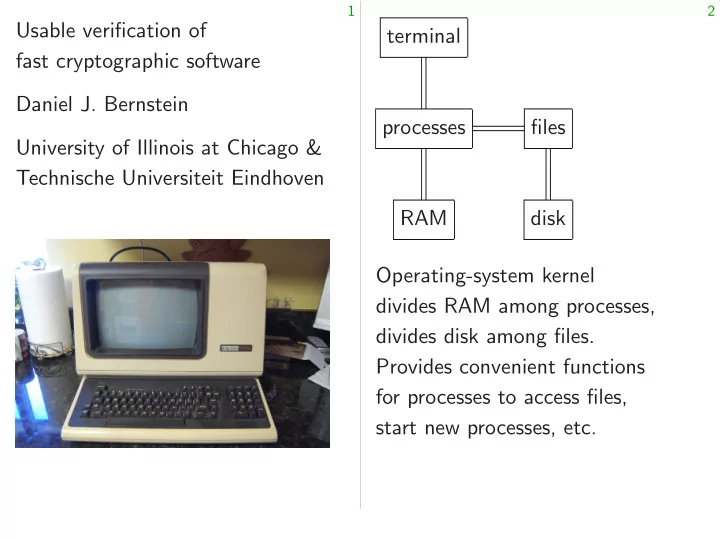

1 2 Usable verification of terminal fast cryptographic software Daniel J. Bernstein processes files University of Illinois at Chicago & Technische Universiteit Eindhoven RAM disk Operating-system kernel divides RAM among processes, divides disk among files. Provides convenient functions for processes to access files, start new processes, etc.
1 2 verification of terminal my terminal cryptographic software J. Bernstein processes files my p University of Illinois at Chicago & echnische Universiteit Eindhoven RAM disk RAM Operating-system kernel divides RAM among processes, Donald’s divides disk among files. Provides convenient functions for processes to access files, Donald’s start new processes, etc.
1 2 verification of terminal my terminal cryptographic software Bernstein processes files my processes Illinois at Chicago & Universiteit Eindhoven RAM disk RAM Operating-system kernel divides RAM among processes, Donald’s processes divides disk among files. Provides convenient functions for processes to access files, Donald’s terminal start new processes, etc.
1 2 terminal my terminal re processes files my processes my Chicago & Eindhoven RAM disk RAM Operating-system kernel divides RAM among processes, Donald’s Donald’s processes divides disk among files. Provides convenient functions for processes to access files, Donald’s terminal start new processes, etc.
2 3 terminal my terminal processes files my processes my files RAM disk RAM disk Operating-system kernel divides RAM among processes, Donald’s Donald’s processes files divides disk among files. Provides convenient functions for processes to access files, Donald’s terminal start new processes, etc.
2 3 Can Donald terminal my terminal appearing cesses files my processes my files RAM disk RAM disk erating-system kernel RAM among processes, Donald’s Donald’s processes files disk among files. Provides convenient functions cesses to access files, Donald’s terminal new processes, etc.
2 3 Can Donald corrupt my terminal appearing on my terminal? files my processes my files disk RAM disk kernel among processes, Donald’s Donald’s processes files among files. convenient functions access files, Donald’s terminal cesses, etc.
2 3 Can Donald corrupt the data my terminal appearing on my terminal? my processes my files RAM disk cesses, Donald’s Donald’s processes files functions files, Donald’s terminal
3 4 Can Donald corrupt the data my terminal appearing on my terminal? my processes my files RAM disk Donald’s Donald’s processes files Donald’s terminal
3 4 Can Donald corrupt the data my terminal appearing on my terminal? Attack: guess my password. my processes my files RAM disk Donald’s Donald’s processes files Donald’s terminal
3 4 Can Donald corrupt the data my terminal appearing on my terminal? Attack: guess my password. my processes my files Defense: I have a high-entropy randomly generated password. RAM disk Donald’s Donald’s processes files Donald’s terminal
3 4 Can Donald corrupt the data my terminal appearing on my terminal? Attack: guess my password. my processes my files Defense: I have a high-entropy randomly generated password. Attack: replace the terminal RAM disk with a rigged terminal that intercepts my password. Donald’s Donald’s processes files Donald’s terminal
3 4 Can Donald corrupt the data my terminal appearing on my terminal? Attack: guess my password. my processes my files Defense: I have a high-entropy randomly generated password. Attack: replace the terminal RAM disk with a rigged terminal that intercepts my password. Defense: physical security. Donald’s Donald’s processes files Donald’s terminal
3 4 Can Donald corrupt the data my terminal appearing on my terminal? Attack: guess my password. my processes my files Defense: I have a high-entropy randomly generated password. Attack: replace the terminal RAM disk with a rigged terminal that intercepts my password. Defense: physical security. Donald’s Donald’s processes files Attack: use my terminal earlier and leave a program running that looks like the usual login screen Donald’s terminal but intercepts my password.
3 4 Can Donald corrupt the data my terminal appearing on my terminal? Attack: guess my password. my processes my files Defense: I have a high-entropy randomly generated password. Attack: replace the terminal RAM disk with a rigged terminal that intercepts my password. Defense: physical security. Donald’s Donald’s processes files Attack: use my terminal earlier and leave a program running that looks like the usual login screen Donald’s terminal but intercepts my password. Defense: secure attention key.
3 4 Can Donald corrupt the data Donald is my terminal appearing on my terminal? data on Attack: guess my password. Attack: processes my files Defense: I have a high-entropy part of RAM, randomly generated password. Attack: replace the terminal RAM disk with a rigged terminal that intercepts my password. Defense: physical security. Donald’s Donald’s processes files Attack: use my terminal earlier and leave a program running that looks like the usual login screen Donald’s terminal but intercepts my password. Defense: secure attention key.
3 4 Can Donald corrupt the data Donald is authorized appearing on my terminal? data on the same computer. Attack: guess my password. Attack: Donald sto my files Defense: I have a high-entropy part of RAM, or my randomly generated password. Attack: replace the terminal disk with a rigged terminal that intercepts my password. Defense: physical security. Donald’s cesses files Attack: use my terminal earlier and leave a program running that looks like the usual login screen terminal but intercepts my password. Defense: secure attention key.
3 4 Can Donald corrupt the data Donald is authorized to store appearing on my terminal? data on the same computer. Attack: guess my password. Attack: Donald stores data in my files Defense: I have a high-entropy part of RAM, or my part of randomly generated password. Attack: replace the terminal disk with a rigged terminal that intercepts my password. Defense: physical security. Donald’s files Attack: use my terminal earlier and leave a program running that looks like the usual login screen but intercepts my password. Defense: secure attention key.
4 5 Can Donald corrupt the data Donald is authorized to store appearing on my terminal? data on the same computer. Attack: guess my password. Attack: Donald stores data in my Defense: I have a high-entropy part of RAM, or my part of disk. randomly generated password. Attack: replace the terminal with a rigged terminal that intercepts my password. Defense: physical security. Attack: use my terminal earlier and leave a program running that looks like the usual login screen but intercepts my password. Defense: secure attention key.
4 5 Can Donald corrupt the data Donald is authorized to store appearing on my terminal? data on the same computer. Attack: guess my password. Attack: Donald stores data in my Defense: I have a high-entropy part of RAM, or my part of disk. randomly generated password. Two-part defense: Attack: replace the terminal 1. “Memory protection”. with a rigged terminal that Hardware does not allow intercepts my password. processes to access data Defense: physical security. outside areas marked by kernel. Attack: use my terminal earlier 2. Kernel keeps track of which and leave a program running that parts of RAM and disk are mine, looks like the usual login screen and which parts are Donald’s. but intercepts my password. Defense: secure attention key.
4 5 Donald corrupt the data Donald is authorized to store Bugs in ring on my terminal? data on the same computer. can comp allowing ttack: guess my password. Attack: Donald stores data in my to my pa Defense: I have a high-entropy part of RAM, or my part of disk. randomly generated password. Two-part defense: ttack: replace the terminal 1. “Memory protection”. rigged terminal that Hardware does not allow intercepts my password. processes to access data Defense: physical security. outside areas marked by kernel. ttack: use my terminal earlier 2. Kernel keeps track of which leave a program running that parts of RAM and disk are mine, like the usual login screen and which parts are Donald’s. intercepts my password. Defense: secure attention key.
4 5 rrupt the data Donald is authorized to store Bugs in this kernel terminal? data on the same computer. can compromise securit allowing Donald to my password. Attack: Donald stores data in my to my part of RAM a high-entropy part of RAM, or my part of disk. generated password. Two-part defense: the terminal 1. “Memory protection”. terminal that Hardware does not allow password. processes to access data physical security. outside areas marked by kernel. terminal earlier 2. Kernel keeps track of which rogram running that parts of RAM and disk are mine, usual login screen and which parts are Donald’s. my password. attention key.
Recommend
More recommend