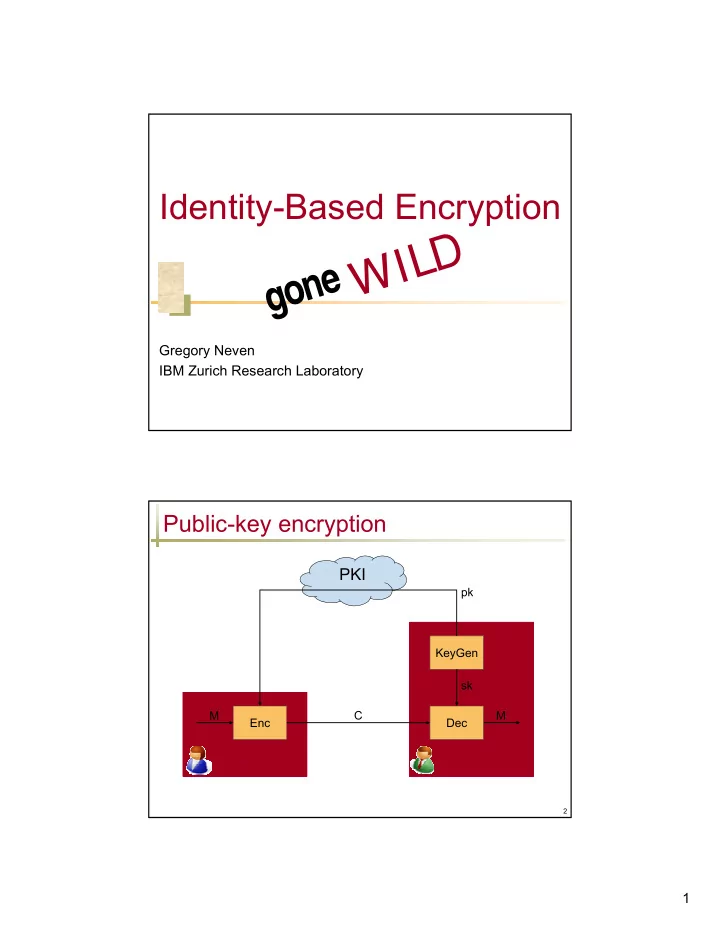

Identity-Based Encryption gone WILD Gregory Neven IBM Zurich Research Laboratory Public-key encryption PKI pk KeyGen sk M C M Enc Dec Sender (pk) Receiver (sk) 2 1
Identity-based encryption (IBE) [S84] Goal: Allow to encrypt based solely on the receiver’s identity Key distribution center (msk) msk Setup KeyDer mpk ID sk ID ID, M C M Enc Dec Sender (mpk) Receiver (sk ID ) 3 Bilinear maps � Concept of IBE due to Shamir (1984) � First efficient implementations [SK01, BF01] based on bilinear maps, aka pairings: Elliptic-curve groups G = (g), G T of prime order p Bilinear map e : G × G → G T so that e(g a ,g b ) = e(g,g) ab = e(g ab ,g) = e(g,g ab ) = e(g a ,g) b = … → DDH problem in G is easy: ? ? Given (g a ,g b ,Z), decide Z = g ab : e(g a ,g b ) = e(g,Z) → Bilinear DDH still assumed to be hard: ? Given (g a , g b , g c , Z), decide Z = e(g,g) abc 4 2
Applications of IBE � Encrypt email to ID = “bob@ibm.com” � Temporary keys, key revocation: ID = “bob@ibm.com, 2007” � User credentials: ID = “bob@ibm.com, role=Adminstrator” Credential is a decryption key → cryptographic policy enforcement � Encrypting to the future: ID = “ release-date ” Trusted “clock” publishes sk date on date � Searchable encryption 5 Searchable encryption (SE) [BDOP04] PKI pk KeyGen sk t W W’ C W Enc Test Trapd W’=W? Mail server Receiver (sk) Sender (pk) high bandwidth low bandwidth 6 3
[BDOP04, Searchable encryption from IBE ABC+05] Generic construction of SE from IBE: � SE.KeyGen = IBE.Setup � SE.Trapd = IBE.KeyDer so t W = sk ID=W � SE.Enc(W) = ( M , IBE.Enc(ID=W,M) ) for random M ? � SE.Test(t W , (M,C)) = ( IBE.Dec(t W ,C) = M ) � Security relies on “anonymity” of IBE meaning ciphertext does not reveal ID 7 Hierarchical IBE (HIBE) [GS02] Root (msk) ID 1 msk KeyDer sk (ID1) ID 2 ID 1 KeyDer Receiver 1 (sk ID1 ) sk (ID1,ID2) … M ID 2 Dec Receiver 2 (sk (ID1,ID2) ) C mpk, (ID 1 ,ID 2 ), M Enc Sender (mpk) 8 4
Application to encrypted email Email addresses as hierarchical identities bob@cs.univ.edu = (edu, univ, cs, bob) (edu, univ) can derive keys for � @ � .univ.edu (edu, univ, cs) can derive keys for � @cs.univ.edu 9 Temporarily searchable encryption [ABC+05] � Restrict validity of trapdoor in time � Trivial solution: encrypt to ID = “W || time ” ; t W = (sk W||1 ,…, sk W|| n ) � Logarithmic-size construction from HIBE: = t W valid for time periods 1,..,7 encrypt to ID = (W, …, i) W’ W … t W[1,7] 1 2 3 4 5 6 7 8 10 5
ECRYPT publications � Searchable encryption revisited: consistency properties, relation to anonymous IBE, and extensions. M. Abdalla, M. Bellare, D. Catalano, E. Kiltz, T. Lange, J. Malone-Lee, G. Neven, P. Paillier, and H. Shi. Crypto 2005, Journal of Cryptology 2008 Institutions involved: ENS, UCSD, DTU, U. Bristol, KUL, Gemalto 11 IBE with wildcards (WIBE) [ACD+05] Allow “wildcards” in recipient identity E.g., send encrypted email to � entire department: � @cs.univ.edu � entire university: � @ � .univ.edu � all computer scientists: � @cs. � .edu � all heads of department: head@ � .univ.edu � the world: � @ � . � . � 12 6
WIBE constructions � Generic WIBE from any HIBE: � Dedicated wildcard string “any ” � WIBE.sk (ID1,ID2) = ( HIBE.sk (ID1,ID2) , HIBE.sk (“any”,ID2) , HIBE.sk (ID1,“any”) , HIBE.sk (“any”, “any”) ) � WIBE.Enc((ID 1 , � ), M) = HIBE.Enc((ID 1 ,“any”), M) � WIBE.Dec : select correct sk (.,.) and HIBE.Dec Disadvantage: |WIBE.sk| = O(2 L ) � Direct constructions with |WIBE.sk| = O(L) 13 ECRYPT publications � Identity-based encryption gone wild. M. Abdalla, D. Catalano, A. Dent, J. Malone-Lee, G. Neven, and N. Smart. ICALP 2006 � Efficient chosen-ciphertext secure identity-based encryption with wildcards. J. Birkett, A. Dent, G. Neven, and J. Schuldt. ACISP 2007 Institutions involved: ENS, RHUL, U. Bristol, KUL 14 7
Wicked IBE [AKN07] � IBE with wildcard key derivation = WKD-IBE = “wicked” IBE ≈ dual of WIBE with wildcards in decryption keys e.g., derive keys for � anyone: � @ � . � . � � entire university: � @ � .univ.edu � all system admininstrators: sysadmin@ � .univ.edu � Applications to identity-based broadcast encryption � Combination: wildcards in keys and ciphertext 15 ECRYPT publications � Generalized key delegation for hierarchical identity-based encryption. Michel Abdalla, Eike Kiltz and Gregory Neven. ESORICS 2007 Institutions involved: ENS, CWI, KUL 16 8
Identity-based traitor tracing [ADM+07] Key distribution center (msk) Sender (mpk) msk mpk KeyDer Setup Enc List 1 , M C List 1 ,ID 1 sk ID1 List 1 List 2 … C M Dec C M Dec Receiver ID 1 (sk ID1 ) Receiver ID 2 (sk ID2 ) Receiver ID 3 (sk ID3 ) 17 Identity-based traitor tracing [ADM+07] Key distribution center (msk) Sender (mpk) msk mpk KeyDer Setup Enc List 1 , M C List 1 ,ID 1 sk ID1 List 1 List 2 … ID 2 ,ID 3 C Trace M Dec C M Dec Receiver ID 1 (sk ID1 ) Receiver ID 2 (sk ID2 ) Receiver ID 3 (sk ID3 ) 18 9
ECRYPT publications � Identity-based traitor tracing. M. Abdalla, A. Dent, J. Malone-Lee, G. Neven, D. Phan, and N. Smart. PKC 2007 Institutions involved: ENS, RHUL, U. Bristol, KUL, France Télécom 19 Conclusions � Several extensions to identity-based encryption � searchable encryption � wildcards � traitor tracing � Research retreats work � top-level research � international collaborations 20 10
Recommend
More recommend