
4 5 An oversimplified plan Strategy to eliminate proof errors: explain all of the target proofs Plan: Verify the security proofs— to a thoroughly audited program make sure there are no mistakes. that completely verifies proofs. Why verification is important: e.g., Asiacrypt 2004 Rogaway “OCB2” was standardized in 2009, completely broken in 2018. The attack exploited proof error. I did some sanity checks ( tiny part of full verification!) and found unproven theorems claimed by frodo , round5n1 , round5nd , saber ; also wrong hypotheses for newhope theorem.
4 5 An oversimplified plan Strategy to eliminate proof errors: explain all of the target proofs Plan: Verify the security proofs— to a thoroughly audited program make sure there are no mistakes. that completely verifies proofs. Why verification is important: My assessment of this strategy: e.g., Asiacrypt 2004 Rogaway • Status today: ≈ 0% completed. “OCB2” was standardized in 2009, completely broken in 2018. The attack exploited proof error. I did some sanity checks ( tiny part of full verification!) and found unproven theorems claimed by frodo , round5n1 , round5nd , saber ; also wrong hypotheses for newhope theorem.
4 5 An oversimplified plan Strategy to eliminate proof errors: explain all of the target proofs Plan: Verify the security proofs— to a thoroughly audited program make sure there are no mistakes. that completely verifies proofs. Why verification is important: My assessment of this strategy: e.g., Asiacrypt 2004 Rogaway • Status today: ≈ 0% completed. “OCB2” was standardized in • Progress is painful and slow. 2009, completely broken in 2018. Will we even reach 1% before The attack exploited proof error. post-quantum standardization? I did some sanity checks ( tiny part of full verification!) and found unproven theorems claimed by frodo , round5n1 , round5nd , saber ; also wrong hypotheses for newhope theorem.
4 5 An oversimplified plan Strategy to eliminate proof errors: explain all of the target proofs Plan: Verify the security proofs— to a thoroughly audited program make sure there are no mistakes. that completely verifies proofs. Why verification is important: My assessment of this strategy: e.g., Asiacrypt 2004 Rogaway • Status today: ≈ 0% completed. “OCB2” was standardized in • Progress is painful and slow. 2009, completely broken in 2018. Will we even reach 1% before The attack exploited proof error. post-quantum standardization? I did some sanity checks • Easier-to-use proof tools ( tiny part of full verification!) could make strategy work. and found unproven theorems claimed by frodo , round5n1 , round5nd , saber ; also wrong hypotheses for newhope theorem.
4 5 An oversimplified plan Strategy to eliminate proof errors: explain all of the target proofs Plan: Verify the security proofs— to a thoroughly audited program make sure there are no mistakes. that completely verifies proofs. Why verification is important: My assessment of this strategy: e.g., Asiacrypt 2004 Rogaway • Status today: ≈ 0% completed. “OCB2” was standardized in • Progress is painful and slow. 2009, completely broken in 2018. Will we even reach 1% before The attack exploited proof error. post-quantum standardization? I did some sanity checks • Easier-to-use proof tools ( tiny part of full verification!) could make strategy work. and found unproven theorems Backup strategies: Clean up claimed by frodo , round5n1 , proofs. Check proofs by hand. round5nd , saber ; also wrong Track bug categories, as in code. hypotheses for newhope theorem.
4 5 oversimplified plan Strategy to eliminate proof errors: Why call explain all of the target proofs Verify the security proofs— What “securit to a thoroughly audited program sure there are no mistakes. is not actually that completely verifies proofs. verification is important: My assessment of this strategy: Asiacrypt 2004 Rogaway • Status today: ≈ 0% completed. “OCB2” was standardized in • Progress is painful and slow. completely broken in 2018. Will we even reach 1% before attack exploited proof error. post-quantum standardization? some sanity checks • Easier-to-use proof tools part of full verification!) could make strategy work. found unproven theorems Backup strategies: Clean up claimed by frodo , round5n1 , proofs. Check proofs by hand. round5nd , saber ; also wrong Track bug categories, as in code. otheses for newhope theorem.
4 5 oversimplified plan Strategy to eliminate proof errors: Why call this “oversimplified”? explain all of the target proofs security proofs— What “security pro to a thoroughly audited program are no mistakes. is not actually securit that completely verifies proofs. is important: My assessment of this strategy: 2004 Rogaway • Status today: ≈ 0% completed. standardized in • Progress is painful and slow. completely broken in 2018. Will we even reach 1% before exploited proof error. post-quantum standardization? y checks • Easier-to-use proof tools full verification!) could make strategy work. roven theorems Backup strategies: Clean up , round5n1 , proofs. Check proofs by hand. ; also wrong Track bug categories, as in code. newhope theorem.
4 5 Strategy to eliminate proof errors: Why call this “oversimplified”? explain all of the target proofs roofs— What “security proofs” prove to a thoroughly audited program mistakes. is not actually security. that completely verifies proofs. rtant: My assessment of this strategy: way • Status today: ≈ 0% completed. in • Progress is painful and slow. 2018. Will we even reach 1% before of error. post-quantum standardization? • Easier-to-use proof tools verification!) could make strategy work. rems Backup strategies: Clean up round5n1 , proofs. Check proofs by hand. wrong Track bug categories, as in code. theorem.
5 6 Strategy to eliminate proof errors: Why call this “oversimplified”? explain all of the target proofs What “security proofs” prove to a thoroughly audited program is not actually security. that completely verifies proofs. My assessment of this strategy: • Status today: ≈ 0% completed. • Progress is painful and slow. Will we even reach 1% before post-quantum standardization? • Easier-to-use proof tools could make strategy work. Backup strategies: Clean up proofs. Check proofs by hand. Track bug categories, as in code.
5 6 Strategy to eliminate proof errors: Why call this “oversimplified”? explain all of the target proofs What “security proofs” prove to a thoroughly audited program is not actually security. that completely verifies proofs. Even with correct proofs, My assessment of this strategy: there are still risks of attacks. • Status today: ≈ 0% completed. We all rely on cryptanalysis • Progress is painful and slow. for analyzing remaining risks. Will we even reach 1% before post-quantum standardization? • Easier-to-use proof tools could make strategy work. Backup strategies: Clean up proofs. Check proofs by hand. Track bug categories, as in code.
5 6 Strategy to eliminate proof errors: Why call this “oversimplified”? explain all of the target proofs What “security proofs” prove to a thoroughly audited program is not actually security. that completely verifies proofs. Even with correct proofs, My assessment of this strategy: there are still risks of attacks. • Status today: ≈ 0% completed. We all rely on cryptanalysis • Progress is painful and slow. for analyzing remaining risks. Will we even reach 1% before Revised plan: post-quantum standardization? 1. Verify the “security proofs”. • Easier-to-use proof tools 2. Verify the cryptanalysis could make strategy work. of the risks left by the proofs. Backup strategies: Clean up Again clean up; check by hand; proofs. Check proofs by hand. track failure categories. Track bug categories, as in code.
5 6 Strategy to eliminate proof errors: Why call this “oversimplified”? Are attack-cost all of the target proofs How tho What “security proofs” prove thoroughly audited program of space is not actually security. completely verifies proofs. How tho Even with correct proofs, claimed assessment of this strategy: there are still risks of attacks. that work Status today: ≈ 0% completed. We all rely on cryptanalysis Do the cryptanalytic Progress is painful and slow. for analyzing remaining risks. match the we even reach 1% before Revised plan: ost-quantum standardization? Long histo 1. Verify the “security proofs”. Easier-to-use proof tools NSA overstated 2. Verify the cryptanalysis could make strategy work. L (1 = 2) optimalit of the risks left by the proofs. for facto Backup strategies: Clean up TLS Triple-DES-CBC Again clean up; check by hand; ofs. Check proofs by hand. without track failure categories. bug categories, as in code.
5 6 eliminate proof errors: Why call this “oversimplified”? Are attack-cost analyses target proofs How thorough is explo What “security proofs” prove audited program of space of optimizations? is not actually security. verifies proofs. How thorough is the Even with correct proofs, claimed barriers to of this strategy: there are still risks of attacks. that work for simila ≈ 0% completed. We all rely on cryptanalysis Do the cryptanalytic painful and slow. for analyzing remaining risks. match the proof risks? reach 1% before Revised plan: standardization? Long history of failures: 1. Verify the “security proofs”. roof tools NSA overstated DES 2. Verify the cryptanalysis strategy work. L (1 = 2) optimality of the risks left by the proofs. for factorization was strategies: Clean up TLS Triple-DES-CBC Again clean up; check by hand; roofs by hand. without Triple-DES track failure categories. categories, as in code.
5 6 of errors: Why call this “oversimplified”? Are attack-cost analyses correct? roofs How thorough is exploration What “security proofs” prove rogram of space of optimizations? is not actually security. roofs. How thorough is the study of Even with correct proofs, claimed barriers to speedups strategy: there are still risks of attacks. that work for similar problems? completed. We all rely on cryptanalysis Do the cryptanalytic targets slow. for analyzing remaining risks. match the proof risks? etc. efore Revised plan: rdization? Long history of failures: e.g., 1. Verify the “security proofs”. NSA overstated DES attack 2. Verify the cryptanalysis rk. L (1 = 2) optimality conjecture of the risks left by the proofs. for factorization was wrong; up TLS Triple-DES-CBC was brok Again clean up; check by hand; hand. without Triple-DES attack; etc. track failure categories. code.
6 7 Why call this “oversimplified”? Are attack-cost analyses correct? How thorough is exploration What “security proofs” prove of space of optimizations? is not actually security. How thorough is the study of Even with correct proofs, claimed barriers to speedups there are still risks of attacks. that work for similar problems? We all rely on cryptanalysis Do the cryptanalytic targets for analyzing remaining risks. match the proof risks? etc. Revised plan: Long history of failures: e.g., 1. Verify the “security proofs”. NSA overstated DES attack cost; 2. Verify the cryptanalysis L (1 = 2) optimality conjecture of the risks left by the proofs. for factorization was wrong; TLS Triple-DES-CBC was broken Again clean up; check by hand; without Triple-DES attack; etc. track failure categories.
6 7 call this “oversimplified”? Are attack-cost analyses correct? Why bother How thorough is exploration “security proofs” prove Plan without of space of optimizations? actually security. Verify crypta How thorough is the study of with correct proofs, claimed barriers to speedups are still risks of attacks. that work for similar problems? rely on cryptanalysis Do the cryptanalytic targets analyzing remaining risks. match the proof risks? etc. Revised plan: Long history of failures: e.g., erify the “security proofs”. NSA overstated DES attack cost; erify the cryptanalysis L (1 = 2) optimality conjecture risks left by the proofs. for factorization was wrong; TLS Triple-DES-CBC was broken clean up; check by hand; without Triple-DES attack; etc. failure categories.
6 7 “oversimplified”? Are attack-cost analyses correct? Why bother with p How thorough is exploration proofs” prove Plan without proofs of space of optimizations? security. Verify cryptanalysis How thorough is the study of rrect proofs, claimed barriers to speedups risks of attacks. that work for similar problems? cryptanalysis Do the cryptanalytic targets remaining risks. match the proof risks? etc. Long history of failures: e.g., “security proofs”. NSA overstated DES attack cost; cryptanalysis L (1 = 2) optimality conjecture by the proofs. for factorization was wrong; TLS Triple-DES-CBC was broken check by hand; without Triple-DES attack; etc. categories.
6 7 “oversimplified”? Are attack-cost analyses correct? Why bother with proofs? How thorough is exploration rove Plan without proofs is simpler: of space of optimizations? Verify cryptanalysis of the KEMs. How thorough is the study of claimed barriers to speedups attacks. that work for similar problems? cryptanalysis Do the cryptanalytic targets risks. match the proof risks? etc. Long history of failures: e.g., ofs”. NSA overstated DES attack cost; L (1 = 2) optimality conjecture ofs. for factorization was wrong; TLS Triple-DES-CBC was broken hand; without Triple-DES attack; etc.
7 8 Are attack-cost analyses correct? Why bother with proofs? How thorough is exploration Plan without proofs is simpler: of space of optimizations? Verify cryptanalysis of the KEMs. How thorough is the study of claimed barriers to speedups that work for similar problems? Do the cryptanalytic targets match the proof risks? etc. Long history of failures: e.g., NSA overstated DES attack cost; L (1 = 2) optimality conjecture for factorization was wrong; TLS Triple-DES-CBC was broken without Triple-DES attack; etc.
7 8 Are attack-cost analyses correct? Why bother with proofs? How thorough is exploration Plan without proofs is simpler: of space of optimizations? Verify cryptanalysis of the KEMs. How thorough is the study of But sometimes the proofs claimed barriers to speedups reduce cost of cryptanalysis. that work for similar problems? Do the cryptanalytic targets match the proof risks? etc. Long history of failures: e.g., NSA overstated DES attack cost; L (1 = 2) optimality conjecture for factorization was wrong; TLS Triple-DES-CBC was broken without Triple-DES attack; etc.
7 8 Are attack-cost analyses correct? Why bother with proofs? How thorough is exploration Plan without proofs is simpler: of space of optimizations? Verify cryptanalysis of the KEMs. How thorough is the study of But sometimes the proofs claimed barriers to speedups reduce cost of cryptanalysis. that work for similar problems? Do the cryptanalytic targets Sometimes this outweighs match the proof risks? etc. cost to verify proofs: reduces cost of thorough security review. Long history of failures: e.g., Hopefully less chance of disaster. NSA overstated DES attack cost; L (1 = 2) optimality conjecture for factorization was wrong; TLS Triple-DES-CBC was broken without Triple-DES attack; etc.
7 8 Are attack-cost analyses correct? Why bother with proofs? How thorough is exploration Plan without proofs is simpler: of space of optimizations? Verify cryptanalysis of the KEMs. How thorough is the study of But sometimes the proofs claimed barriers to speedups reduce cost of cryptanalysis. that work for similar problems? Do the cryptanalytic targets Sometimes this outweighs match the proof risks? etc. cost to verify proofs: reduces cost of thorough security review. Long history of failures: e.g., Hopefully less chance of disaster. NSA overstated DES attack cost; L (1 = 2) optimality conjecture This paper’s verification plan for factorization was wrong; skips proofs that clearly fail TLS Triple-DES-CBC was broken to reduce cost of cryptanalysis: without Triple-DES attack; etc. e.g., frodo seed “reduction”.
7 8 attack-cost analyses correct? Why bother with proofs? Risks not thorough is exploration Plan without proofs is simpler: A “securit space of optimizations? Verify cryptanalysis of the KEMs. security thorough is the study of against all But sometimes the proofs claimed barriers to speedups assuming reduce cost of cryptanalysis. ork for similar problems? for underlying the cryptanalytic targets Sometimes this outweighs the proof risks? etc. cost to verify proofs: reduces cost of thorough security review. history of failures: e.g., Hopefully less chance of disaster. overstated DES attack cost; 2) optimality conjecture This paper’s verification plan factorization was wrong; skips proofs that clearly fail riple-DES-CBC was broken to reduce cost of cryptanalysis: without Triple-DES attack; etc. e.g., frodo seed “reduction”.
7 8 analyses correct? Why bother with proofs? Risks not ruled out exploration Plan without proofs is simpler: A “security proof” optimizations? Verify cryptanalysis of the KEMs. security level – for the study of against all attacks But sometimes the proofs to speedups assuming security reduce cost of cryptanalysis. imilar problems? for underlying problem cryptanalytic targets Sometimes this outweighs risks? etc. cost to verify proofs: reduces cost of thorough security review. failures: e.g., Hopefully less chance of disaster. DES attack cost; optimality conjecture This paper’s verification plan was wrong; skips proofs that clearly fail riple-DES-CBC was broken to reduce cost of cryptanalysis: riple-DES attack; etc. e.g., frodo seed “reduction”.
7 8 correct? Why bother with proofs? Risks not ruled out by proofs ration Plan without proofs is simpler: A “security proof” guarantees Verify cryptanalysis of the KEMs. security level – for system X of against all attacks of type T But sometimes the proofs eedups assuming security level – ′ reduce cost of cryptanalysis. roblems? for underlying problem P . rgets Sometimes this outweighs etc. cost to verify proofs: reduces cost of thorough security review. e.g., Hopefully less chance of disaster. attack cost; conjecture This paper’s verification plan wrong; skips proofs that clearly fail broken to reduce cost of cryptanalysis: attack; etc. e.g., frodo seed “reduction”.
8 9 Why bother with proofs? Risks not ruled out by proofs Plan without proofs is simpler: A “security proof” guarantees Verify cryptanalysis of the KEMs. security level – for system X against all attacks of type T But sometimes the proofs assuming security level – ′ reduce cost of cryptanalysis. for underlying problem P . Sometimes this outweighs cost to verify proofs: reduces cost of thorough security review. Hopefully less chance of disaster. This paper’s verification plan skips proofs that clearly fail to reduce cost of cryptanalysis: e.g., frodo seed “reduction”.
8 9 Why bother with proofs? Risks not ruled out by proofs Plan without proofs is simpler: A “security proof” guarantees Verify cryptanalysis of the KEMs. security level – for system X against all attacks of type T But sometimes the proofs assuming security level – ′ reduce cost of cryptanalysis. for underlying problem P . Sometimes this outweighs Risk #1: P does not reach cost to verify proofs: reduces security level – ′ . cost of thorough security review. Hopefully less chance of disaster. This paper’s verification plan skips proofs that clearly fail to reduce cost of cryptanalysis: e.g., frodo seed “reduction”.
8 9 Why bother with proofs? Risks not ruled out by proofs Plan without proofs is simpler: A “security proof” guarantees Verify cryptanalysis of the KEMs. security level – for system X against all attacks of type T But sometimes the proofs assuming security level – ′ reduce cost of cryptanalysis. for underlying problem P . Sometimes this outweighs Risk #1: P does not reach cost to verify proofs: reduces security level – ′ . cost of thorough security review. Hopefully less chance of disaster. Risk #2 (looseness): – is below claimed security level of X . This paper’s verification plan skips proofs that clearly fail to reduce cost of cryptanalysis: e.g., frodo seed “reduction”.
8 9 Why bother with proofs? Risks not ruled out by proofs Plan without proofs is simpler: A “security proof” guarantees Verify cryptanalysis of the KEMs. security level – for system X against all attacks of type T But sometimes the proofs assuming security level – ′ reduce cost of cryptanalysis. for underlying problem P . Sometimes this outweighs Risk #1: P does not reach cost to verify proofs: reduces security level – ′ . cost of thorough security review. Hopefully less chance of disaster. Risk #2 (looseness): – is below claimed security level of X . This paper’s verification plan skips proofs that clearly fail Risk #3: There are faster to reduce cost of cryptanalysis: attacks outside type T . e.g., frodo seed “reduction”.
8 9 Why bother with proofs? Risks not ruled out by proofs Plan without proofs is simpler: A “security proof” guarantees Verify cryptanalysis of the KEMs. security level – for system X against all attacks of type T But sometimes the proofs assuming security level – ′ reduce cost of cryptanalysis. for underlying problem P . Sometimes this outweighs Risk #1: P does not reach cost to verify proofs: reduces security level – ′ . cost of thorough security review. Hopefully less chance of disaster. Risk #2 (looseness): – is below claimed security level of X . This paper’s verification plan skips proofs that clearly fail Risk #3: There are faster to reduce cost of cryptanalysis: attacks outside type T . e.g., frodo seed “reduction”. Risk #4: Proof is incorrect.
8 9 other with proofs? Risks not ruled out by proofs Targets fo without proofs is simpler: A “security proof” guarantees Attack O cryptanalysis of the KEMs. security level – for system X security against all attacks of type T sometimes the proofs assuming security level – ′ cost of cryptanalysis. for underlying problem P . Sometimes this outweighs Risk #1: P does not reach verify proofs: reduces security level – ′ . of thorough security review. efully less chance of disaster. Risk #2 (looseness): – is below claimed security level of X . paper’s verification plan roofs that clearly fail Risk #3: There are faster reduce cost of cryptanalysis: attacks outside type T . frodo seed “reduction”. Risk #4: Proof is incorrect.
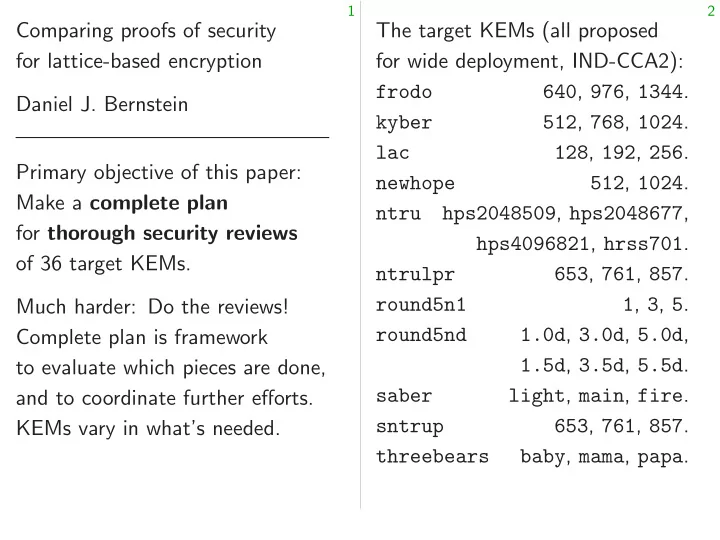
8 9 with proofs? Risks not ruled out by proofs Targets for lattice ofs is simpler: A “security proof” guarantees Attack OW-Passive nalysis of the KEMs. security level – for system X security of the 36 co against all attacks of type T the proofs assuming security level – ′ cryptanalysis. for underlying problem P . outweighs Risk #1: P does not reach roofs: reduces security level – ′ . security review. hance of disaster. Risk #2 (looseness): – is below claimed security level of X . verification plan that clearly fail Risk #3: There are faster of cryptanalysis: attacks outside type T . “reduction”. Risk #4: Proof is incorrect.
8 9 Risks not ruled out by proofs Targets for lattice cryptanalysis simpler: A “security proof” guarantees Attack OW-Passive (“OW-CP KEMs. security level – for system X security of the 36 core PKEs. against all attacks of type T assuming security level – ′ cryptanalysis. for underlying problem P . Risk #1: P does not reach reduces security level – ′ . review. disaster. Risk #2 (looseness): – is below claimed security level of X . plan fail Risk #3: There are faster cryptanalysis: attacks outside type T . “reduction”. Risk #4: Proof is incorrect.
9 10 Risks not ruled out by proofs Targets for lattice cryptanalysis A “security proof” guarantees Attack OW-Passive (“OW-CPA”) security level – for system X security of the 36 core PKEs. against all attacks of type T assuming security level – ′ for underlying problem P . Risk #1: P does not reach security level – ′ . Risk #2 (looseness): – is below claimed security level of X . Risk #3: There are faster attacks outside type T . Risk #4: Proof is incorrect.
9 10 Risks not ruled out by proofs Targets for lattice cryptanalysis A “security proof” guarantees Attack OW-Passive (“OW-CPA”) security level – for system X security of the 36 core PKEs. against all attacks of type T For some targets: Attack assuming security level – ′ IND-CPA security of core PKEs. for underlying problem P . Risk #1: P does not reach security level – ′ . Risk #2 (looseness): – is below claimed security level of X . Risk #3: There are faster attacks outside type T . Risk #4: Proof is incorrect.
9 10 Risks not ruled out by proofs Targets for lattice cryptanalysis A “security proof” guarantees Attack OW-Passive (“OW-CPA”) security level – for system X security of the 36 core PKEs. against all attacks of type T For some targets: Attack assuming security level – ′ IND-CPA security of core PKEs. for underlying problem P . For some targets: Attack Risk #1: P does not reach pseudorandom multipliers. security level – ′ . Risk #2 (looseness): – is below claimed security level of X . Risk #3: There are faster attacks outside type T . Risk #4: Proof is incorrect.
9 10 Risks not ruled out by proofs Targets for lattice cryptanalysis A “security proof” guarantees Attack OW-Passive (“OW-CPA”) security level – for system X security of the 36 core PKEs. against all attacks of type T For some targets: Attack assuming security level – ′ IND-CPA security of core PKEs. for underlying problem P . For some targets: Attack Risk #1: P does not reach pseudorandom multipliers. security level – ′ . For some targets: KEM proofs Risk #2 (looseness): – is below are loose. Find faster attacks. claimed security level of X . Risk #3: There are faster attacks outside type T . Risk #4: Proof is incorrect.
9 10 Risks not ruled out by proofs Targets for lattice cryptanalysis A “security proof” guarantees Attack OW-Passive (“OW-CPA”) security level – for system X security of the 36 core PKEs. against all attacks of type T For some targets: Attack assuming security level – ′ IND-CPA security of core PKEs. for underlying problem P . For some targets: Attack Risk #1: P does not reach pseudorandom multipliers. security level – ′ . For some targets: KEM proofs Risk #2 (looseness): – is below are loose. Find faster attacks. claimed security level of X . Also, some KEM “proofs” Risk #3: There are faster rely on unproven conjectures. attacks outside type T . Risk #4: Proof is incorrect.
9 10 Risks not ruled out by proofs Targets for lattice cryptanalysis A “security proof” guarantees Attack OW-Passive (“OW-CPA”) security level – for system X security of the 36 core PKEs. against all attacks of type T For some targets: Attack assuming security level – ′ IND-CPA security of core PKEs. for underlying problem P . For some targets: Attack Risk #1: P does not reach pseudorandom multipliers. security level – ′ . For some targets: KEM proofs Risk #2 (looseness): – is below are loose. Find faster attacks. claimed security level of X . Also, some KEM “proofs” Risk #3: There are faster rely on unproven conjectures. attacks outside type T . For all targets: KEM proofs Risk #4: Proof is incorrect. allow non-ROM attacks.
9 10 not ruled out by proofs Targets for lattice cryptanalysis The core “security proof” guarantees Attack OW-Passive (“OW-CPA”) Key gene y level – for system X security of the 36 core PKEs. • Table 8.6: against all attacks of type T • Table 8.7: For some targets: Attack assuming security level – ′ • Table 8.8: IND-CPA security of core PKEs. underlying problem P . For some targets: Attack #1: P does not reach pseudorandom multipliers. y level – ′ . For some targets: KEM proofs #2 (looseness): – is below are loose. Find faster attacks. claimed security level of X . Also, some KEM “proofs” #3: There are faster rely on unproven conjectures. attacks outside type T . For all targets: KEM proofs #4: Proof is incorrect. allow non-ROM attacks.
9 10 out by proofs Targets for lattice cryptanalysis The core PKEs (“ P of” guarantees Attack OW-Passive (“OW-CPA”) Key generation: for system X security of the 36 core PKEs. • Table 8.6: Public ttacks of type T • Table 8.7: Short For some targets: Attack y level – ′ • Table 8.8: Public IND-CPA security of core PKEs. roblem P . For some targets: Attack es not reach pseudorandom multipliers. For some targets: KEM proofs eness): – is below are loose. Find faster attacks. level of X . Also, some KEM “proofs” are faster rely on unproven conjectures. type T . For all targets: KEM proofs is incorrect. allow non-ROM attacks.
9 10 ofs Targets for lattice cryptanalysis The core PKEs (“ P ”) rantees Attack OW-Passive (“OW-CPA”) Key generation: X security of the 36 core PKEs. • Table 8.6: Public multiplier T • Table 8.7: Short secret a . For some targets: Attack • Table 8.8: Public A ≈ aG . IND-CPA security of core PKEs. For some targets: Attack reach pseudorandom multipliers. For some targets: KEM proofs below are loose. Find faster attacks. . Also, some KEM “proofs” rely on unproven conjectures. For all targets: KEM proofs rrect. allow non-ROM attacks.
10 11 Targets for lattice cryptanalysis The core PKEs (“ P ”) Attack OW-Passive (“OW-CPA”) Key generation: security of the 36 core PKEs. • Table 8.6: Public multiplier G . • Table 8.7: Short secret a . For some targets: Attack • Table 8.8: Public A ≈ aG . IND-CPA security of core PKEs. For some targets: Attack pseudorandom multipliers. For some targets: KEM proofs are loose. Find faster attacks. Also, some KEM “proofs” rely on unproven conjectures. For all targets: KEM proofs allow non-ROM attacks.
10 11 Targets for lattice cryptanalysis The core PKEs (“ P ”) Attack OW-Passive (“OW-CPA”) Key generation: security of the 36 core PKEs. • Table 8.6: Public multiplier G . • Table 8.7: Short secret a . For some targets: Attack • Table 8.8: Public A ≈ aG . IND-CPA security of core PKEs. Encryption: Short secret b ; For some targets: Attack public ciphertext B ≈ Gb pseudorandom multipliers. (or B ≈ Gb= 3 or B ≈ 3 Gb ). For some targets: KEM proofs are loose. Find faster attacks. Also, some KEM “proofs” rely on unproven conjectures. For all targets: KEM proofs allow non-ROM attacks.
10 11 Targets for lattice cryptanalysis The core PKEs (“ P ”) Attack OW-Passive (“OW-CPA”) Key generation: security of the 36 core PKEs. • Table 8.6: Public multiplier G . • Table 8.7: Short secret a . For some targets: Attack • Table 8.8: Public A ≈ aG . IND-CPA security of core PKEs. Encryption: Short secret b ; For some targets: Attack public ciphertext B ≈ Gb pseudorandom multipliers. (or B ≈ Gb= 3 or B ≈ 3 Gb ). For some targets: KEM proofs That’s it for Quotient NTRU. are loose. Find faster attacks. Also, some KEM “proofs” rely on unproven conjectures. For all targets: KEM proofs allow non-ROM attacks.
10 11 Targets for lattice cryptanalysis The core PKEs (“ P ”) Attack OW-Passive (“OW-CPA”) Key generation: security of the 36 core PKEs. • Table 8.6: Public multiplier G . • Table 8.7: Short secret a . For some targets: Attack • Table 8.8: Public A ≈ aG . IND-CPA security of core PKEs. Encryption: Short secret b ; For some targets: Attack public ciphertext B ≈ Gb pseudorandom multipliers. (or B ≈ Gb= 3 or B ≈ 3 Gb ). For some targets: KEM proofs That’s it for Quotient NTRU. are loose. Find faster attacks. Also, some KEM “proofs” More for Product NTRU: rely on unproven conjectures. • Table 8.9: Public C ≈ Ab + M . • Table 8.10: Secret M . For all targets: KEM proofs allow non-ROM attacks.
10 11 rgets for lattice cryptanalysis The core PKEs (“ P ”) OW-Pass OW-Passive (“OW-CPA”) Key generation: Quotient y of the 36 core PKEs. • Table 8.6: Public multiplier G . asks for • Table 8.7: Short secret a . 2003 Nao some targets: Attack • Table 8.8: Public A ≈ aG . IND-CPA security of core PKEs. Encryption: Short secret b ; some targets: Attack public ciphertext B ≈ Gb random multipliers. (or B ≈ Gb= 3 or B ≈ 3 Gb ). some targets: KEM proofs That’s it for Quotient NTRU. ose. Find faster attacks. some KEM “proofs” More for Product NTRU: unproven conjectures. • Table 8.9: Public C ≈ Ab + M . • Table 8.10: Secret M . targets: KEM proofs non-ROM attacks.
10 11 lattice cryptanalysis The core PKEs (“ P ”) OW-Passive vs. IND-CP assive (“OW-CPA”) Key generation: Quotient NTRU ( ntru 36 core PKEs. • Table 8.6: Public multiplier G . asks for OW-Passive • Table 8.7: Short secret a . 2003 Naor: this is rgets: Attack • Table 8.8: Public A ≈ aG . security of core PKEs. Encryption: Short secret b ; rgets: Attack public ciphertext B ≈ Gb ultipliers. (or B ≈ Gb= 3 or B ≈ 3 Gb ). rgets: KEM proofs That’s it for Quotient NTRU. faster attacks. “proofs” More for Product NTRU: conjectures. • Table 8.9: Public C ≈ Ab + M . • Table 8.10: Secret M . KEM proofs attacks.
10 11 cryptanalysis The core PKEs (“ P ”) OW-Passive vs. IND-CPA (“dist”) W-CPA”) Key generation: Quotient NTRU ( ntru , sntrup PKEs. • Table 8.6: Public multiplier G . asks for OW-Passive cryptanalysis. • Table 8.7: Short secret a . 2003 Naor: this is “falsifiable”. • Table 8.8: Public A ≈ aG . PKEs. Encryption: Short secret b ; public ciphertext B ≈ Gb (or B ≈ Gb= 3 or B ≈ 3 Gb ). roofs That’s it for Quotient NTRU. attacks. More for Product NTRU: conjectures. • Table 8.9: Public C ≈ Ab + M . • Table 8.10: Secret M . ofs
11 12 The core PKEs (“ P ”) OW-Passive vs. IND-CPA (“dist”) Key generation: Quotient NTRU ( ntru , sntrup ) • Table 8.6: Public multiplier G . asks for OW-Passive cryptanalysis. • Table 8.7: Short secret a . 2003 Naor: this is “falsifiable”. • Table 8.8: Public A ≈ aG . Encryption: Short secret b ; public ciphertext B ≈ Gb (or B ≈ Gb= 3 or B ≈ 3 Gb ). That’s it for Quotient NTRU. More for Product NTRU: • Table 8.9: Public C ≈ Ab + M . • Table 8.10: Secret M .
11 12 The core PKEs (“ P ”) OW-Passive vs. IND-CPA (“dist”) Key generation: Quotient NTRU ( ntru , sntrup ) • Table 8.6: Public multiplier G . asks for OW-Passive cryptanalysis. • Table 8.7: Short secret a . 2003 Naor: this is “falsifiable”. • Table 8.8: Public A ≈ aG . Product NTRU ( ntrulpr and Encryption: Short secret b ; systems not named after NTRU) public ciphertext B ≈ Gb asks for IND-CPA cryptanalysis. (or B ≈ Gb= 3 or B ≈ 3 Gb ). Lower security than OW-Passive? Only “somewhat falsifiable”. That’s it for Quotient NTRU. More for Product NTRU: • Table 8.9: Public C ≈ Ab + M . • Table 8.10: Secret M .
11 12 The core PKEs (“ P ”) OW-Passive vs. IND-CPA (“dist”) Key generation: Quotient NTRU ( ntru , sntrup ) • Table 8.6: Public multiplier G . asks for OW-Passive cryptanalysis. • Table 8.7: Short secret a . 2003 Naor: this is “falsifiable”. • Table 8.8: Public A ≈ aG . Product NTRU ( ntrulpr and Encryption: Short secret b ; systems not named after NTRU) public ciphertext B ≈ Gb asks for IND-CPA cryptanalysis. (or B ≈ Gb= 3 or B ≈ 3 Gb ). Lower security than OW-Passive? Only “somewhat falsifiable”. That’s it for Quotient NTRU. Compare 2006 Goldreich: “What More for Product NTRU: concerns us about” DDH is that • Table 8.9: Public C ≈ Ab + M . “DDH is less simple than DH” • Table 8.10: Secret M . making it “harder to evaluate.”
11 12 re PKEs (“ P ”) OW-Passive vs. IND-CPA (“dist”) Pseudorandom generation: Quotient NTRU ( ntru , sntrup ) Product able 8.6: Public multiplier G . asks for OW-Passive cryptanalysis. into PKE able 8.7: Short secret a . 2003 Naor: this is “falsifiable”. pseudorandomly able 8.8: Public A ≈ aG . Product NTRU ( ntrulpr and Encryption: Short secret b ; systems not named after NTRU) ciphertext B ≈ Gb asks for IND-CPA cryptanalysis. ≈ Gb= 3 or B ≈ 3 Gb ). Lower security than OW-Passive? Only “somewhat falsifiable”. it for Quotient NTRU. Compare 2006 Goldreich: “What for Product NTRU: concerns us about” DDH is that able 8.9: Public C ≈ Ab + M . “DDH is less simple than DH” able 8.10: Secret M . making it “harder to evaluate.”
11 12 (“ P ”) OW-Passive vs. IND-CPA (“dist”) Pseudorandom mul Quotient NTRU ( ntru , sntrup ) Product NTRU: convert Public multiplier G . asks for OW-Passive cryptanalysis. into PKE that builds rt secret a . 2003 Naor: this is “falsifiable”. pseudorandomly from Public A ≈ aG . Product NTRU ( ntrulpr and rt secret b ; systems not named after NTRU) B ≈ Gb asks for IND-CPA cryptanalysis. r B ≈ 3 Gb ). Lower security than OW-Passive? Only “somewhat falsifiable”. Quotient NTRU. Compare 2006 Goldreich: “What duct NTRU: concerns us about” DDH is that Public C ≈ Ab + M . “DDH is less simple than DH” Secret M . making it “harder to evaluate.”
11 12 OW-Passive vs. IND-CPA (“dist”) Pseudorandom multipliers (“ROM2”) Quotient NTRU ( ntru , sntrup ) Product NTRU: convert core multiplier G . asks for OW-Passive cryptanalysis. into PKE that builds multiplier a . 2003 Naor: this is “falsifiable”. pseudorandomly from public G . Product NTRU ( ntrulpr and ; systems not named after NTRU) asks for IND-CPA cryptanalysis. ). Lower security than OW-Passive? Only “somewhat falsifiable”. NTRU. Compare 2006 Goldreich: “What concerns us about” DDH is that Ab + M . “DDH is less simple than DH” making it “harder to evaluate.”
12 13 OW-Passive vs. IND-CPA (“dist”) Pseudorandom multipliers (“ROM2”) Quotient NTRU ( ntru , sntrup ) Product NTRU: convert core PKE asks for OW-Passive cryptanalysis. into PKE that builds multiplier G 2003 Naor: this is “falsifiable”. pseudorandomly from public seed. Product NTRU ( ntrulpr and systems not named after NTRU) asks for IND-CPA cryptanalysis. Lower security than OW-Passive? Only “somewhat falsifiable”. Compare 2006 Goldreich: “What concerns us about” DDH is that “DDH is less simple than DH” making it “harder to evaluate.”
12 13 OW-Passive vs. IND-CPA (“dist”) Pseudorandom multipliers (“ROM2”) Quotient NTRU ( ntru , sntrup ) Product NTRU: convert core PKE asks for OW-Passive cryptanalysis. into PKE that builds multiplier G 2003 Naor: this is “falsifiable”. pseudorandomly from public seed. Product NTRU ( ntrulpr and saber , round5n1 , round5nd systems not named after NTRU) claim that this provably preserves asks for IND-CPA cryptanalysis. security assuming PRG/PRF. Lower security than OW-Passive? Only “somewhat falsifiable”. Compare 2006 Goldreich: “What concerns us about” DDH is that “DDH is less simple than DH” making it “harder to evaluate.”
12 13 OW-Passive vs. IND-CPA (“dist”) Pseudorandom multipliers (“ROM2”) Quotient NTRU ( ntru , sntrup ) Product NTRU: convert core PKE asks for OW-Passive cryptanalysis. into PKE that builds multiplier G 2003 Naor: this is “falsifiable”. pseudorandomly from public seed. Product NTRU ( ntrulpr and saber , round5n1 , round5nd systems not named after NTRU) claim that this provably preserves asks for IND-CPA cryptanalysis. security assuming PRG/PRF. Lower security than OW-Passive? I dispute this. Need non-ROM Only “somewhat falsifiable”. cryptanalysis for all these PKEs. Compare 2006 Goldreich: “What Proofs cover only ROM attacks. concerns us about” DDH is that Must modify theorem statements. “DDH is less simple than DH” making it “harder to evaluate.”
12 13 OW-Passive vs. IND-CPA (“dist”) Pseudorandom multipliers (“ROM2”) Quotient NTRU ( ntru , sntrup ) Product NTRU: convert core PKE asks for OW-Passive cryptanalysis. into PKE that builds multiplier G 2003 Naor: this is “falsifiable”. pseudorandomly from public seed. Product NTRU ( ntrulpr and saber , round5n1 , round5nd systems not named after NTRU) claim that this provably preserves asks for IND-CPA cryptanalysis. security assuming PRG/PRF. Lower security than OW-Passive? I dispute this. Need non-ROM Only “somewhat falsifiable”. cryptanalysis for all these PKEs. Compare 2006 Goldreich: “What Proofs cover only ROM attacks. concerns us about” DDH is that Must modify theorem statements. “DDH is less simple than DH” frodo seed “reduction”: Useless. making it “harder to evaluate.” Still need non-ROM cryptanalysis.
12 13 assive vs. IND-CPA (“dist”) Pseudorandom multipliers (“ROM2”) More hashin Quotient NTRU ( ntru , sntrup ) Product NTRU: convert core PKE Want the r OW-Passive cryptanalysis. into PKE that builds multiplier G to provid Naor: this is “falsifiable”. pseudorandomly from public seed. The proofs duct NTRU ( ntrulpr and saber , round5n1 , round5nd even assuming systems not named after NTRU) claim that this provably preserves of the underlying r IND-CPA cryptanalysis. security assuming PRG/PRF. The proofs security than OW-Passive? ROM IND-CCA2 I dispute this. Need non-ROM “somewhat falsifiable”. cryptanalysis for all these PKEs. Issue for Compare 2006 Goldreich: “What Proofs cover only ROM attacks. and for Quotient concerns us about” DDH is that Must modify theorem statements. is less simple than DH” frodo seed “reduction”: Useless. making it “harder to evaluate.” Still need non-ROM cryptanalysis.
12 13 IND-CPA (“dist”) Pseudorandom multipliers (“ROM2”) More hashing (“ROM”) ( ntru , sntrup ) Product NTRU: convert core PKE Want the target KEMs assive cryptanalysis. into PKE that builds multiplier G to provide IND-CCA2 is “falsifiable”. pseudorandomly from public seed. The proofs don’t give ( ntrulpr and saber , round5n1 , round5nd even assuming securit named after NTRU) claim that this provably preserves of the underlying PKEs. A cryptanalysis. security assuming PRG/PRF. The proofs are limited than OW-Passive? ROM IND-CCA2 attacks. I dispute this. Need non-ROM “somewhat falsifiable”. cryptanalysis for all these PKEs. Issue for Product NTRU Goldreich: “What Proofs cover only ROM attacks. and for Quotient NTRU. out” DDH is that Must modify theorem statements. simple than DH” frodo seed “reduction”: Useless. rder to evaluate.” Still need non-ROM cryptanalysis.
12 13 (“dist”) Pseudorandom multipliers (“ROM2”) More hashing (“ROM”) sntrup ) Product NTRU: convert core PKE Want the target KEMs cryptanalysis. into PKE that builds multiplier G to provide IND-CCA2 securit “falsifiable”. pseudorandomly from public seed. The proofs don’t give this, and saber , round5n1 , round5nd even assuming security NTRU) claim that this provably preserves of the underlying PKEs. cryptanalysis. security assuming PRG/PRF. The proofs are limited to assive? ROM IND-CCA2 attacks. I dispute this. Need non-ROM falsifiable”. cryptanalysis for all these PKEs. Issue for Product NTRU “What Proofs cover only ROM attacks. and for Quotient NTRU. is that Must modify theorem statements. DH” frodo seed “reduction”: Useless. evaluate.” Still need non-ROM cryptanalysis.
13 14 Pseudorandom multipliers (“ROM2”) More hashing (“ROM”) Product NTRU: convert core PKE Want the target KEMs into PKE that builds multiplier G to provide IND-CCA2 security. pseudorandomly from public seed. The proofs don’t give this, saber , round5n1 , round5nd even assuming security claim that this provably preserves of the underlying PKEs. security assuming PRG/PRF. The proofs are limited to ROM IND-CCA2 attacks. I dispute this. Need non-ROM cryptanalysis for all these PKEs. Issue for Product NTRU Proofs cover only ROM attacks. and for Quotient NTRU. Must modify theorem statements. frodo seed “reduction”: Useless. Still need non-ROM cryptanalysis.
13 14 Pseudorandom multipliers (“ROM2”) More hashing (“ROM”) Product NTRU: convert core PKE Want the target KEMs into PKE that builds multiplier G to provide IND-CCA2 security. pseudorandomly from public seed. The proofs don’t give this, saber , round5n1 , round5nd even assuming security claim that this provably preserves of the underlying PKEs. security assuming PRG/PRF. The proofs are limited to ROM IND-CCA2 attacks. I dispute this. Need non-ROM cryptanalysis for all these PKEs. Issue for Product NTRU Proofs cover only ROM attacks. and for Quotient NTRU. Must modify theorem statements. For all target KEMs, need non- frodo seed “reduction”: Useless. ROM IND-CCA2 cryptanalysis. Still need non-ROM cryptanalysis.
13 14 Pseudorandom multipliers (“ROM2”) More hashing (“ROM”) Decryption duct NTRU: convert core PKE Want the target KEMs 2017 Hofheinz–H¨ PKE that builds multiplier G to provide IND-CCA2 security. proofs do randomly from public seed. CCA2 attacks The proofs don’t give this, even if the , round5n1 , round5nd even assuming security that this provably preserves of the underlying PKEs. Q : numb y assuming PRG/PRF. The proofs are limited to ‹ : failure ROM IND-CCA2 attacks. dispute this. Need non-ROM cryptanalysis for all these PKEs. Issue for Product NTRU cover only ROM attacks. and for Quotient NTRU. modify theorem statements. For all target KEMs, need non- seed “reduction”: Useless. ROM IND-CCA2 cryptanalysis. need non-ROM cryptanalysis.
13 14 ultipliers (“ROM2”) More hashing (“ROM”) Decryption failures convert core PKE Want the target KEMs 2017 Hofheinz–H¨ ovelmanns–Kiltz builds multiplier G to provide IND-CCA2 security. proofs do not rule from public seed. CCA2 attacks with The proofs don’t give this, even if the PKEs a , round5nd even assuming security rovably preserves of the underlying PKEs. Q : number of hash assuming PRG/PRF. The proofs are limited to ‹ : failure probabilit ROM IND-CCA2 attacks. Need non-ROM all these PKEs. Issue for Product NTRU only ROM attacks. and for Quotient NTRU. theorem statements. For all target KEMs, need non- “reduction”: Useless. ROM IND-CCA2 cryptanalysis. non-ROM cryptanalysis.
13 14 (“ROM2”) More hashing (“ROM”) Decryption failures (“fail”/“c core PKE Want the target KEMs 2017 Hofheinz–H¨ ovelmanns–Kiltz multiplier G to provide IND-CCA2 security. proofs do not rule out ROM public seed. CCA2 attacks with probabilit The proofs don’t give this, even if the PKEs are secure. even assuming security round5nd reserves of the underlying PKEs. Q : number of hash calls. PRG/PRF. The proofs are limited to ‹ : failure probability. ROM IND-CCA2 attacks. non-ROM PKEs. Issue for Product NTRU attacks. and for Quotient NTRU. statements. For all target KEMs, need non- Useless. ROM IND-CCA2 cryptanalysis. cryptanalysis.
14 15 More hashing (“ROM”) Decryption failures (“fail”/“conj”) Want the target KEMs 2017 Hofheinz–H¨ ovelmanns–Kiltz to provide IND-CCA2 security. proofs do not rule out ROM IND- CCA2 attacks with probability Q‹ , The proofs don’t give this, even if the PKEs are secure. even assuming security of the underlying PKEs. Q : number of hash calls. The proofs are limited to ‹ : failure probability. ROM IND-CCA2 attacks. Issue for Product NTRU and for Quotient NTRU. For all target KEMs, need non- ROM IND-CCA2 cryptanalysis.
14 15 More hashing (“ROM”) Decryption failures (“fail”/“conj”) Want the target KEMs 2017 Hofheinz–H¨ ovelmanns–Kiltz to provide IND-CCA2 security. proofs do not rule out ROM IND- CCA2 attacks with probability Q‹ , The proofs don’t give this, even if the PKEs are secure. even assuming security of the underlying PKEs. Q : number of hash calls. The proofs are limited to ‹ : failure probability. ROM IND-CCA2 attacks. ‹ = 0 proven for 10 KEMs: Issue for Product NTRU ntru , ntrulpr , sntrup . (Also, and for Quotient NTRU. simpler ROM IND-CCA2 proof.) For all target KEMs, need non- ROM IND-CCA2 cryptanalysis.
14 15 More hashing (“ROM”) Decryption failures (“fail”/“conj”) Want the target KEMs 2017 Hofheinz–H¨ ovelmanns–Kiltz to provide IND-CCA2 security. proofs do not rule out ROM IND- CCA2 attacks with probability Q‹ , The proofs don’t give this, even if the PKEs are secure. even assuming security of the underlying PKEs. Q : number of hash calls. The proofs are limited to ‹ : failure probability. ROM IND-CCA2 attacks. ‹ = 0 proven for 10 KEMs: Issue for Product NTRU ntru , ntrulpr , sntrup . (Also, and for Quotient NTRU. simpler ROM IND-CCA2 proof.) For all target KEMs, need non- frodo640 , kyber512 prove ‹ ≤ 2 − 128 with security goal 2 128 . ROM IND-CCA2 cryptanalysis. frodo976 proves ‹ ≤ 2 − 192 .
14 15 hashing (“ROM”) Decryption failures (“fail”/“conj”) The other Security the target KEMs 2017 Hofheinz–H¨ ovelmanns–Kiltz without rovide IND-CCA2 security. proofs do not rule out ROM IND- So need CCA2 attacks with probability Q‹ , roofs don’t give this, even if the PKEs are secure. assuming security underlying PKEs. Q : number of hash calls. roofs are limited to ‹ : failure probability. IND-CCA2 attacks. ‹ = 0 proven for 10 KEMs: for Product NTRU ntru , ntrulpr , sntrup . (Also, r Quotient NTRU. simpler ROM IND-CCA2 proof.) target KEMs, need non- frodo640 , kyber512 prove ‹ ≤ 2 − 128 with security goal 2 128 . IND-CCA2 cryptanalysis. frodo976 proves ‹ ≤ 2 − 192 .
14 15 (“ROM”) Decryption failures (“fail”/“conj”) The other 23 KEMs: Security goal 2 k KEMs 2017 Hofheinz–H¨ ovelmanns–Kiltz without proof that IND-CCA2 security. proofs do not rule out ROM IND- So need CCA cryptanalysis. CCA2 attacks with probability Q‹ , ’t give this, even if the PKEs are secure. security underlying PKEs. Q : number of hash calls. limited to ‹ : failure probability. attacks. ‹ = 0 proven for 10 KEMs: duct NTRU ntru , ntrulpr , sntrup . (Also, Quotient NTRU. simpler ROM IND-CCA2 proof.) KEMs, need non- frodo640 , kyber512 prove ‹ ≤ 2 − 128 with security goal 2 128 . cryptanalysis. frodo976 proves ‹ ≤ 2 − 192 .
14 15 Decryption failures (“fail”/“conj”) The other 23 KEMs: Security goal 2 k 2017 Hofheinz–H¨ ovelmanns–Kiltz without proof that ‹ ≤ 2 − k . security. proofs do not rule out ROM IND- So need CCA cryptanalysis. CCA2 attacks with probability Q‹ , this, even if the PKEs are secure. Q : number of hash calls. ‹ : failure probability. ‹ = 0 proven for 10 KEMs: ntru , ntrulpr , sntrup . (Also, simpler ROM IND-CCA2 proof.) non- frodo640 , kyber512 prove ‹ ≤ 2 − 128 with security goal 2 128 . cryptanalysis. frodo976 proves ‹ ≤ 2 − 192 .
15 16 Decryption failures (“fail”/“conj”) The other 23 KEMs: Security goal 2 k 2017 Hofheinz–H¨ ovelmanns–Kiltz without proof that ‹ ≤ 2 − k . proofs do not rule out ROM IND- So need CCA cryptanalysis. CCA2 attacks with probability Q‹ , even if the PKEs are secure. Q : number of hash calls. ‹ : failure probability. ‹ = 0 proven for 10 KEMs: ntru , ntrulpr , sntrup . (Also, simpler ROM IND-CCA2 proof.) frodo640 , kyber512 prove ‹ ≤ 2 − 128 with security goal 2 128 . frodo976 proves ‹ ≤ 2 − 192 .
15 16 Decryption failures (“fail”/“conj”) The other 23 KEMs: Security goal 2 k 2017 Hofheinz–H¨ ovelmanns–Kiltz without proof that ‹ ≤ 2 − k . proofs do not rule out ROM IND- So need CCA cryptanalysis. CCA2 attacks with probability Q‹ , even if the PKEs are secure. Main issues in these 23 KEMs: Q : number of hash calls. • 14 KEMs do not claim ‹ : failure probability. that ‹ is small enough. ‹ = 0 proven for 10 KEMs: ntru , ntrulpr , sntrup . (Also, simpler ROM IND-CCA2 proof.) frodo640 , kyber512 prove ‹ ≤ 2 − 128 with security goal 2 128 . frodo976 proves ‹ ≤ 2 − 192 .
15 16 Decryption failures (“fail”/“conj”) The other 23 KEMs: Security goal 2 k 2017 Hofheinz–H¨ ovelmanns–Kiltz without proof that ‹ ≤ 2 − k . proofs do not rule out ROM IND- So need CCA cryptanalysis. CCA2 attacks with probability Q‹ , even if the PKEs are secure. Main issues in these 23 KEMs: Q : number of hash calls. • 14 KEMs do not claim ‹ : failure probability. that ‹ is small enough. ‹ = 0 proven for 10 KEMs: • 15 KEMs conjecture ‹ ≤ · · · ntru , ntrulpr , sntrup . (Also, without claiming proof. simpler ROM IND-CCA2 proof.) frodo640 , kyber512 prove ‹ ≤ 2 − 128 with security goal 2 128 . frodo976 proves ‹ ≤ 2 − 192 .
15 16 Decryption failures (“fail”/“conj”) The other 23 KEMs: Security goal 2 k 2017 Hofheinz–H¨ ovelmanns–Kiltz without proof that ‹ ≤ 2 − k . proofs do not rule out ROM IND- So need CCA cryptanalysis. CCA2 attacks with probability Q‹ , even if the PKEs are secure. Main issues in these 23 KEMs: Q : number of hash calls. • 14 KEMs do not claim ‹ : failure probability. that ‹ is small enough. ‹ = 0 proven for 10 KEMs: • 15 KEMs conjecture ‹ ≤ · · · ntru , ntrulpr , sntrup . (Also, without claiming proof. simpler ROM IND-CCA2 proof.) • 5 KEMs have proofs but do not frodo640 , kyber512 prove clearly use correct ‹ definition. ‹ ≤ 2 − 128 with security goal 2 128 . (LEDA uses wrong definition.) frodo976 proves ‹ ≤ 2 − 192 .
15 16 Decryption failures (“fail”/“conj”) The other 23 KEMs: What ab Security goal 2 k Hofheinz–H¨ ovelmanns–Kiltz Consider without proof that ‹ ≤ 2 − k . do not rule out ROM IND- for each So need CCA cryptanalysis. attacks with probability Q‹ , if the PKEs are secure. Main issues in these 23 KEMs: number of hash calls. • 14 KEMs do not claim failure probability. that ‹ is small enough. proven for 10 KEMs: • 15 KEMs conjecture ‹ ≤ · · · ntrulpr , sntrup . (Also, without claiming proof. simpler ROM IND-CCA2 proof.) • 5 KEMs have proofs but do not frodo640 , kyber512 prove clearly use correct ‹ definition. 128 with security goal 2 128 . (LEDA uses wrong definition.) frodo976 proves ‹ ≤ 2 − 192 .
15 16 failures (“fail”/“conj”) The other 23 KEMs: What about quantum Security goal 2 k Hofheinz–H¨ ovelmanns–Kiltz Consider quantum without proof that ‹ ≤ 2 − k . rule out ROM IND- for each cryptanalytic So need CCA cryptanalysis. with probability Q‹ , PKEs are secure. Main issues in these 23 KEMs: hash calls. • 14 KEMs do not claim robability. that ‹ is small enough. 10 KEMs: • 15 KEMs conjecture ‹ ≤ · · · sntrup . (Also, without claiming proof. IND-CCA2 proof.) • 5 KEMs have proofs but do not kyber512 prove clearly use correct ‹ definition. security goal 2 128 . (LEDA uses wrong definition.) roves ‹ ≤ 2 − 192 .
15 16 ”/“conj”) The other 23 KEMs: What about quantum attacks? Security goal 2 k ovelmanns–Kiltz Consider quantum computers without proof that ‹ ≤ 2 − k . ROM IND- for each cryptanalytic target. So need CCA cryptanalysis. robability Q‹ , secure. Main issues in these 23 KEMs: • 14 KEMs do not claim that ‹ is small enough. KEMs: • 15 KEMs conjecture ‹ ≤ · · · (Also, without claiming proof. roof.) • 5 KEMs have proofs but do not rove clearly use correct ‹ definition. goal 2 128 . (LEDA uses wrong definition.) 192 .
16 17 The other 23 KEMs: What about quantum attacks? Security goal 2 k Consider quantum computers without proof that ‹ ≤ 2 − k . for each cryptanalytic target. So need CCA cryptanalysis. Main issues in these 23 KEMs: • 14 KEMs do not claim that ‹ is small enough. • 15 KEMs conjecture ‹ ≤ · · · without claiming proof. • 5 KEMs have proofs but do not clearly use correct ‹ definition. (LEDA uses wrong definition.)
16 17 The other 23 KEMs: What about quantum attacks? Security goal 2 k Consider quantum computers without proof that ‹ ≤ 2 − k . for each cryptanalytic target. So need CCA cryptanalysis. When hashing is involved, Main issues in these 23 KEMs: analyze three types of attacks: • 14 KEMs do not claim (1) ROM attacks. that ‹ is small enough. (2) Non-ROM QROM attacks. (3) Non-QROM attacks. • 15 KEMs conjecture ‹ ≤ · · · without claiming proof. • 5 KEMs have proofs but do not clearly use correct ‹ definition. (LEDA uses wrong definition.)
16 17 The other 23 KEMs: What about quantum attacks? Security goal 2 k Consider quantum computers without proof that ‹ ≤ 2 − k . for each cryptanalytic target. So need CCA cryptanalysis. When hashing is involved, Main issues in these 23 KEMs: analyze three types of attacks: • 14 KEMs do not claim (1) ROM attacks. that ‹ is small enough. (2) Non-ROM QROM attacks. (3) Non-QROM attacks. • 15 KEMs conjecture ‹ ≤ · · · without claiming proof. Sometimes proofs eliminate #1. Ongoing efforts to extend proofs • 5 KEMs have proofs but do not to similarly eliminate #2. clearly use correct ‹ definition. Most QROM proofs are loose, (LEDA uses wrong definition.) but see 2019 Bindel–Hamburg– H¨ ulsing–Persichetti.
16 17 other 23 KEMs: What about quantum attacks? What ab Security goal 2 k Consider quantum computers Each KEM without proof that ‹ ≤ 2 − k . for each cryptanalytic target. of single-user need CCA cryptanalysis. When hashing is involved, issues in these 23 KEMs: analyze three types of attacks: KEMs do not claim (1) ROM attacks. ‹ is small enough. (2) Non-ROM QROM attacks. (3) Non-QROM attacks. KEMs conjecture ‹ ≤ · · · without claiming proof. Sometimes proofs eliminate #1. Ongoing efforts to extend proofs KEMs have proofs but do not to similarly eliminate #2. rly use correct ‹ definition. Most QROM proofs are loose, A uses wrong definition.) but see 2019 Bindel–Hamburg– H¨ ulsing–Persichetti.
16 17 KEMs: What about quantum attacks? What about multi-user Consider quantum computers Each KEM has quantitative that ‹ ≤ 2 − k . for each cryptanalytic target. of single-user securit cryptanalysis. When hashing is involved, these 23 KEMs: analyze three types of attacks: not claim (1) ROM attacks. enough. (2) Non-ROM QROM attacks. (3) Non-QROM attacks. conjecture ‹ ≤ · · · claiming proof. Sometimes proofs eliminate #1. Ongoing efforts to extend proofs proofs but do not to similarly eliminate #2. rrect ‹ definition. Most QROM proofs are loose, wrong definition.) but see 2019 Bindel–Hamburg– H¨ ulsing–Persichetti.
16 17 What about quantum attacks? What about multi-user attacks? Consider quantum computers Each KEM has quantitative k . for each cryptanalytic target. of single-user security level – cryptanalysis. When hashing is involved, KEMs: analyze three types of attacks: (1) ROM attacks. (2) Non-ROM QROM attacks. (3) Non-QROM attacks. · · · Sometimes proofs eliminate #1. Ongoing efforts to extend proofs do not to similarly eliminate #2. definition. Most QROM proofs are loose, definition.) but see 2019 Bindel–Hamburg– H¨ ulsing–Persichetti.
Recommend
More recommend