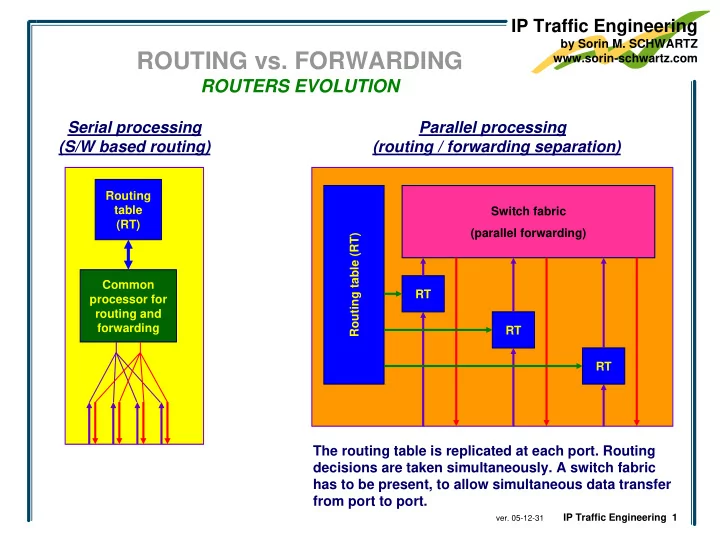

IP Traffic Engineering by Sorin M. SCHWARTZ ROUTING vs. FORWARDING www.sorin-schwartz.com ROUTERS EVOLUTION Serial processing Parallel processing (S/W based routing) (routing / forwarding separation) Routing table Switch fabric (RT) (parallel forwarding) Routing table (RT) Common RT processor for routing and forwarding RT RT The routing table is replicated at each port. Routing decisions are taken simultaneously. A switch fabric has to be present, to allow simultaneous data transfer from port to port. IP Traffic Engineering 1 ver. 05-12-31
IP Traffic Engineering by Sorin M. SCHWARTZ ROUTING vs. FORWARDING www.sorin-schwartz.com ROUTERS EVOLUTION Label switching Switch fabric Switch fabric Switch fabric (parallel forwarding) (parallel forwarding) (parallel forwarding) Routing table (RT) Routing table (RT) Routing table (RT) remove LABEL LABEL add RT RT RT Concepts • Ingress router adds a label • Core routers identify the label and forward to apriori decided port (next hop) • Egress router removes the label • Assumptions • The route to be followed has been decided in an independent process that occurred before the network operation • Routers have bindings between specific labels and specific, apriori decided routes to be followed by packets marked with that labels IP Traffic Engineering 2 ver. 05-12-31
IP Traffic Engineering by Sorin M. SCHWARTZ MULTIPROTOCOL LABEL SWITCHING (MPLS) www.sorin-schwartz.com BASIC OPERATION Q S IP DA = Y Label payload T MPLS cloud LSR LSR stacking P 2 5 Rd 1 IP DA = Y L211 payload IP DA = T LSR X L411 IP DA = Y Rb payload L652 4 payload 1 1 1 2 2 2 LSR LSR LSR LSR Ra Re 1 3 3 6 7 Y IP DA = Y L161 L363 payloa d IP DA = T IP DA = T L162 L363 L672 payload payload FTN ILM LSR6 tables NHLF (Next Hop Label Forwarding) (FEC-To-NHLF) (Incoming Label Map) NHLFE NHLFE next physical FEC (Next Hop Label label (Next Hop Label NHLFE operation label hop interface Forwarding Entry) Forwarding Entry) - (-) 361 (1) (1) label swap L651 LSR5 1 - (-) 362 (2) (2) label swap L671 LSR7 2 363 (3) (3) label pop L363 - - 161 (4) (4) label swap L652 LSR5 1 162 (5) (5) label swap L672 LSR7 2 IP Traffic Engineering 3 ver. 05-12-31
IP Traffic Engineering by Sorin M. SCHWARTZ MULTIPROTOCOL LABEL SWITCHING (MPLS) www.sorin-schwartz.com LABEL ENCODING Identifying labeled packets • Layer 2 header is written following the rules in effect between the sending LSR and the receiving next hop LSR • The receiving LSR should identify the packet as a “labeled” one, as opposed to a non-labeled packet which could arrive on the same link MPLS label presence is indicated by new Layer 2 header Ethernet Layer 3 header IP + … Ethertypes - hex 8847 (dec 34,887) - MPLS unicast DA SA Type = IP - hex 8848 (dec 34,888) - MPLS multicast (To be used with LLC/SNAP/OUI 000000, too) LSR 1 Layer 2 header Ethernet Layer 3 header IP + … LABEL EXP S TTL DA SA Type = MPLS 1 After removing the last label, the packet should be processed based on its original layer 3 LSR header, but the information related to layer 3 protocol in the original packet is lost! 2 LSR should be able to identify original layer 3 protocol for internal processing and for the generation of the packet to be sent to the next hop. Layer 2 header Ethernet Layer 3 header ?? + … DA SA Type = ?? IP Traffic Engineering 4 ver. 05-12-31
IP Traffic Engineering by Sorin M. SCHWARTZ Virtual Private Networks www.sorin-schwartz.com LAYER 3, BGP/MPLS based VPN Basic operation - Routing information exchange Step 6 site 5 (simplified) CEe • PE4 has “VRF site6” site 1 CEd export route target “VPN NET2 PE PE RED” 2 3 NET1 site 2 • PE1 has “VRF site2” import site CEc 6 route target “VPN RED”, so CEf site 3 CEb NET4 it will accept the MP-iBGP P6 NET3 NET1 update arriving from PE4 • PE1 updates its “VRF PE PE site2” table CEa CEg P5 P7 1 L57 4 L15 site 4 NET2 NET3 site 7 CE VRF VRF MP-iBGP session CEf site 2 site 6 b BGP BGP tables tables VRF VRF CE P5 P7 site 4 site 7 CE g a IGP and IGP and IGP IGP IGP IGP and MPLS IGP and MPLS MPLS MPLS tables tables LDP LDP LDP PE1 tables tables PE4 PE1 “VRF site2” routing table PE1 BGP routing table PE1 IGP routing table To Deliver to To Deliver To Deliver physical nr of int’f int’f destination router destination to router destination to router interface hops FEC FEC FEC a / PE4 PE4 0 net3 PE4 site6:net3 site6:net3 PE4 site6:net3 L15 (L63) (L63) IP Traffic Engineering 5 ver. 05-12-31
IP Traffic Engineering by Sorin M. SCHWARTZ Virtual Private Networks www.sorin-schwartz.com IP Sec based VPN Authentication and Integrity Check principles Generating and Using the ICV - Transmission process Original packet before authentication process ICV (Integrity Check (IP header + payload) Value) is the result of two Packet with consecutive processes added executed over the packet authentication Original packet (IP header + payload) ICV Authentication Field to be protected: fields , including ICV - step 1 - A hash value is field (sent to the other site) calculated for the packet - For calculation purposes only, the ICV field value is set to “0” to be protected. The hash - For calculation purposes only, fields expected to change during variable length the travel through the network are set to “0” (e.g. time to live) input data function is not a secret. - step 2 - The hash value SHA-1 obtained in step 1 is MD5 encrypted using a secret hash function key, generating the ICV value to be added to the fixed length encryption key packet. output data (128 or 160 bits) The encrypted hash value DES 3DES (the MAC) can be encryption correctly decoded ONLY function by the SAME secret key, MAC at reception side. HMAC-SHA-1-96 HMAC-MD5-96 IP Traffic Engineering 6 ver. 05-12-31
Recommend
More recommend