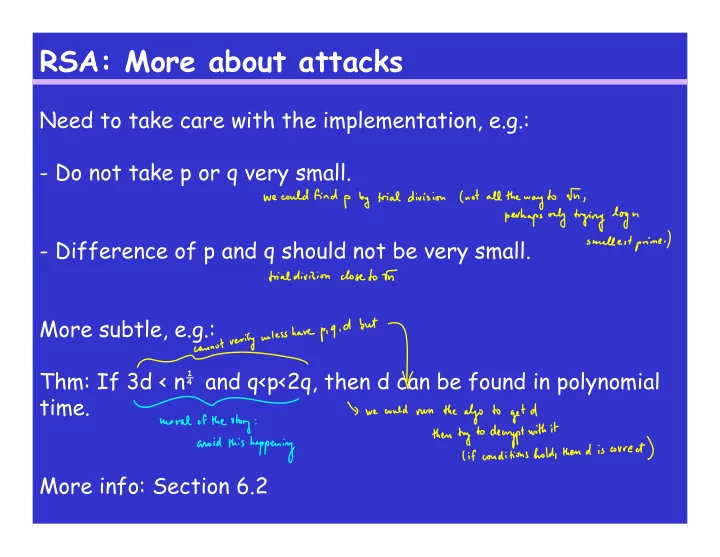

RSA: More about attacks Need to take care with the implementation, e.g.: - Do not take p or q very small. - Difference of p and q should not be very small. More subtle, e.g.: Thm: If 3d < n ¼ and q<p<2q, then d can be found in polynomial time. More info: Section 6.2
RSA: More about attacks Public-key cryptosystem: can it have perfect secrecy ? RSA is insecure against a chosen-ciphertext attack (we’ll do soon). Is RSA insecure against a known-plaintext attack ? Is RSA insecure against a chosen-plaintext attack ?
RSA: Protocol Failures Secure system can still be used in an insecure (careless) way. This is called a protocol failure. Examples: Exercises 16 and 17 (Chapter 6, page 194)
RSA: Insecurity against Chosen-Ciphertext Eve wants to decrypt y (a ciphertext). She can choose another ciphertext ŷ y that she can use to decrypt y. Choose a random x 0 and compute y 0 = (x 0 ) e mod n. Let ŷ = y 0 y mod n. Eve gets the decryption of ŷ . How to find x ?
RSA: Timing Attacks In 1995, Paul Kocher (an undergraduate at Standford), discovered that it is possible to determine d (the decryption exponent) by carefully timing the computation times for a sequence of decryptions. Moral of the story: a new type of attack can break a system that is though to be secure… Good news for RSA: it is possible to thwart the timing attack.
Other Public-key Cryptosystems RSA is the “standard” but there are other public-key cryptosystems. E.g. one by Rabin and one by ElGamal. All three cryptosystems: - thought to be secure - can be used for digital signatures - slow Hence: used to encrypt a session key, then use a (secure) private key cryptosystem
Other Public-key Cryptosystems The Rabin cryptosystem: - based on the difficulty of finding square roots mod a composite number (problem equivalent to factoring) - provably secure (unlike RSA; assuming factoring is computationally infeasible, the Rabin cryptosystem is secure) - 4 possible plaintexts for each ciphertext [RSA: conjectured to be as secure as factoring.] The ElGamal cryptosystem: - based on the difficulty of computing discrete logarithms in a finite field - used in many cryptographic protocols
Public-key Cryptosystems Outline of a general public-key cryptosystem: - components: a set M of messages, a set K of keys, for each key k ∈ K, an encryption function E k and a decryption function D k (usually functions from M to M) - requirements: - E k (D k (m)) = D k (E k (m)) for all m, k. - E k (m) and D k (m) are easy to compute for all m, k. - figuring out D k from E k is computationally infeasible for almost all k ∈ K - given k ∈ K, finding E k and D k is easy
Recommend
More recommend