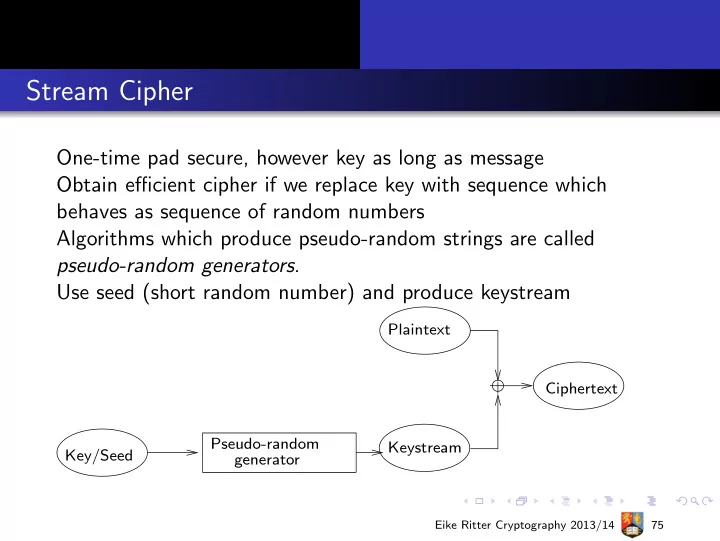

Stream Cipher One-time pad secure, however key as long as message Obtain efficient cipher if we replace key with sequence which behaves as sequence of random numbers Algorithms which produce pseudo-random strings are called pseudo-random generators . Use seed (short random number) and produce keystream Plaintext Ciphertext Pseudo-random Keystream Key/Seed generator Eike Ritter Cryptography 2013/14 75
Sources of randomness Thermal noise in various electric circuits Radioactive decay Atmospheric noise measurement of times between user key-strokes time needed to access different sectors on hard-disk drive (air turbulence caused by spinning disk supposed to be random) Eike Ritter Cryptography 2013/14 76
RC4 Stream cipher invented 1987 by Ron Rivest Consists of tow phases: Initalisation phase (key schedule) Keystream generation phase Main datastructure is array S of 256 bytes Eike Ritter Cryptography 2013/14 77
Initialisation for i := 0 to 255 do S[ i ] := i end j := 0 for i := 0 to 255 do j := ( j + S[ i ] + K[ i mod keylength]) mod 256 swap(S[ i ],S[ j ]) end Eike Ritter Cryptography 2013/14 78
Keystream generation i := 0 j := 0 while GeneratingOutput: i := ( i + 1) mod 256 j := ( j + S[ i ]) mod 256 swap(S[ i ],S[ j ]) output S[(S[ i ] + S[ j ]) mod 256] end Eike Ritter Cryptography 2013/14 79
Graphical representation Source: Wikipedia Eike Ritter Cryptography 2013/14 80
LFSR Linear Feedback Shift Register: Building block for many modern stream ciphers Can be implemented very efficiently Key idea: have register of single bit cells shifted by one at every clock cycle together with feedback function Source: Wikipedia Eike Ritter Cryptography 2013/14 81
Example: Source: Wikipedia Eike Ritter Cryptography 2013/14 82
Reasoning about LFSRs Interesting property: Length of keystream period Reasoning works as follows: Have state vector s = [ s 1 , . . . , s n ] for shift register with n cells Have connection polynomial c ( x ) = c n x n + . . . + c 1 x + 1, where c i is 1 if the i th cell in s is used for feedback and 0 if not. c 1 c 2 c n − 1 c n · · · 1 0 0 0 · · · 0 1 0 0 · · · a matrix M = . . . ... ... . . . . . . 0 0 1 0 · · · Next state vector given by M · s . Eike Ritter Cryptography 2013/14 83
Combining LFSRs LFSRs are insecure in practice (Connection polynomial can be computed fairly efficiently) Hence multiple LFSRs are combined in non-linear fashion Source: Wikipedia Eike Ritter Cryptography 2013/14 84
Keys for stream ciphers must not be reused. Formally, RC4 and LFSR as presented do not satisfy IND-CPA security. Need carefully used initialisation vectors or nonces to obtain IND-CPA. Eike Ritter Cryptography 2013/14 85
WEP Old standard for encryption on wireless networks based on RC4, but seriously broken - don’t use Source: Wikipedia Eike Ritter Cryptography 2013/14 86
Weaknesses in WEP Initialisation vector only 24 bits, hence keys repeat after at most 2 24 frames With certain initialisation vectors knowing m bytes of key and keystream means you can deduce byte m + 1 of key First bytes of key stream known because standard headers are always sent With this method, can crack the key in minutes on modern PC hardware Eike Ritter Cryptography 2013/14 87
CSS CSS used to encrypt DVD for copy protection Following steps are taken: Check whether region code and code on DVD match Use player keys to extract disk key from DVD Use disk key to extract title key for track Use title key to extract for each sector a sector key, which is used to decrypt the sector. Eike Ritter Cryptography 2013/14 88
Sector encryption is combination of two LFSR’s added modulo 256 seed 17 bit LFSR 1 || K 0 || K 1 8 bit keystream add modulo 256 1 || K 2 || K 3 || K 4 25 bit LFSR Eike Ritter Cryptography 2013/14 89
Security of CSS Can be broken in time 2 17 : Idea: Because of structure of MP4, first 20 bytes of plaintext are known Hence also first 20 bytes of keystream are known Given output of 17 bit LFSR, can deduce output of 25 bit LFSR by subtraction Hence try all 2 17 possibilities for 17 bit LFSR and if generated 25 bit LFSR produces observed keystream, cipher is cracked Eike Ritter Cryptography 2013/14 90
A5/1 Stream cipher used in GSM mobile phone communication Became public knowledge through leaks and reverse engineering Built from three LFSRs with irregular clock cycle 54 bit secret key and 22 bit initialisation vector Shift register only shifted if clock bit is the same as majority of three clock bits Eike Ritter Cryptography 2013/14 91
Source: Wikipedia Eike Ritter Cryptography 2013/14 92
Security of A5/1 Better design: Clock shift make cryptanalysis much harder However, advanced techniques means mainstream PC with terabytes of flash memory (to store pre-processed tables) can break A5/1 with probability ≥ 90% in a few seconds Eike Ritter Cryptography 2013/14 93
Recommend
More recommend