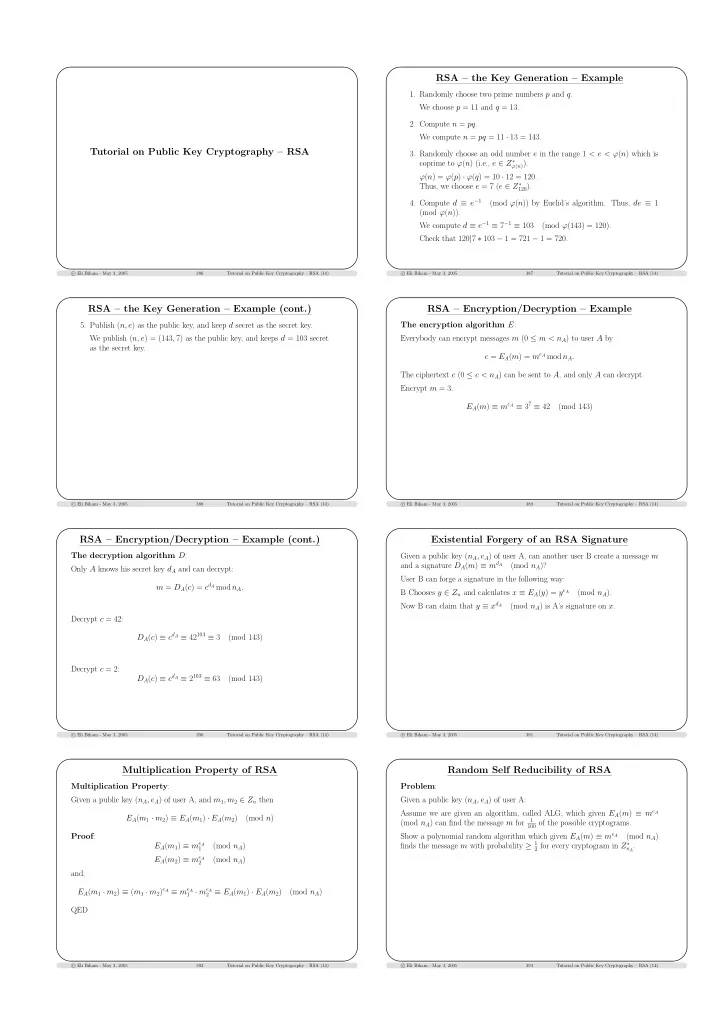

RSA – the Key Generation – Example 1. Randomly choose two prime numbers p and q . We choose p = 11 and q = 13. 2. Compute n = pq . We compute n = pq = 11 · 13 = 143. Tutorial on Public Key Cryptography – RSA 3. Randomly choose an odd number e in the range 1 < e < ϕ ( n ) which is coprime to ϕ ( n ) (i.e., e ∈ Z ∗ ϕ ( n ) ). ϕ ( n ) = ϕ ( p ) · ϕ ( q ) = 10 · 12 = 120. Thus, we choose e = 7 ( e ∈ Z ∗ 120 ). 4. Compute d ≡ e − 1 (mod ϕ ( n )) by Euclid’s algorithm. Thus, de ≡ 1 (mod ϕ ( n )). We compute d ≡ e − 1 ≡ 7 − 1 ≡ 103 (mod ϕ (143) = 120). Check that 120 | 7 ∗ 103 − 1 = 721 − 1 = 720. � Eli Biham - May 3, 2005 c 386 Tutorial on Public Key Cryptography – RSA (14) � Eli Biham - May 3, 2005 c 387 Tutorial on Public Key Cryptography – RSA (14) RSA – the Key Generation – Example (cont.) RSA – Encryption/Decryption – Example 5. Publish ( n, e ) as the public key, and keep d secret as the secret key. The encryption algorithm E : We publish ( n, e ) = (143 , 7) as the public key, and keeps d = 103 secret Everybody can encrypt messages m (0 ≤ m < n A ) to user A by as the secret key. c = E A ( m ) = m e A mod n A . The ciphertext c (0 ≤ c < n A ) can be sent to A , and only A can decrypt. Encrypt m = 3: E A ( m ) ≡ m e A ≡ 3 7 ≡ 42 (mod 143) � Eli Biham - May 3, 2005 c 388 Tutorial on Public Key Cryptography – RSA (14) � Eli Biham - May 3, 2005 c 389 Tutorial on Public Key Cryptography – RSA (14) RSA – Encryption/Decryption – Example (cont.) Existential Forgery of an RSA Signature The decryption algorithm D : Given a public key ( n A , e A ) of user A, can another user B create a message m and a signature D A ( m ) ≡ m d A (mod n A )? Only A knows his secret key d A and can decrypt: User B can forge a signature in the following way: m = D A ( c ) = c d A mod n A . B Chooses y ∈ Z n and calculates x ≡ E A ( y ) = y e A (mod n A ). Now B can claim that y ≡ x d A (mod n A ) is A’s signature on x . Decrypt c = 42: D A ( c ) ≡ c d A ≡ 42 103 ≡ 3 (mod 143) Decrypt c = 2: D A ( c ) ≡ c d A ≡ 2 103 ≡ 63 (mod 143) � Eli Biham - May 3, 2005 c 390 Tutorial on Public Key Cryptography – RSA (14) � Eli Biham - May 3, 2005 c 391 Tutorial on Public Key Cryptography – RSA (14) Multiplication Property of RSA Random Self Reducibility of RSA Multiplication Property : Problem : Given a public key ( n A , e A ) of user A, and m 1 , m 2 ∈ Z n then Given a public key ( n A , e A ) of user A: Assume we are given an algorithm, called ALG, which given E A ( m ) ≡ m e A E A ( m 1 · m 2 ) ≡ E A ( m 1 ) · E A ( m 2 ) (mod n ) 1 (mod n A ) can find the message m for 100 of the possible cryptograms. Proof : Show a polynomial random algorithm which given E A ( m ) ≡ m e A (mod n A ) E A ( m 1 ) ≡ m e A finds the message m with probability ≥ 1 (mod n A ) 2 for every cryptogram in Z ∗ n A . 1 E A ( m 2 ) ≡ m e A (mod n A ) 2 and, E A ( m 1 · m 2 ) ≡ ( m 1 · m 2 ) e A ≡ m e A 1 · m e A 2 ≡ E A ( m 1 ) · E A ( m 2 ) (mod n A ) QED c c � Eli Biham - May 3, 2005 392 Tutorial on Public Key Cryptography – RSA (14) � Eli Biham - May 3, 2005 393 Tutorial on Public Key Cryptography – RSA (14)
Random Self Reducibility of RSA (cont.) Random Self Reducibility of RSA (cont.) The Algorithm : Correctness : Make t iterations of the following: If algorithm ALG succeeds, i.e., outputs x such that x e A ≡ ( mz ) e A ≡ m e A · z e A (mod n A ) 1. Randomly Choose z ∈ Z ∗ n A . Then, m ≡ x · z − 1 2. Calculate z e A (mod n A ). (mod n a ). 3. Let x = ALG( m e A z e A (mod n A )). For z ∈ Z ∗ n { z · x : x ∈ Z n } = z · Z n = Z n 4. If x e A ≡ m e A z e A (mod n A ) then output x · z − 1 (mod n A ) and finish. because if for x 1 , x 2 we have: z · x 1 ≡ z · x 2 (mod n ) which implies x 1 ≡ z − 1 · z · x 1 ≡ z − 1 · z · x 2 ≡ x 2 (mod n ) � Eli Biham - May 3, 2005 c 394 Tutorial on Public Key Cryptography – RSA (14) � Eli Biham - May 3, 2005 c 395 Tutorial on Public Key Cryptography – RSA (14) Random Self Reducibility of RSA (cont.) Random Self Reducibility of RSA (cont.) 1 Note : Thus, for every iteration we have 100 probability of success, thus in order to find m with probability ≥ 1 2 , t must satisfy: Let p be a prime and g be a generator of Z ∗ p . p there exists z such that g z ≡ a Thus, for a ∈ Z ∗ (mod p ). This z is called the t 99 ≤ 1 discrete logarithm or index of a , modulo p , to the base of g . We denote 100 2 this value as ind p,g ( a ) or DLOG p,g ( a ). 99 ≤ log 1 t log DLOG is also random self reducible given a generator g of Z ∗ 100 2 p . Thus, t ≥ 69 suffices. Note : Can we find the message when E A ( m ) �∈ Z ∗ n A ? When the cryptogram E A ( m ) �∈ Z ∗ n , we can find either p or q . Thus, we can find d and then m . � Eli Biham - May 3, 2005 c 396 Tutorial on Public Key Cryptography – RSA (14) � Eli Biham - May 3, 2005 c 397 Tutorial on Public Key Cryptography – RSA (14) Blind Signatures Blind Signatures using RSA Usually when we sign a document we check its contents. Can Bob, with a public key ( n, e ), sign a message m (actually signs H ( m )) without knowing its contents? But we might want people to sign documents without ever seeing them. Yes. For example, Bob is a notary. Alice wants him to sign a document, but does We choose a random α ∈ Z ∗ not want him to have any idea what he is signing. Bob doesn’t care what the n and then ask Bob to sign document says, he is just certifying that he notarized it at a certain time. E ( α ) · m ≡ α e · m (mod n ) 1. Alice takes the document and uses a “ blinding factor ”. we get: 2. Alice sends the blinded document to Bob. D ( E ( α ) · m ) ≡ ( E ( α ) · m ) d ≡ ( α e · m ) d ≡ α · m d (mod n ) 3. Bob signs the blinded document. thus we need only to calculate α − 1 (mod n ): 4. Alice computes the signature on the original document. m d ≡ α − 1 · D ( E ( α ) · m ) (mod n ) Note that the function f ( x ) ≡ x e (mod n ) is a permutation of Z n . Moreover, n then α e ∈ Z ∗ if α ∈ Z ∗ n . � Eli Biham - May 3, 2005 c 398 Tutorial on Public Key Cryptography – RSA (14) � Eli Biham - May 3, 2005 c 399 Tutorial on Public Key Cryptography – RSA (14) An Example of Using Blind Signatures An Example of Using Blind Signatures (cont.) Problem 1 : Problem 2 : Alice wants a virtual 100 dollar note. The bank can trace this check to Alice. Solution 1 : Solution 2 : Alice goes to the bank and asks for such a note. The bank gives Alice a signature Use a blind signature. on a virtual 100 dollar check. The bank signs a check m by using a blind signature: Denote the bank’s public key by ( n, e ) and its secret key by d . Alice wants to get m d . Thus, Alice chooses a random α ∈ Z ∗ n and then asks the bank to sign: E ( α ) · m ≡ α e · m (mod n ) now Alice needs only to calculate α − 1 (mod n ): m d ≡ α − 1 · D ( E ( α ) · m ) (mod n ) c † c � Eli Biham - May 3, 2005 400 Tutorial on Public Key Cryptography – RSA (14) � Eli Biham - May 3, 2005 401 Tutorial on Public Key Cryptography – RSA (14)
Recommend
More recommend