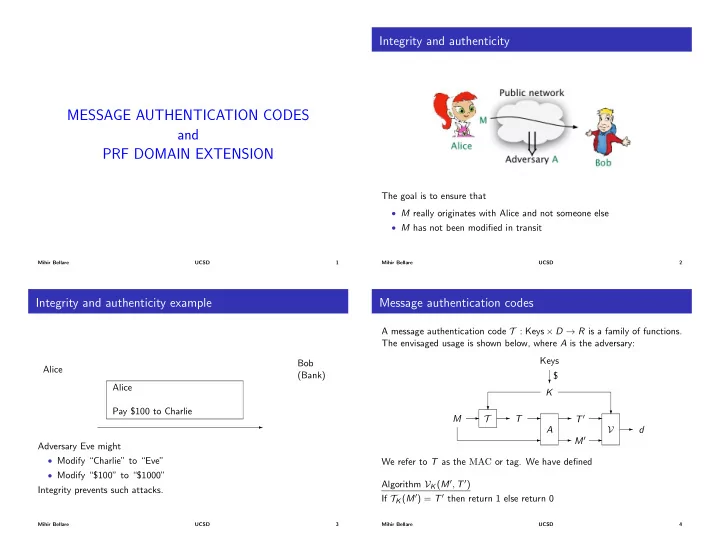

Integrity and authenticity MESSAGE AUTHENTICATION CODES and PRF DOMAIN EXTENSION The goal is to ensure that • M really originates with Alice and not someone else • M has not been modified in transit Mihir Bellare UCSD 1 Mihir Bellare UCSD 2 Integrity and authenticity example Message authentication codes A message authentication code T : Keys ⇥ D ! R is a family of functions. The envisaged usage is shown below, where A is the adversary: Keys Bob Alice (Bank) $ ? Alice K ? Pay $100 to Charlie ? - T T M - - - T 0 - - d - A V - - M 0 - Adversary Eve might • Modify “Charlie” to “Eve” We refer to T as the MAC or tag. We have defined • Modify “$100” to “$1000” Algorithm V K ( M 0 , T 0 ) Integrity prevents such attacks. If T K ( M 0 ) = T 0 then return 1 else return 0 Mihir Bellare UCSD 3 Mihir Bellare UCSD 4
MAC usage UF-CMA Let T : Keys ⇥ D ! R be a message authentication code. Let A be an adversary. Game UFCMA T Sender and receiver share key K . procedure Initialize procedure Finalize ( M , T ) To authenticate M , sender transmits ( M , T ) where T = T K ( M ). $ If M 2 S then return false K Keys ; S ; If M 62 D then return false Upon receiving ( M 0 , T 0 ), the receiver accepts M 0 as authentic i ff procedure Tag ( M ) Return ( T = T K ( M )) V K ( M 0 , T 0 ) = 1, or, equivalently, i ff T K ( M 0 ) = T 0 . T T K ( M ); S S [ { M } return T The uf-cma advantage of adversary A is Adv uf - cma h i UFCMA A ( A ) = Pr T ) true T Mihir Bellare UCSD 5 Mihir Bellare UCSD 6 UF-CMA: Explanations Exercise: Tag lengths Adversary A does not get the key K . It can call Tag with any message M of its choice to get back the correct Let T : Keys ⇥ D ! { 0 , 1 } ` be a message authentication code. Specify in tag T = T K ( M ). pseudocode an e ffi cient adversary A making zero Tag queries and To win, the adversary A must output a message M 2 D and a tag T that achieving Adv uf - cma ( A ) = 2 � ` . are T • Correct: T = T K ( M ) Conclusion: Tags have to be long enough. • New: M 62 S , meaning M was not a query to Tag For 80 bit security, tags have to be at least 80 bits. Interpretation: Tag represents the sender and Finalize represents the receiver. Security means that the adversary can’t get the receiver to accept a message that is not authentic, meaning was not already transmitted by the sender. Mihir Bellare UCSD 7 Mihir Bellare UCSD 8
Example: Basic CBC MAC Splicing attack on basic CBC MAC Let E : { 0 , 1 } k ⇥ B ! B be a blockcipher, where B = { 0 , 1 } n . View a message M 2 B ⇤ as a sequence of n -bit blocks, M = M [1] . . . M [ m ]. adversary A The basic CBC MAC T : { 0 , 1 } k ⇥ B ⇤ ! B is defined by Alg T K ( M ) Let x 2 { 0 , 1 } n C [0] 0 n Alg T K ( M ) T 1 Tag ( x ) for i = 1 , . . . , m do C [0] 0 n M x || T 1 � x C [ i ] E K ( C [ i � 1] � M [ i ]) for i = 1 , . . . , m do C [ i ] E K ( C [ i � 1] � M [ i ]) Return M , T 1 return C [ m ] return C [ m ] Then, M [ m � 1] M [ m ] M [1] M [2] T 1 � x x E K ( E K ( x ) � T 1 � x ) T K ( M ) = E K E K E K ( T 1 � T 1 � x ) = E K E K E K E K = E K ( x ) T 1 T 1 C [ m ] = T K ( M ) = T 1 Mihir Bellare UCSD 9 Mihir Bellare UCSD 10 Insecurity of basic CBC MAC Exercise Let E : { 0 , 1 } k ⇥ { 0 , 1 } n ! { 0 , 1 } n be a blockcipher. Let D = { M 2 { 0 , 1 } ⇤ : 0 < | M | < n 2 n and | M | mod n = 0 } . Let T : { 0 , 1 } k ⇥ D ! { 0 , 1 } n be defined as follows: adversary A Alg T K ( M ) Let x 2 { 0 , 1 } n C [0] 0 n Alg T K ( M ) T 1 Tag ( x ) for i = 1 , . . . , m do M [1] . . . M [ m ] M ; M [ m + 1] h m i ; C [0] 0 n M x || T 1 � x C [ i ] E K ( C [ i � 1] � M [ i ]) For i = 1 , . . . , m + 1 do C [ i ] E K ( C [ i � 1] � M [ i ]) Return M , T 1 return C [ m ] T C [ m + 1]; return T Then Adv uf - cma ( A ) = 1 and A is e ffi cient, so the basic CBC MAC is not Above, h m i denotes the n -bit binary representation of the integer m . T UF-CMA secure. Show that T is not UF-CMA-secure by presenting in pseudocode a practical adversary A making at most 4 Tag queries and achieving Adv uf - cma ( A ) = 1. T Mihir Bellare UCSD 11 Mihir Bellare UCSD 12
Exercise Replay Let E : { 0 , 1 } k ⇥ { 0 , 1 } n ! { 0 , 1 } n be a blockcipher. Let Suppose Alice transmits ( M 1 , T 1 ) to Bank where M 1 =“Pay $100 to D = { M 2 { 0 , 1 } ⇤ : 0 < | M | < n 2 n and | M | mod n = 0 } . Bob”. Adversary Let T : { 0 , 1 } k ⇥ D ! { 0 , 1 } n be defined as follows: • Captures ( M 1 , T 1 ) • Keeps re-transmitting it to bank Alg T K ( M ) Result: Bob gets $100, $200, $300,... M [1] . . . M [ m ] M ; C [0] E K ( h m i ) Our UF-CMA notion of security does not ask for protection against replay, For i = 1 , . . . , m do C [ i ] E K ( C [ i � 1] � M [ i ]) because A will not win if it outputs M , T with M 2 S , even if T = T K ( M ) T C [ m ]; return T is the correct tag. Above, h m i denotes the n -bit binary representation of the integer m . Question: Why not? Is T UF-CMA-secure? If you say NO, present a practical adversary A Answer: Replay is best addressed as an add-on to standard message achieving Adv uf - cma ( A ) � 1 / 2. If you say YES, prove this correct authentication. T assuming E is PRF-secure. Mihir Bellare UCSD 13 Mihir Bellare UCSD 14 Preventing Replay Using Timestamps Preventing Replay Using Timestamps Let Time A be the time as per Alice’s local clock and Time B the time as Let Time A be the time as per Alice’s local clock and Time B the time as per Bob’s local clock. per Bob’s local clock. • Alice sends ( M , T K ( M ) , Time A ) • Alice sends ( M , T K ( M ) , Time A ) • Bob receives ( M , T , Time ) and accepts i ff T = T K ( M ) and • Bob receives ( M , T , Time ) and accepts i ff T = T K ( M ) and | Time B � Time | ∆ where ∆ is a small threshold. | Time B � Time | ∆ where ∆ is a small threshold. Does this work? Does this work? Obviously forgery is possible within a ∆ interval. But the main problem is that Time A is not authenticated, so adversary can transmit ( M , T K ( M ) , Time 1 ) , ( M , T K ( M ) , Time 2 ) , . . . for any times Time 1 , Time 2 , . . . of its choice, and Bob will accept. Mihir Bellare UCSD 15 Mihir Bellare UCSD 16
Preventing Replay Using Timestamps Preventing Replay Using Counters Alice maintains a counter ctr A and Bob maintains a counter ctr B . Initially Let Time A be the time as per Alice’s local clock and Time B the time as both are zero. per Bob’s local clock. • Alice sends ( M , T K ( M k ctr A )) and then increments ctr A • Alice sends ( M , T K ( M k Time A ) , Time A ) • Bob receives ( M , T ). If T K ( M k ctr B ) = T then Bob accepts and • Bob receives ( M , T , Time ) and accepts i ff T K ( M k Time ) = T and increments ctr B . | Time B � Time | ∆ where ∆ is a small threshold. Counters need to stay synchronized. Mihir Bellare UCSD 17 Mihir Bellare UCSD 18 Any PRF is a MAC Intuition for why PRFs are UF-CMA-secure If F is PRF-secure then it is also UF-CMA-secure: 1 Random functions make good (UF-CMA) MACs Theorem [GGM86,BKR96]: Let F : { 0 , 1 } k ⇥ D ! { 0 , 1 } n be a family of 2 PRFs are pretty much as good as random functions functions. Let A be a uf-cma adversary making q Tag queries and having running time t . Then there is a prf-adversary B such that For (1), suppose Fn : D ! { 0 , 1 } n is random and consider A who F ( B ) + 2 Adv uf - cma • Can query Fn at any points x 1 , . . . , x q 2 D it likes ( A ) Adv prf 2 n . F • To win, must output x , T such that x / 2 { x 1 , . . . , x q } but T = Fn ( x ) Adversary B makes q + 1 queries to its Fn oracle and has running time t Then, plus some overhead. Pr[ A wins] = Exercise: Prove this theorem. We now give some intuition. Mihir Bellare UCSD 19 Mihir Bellare UCSD 20
Recommend
More recommend