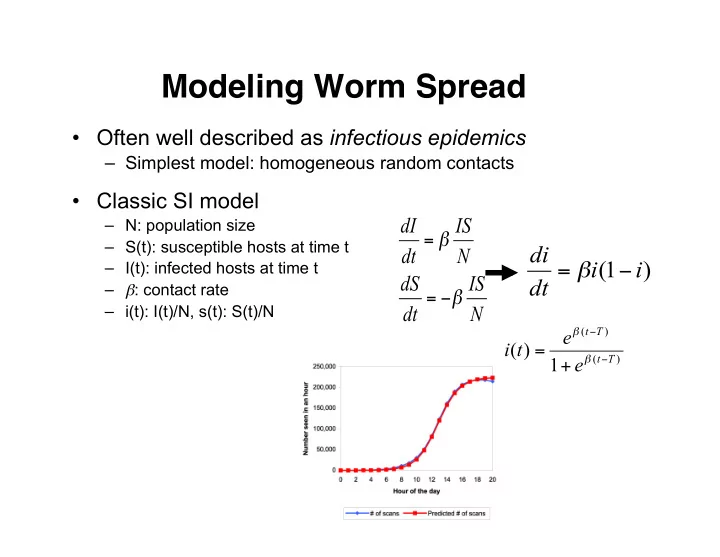

Modeling Worm Spread • Often well described as infectious epidemics – Simplest model: homogeneous random contacts • Classic SI model dI IS – N: population size = β – S(t): susceptible hosts at time t di dt N i ( 1 i ) – I(t): infected hosts at time t = β − dS IS dt – β : contact rate = − β dt N – i(t): I(t)/N, s(t): S(t)/N ( t T ) e β − i ( t ) = ( t T ) 1 e β − +
The Usual Logistic Growth
Slammer ’ s Growth (2003)
80% of Code Red 2 Code Red 2 re-re- Code Red 1 and Code Red 2 Code Red 2 re- cleaned up due to released Jan 2004 Nimda endemic dies off released with Oct. onset of Blaster (and 2005; not since … ?) again 2003 die-off
Code Red 2 re-re- Feb 19 2013! released Jan 2004 (and 2005; not since … ?)
2009 - 2010
2015-2016
Stuxnet : Slowly ramped up centrifuge speeds until they flew apart … … while feeding false readings to control system. Included 4 zero days for spreading
Flame : General information stealer. Includes geolocation from local photos, taking screenshots, microphone access to capture local audio, recording Skype calls, download contacts from nearby BlueTooth devices. Exploited previously unknown MD5 hash collision vulnerability . Built-in autowipe “ kill switch ” .
Gauss : Specifically targets banking transactions, mainly in Lebanon. Includes trapdoor looking for specific accounts, undeciphered to date.
#!/usr/bin/perl while (<>) { chomp; if ( /^(get|post|options|head|...)(.*)/i ) { # Do not respond if it looks like an exploit last if length > 1000; my $date = gmtime; if ( $1 =~ /get|head/i ) print "HTTP/1.1 200 OK\r\n"; elsif ( $1 =~ /search/i ) print "HTTP/1.1 411 Length Required\r\n"; elsif ( $1 =~ /options/i ) { print "HTTP/1.1 200 OK\r\n"; print "DASL: \r\nDAV: 1, 2\r\n"; print "Public: OPTIONS, TRACE, GET, HEAD, DELETE, ...\r\n"; print "Allow: OPTIONS, TRACE, GET, HEAD, DELETE, ...\r\n"; } elsif ( $1 =~ /propfind/i ) print "HTTP/1.1 207 Multi-Status\r\n"; else print "HTTP/1.1 405 Method Not Allowed\r\n"; } print <<EOF; Server: Microsoft-IIS/5.0 Date: $date GMT Content-Length: 0 Content-Type: text/html Set-Cookie: ASPSESSIONIDACBAABCQ=BHAMAEHAOAIHMOMGJCPFLBGO; path=/ Cache-control: private EOF last; } }
Polymorphic Propagation Decryptor Key Encrypted Glob of Bits ê Decryptor Once running, worm Encryptor uses an encryptor with Key Main Worm Code a new key to propagate } Jmp ê Decryptor Key ' Different Encrypted Glob of Bits
Metamorphic Propagation When ready to propagate, Rewriter worm invokes a randomized Main Worm Code rewriter to construct new but semantically equivalent worm code (incl. rewriter) } ê Rewriter' (Main Worm Code)' } ê Rewriter'' (Main Worm Code)''
Recommend
More recommend