TLS/SSL TLS/SSL aims to provide a secure channel Username and - PowerPoint PPT Presentation
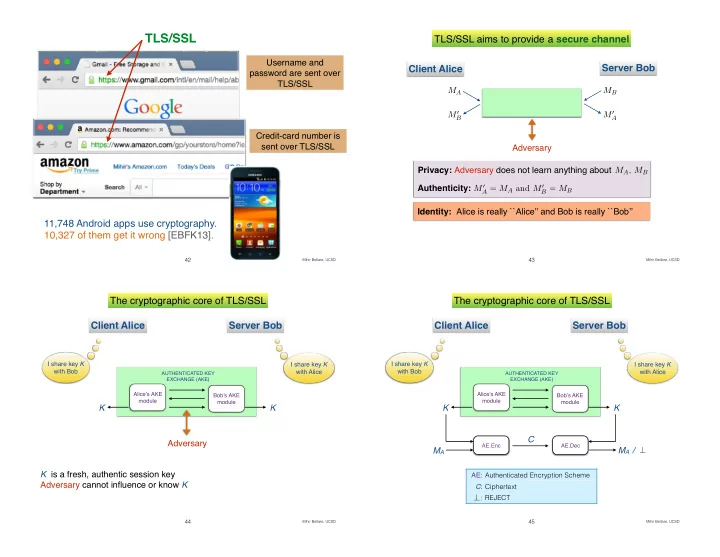
TLS/SSL TLS/SSL aims to provide a secure channel Username and Server Bob Client Alice password are sent over TLS/SSL M A M B M 0 M 0 A B Credit-card number is sent over TLS/SSL Adversary Privacy: Adversary does not learn anything about M A
TLS/SSL TLS/SSL aims to provide a secure channel Username and Server Bob Client Alice password are sent over TLS/SSL M A M B M 0 M 0 A B Credit-card number is sent over TLS/SSL Adversary Privacy: Adversary does not learn anything about M A , M B Authenticity: M 0 A = M A and M 0 B = M B Identity: Alice is really ``Alice’’ and Bob is really ``Bob’’ 11,748 Android apps use cryptography. 10,327 of them get it wrong [EBFK13]. 42 Mihir Bellare, UCSD 43 Mihir Bellare, UCSD The cryptographic core of TLS/SSL The cryptographic core of TLS/SSL Client Alice Server Bob Client Alice Server Bob I share key K I share key K I share key K I share key K with Bob with Bob with Alice with Alice AUTHENTICATED KEY AUTHENTICATED KEY EXCHANGE (AKE) EXCHANGE (AKE) Alice’s AKE Alice’s AKE Bob’s AKE Bob’s AKE module module module module K K K K C Adversary AE.Enc AE.Dec M A M A / ⊥ K is a fresh, authentic session key AE: Authenticated Encryption Scheme Adversary cannot influence or know K C : Ciphertext ⊥ : REJECT 44 Mihir Bellare, UCSD 45 Mihir Bellare, UCSD
The question of identity: Who are ``Alice’’ and ``Bob’’? Who is ``Bob’’? Client Alice Server Bob Client Alice Server Bob ? ? google.com I share key K I share key K I share key K with Bob with Bob with Alice AUTHENTICATED KEY EXCHANGE (AKE) amazon.com Alice’s AKE Bob’s AKE module module K K snapchat.com Think of Bob = example.com as a url or an ip address twitter.com On the Internet, nobody knows you are a dog. 46 Mihir Bellare, UCSD 47 Mihir Bellare, UCSD Certificate Authority (CA) Certificate authorities CERT Bob Client Alice PK CA Server Bob CERT Bob I share key I share key K K with someone with someone CA calling herself Alice thinks is Bob AUTHENTICATED KEY EXCHANGE (AKE) SK Bob Alice’s AKE Bob’s AKE module module K K As of February 2015 CERT Bob : Bob’s certificate, issued by CA PK CA : CA’s public key SK Bob : Bob’s secret key, tied to CERT Bob 48 Mihir Bellare, UCSD 49 Mihir Bellare, UCSD
Certificate Authority (CA) The cryptographic core of TLS/SSL CERT Bob Client Alice PK CA Client Alice PK CA Server Bob Server Bob CERT Bob CERT Bob I share key I share key K K with someone with someone CA calling herself Alice thinks is Bob AUTHENTICATED KEY AUTHENTICATED KEY EXCHANGE (AKE) EXCHANGE (AKE) SK Bob SK Bob Alice’s AKE Alice’s AKE Bob’s AKE Bob’s AKE module module module module K K K K C CERT Bob : Sent by Bob to Alice AE.Enc AE.Dec M A / M A ⊥ PK CA : Stored by Alice SK Bob : Stored by Bob 50 Mihir Bellare, UCSD 51 Mihir Bellare, UCSD But who is ``Alice?’’ TLS/SSL Vulnerabilities AliceWonder@wonderland AliceWaters@chezpanisse Default TLS/SSL provides unilateral AliceWalker@colorpurple authentication : Bob authenticates himself to Alice but not vice versa. Alice does not typically have a certificate. AlicePoker@saloon Alice will typically authenticate herself to Bob with username and password over the TLS/SSL channel itself. 52 Mihir Bellare, UCSD 53 Mihir Bellare, UCSD
Get it right! TLS/SSL Vulnerabilities Implementation/ Vulnerability crypto The cryptographic core of a secure channel Many different TLS/SSL Implementations: Usage OpenSSL, GnuTLS, cryptlib, JSSE, RSA FREAK x BSafe, SChannel, … Re-negotiation x Version Rollback x Issues: Cipher suites, re-negotiation, side- BEAST x channels, buffer overflows, bad Padding Oracle x randomness, … Lucky 13 x Poodle Lots of bad crypto in TLS/SSL, often for x x historic and legacy reasons. Heartbleed x RC4 x AllYourSSLsAreBelongToUs x 54 Mihir Bellare, UCSD 55 Mihir Bellare, UCSD Summary, take away Appreciate that there is a ton going on every time you TLS/SSL: access a website! Providing a well-designed and analyzed cryptographic core is a central problem for us to address. 56 Mihir Bellare, UCSD
Recommend
More recommend
Explore More Topics
Stay informed with curated content and fresh updates.