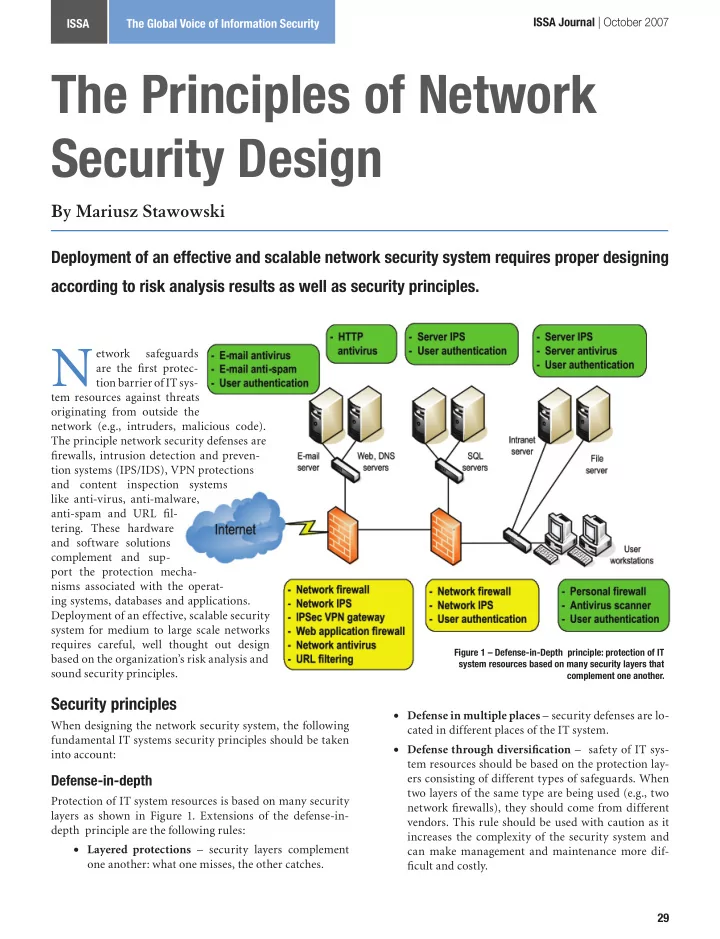

ISSA Journal | October 2007 ISSA The Global Voice of Information Security The Principles of Network Security Design By Mariusz Stawowski Deployment of an effective and scalable network security system requires proper designing according to risk analysis results as well as security principles. N etwork safeguards are the first protec- tion barrier of IT sys- tem resources against threats originating from outside the network (e.g., intruders, malicious code). The principle network security defenses are firewalls, intrusion detection and preven- tion systems (IPS/IDS), VPN protections and content inspection systems like anti-virus, anti-malware, anti-spam and URL fil- tering. These hardware and software solutions complement and sup- port the protection mecha- nisms associated with the operat- ing systems, databases and applications. Deployment of an effective, scalable security system for medium to large scale networks requires careful, well thought out design Figure 1 – Defense-in-Depth principle: protection of IT based on the organization’s risk analysis and system resources based on many security layers that sound security principles. complement one another. Security principles • Defense in multiple places – security defenses are lo- When designing the network security system, the following cated in different places of the IT system. fundamental IT systems security principles should be taken • Defense through diversification – safety of IT sys- into account: tem resources should be based on the protection lay- Defense-in-depth ers consisting of different types of safeguards. When two layers of the same type are being used (e.g., two Protection of IT system resources is based on many security network firewalls), they should come from different layers as shown in Figure 1. Extensions of the defense-in- vendors. This rule should be used with caution as it depth principle are the following rules: increases the complexity of the security system and • Layered protections – security layers complement can make management and maintenance more dif- one another: what one misses, the other catches. ficult and costly. 29
The Principles of Network Security Design | Mariusz Stawowski ISSA Journal | October 2007 Compartmentalization of information IT system resources of different sensitivity levels (i.e., different risk tolerance values and threat susceptibility) should be located in different security zones. The concept of this principle is shown in Figure 2. An extension of this rule is “informa- tion hiding”: the IT system makes available only such data that is necessary for conducting the IT system tasks (e.g., only servers pro- viding services to the Internet are registered in pub- lic DNS). Principle of Figure 2 – Compartmentalization of information: IT system resources of different sensitivity levels should be located in different security zones. least privilege create secure architectures, dividing the IT system network IT system subjects (e.g., users, administrators) should have infrastructure into security zones and controlling commu- minimal privileges necessary for proper functioning within nication between them. The compartmentalization principle the organization. This rule applies also to data and services describes the following network security design rules: made available for external users. An extension to this rule is the “Need-To-Know” principle which says that users and ad- 1. IT system resources of different sensitivity levels should be ministrators of IT system have access to only the information located in different security zones: relevant to their role and duties performed. • Devices and computer systems providing services for Weakest link in the chain external networks (e.g., the Internet) should be locat- ed in different zones (De-Militarized Zone – DMZ) The security level of the IT system depends on the least se- than internal network devices and computer systems cured element of the system. An extension of this rule in re- • Strategic IT system resources should be located in spect to network services availability is the “single point of dedicated security zones failure” principle, which says that on the network paths be- • tween users and mission-critical IT system resources, all the Devices and computer systems of low trust level such links, devices (networking and security) as well as the servers as remote access servers and wireless network access should be deployed in redundant configurations (so called points should be located in dedicated security zones High Availability – HA). 2. IT system resources of different types should be located in When designing the network security system, the principles separate security zones: of organizational security such as “Separation of Duty” and • User workstations should be located in different secu- “Job Rotation” rules should also be taken into account. Their rity zones than servers goal is to limit an employee’s ability to neglect and break the • Network and security management systems should be IT system’s security policy. Separation of duty dictates that located in dedicated security zones important tasks/functions should be performed by two or • more employees. Job rotation states that there should be rota- Systems in development stage should be located in tion of employees in important positions. different zones than production systems Security zones Intrusion prevention The basic means of keeping network traffic flowing where IPS devices are responsible for detecting and blocking pen- you want and restricting it where you do not is the firewall: etrations and attacks conducted by intruders and malicious dedicated firewall devices, firewall functions in IPS devices, malware applications. They should be installed in the net- and access control lists in network routers and switches. work path between potential threat sources and sensitive With proper placement and configuration, firewalls help IT system resources. When designing IPS systems, attacks 30
Recommend
More recommend