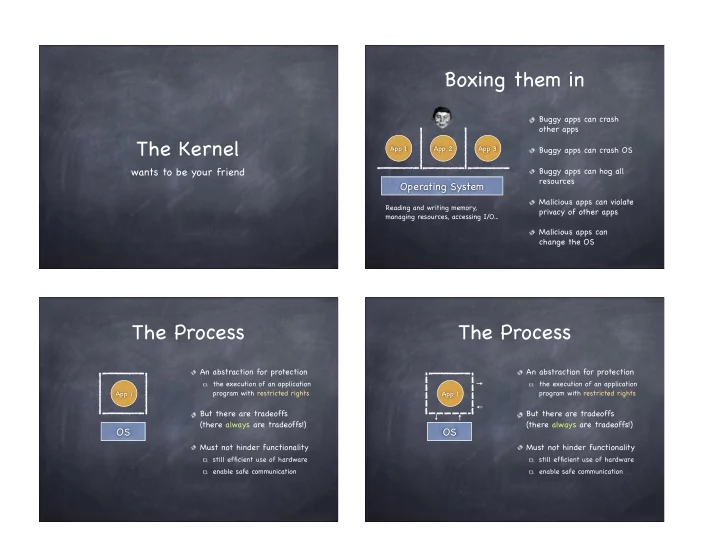

Boxing them in Buggy apps can crash other apps The Kernel App 1 App 2 App 3 Buggy apps can crash OS wants to be your friend Buggy apps can hog all resources Operating System Malicious apps can violate Reading and writing memory, privacy of other apps managing resources, accessing I/O... Malicious apps can change the OS The Process The Process An abstraction for protection An abstraction for protection the execution of an application the execution of an application program with restricted rights program with restricted rights App 1 App 1 But there are tradeoffs But there are tradeoffs (there always are tradeoffs!) (there always are tradeoffs!) OS OS Must not hinder functionality Must not hinder functionality still efficient use of hardware still efficient use of hardware enable safe communication enable safe communication
I know what you are thinking… Actually… Special Part of the OS all kernel is in the OS not all the OS is in the kernel (why not? robustness) widgets libraries, window managers etc Process: Keeping track of a process Getting to know you Process Control A process is a program during execution A process has code Block program is a static file OS must track program counter PC Stack Pointer process = executing program = program + execution state Registers A process has a stack PID UID Header OS must track stack pointer Priority Code List of open files compiler Process status Initialized data OS stores state of process … in Process Control Block (PCB) OS copy Source code Data (program instructions, stack & heap) Executable Image resides in memory, metadata is in PCB Physical memory Code Data Heap Stack Code Data Heap Stack
How can the OS How can the OS enforce restricted rights? enforce restricted rights? Easy: kernel interprets each instruction! Easy: kernel interprets each instruction! slow slow many instructions are safe: do we really need to involve many instructions are safe: do we really need to involve the OS? the OS? Dual Mode Operation hardware to the rescue: use a mode bit in user mode, processor checks every instruction in kernel mode, unrestricted rights hardware to the rescue (again) to make checks efficient Efficient protection in I. Privileged instructions dual mode operation Privileged instructions Examples: Set mode bit; set accessible memory; disable interrupts; etc in user mode, no way to execute potentially unsafe instructions But how can an app do I/O then? Memory protection system calls achieve access to kernel mode only at in user mode, memory accesses outside a process’ specific locations specified by OS memory region are prohibited Executing a privileged instruction while in user Timer interrupts mode causes a processor exception.... kernel must be able to periodically regain control from ...which passes control to the kernel running process + Efficient mechanism for switching modes
II. Memory Protection II. Memory Protection Step 2: Address Translation Step 1: Virtualize Memory Implement a function mapping into ⟨ pid, virtual address ⟩ physical address Virtual address space: set of memory mapped segments Virtual Physical addresses that process can “touch” DLL ’ s p i CPU works with virtual addresses Stack Physical address space: set of memory Advantages: addresses supported by hardware a486d9 Heap protection Virtual Initialized data relocation address 5e3a07 data sharing space Code multiplexing Protection Relocation At all times, the functions used by different The range of the function used by a process processes map to disjoint ranges can change over time p i p i p j
Relocation Data Sharing The range of the function used by a process Map different virtual addresses of different can change over time processes to the same physical address p i p i 04d26a 5e3a07 p j 119af3 Multiplexing Multiplexing Create illusion of almost infinite memory by The domain (set of virtual addresses) that map changing domain (set of virtual addresses) that to a given range of physical addresses can maps to a given range of physical addresses change over time p i p i
Multiplexing Multiplexing The domain (set of virtual addresses) that map The domain (set of virtual addresses) that map to a given range of physical addresses can to a given range of physical addresses can change over time change over time p i p i A simple mapping mechanism: Multiplexing Base & Bound MAX sys The domain (set of virtual addresses) that map to a given range of physical addresses can Memory Exception change over time Logical Physical no 1500 p’ s physical p i addresses addresses CPU ≤ + address yes space 1000 1000 500 Bound Base Register Register 0
On Base & Limit III. Timer Interrupts Contiguous Allocation: contiguous virtual Hardware timer addresses are mapped to contiguous physical can be set to expire after specified delay addresses (time or instructions) Protection is easy, but sharing is hard when it does, control is passed back to the kernel Two copies of emacs: want to share code, but have data and stack distinct... Other interrupts (e.g. I/O completion) also And there is more… give control to kernel Hard to relocate We want them as far as as possible in virtual address space, but... From user mode Crossing the line to kernel mode... user process mode bit = 1 Exceptions user process executing calls system call return from system call user program acts silly (e.g. division by zero) attempt to perform a privileged instruction sometime on purpose! (breakpoints) trap mode bit := 1 synchronous System calls/traps mode bit := 0 return user program requests OS service Interrupts kernel mode bit = 0 synchronous HW device requires OS service execute system call timer, I/O device, interprocessor asynchronous
Making the transition: ...and viceversa Safe mode switch Resume after exception, Common sequences of instructions to cross p interrupt or syscall boundary, which provide: restore PC, SP, registers; Limited entry Switch to different process q toggle mode entry point in the kernel set up by kernel load PC, SP, registers from ’ s q PCB Atomic changes to process state If new process toggles mode PC, SP, memory protection, mode copy program in memory, Transparent restartable execution set PC and SP user program must be restarted exactly as it User-level upcall toggle mode was before kernel got control a sort of user-level interrupt handling Interrupt vector Interrupt stack Processor Register Interrupt Vector Stores execution context of interrupted process 0 Hardware identifies why handleDivideByZero() { HW saves SP, PC boundary is crossed ... } trap? Handler saves remaining registers interrupt (which 31 device)? Stores handler’ s local variables 32 exception? Pointed by privileged register Hardware selects entry handleTrap() { from interrupt vector ... 128 One per process (or per thread!) } Appropriate handler is invoked handleTimerInterrupt() { Why not use the stack in user’ s space? ... } 255
Interrupt masking Mode switch on x86 User-level Registers Kernel Process Stack segment Offset What if an interrupt occurs while running an Code Code Code segment Offset SS:ESP interrupt handler? foo() { handler() { CS:EIP while(...) { pusha Disable interrupts via privileged instruction EFLAGS x = x+1; ... y = y-2 } Other Overdramatic… it actually defers them } Registers: } Just use the current SP of Interrupt stack EAX, EBX, ... Stack Interrupt Stack Mode switch on x86 Mode switch on x86 User-level User-level Registers Kernel Registers Kernel Process Process Code Code Code Code SS:ESP SS:ESP SS:ESP foo() { foo() { CS:EIP handler() { handler() { CS:EIP CS:EIP while(...) { while(...) { pusha pusha EFLAGS EFLAGS EFLAGS x = x+1; x = x+1; ... ... y = y-2 y = y-2 } } Other Other SS:ESP } } CS:EIP Registers: Registers: } } EFLAGS EAX, EBX, EAX, EBX, ... ... Stack Interrupt Stack Stack Interrupt Stack 1. Disable interrupts 1. Disable interrupts 2. Save key registers 2. Save key registers 3. Switch onto the kernel interrupt stack 3. Switch onto the kernel interrupt stack 4. Push key registers onto new stack
Recommend
More recommend