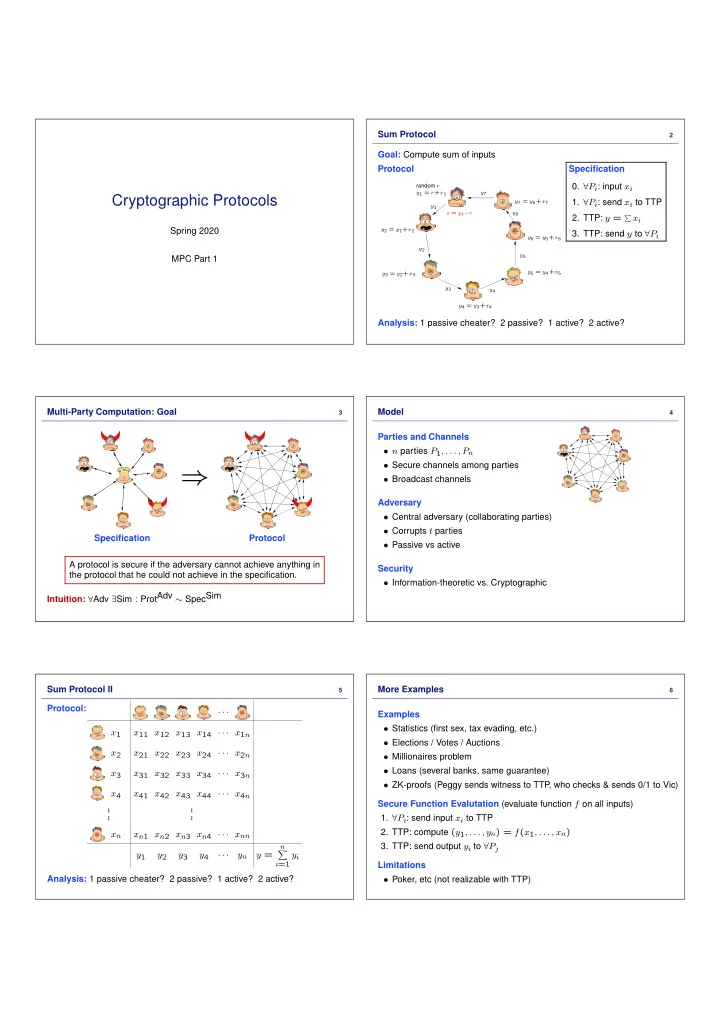

Sum Protocol 2 Goal: Compute sum of inputs Protocol Specification 0. ∀ P i : input x i random r y 1 = r + x 1 y 7 Cryptographic Protocols 1. ∀ P i : send x i to TTP y 7 = y 6 + x 7 y 1 � x i s = y 7 − r y 6 2. TTP: y = Spring 2020 y 2 = y 1 + x 2 3. TTP: send y to ∀ P i y 6 = y 5 + x 6 y 2 y 5 MPC Part 1 y 5 = y 4 + x 5 y 3 = y 2 + x 3 y 3 y 4 y 4 = y 3 + x 4 Analysis: 1 passive cheater? 2 passive? 1 active? 2 active? Multi-Party Computation: Goal Model 3 4 Parties and Channels • n parties P 1 , . . . , P n • Secure channels among parties ⇒ • Broadcast channels Adversary • Central adversary (collaborating parties) • Corrupts t parties Specification Protocol • Passive vs active A protocol is secure if the adversary cannot achieve anything in Security the protocol that he could not achieve in the specification. • Information-theoretic vs. Cryptographic Intuition: ∀ Adv ∃ Sim : ProtAdv ∼ SpecSim Sum Protocol II More Examples 5 6 Protocol: · · · Examples • Statistics (first sex, tax evading, etc.) x 1 x 11 x 12 x 13 x 14 · · · x 1 n • Elections / Votes / Auctions x 2 x 21 x 22 x 23 x 24 · · · x 2 n • Millionaires problem • Loans (several banks, same guarantee) x 3 x 31 x 32 x 33 x 34 · · · x 3 n • ZK-proofs (Peggy sends witness to TTP , who checks & sends 0/1 to Vic) x 4 x 41 x 42 x 43 x 44 · · · x 4 n Secure Function Evalutation (evaluate function f on all inputs) . . . . . . . . . . . . 1. ∀ P i : send input x i to TTP 2. TTP: compute ( y 1 , . . . , y n ) = f ( x 1 , . . . , x n ) x n x n 1 x n 2 x n 3 x n 4 · · · x nn 3. TTP: send output y i to ∀ P j n y 1 y 2 y 3 y 4 · · · y n y = � y i i =1 Limitations Analysis: 1 passive cheater? 2 passive? 1 active? 2 active? • Poker, etc (not realizable with TTP)
Known Results Oblivious Transfer 7 8 Rabin-OT Sender Receiver r =0: s − → Setting Condition Literature s r ∈ R { 0 , 1 } − → r =1: ⊥ Cryptographic, passive t < n [GMW87] Cryptographic, active t < n/ 2 [GMW87] 1-2-OT Sender Receiver Information-theoretic, passive t < n/ 2 [BGW88,CCD88] ← − b − s 0 , s 1 → s b − → Information-theoretic, active t < n/ 3 [BGW88,CCD88] Information-theoretic, active t < n/ 2 [RB89,Bea91] assuming broadcast 1- k -OT Sender Receiver ← − i s 1 , .., s k − → s i − → 1-2-OST based on RSA and AES MPC from OT 9 10 Sender Receiver Truth table: Starting Point a b c Messages s 0 , s 1 Selector b ∈ { 0 , 1 } • 2 parties Alice and Bob 0 0 17 0 1 23 • Inputs a ∈ A and b ∈ B Generate RSA-Keys 0 2 8 • Fixed function f : A × B → C 1 0 17 n 0 , e 0 , d 0 and n 1 , e 1 , d 1 1 1 10 n 0 , e 0 , n 1 , e 1 1 2 − 4 with n 0 ≈ n 1 ✲ 2 0 . . . 2 1 . . . k at random, Protocol u u = k e b (mod n b ) ✛ 1. Alice sends [ f ( a, b 1 ) | f ( a, b 2 ) | . . . | f ( a, b ℓ )] via OT k 0 = u d 0 2. Bob selects b -th value (mod n 0 ) k 1 = u d 1 (mod n 1 ) Analysis: • Security • Efficiency y 0 = AES k 0 ( s 0 ) y 0 , y 1 s b = AES − 1 Extension: 3 parties . . . y 1 = AES k 1 ( s 1 ) k ( y b ) ✲ Multi-Party Computation: Goal II Multi-Party Computation: Goal II 11 12 ⇒ ⇒ Trusted party Simulating players . . . • Receive input • n players: P = { P 1 , . . . , P n } • ⊕ and ⊗ over finite field F • Players can ⊕ and ⊗ in F Specification Protocol • Give output • Players can communicate
Sum Protocol III Secret-Sharing Schemes – Definition 13 14 Protocol: Intuition · · · • Dealer D can share a secret s among parties P x 1 x 11 x 12 x 13 x 14 · · · x 1 n • Qualified subsets of P can reconstruct s (w/o D ) • Access structure Γ ⊆ 2 P x 2 x 21 x 22 x 23 x 24 · · · x 2 n Definition x 3 x 31 x 32 x 33 x 34 · · · x 3 n A secret-sharing scheme for parties P and access structure Γ x 4 x 41 x 42 x 43 x 44 · · · x 4 n is a pair of protocols ( S HARE , R ECONSTRUCT ) , s.t. . . . . . . • Correctness: . . . . . . 1. After S HARE , there is a unique value s ′ , x n x n 1 x n 2 x n 3 x n 4 · · · x nn where s ′ = s (the dealer’s input) if the dealer is honest n 2. After R ECONSTRUCT ( M ) , if M ∈ Γ , all players in M know s ′ y = � y 1 y 2 y 3 y 4 · · · y n y i i =1 • Privacy: After S HARE , non-qualified sets have no information about s Analysis: 1 passive cheater? 2 passive? 1 active? 2 active? Secret-Sharing Schemes – Examples Shamir’s Secret-Sharing Scheme (1/3) 15 16 Goal Example 1 • n parties, k needed for reconstruction • Parties P • Threshold access structure Γ = { M ⊆ P : | M | ≥ k } • Γ = {P} (only all parties jointly can reconstruct) � x i = s , send x i to P i • S HARE : select random x 1 , . . . , x n with Idea • R ECONSTRUCT : Obvious • Random polynomial f of degree d is defined by d + 1 points • s = f (0) = secret, party P i gets share s i = f ( α i ) for fixed α i Example 2 • Degree d = k − 1 ⇒ k parties can reconstruct, k − 1 cannot • Parties P , arbitrary access structure Γ s 2 s 1 • S HARE : ∀ M i ∈ Γ : select random { x ij } P j ∈ Γ , send x ij to P j ∈ Γ f ( x ) s 3 s • R ECONSTRUCT : Obvious s n α 1 α 2 α 3 α n Shamir’s Secret-Sharing Scheme (2/3) Shamir’s Secret-Sharing Scheme (3/3) 17 18 Starting Point: To each party P i , some unique α i ∈ F \ { 0 } is assigned. Analysis for passive adversary: S HARE 1. D : choose random f with f (0) = s and deg( f ) ≤ d Correctness (i.e., choose random r 1 , . . . , r d , let f ( x ) = s + r 1 x + . . . + r d x d ) • 1: by inspection, s ′ = f (0) 2. D : send s i = f ( α i ) to ∀ P i • 2: due to Lagrange interpolation (given | M | ≥ k = d + 1 ) R ECONSTRUCT Privacy 1. ∀ P i : send s i to P • For ≤ d = k − 1 shares, every secret s is “compatible” (same #polys) 2. P : compute s with Lagrange interpolation: • ⇒ adversary with < k shares obtains no information about s . n n x − α j � � f ( x ) = λ i ( x ) s i , where λ i ( x ) = . Note α i − α j i =1 j =1 j � = i • Degree is at most d , not exactly d n n − α j hence s = � w i s i , where w i = λ i (0) = � . • Otherwise privacy violation α i − α j i =1 j =1 j � = i
Linear Secret-Sharing Schemes MPC Passive: Secret-Sharing and Addition 19 20 Definition: Secret-Sharing is linear, if each share s i = L i ( s, r 1 , . . . , r ℓ ) : Setting s 1 A 10 A 11 · · · A 1 ℓ • n parties, t corrupted (passive), t < n/ 2 s s 2 A 20 A 21 · · · A 2 ℓ r 1 = · Secret Sharing . . . . . . . . . . . . . . . • Shamir-Sharing with degree t r ℓ s n A n 0 A n 1 · · · A nℓ • ⇒ any t (corrupted) parties do not learn anything Addition [ s 1 , . . . , s n ] = A · [ s, r 0 , . . . , r ℓ ] Addition and Linear Functions s ′ s ′ s ′ , r ′ r ′ [ 1 , . . . , ] = A · [ 0 , . . . , ] n • Shamir-Sharing is linear ⇒ apply linear function on shares ℓ [ s 1 + s ′ 1 , . . . , s n + s ′ n ] = A · [ s + s ′ , r 0 + r ′ 0 , . . . , r ℓ + r ′ ℓ ] • a, b, . . . shared by a 1 , ..., a n , b 1 , ..., b n , etc. • Every P i computes c i = L ( a i , b i , . . . ) Shamir Sharing is linear 1 α 1 . . . α d • c 1 , ..., c n is a sharing of c = L ( a, b, . . . ) 1 . . . . . . . . A = . . . . (Van der Monde Matrix) 1 α n . . . α d n MPC Passive: Multiplication Passive Protocol 21 22 Share input Reconstruct Output Starting Point: a, b shared by a 1 , ..., a n , b 1 , ..., b n 0. P i has input s . 0. a is shared by a 1 , ..., a n . 1. P i : select r 1 , ..., r t at random. 1. ∀ P j : send a j to P i . Idea � s 1 s � r 1 2. P i : comp. a = L ( a 1 , ..., a n ) . . • Every P i computes d i = a i · b i 2. P i : comp. . = A . . . . . s n r t • Observe: d 1 , . . . , d n is some-kind-of sharing of c = a · b 3. P i : send s j to every P j . n • Could compute c from d 1 , . . . , d n : c = � w i d i (Lagrange) i =1 Addition and Linear Functions • Compute c as MPC: Every P i has input d i , compute (sharing of) c 0. a, b, . . . are shared by a 1 , ..., a n , b 1 , ..., b n , etc. 1. ∀ P i : compute c i = L ( a i , b i , . . . ) . Multiplication Protocol 1. ∀ P i : compute d i = a i b i . Multiplication 2. ∀ P i : share d i → d i 1 , . . . , d in . 0. a , b are shared by a 1 , ..., a n , b 1 , ..., b n . 3. ∀ P j : compute c j = w 1 d 1 j + . . . + w n d nj . 1. ∀ P i : compute d i = a i b i . 2. ∀ P i : share d i → d i 1 , . . . , d in . 3. ∀ P j : compute c j = L ( d 1 j , . . . , d nj ) .
Recommend
More recommend