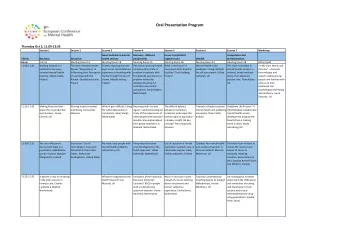
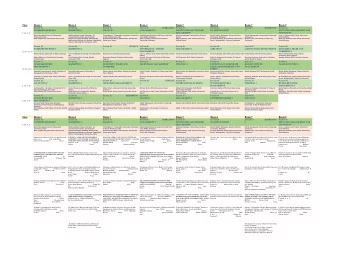
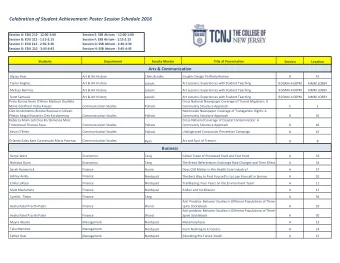
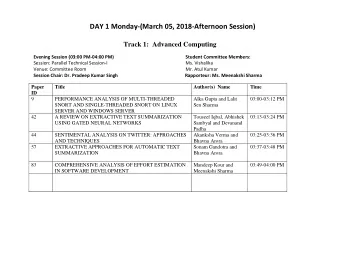
Session 2 Background Lecture Objectives Understand how an Internet - PDF document
Session 2 Background Session 2 Background Lecture Objectives Understand how an Internet resource is accessed Understand the high level structure of the Internet cloud Understand the high level structure of the TCP/IP
Session 2 – Background Session 2 Background Lecture Objectives � Understand how an Internet resource is accessed � Understand the high level structure of the “Internet cloud” � Understand the high level structure of the TCP/IP protocols � Understand how a computer finds the IP address of a host using DNS � Know the structure of MIME type standards 2 � Robert Kelly, 2001-2018 1 9/5/2018 � Robert Kelly, 2001-2018
Session 2 – Background Reference � Mime types http://en.wikipedia.org/wiki/Internet_media_type 3 � Robert Kelly, 2001-2018 What is a URL? � A short string that identifies a resource on the Web � Stands for Uniform Resource Locator � Uniform – varied and new types of resources � Resource – Anything that has identity (e.g., image) � Reduces the tedium of connecting to a host, selecting a path, selecting a resource, etc. into a single string that: � Can be saved as a bookmark in your browser � Can be saved as an object in your Java code 4 � Robert Kelly, 2001-2018 2 9/5/2018 � Robert Kelly, 2001-2018
Session 2 – Background URL Example http://www.cs.sunysb.edu Protocol identifier Resource name � Protocol Identifier - Indicates the name of the protocol to be used to fetch the resource � Resource name is the complete address of the resource � Resource name may be appended with a fragment / reference / named anchor (denoted by #) or include a query string (denoted by ?) 5 � Robert Kelly, 2001-2018 URL Resource Name � For http, the name includes: host name, path name to the file, port number (optional), and location within the resource (optional) � The resource is not necessarily a file, it can be generated dynamically important concept � A trailing slash (www.sun.com/) is shorthand for the file named /index.html 6 � Robert Kelly, 2001-2018 3 9/5/2018 � Robert Kelly, 2001-2018
Session 2 – Background Relative URLs � Contains only enough information to reach the resource relative to (in the context of) another URL � Used within HTML files <td> <a href=“LectureCode.html“ >Intro</a></td> � specified relative to the location of the file in which they are contained 7 � Robert Kelly, 2001-2018 Web Architecture Reason for the term “cloud computing” ISP ISP HTML Web browsers Web servers ISP ISP GIF graphic 8 � Robert Kelly, 2001-2018 4 9/5/2018 � Robert Kelly, 2001-2018
Session 2 – Background 9 Internet Origins � Late 1960s � ARPA (Advanced Research Projects Agency) � Funded research project � ARPANet – redundant network, connecting research labs and US Government installations DARPA has changed its name � 1970s – 1980s (back and forth) to ARPA � Enormous growth in US sponsored Internet � 1990s � US Government turns Internet over to independent global agencies � Robert Kelly, 2001-2018 10 ARPANet Principles � Free and open information sharing � Datagram message packets - data carried in chunks (not streams) � Uniform protocol for communications between dissimilar computers � Robert Kelly, 2001-2018 5 9/5/2018 � Robert Kelly, 2001-2018
Session 2 – Background Internet Physical Layer � Multiple backbones � Multiple ISPs � Multiple exchange points 11 � Robert Kelly, 2001-2018 Internet Interconnect Points 12 � Robert Kelly, 2001-2018 6 9/5/2018 � Robert Kelly, 2001-2018
Session 2 – Background 13 Terms � Protocols – control the sending and receiving of information over the Internet � Physical media – cable, copper wire, fiber, radio spectrum � Routers – intermediate switching devices � Route (or path) – sequence of physical media and routers to complete end-to-end communication � Packet switching – decomposing a message into packets and routing the packets to a destination � Robert Kelly, 2001-2018 Protocol Stacks � Makes interfaces portable and maintainable � Each layer of the stack only interfaces with the adjacent layers � Protocol conversion occurs between the same layer on different computers � Examples � ISO/OSI 14 � Robert Kelly, 2001-2018 7 9/5/2018 � Robert Kelly, 2001-2018
Session 2 – Background Internet Protocol Stacks Application Application (http, ftp, telnet, (http, ftp, telnet, Transport Transport When you design a (TCP, UDP, … (TCP, UDP, … system, you think Network that there is a Network (IP, … (IP, … connection here Link Link (device driver, … (device driver, … 15 � Robert Kelly, 2001-2018 16 Data Encapsulation � Layer to layer interface usually involves encapsulation of data � Encapsulation – wrapping the data with information that describes the data and helps route the data � Robert Kelly, 2001-2018 8 9/5/2018 � Robert Kelly, 2001-2018
Session 2 – Background Global Traffic 17 � Robert Kelly, 2001-2018 18 Transoceanic Cables Fiber Fiber Protective layers Protective layers � Robert Kelly, 2001-2018 9 9/5/2018 � Robert Kelly, 2001-2018
Session 2 – Background Asia Backbone 19 � Robert Kelly, 2001-2018 Transport Protocols � Internet connection-oriented service is implemented through buffers at the sending and receiving end � TCP � UDP � Transmission Control Protocol � User Datagram Protocol � Connection based � Connectionless service � Reliable flow of data between two � Order of delivery is not guaranteed computers 20 � Robert Kelly, 2001-2018 10 9/5/2018 � Robert Kelly, 2001-2018
Session 2 – Background TCP/IP � IP (Internet Protocol) - network layer protocol that specifies the format of information that is sent and received among routers and end nodes 21 � Robert Kelly, 2001-2018 22 TCP/IP Network Architecture � Datagrams can take any route available to them without human intervention � Robert Kelly, 2001-2018 11 9/5/2018 � Robert Kelly, 2001-2018
Session 2 – Background 23 IPv4 � Current version of IP � Not adequate to serve millions of network components scattered across the globe. � Limitations � 32-bit addresses � a packet length limited to 65,635 bytes � all security measures are optional � Network addresses have been assigned with little planning resulting in slow and cumbersome routing hardware and software � Robert Kelly, 2001-2018 IP Addressing � Hosts and other devices have network interfaces identified by an IP address � IP (IPv4) addresses are 32-bit numbers represented as four groups of 8 bits (byte) � Written in dotted-decimal notation � IP address consists of � Network ID - portion of the IP address that defines the network to which the device is connected � Host ID – portion of the IP address that defines 2 32 possible IP the host addresses (not enough) 24 � Robert Kelly, 2001-2018 12 9/5/2018 � Robert Kelly, 2001-2018
Session 2 – Background 25 IP Packet Can be used to distinguish Can be used to distinguish differing levels of service differing levels of service IPv4 or IPv6 IPv4 or IPv6 � Header � Data section (payload) Usually TCP or UDP Usually TCP or UDP � Robert Kelly, 2001-2018 26 Application Interface � Interface is designated by a port number � Socket - combination of the port number, the host ID, and the protocol designation (equivalent to a file name to the application running above TCP) � Robert Kelly, 2001-2018 13 9/5/2018 � Robert Kelly, 2001-2018
Session 2 – Background Port Numbers � Port numbers 0 through 1023 are reserved for particular TCP applications � Examples � telnet – 23 � smtp – 25 � http - 80 27 � Robert Kelly, 2001-2018 TCP Segment Format 28 � Robert Kelly, 2001-2018 14 9/5/2018 � Robert Kelly, 2001-2018
Session 2 – Background IPv6 � In 1994, the Internet Engineering Task Force began work on what is now IP Version 6 � Motivation � Extend IP's address space beyond its current 32-bit limit to 128 bits for both the source and destination host addresses � Slow roll-out 29 � Robert Kelly, 2001-2018 How Does a Browser Work? � It reads a named resource (usually an HTML document) on an Internet-based server � Begins to display the page � Finds all the URLs in the HTML � Requests the resources associated with the other URLs (e.g., images) � Includes the additional resources in the display of the page 30 � Robert Kelly, 2001-2018 15 9/5/2018 � Robert Kelly, 2001-2018
Session 2 – Background How Does the Internet Find a Host? � URL contains a host name, (e.g., www.cnn.com) � Internet routers identify hosts by their IP address � 4 bytes, presented in dotted-decimal notation � decimal numbers, separated by periods (e.g., 121.7.106.83) � Each number is between 0 and 255 (8-bit binary number) � 2 32 possible IP addresses in IP V4 (theoretical maximum) � DNS (Domain Name System) is a directory service that translates host names (sometimes referred to as domain names) into IP addresses 31 � Robert Kelly, 2001-2018 How DNS Works root name server … DNS client browser local name server � Browser passes host name to DNS client. Authoritative name server � DNS client looks up IP address from the distributed database located on the DNS name servers � Local There are 13 root server identities � Root (A, B, C, …, M), but many of them are aliased � Authoritative 32 � Robert Kelly, 2001-2018 16 9/5/2018 � Robert Kelly, 2001-2018
Recommend
More recommend
Explore More Topics
Stay informed with curated content and fresh updates.