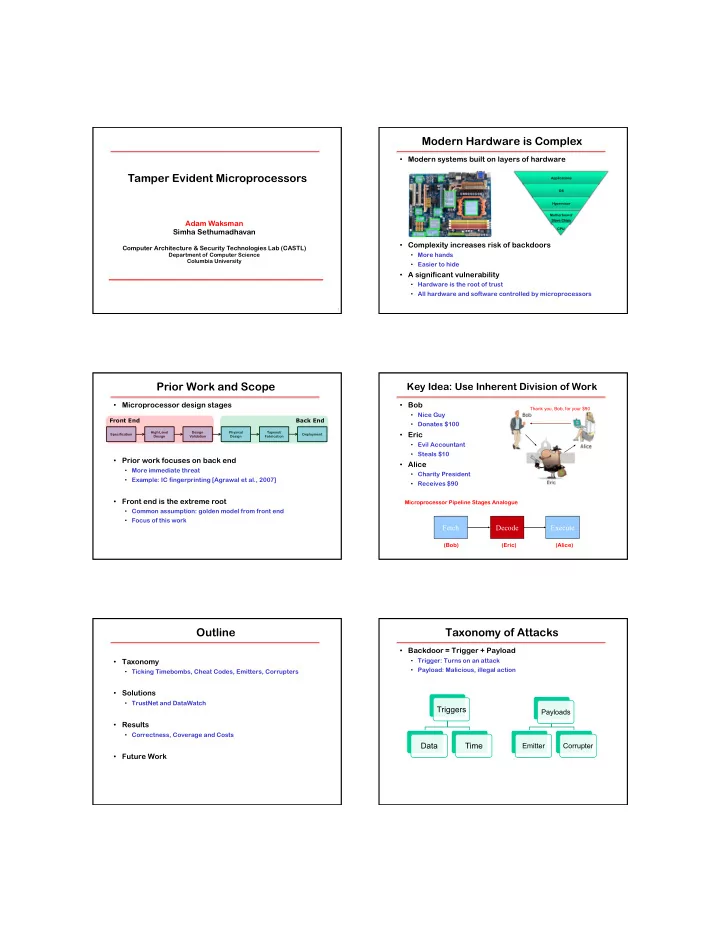

5/24/10 Modern Hardware is Complex • Modern systems built on layers of hardware Tamper Evident Microprocessors Applications OS Hypervisor Motherboard/ Slave Chips Adam Waksman CPU Simha Sethumadhavan • Complexity increases risk of backdoors Computer Architecture & Security Technologies Lab (CASTL) Department of Computer Science • More hands Columbia University • Easier to hide • A significant vulnerability • Hardware is the root of trust • All hardware and software controlled by microprocessors 1 Prior Work and Scope Key Idea: Use Inherent Division of Work • Microprocessor design stages • Bob Thank you, Bob, for your $90 • Nice Guy Front End Back End • Donates $100 High Level Design Physical Tapeout/ • Eric Specification Deployment Design Validation Design Fabrication • Evil Accountant • Steals $10 • Prior work focuses on back end • Alice • More immediate threat • Charity President • Example: IC fingerprinting [Agrawal et al., 2007] • Receives $90 • Front end is the extreme root Microprocessor Pipeline Stages Analogue • Common assumption: golden model from front end • Focus of this work Fetch Decode Execute (Bob) (Eric) (Alice) Outline Taxonomy of Attacks • Backdoor = Trigger + Payload • Taxonomy • Trigger: Turns on an attack • Payload: Malicious, illegal action • Ticking Timebombs, Cheat Codes, Emitters, Corrupters • Solutions • TrustNet and DataWatch Triggers Payloads • Results • Correctness, Coverage and Costs Data Time Emitter Corrupter • Future Work 1
5/24/10 Taxonomy of Attacks: Triggers Taxonomy of Attacks: Payloads Triggers Payloads Data Time Emitter Corrupter • Emitter Attacks • Corrupter Attacks • Extra malicious events • No extra malicious events • Separate from normal events • Normal instructions altered Taxonomy of Attacks: Summary Assumptions • Large design team • Each designer works on one unit or part of one Emitter Corrupter • Security add-ons cannot be done by one member Timebomb Timebomb • Full knowledge • Attacker has complete access to all design specifications • Attacker also knows about additional security mechanism Emitter Corrupter • Equal distrust Cheatcode Cheatcode • Any one designer/unit may be evil • Security add-ons may contain backdoors Outline Sample Emitter Backdoor • Taxonomy • Consider a malicious instruction decoder • Ticking Timebombs, Cheat Codes, Emitters, Corrupters • Decoder emits instructions not in the original program • Execution unit faithfully executes them • Solutions Spurious Output • TrustNet and DataWatch • Results Fetch Fetch Fetch Decode Execute • Correctness, Coverage and Costs • Future Work 2
5/24/10 TrustNet Corrupter Backdoors • Bob • Still nice Thank you, Bob, for your C$100 Predictor Fetch Reactor Execute • Donates $100 • Eric add $r1, $r2, $r3 • Evil (and smarter) Decode Target • Converts to Canadian $ • Alice • Predictor and Reactor monitor the Target • Still president • Division of work prevents one bad guy from breaking two units • Fooled by Eric’s C$100 • Scaling to larger number increases design complexity DataWatch Outline • Taxonomy STOP • Ticking Timebombs, Cheat Codes, Emitters, Corrupters Predictor Fetch Execute Reactor • Solutions • TrustNet and DataWatch add $r1, $r2, $r3 Decode Target • Results SUB $r1, $r2, $r3 • Correctness, Coverage and Costs • Scaled up version of TrustNet • Future Work • Multiple bit messages • Confirms types of messages (instead of just yes/no) Coverage: Vulnerability Space Experimental Context, Correctness, Costs • Context • Simplified OpenSPARC T2 • Correctness • Designed attacks • No false positives or negatives • Costs • Low area overhead (2 KB per core) • No performance impact • How to measure coverage? Units with a core Units with a core Paper has plots for other units at a chip level 18 3
5/24/10 Summary and Future Work Coverage Visualization • Strengthen root of trust: microprocessors • Hardware-only solution. No perf impact, low area overhead • Security add-on highly resilient to corruption • Provided attack taxonomy, method to characterize attack space • Applicability of TrustNet & DataWatch • Covered: pipelines, caches and content associative memory • Not covered: ALU, microcode, power mgmt., side-channels • Moving Forward • Expand coverage • Out-of-order processors ✔ • Motherboard components • Design automation tools • Reaction to errors WARNING: • Applying techniques for reliable execution This is an approximate • First steps toward a secure trusted hardware w/ untrusted units vizualization Thank You! and Questions? 19 19 4
Recommend
More recommend