Wait, y most imp assive security is too weak. Cycles on Intel Haswell CPU core: to have such Messages are not random. params op cycles ers choose ciphertexts params 45888 348864 enc observe reactions. 348864 82684 460896 enc 348864f McEliece does more work 6688128 enc 153372 460896 D-CCA2 security”. 6960119 enc 154972 460896f 8192128 enc 183892 Combines coding theory with 6688128 AES-GCM “authenticated cipher” dec 136840 348864 6688128f SHA-3 “hash function”. dec 273872 460896 6960119 6688128 dec 320428 messages are safe. 6960119f 6960119 dec 302460 Reusing keys is safe. 8192128 8192128 dec 324008 8192128f
13 14 rity Time “Wait, you’re leaving most important cost! security is too weak. Cycles on Intel Haswell CPU core: to have such slow not random. params op cycles ose ciphertexts params op 45888 348864 enc reactions. 348864 keygen 82684 460896 enc 348864f keygen does more work 6688128 enc 153372 460896 keygen security”. 6960119 enc 154972 460896f keygen 8192128 enc 183892 ding theory with 6688128 keygen “authenticated cipher” dec 136840 348864 6688128f keygen h function”. dec 273872 460896 6960119 keygen 6688128 dec 320428 safe. 6960119f keygen 6960119 dec 302460 safe. 8192128 keygen 8192128 dec 324008 8192128f keygen
13 14 Time “Wait, you’re leaving out the most important cost! It’s crazy weak. Cycles on Intel Haswell CPU core: to have such slow keygen!” params op cycles ciphertexts params op cycles 45888 348864 enc 140870324 348864 keygen 82684 460896 enc 82232360 348864f keygen re work 6688128 enc 153372 441517292 460896 keygen 6960119 enc 154972 282869316 460896f keygen 8192128 enc 183892 with keygen 1180468912 6688128 cipher” dec 136840 348864 625470504 6688128f keygen function”. dec 273872 460896 keygen 1109340668 6960119 6688128 dec 320428 564570384 6960119f keygen 6960119 dec 302460 933422948 8192128 keygen 8192128 dec 324008 678860388 8192128f keygen
14 15 Time “Wait, you’re leaving out the most important cost! It’s crazy Cycles on Intel Haswell CPU core: to have such slow keygen!” params op cycles params op cycles 45888 348864 enc 140870324 348864 keygen 82684 460896 enc 82232360 348864f keygen 6688128 enc 153372 441517292 460896 keygen 6960119 enc 154972 282869316 460896f keygen 8192128 enc 183892 keygen 1180468912 6688128 dec 136840 348864 625470504 6688128f keygen dec 273872 460896 keygen 1109340668 6960119 6688128 dec 320428 564570384 6960119f keygen 6960119 dec 302460 933422948 8192128 keygen 8192128 dec 324008 678860388 8192128f keygen
14 15 “Wait, you’re leaving out the 1. What most important cost! It’s crazy that this on Intel Haswell CPU core: to have such slow keygen!” a problem rams op cycles params op cycles 45888 enc 140870324 348864 keygen 82684 enc 82232360 348864f keygen 6688128 enc 153372 441517292 460896 keygen 6960119 enc 154972 282869316 460896f keygen 8192128 enc 183892 keygen 1180468912 6688128 dec 136840 625470504 6688128f keygen dec 273872 keygen 1109340668 6960119 6688128 dec 320428 564570384 6960119f keygen 6960119 dec 302460 933422948 8192128 keygen 8192128 dec 324008 678860388 8192128f keygen
14 15 “Wait, you’re leaving out the 1. What evidence most important cost! It’s crazy that this keygen time Haswell CPU core: to have such slow keygen!” a problem for applications? cycles params op cycles 45888 140870324 348864 keygen 82684 82232360 348864f keygen 153372 441517292 460896 keygen 154972 282869316 460896f keygen 183892 keygen 1180468912 6688128 136840 625470504 6688128f keygen 273872 keygen 1109340668 6960119 320428 564570384 6960119f keygen 302460 933422948 8192128 keygen 324008 678860388 8192128f keygen
14 15 “Wait, you’re leaving out the 1. What evidence do we have most important cost! It’s crazy that this keygen time is CPU core: to have such slow keygen!” a problem for applications? params op cycles 140870324 348864 keygen 82232360 348864f keygen 441517292 460896 keygen 282869316 460896f keygen keygen 1180468912 6688128 625470504 6688128f keygen keygen 1109340668 6960119 564570384 6960119f keygen 933422948 8192128 keygen 678860388 8192128f keygen
15 16 “Wait, you’re leaving out the 1. What evidence do we have most important cost! It’s crazy that this keygen time is to have such slow keygen!” a problem for applications? params op cycles 140870324 348864 keygen 82232360 348864f keygen 441517292 460896 keygen 282869316 460896f keygen keygen 1180468912 6688128 625470504 6688128f keygen keygen 1109340668 6960119 564570384 6960119f keygen 933422948 8192128 keygen 678860388 8192128f keygen
15 16 “Wait, you’re leaving out the 1. What evidence do we have most important cost! It’s crazy that this keygen time is to have such slow keygen!” a problem for applications? params op cycles 2. Classic McEliece is designed for IND-CCA2 security, so 140870324 348864 keygen a key can be generated once and 82232360 348864f keygen used a huge number of times. 441517292 460896 keygen 282869316 460896f keygen keygen 1180468912 6688128 625470504 6688128f keygen keygen 1109340668 6960119 564570384 6960119f keygen 933422948 8192128 keygen 678860388 8192128f keygen
15 16 “Wait, you’re leaving out the 1. What evidence do we have most important cost! It’s crazy that this keygen time is to have such slow keygen!” a problem for applications? params op cycles 2. Classic McEliece is designed for IND-CCA2 security, so 140870324 348864 keygen a key can be generated once and 82232360 348864f keygen used a huge number of times. 441517292 460896 keygen 282869316 460896f keygen 3. McEliece’s binary operations keygen 1180468912 6688128 are very well suited for hardware. 625470504 6688128f keygen See 2018 Wang–Szefer– keygen 1109340668 6960119 Niederhagen. Isn’t this what’s 564570384 6960119f keygen most important for the future? 933422948 8192128 keygen 678860388 8192128f keygen
15 16 ait, you’re leaving out the 1. What evidence do we have Bytes com important cost! It’s crazy that this keygen time is params have such slow keygen!” a problem for applications? 348864 rams op cycles 2. Classic McEliece is designed 460896 for IND-CCA2 security, so 140870324 keygen 6688128 a key can be generated once and 82232360 348864f keygen 6960119 used a huge number of times. 441517292 keygen 8192128 282869316 460896f keygen 3. McEliece’s binary operations 348864 keygen 1180468912 6688128 are very well suited for hardware. 460896 625470504 6688128f keygen See 2018 Wang–Szefer– 6688128 keygen 1109340668 6960119 Niederhagen. Isn’t this what’s 6960119 564570384 6960119f keygen most important for the future? 8192128 933422948 8192128 keygen “It’s crazy 678860388 8192128f keygen
15 16 leaving out the 1. What evidence do we have Bytes communicat cost! It’s crazy that this keygen time is params object w keygen!” a problem for applications? ciphertext 348864 cycles 2. Classic McEliece is designed ciphertext 460896 for IND-CCA2 security, so 140870324 6688128 ciphertext keygen a key can be generated once and 82232360 6960119 ciphertext keygen used a huge number of times. 441517292 8192128 ciphertext keygen 282869316 keygen 3. McEliece’s binary operations key 348864 keygen 1180468912 are very well suited for hardware. key 460896 625470504 keygen See 2018 Wang–Szefer– 6688128 key keygen 1109340668 Niederhagen. Isn’t this what’s 6960119 key 564570384 keygen most important for the future? 8192128 key 933422948 keygen “It’s crazy to have 678860388 keygen
15 16 the 1. What evidence do we have Bytes communicated crazy that this keygen time is params object bytes eygen!” a problem for applications? ciphertext 128 348864 cycles 2. Classic McEliece is designed ciphertext 188 460896 for IND-CCA2 security, so 140870324 6688128 ciphertext 240 a key can be generated once and 82232360 6960119 ciphertext 226 used a huge number of times. 441517292 8192128 ciphertext 240 282869316 3. McEliece’s binary operations key 261120 348864 1180468912 are very well suited for hardware. key 524160 460896 625470504 See 2018 Wang–Szefer– 6688128 key 1044992 1109340668 Niederhagen. Isn’t this what’s 6960119 key 1047319 564570384 most important for the future? 8192128 key 1357824 933422948 “It’s crazy to have big keys!” 678860388
16 17 1. What evidence do we have Bytes communicated that this keygen time is params object bytes a problem for applications? ciphertext 128 348864 2. Classic McEliece is designed ciphertext 188 460896 for IND-CCA2 security, so 6688128 ciphertext 240 a key can be generated once and 6960119 ciphertext 226 used a huge number of times. 8192128 ciphertext 240 3. McEliece’s binary operations key 261120 348864 are very well suited for hardware. key 524160 460896 See 2018 Wang–Szefer– 6688128 key 1044992 Niederhagen. Isn’t this what’s 6960119 key 1047319 most important for the future? 8192128 key 1357824 “It’s crazy to have big keys!”
16 17 What evidence do we have Bytes communicated What evidence this keygen time is that these params object bytes roblem for applications? a problem ciphertext 128 348864 Classic McEliece is designed ciphertext 188 460896 D-CCA2 security, so 6688128 ciphertext 240 can be generated once and 6960119 ciphertext 226 huge number of times. 8192128 ciphertext 240 McEliece’s binary operations key 261120 348864 very well suited for hardware. key 524160 460896 2018 Wang–Szefer– 6688128 key 1044992 Niederhagen. Isn’t this what’s 6960119 key 1047319 important for the future? 8192128 key 1357824 “It’s crazy to have big keys!”
16 17 evidence do we have Bytes communicated What evidence do time is that these key sizes params object bytes applications? a problem for applications? ciphertext 128 348864 McEliece is designed ciphertext 188 460896 security, so 6688128 ciphertext 240 generated once and 6960119 ciphertext 226 number of times. 8192128 ciphertext 240 inary operations key 261120 348864 suited for hardware. key 524160 460896 ang–Szefer– 6688128 key 1044992 Isn’t this what’s 6960119 key 1047319 for the future? 8192128 key 1357824 “It’s crazy to have big keys!”
16 17 ave Bytes communicated What evidence do we have that these key sizes are params object bytes applications? a problem for applications? ciphertext 128 348864 designed ciphertext 188 460896 6688128 ciphertext 240 once and 6960119 ciphertext 226 times. 8192128 ciphertext 240 erations key 261120 348864 rdware. key 524160 460896 6688128 key 1044992 what’s 6960119 key 1047319 future? 8192128 key 1357824 “It’s crazy to have big keys!”
17 18 Bytes communicated What evidence do we have that these key sizes are params object bytes a problem for applications? ciphertext 128 348864 ciphertext 188 460896 6688128 ciphertext 240 6960119 ciphertext 226 8192128 ciphertext 240 key 261120 348864 key 524160 460896 6688128 key 1044992 6960119 key 1047319 8192128 key 1357824 “It’s crazy to have big keys!”
17 18 Bytes communicated What evidence do we have that these key sizes are params object bytes a problem for applications? ciphertext 128 348864 Compare to, e.g., web-page size. ciphertext 188 460896 6688128 ciphertext 240 httparchive.org statistics: 6960119 ciphertext 226 50% of web pages are > 1.8MB. 8192128 ciphertext 240 25% of web pages are > 3.5MB. 10% of web pages are > 6.5MB. key 261120 348864 The sizes keep growing. key 524160 460896 6688128 key 1044992 Typically browser receives one web 6960119 key 1047319 page from multiple servers, but 8192128 key 1357824 reuses servers for more pages. Is key size a big part of this? “It’s crazy to have big keys!”
17 18 communicated What evidence do we have 2015 McGrew that these key sizes are postquantum rams object bytes a problem for applications? Use standa ciphertext 128 techniques Compare to, e.g., web-page size. ciphertext 188 etc.) to reduce 6688128 ciphertext 240 httparchive.org statistics: communicating 6960119 ciphertext 226 50% of web pages are > 1.8MB. Each ciphertext 8192128 ciphertext 240 25% of web pages are > 3.5MB. the way 10% of web pages are > 6.5MB. key 261120 the server, The sizes keep growing. key 524160 can often 6688128 key 1044992 Typically browser receives one web much faster 6960119 key 1047319 page from multiple servers, but Again IND-CCA2 8192128 key 1357824 reuses servers for more pages. Is key size a big part of this? crazy to have big keys!”
17 18 ated What evidence do we have 2015 McGrew “Living that these key sizes are postquantum cryptography”: bytes a problem for applications? Use standard netw ciphertext 128 techniques (multicasts, Compare to, e.g., web-page size. ciphertext 188 etc.) to reduce cost ciphertext 240 httparchive.org statistics: communicating public ciphertext 226 50% of web pages are > 1.8MB. Each ciphertext has ciphertext 240 25% of web pages are > 3.5MB. the way between the 10% of web pages are > 6.5MB. 261120 the server, but public The sizes keep growing. 524160 can often be retrieved 1044992 Typically browser receives one web much faster local net 1047319 page from multiple servers, but Again IND-CCA2 is 1357824 reuses servers for more pages. Is key size a big part of this? have big keys!”
17 18 What evidence do we have 2015 McGrew “Living with that these key sizes are postquantum cryptography”: ytes a problem for applications? Use standard networking 128 techniques (multicasts, caching, Compare to, e.g., web-page size. 188 etc.) to reduce cost of 240 httparchive.org statistics: communicating public keys. 226 50% of web pages are > 1.8MB. Each ciphertext has to travel 240 25% of web pages are > 3.5MB. the way between the client and 10% of web pages are > 6.5MB. 261120 the server, but public keys The sizes keep growing. 524160 can often be retrieved through 1044992 Typically browser receives one web much faster local network. 1047319 page from multiple servers, but Again IND-CCA2 is critical. 1357824 reuses servers for more pages. Is key size a big part of this? eys!”
18 19 What evidence do we have 2015 McGrew “Living with that these key sizes are postquantum cryptography”: a problem for applications? Use standard networking techniques (multicasts, caching, Compare to, e.g., web-page size. etc.) to reduce cost of httparchive.org statistics: communicating public keys. 50% of web pages are > 1.8MB. Each ciphertext has to travel all 25% of web pages are > 3.5MB. the way between the client and 10% of web pages are > 6.5MB. the server, but public keys The sizes keep growing. can often be retrieved through Typically browser receives one web much faster local network. page from multiple servers, but Again IND-CCA2 is critical. reuses servers for more pages. Is key size a big part of this?
18 19 evidence do we have 2015 McGrew “Living with Denial of these key sizes are postquantum cryptography”: Standard roblem for applications? Use standard networking strategy: techniques (multicasts, caching, Compare to, e.g., web-page size. of connections etc.) to reduce cost of up all memo httparchive.org statistics: communicating public keys. for keeping of web pages are > 1.8MB. Each ciphertext has to travel all of web pages are > 3.5MB. SYN floo the way between the client and of web pages are > 6.5MB. Server is the server, but public keys sizes keep growing. some con can often be retrieved through ypically browser receives one web connections much faster local network. from multiple servers, but Again IND-CCA2 is critical. servers for more pages. size a big part of this?
18 19 do we have 2015 McGrew “Living with Denial of service sizes are postquantum cryptography”: Standard low-cost applications? Use standard networking strategy: make a huge techniques (multicasts, caching, e.g., web-page size. of connections to a etc.) to reduce cost of up all memory available httparchive.org statistics: communicating public keys. for keeping track of pages are > 1.8MB. Each ciphertext has to travel all pages are > 3.5MB. SYN flood, HTTP the way between the client and pages are > 6.5MB. Server is forced to the server, but public keys growing. some connections, can often be retrieved through wser receives one web connections from honest much faster local network. multiple servers, but Again IND-CCA2 is critical. r more pages. part of this?
18 19 2015 McGrew “Living with Denial of service postquantum cryptography”: Standard low-cost attack applications? Use standard networking strategy: make a huge numb techniques (multicasts, caching, eb-page size. of connections to a server, filling etc.) to reduce cost of up all memory available on server statistics: communicating public keys. for keeping track of connections. 1.8MB. Each ciphertext has to travel all 3.5MB. SYN flood, HTTP flood, etc. the way between the client and 6.5MB. Server is forced to stop serving the server, but public keys some connections, including can often be retrieved through one web connections from honest clients. much faster local network. servers, but Again IND-CCA2 is critical. pages. this?
19 20 2015 McGrew “Living with Denial of service postquantum cryptography”: Standard low-cost attack Use standard networking strategy: make a huge number techniques (multicasts, caching, of connections to a server, filling etc.) to reduce cost of up all memory available on server communicating public keys. for keeping track of connections. Each ciphertext has to travel all SYN flood, HTTP flood, etc. the way between the client and Server is forced to stop serving the server, but public keys some connections, including can often be retrieved through connections from honest clients. much faster local network. Again IND-CCA2 is critical.
19 20 2015 McGrew “Living with Denial of service postquantum cryptography”: Standard low-cost attack Use standard networking strategy: make a huge number techniques (multicasts, caching, of connections to a server, filling etc.) to reduce cost of up all memory available on server communicating public keys. for keeping track of connections. Each ciphertext has to travel all SYN flood, HTTP flood, etc. the way between the client and Server is forced to stop serving the server, but public keys some connections, including can often be retrieved through connections from honest clients. much faster local network. But some Internet protocols Again IND-CCA2 is critical. are not vulnerable to this attack.
19 20 McGrew “Living with Denial of service A tiny net ostquantum cryptography”: handles and Standard low-cost attack standard networking each incoming strategy: make a huge number techniques (multicasts, caching, without of connections to a server, filling to reduce cost of up all memory available on server communicating public keys. for keeping track of connections. ciphertext has to travel all SYN flood, HTTP flood, etc. y between the client and Server is forced to stop serving server, but public keys some connections, including often be retrieved through connections from honest clients. faster local network. But some Internet protocols IND-CCA2 is critical. are not vulnerable to this attack.
19 20 “Living with Denial of service A tiny network server cryptography”: handles and immediately Standard low-cost attack networking each incoming netw strategy: make a huge number (multicasts, caching, without allocating of connections to a server, filling cost of up all memory available on server public keys. for keeping track of connections. has to travel all SYN flood, HTTP flood, etc. the client and Server is forced to stop serving public keys some connections, including retrieved through connections from honest clients. cal network. But some Internet protocols IND-CCA2 is critical. are not vulnerable to this attack.
19 20 with Denial of service A tiny network server cryptography”: handles and immediately forgets Standard low-cost attack each incoming network pack strategy: make a huge number caching, without allocating any memo of connections to a server, filling up all memory available on server eys. for keeping track of connections. travel all SYN flood, HTTP flood, etc. client and Server is forced to stop serving some connections, including through connections from honest clients. rk. But some Internet protocols critical. are not vulnerable to this attack.
20 21 Denial of service A tiny network server handles and immediately forgets Standard low-cost attack each incoming network packet, strategy: make a huge number without allocating any memory. of connections to a server, filling up all memory available on server for keeping track of connections. SYN flood, HTTP flood, etc. Server is forced to stop serving some connections, including connections from honest clients. But some Internet protocols are not vulnerable to this attack.
Recommend
More recommend