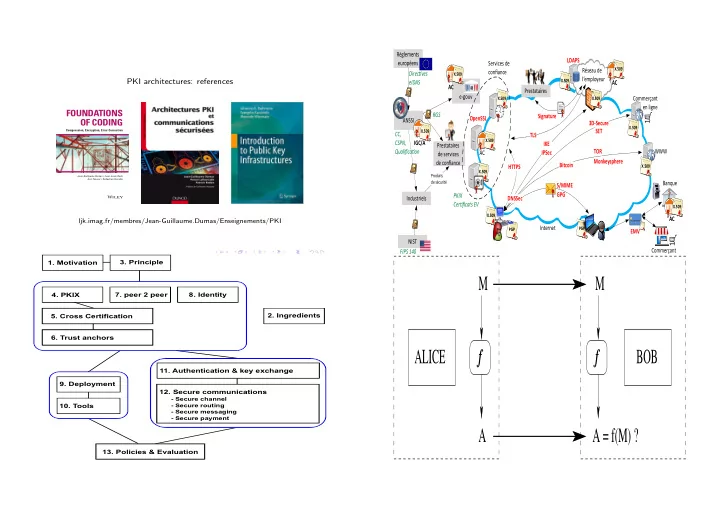

Règlements LDAPS européens Services de X.509 Réseau de con fi ance Direc � ves X.509 l’employeur PKI architectures: references X.509 eIDAS AC AC @ Prestataires e-gouv Commerçant X.509 X.509 en ligne FOUNDATIONS RGS Signature OpenSSL ANSSI OF CODING 3D-Secure X.509 SET Compression, Encryption, Error Correction X.509 CC, TLS X.509 CSPN, IGC/A IKE Prestataires Quali fi ca � on TOR WWW AC IPSec de services Monkeysphere de con fi ance Bitcoin HTTPS X.509 X.509 Produits Jean-Guillaume Dumas • Jean-Louis Roch Éric Tannier • Sébastien Varrette de sécurité Banque S/MIME $ GPG PKIX Industriels DNSSec Cer �fi cats EV X.509 X.509 AC ljk.imag.fr/membres/Jean-Guillaume.Dumas/Enseignements/PKI Internet PGP PGP EMV NIST Commerçant FIPS 140 3. Principle 1. Motivation M M 4. PKIX 7. peer 2 peer 8. Identity 5. Cross Certification 2. Ingredients 6. Trust anchors ALICE f f BOB 11. Authentication & key exchange 9. Deployment 12. Secure communications - Secure channel 10. Tools - Secure routing - Secure messaging - Secure payment A A = f(M) ? 13. Policies & Evaluation
Document Signature function Signed document PKCS Standards Summary, From Wikipedia Version Name Comments PKCS RSA Cryptography Standard [1] See RFC 3447. Defines the mathematical properties and format of RSA public and private keys (ASN.1-encoded in clear-text), and the basic 2.1 #1 blablabbla blablabbla algorithms and encoding/padding schemes for performing RSA encryption, decryption, and producing and verifying signatures. Hash PKCS Signature blablabbla blablabbla Withdrawn - No longer active as of 2010. Covered RSA encryption of message digests; subsequently merged into PKCS #1. #2 function algorithm PKCS Diffie–Hellman Key A cryptographic protocol that allows two parties that have no prior knowledge of each other to jointly establish a shared secret key over an 1.4 #3 ALICE Agreement Standard [2] insecure communications channel. PKCS Withdrawn - No longer active as of 2010. Covered RSA key syntax; subsequently merged into PKCS #1. #4 PKCS Password-based Encryption 2.0 See RFC 2898 and PBKDF2. #5 Standard [3] PKCS Extended-Certificate Syntax 1.5 Defines extensions to the old v1 X.509 certificate specification. Obsoleted by v3 of the same. #6 Standard [4] Public key and private See RFC 2315. Used to sign and/or encrypt messages under a PKI. Used also for certificate dissemination (for instance as a response to a PKCS Cryptographic Message Syntax 1.5 PKCS#10 message). Formed the basis for S/MIME, which is as of 2010 based on RFC 5652, an updated Cryptographic Message Syntax #7 key generation Standard [5] Private key Standard (CMS). Often used for single sign-on. PKCS Private-Key Information 1.2 See RFC 5208. Used to carry private certificate keypairs (encrypted or unencrypted). #8 Syntax Standard [6] PKCS See RFC 2985. Defines selected attribute types for use in PKCS #6 extended certificates, PKCS #7 digitally signed messages, PKCS #8 Selected Attribute Types [7] 2.0 #9 private-key information, and PKCS #10 certificate-signing requests. PKCS Certification Request 1.7 See RFC 2986. Format of messages sent to a certification authority to request certification of a public key. See certificate signing request. #10 Standard [8] Alice PKCS Public key Cryptographic Token Also known as "Cryptoki". An API defining a generic interface to cryptographic tokens (see also Hardware Security Module). Often used in 2.20 #11 Interface [9] single sign-on, Public-key cryptography and disk encryption [10] systems. Defines a file format commonly used to store private keys with accompanying public key certificates, protected with a password-based symmetric key. PFX is a predecessor to PKCS#12. PKCS Personal Information Exchange Verification function 1.0 Signed document #12 Syntax Standard [11] This container format can contain multiple embedded objects, such as multiple certificates. Usually protected/encrypted with a password. Response Usable as a format for the Java key store and to establish client authentication certificates in Mozilla Firefox. Usable by Apache Tomcat. Signature Signature Valid signature PKCS ALICE Elliptic Curve Cryptography (Under development as of 2012.) [13] – #13 Standard [12] blablabbla verification algorithm or PKCS blablabbla Pseudo-random Number (Under development as of 2012.) [13] Invalid signature – #14 Generation Extraction Document Cryptographic Token PKCS Defines a standard allowing users of cryptographic tokens to identify themselves to applications, independent of the application's Cryptoki ALICE 1.1 Information Format #15 implementation (PKCS #11) or other API. RSA has relinquished IC-card-related parts of this standard to ISO/IEC 7816-15. [15] Hash Standard [14] blablabbla blablabbla function KDC : Key Distribution Center M Clients and keys Data basis (1) KRB_AS_REQ : ticket request for the TGS AS : Authentification Server (2) KRB_AS_REP : ticket for the TGS Hash TGS : Ticket−Granting Service ALICE (3) KRB_TGS_REQ : ticket request 00.........00 mH salt K tgs for Bob K A (4) KRB_TGS_REP : ticket for Bob 00.........00 0x01 salt Hash (1) : a,tgs BOB K ( || Alice ||...), T K a,tgs (5) KRB_AP_REQ : service request (2) : a a,tgs MGF A a,tgs ,b, T a,tgs KB (3) : (6) KRB_AP_REP : Bob’s answer ( || Alice ||...), T K (4) : K a,tgs a,b a,b (5) : A , T a,b a,b mask H 0xbc K (t+1) (6) : a,b
Another entity Entity Realm 1 KDC Kerberos using certificates (5) (Possibly) (Alice) (1) KRB_AS1_REQ (Bob) CA provides AS 1 the certificate to Alice (2) KRB_AS1_REP (2) Applicant TGS 1 (1) Certificate (3) KRB_TGS1_REQ : for TGS2 ALICE authentification K tgs1 request K A PKI Users (4) KRB_TGS1_REP : ticket for TGS2 (7) KRB_AP_REQ : service request PKI Administration Lookup KDC Kerberos (5) KRB_TGS2_REQ : for Bob (6) KRB_TGS2_REP : ticket for Bob RA AS 2 Directory (3) Certification request BOB TGS 2 KB K tgs2 Certificates CA + CRL Realm 2 (4) CA publishes the certificate Information X.509 Electronic Certificate C (country) : France Version Version v3 (0x2) L (Locality) : Grenoble ST : (State or Province) : Isère Serial Number Serial Number 14 (0xE) O (Organisation) : UdG SO (Organizational Unit) : icluster Signature Algorithm ID Signature Algorithm ID md5WithRSAEncryption CN (Common Name) : Icluster_CA Issuer Name Issuer Name STREET (Adress): 50 av Jean Kuntzmann E (Email) : ca@udg.fr Validity Period Not Before : Validity Périod Jun 8 14:52:40 2003 GMT − Start Date/Time − Start Date/Time C (country) : France Not After − End Date/Time − End Date/Time L (Locality) : Grenoble Jun 7 14:52:40 2004 GMT ST : (State or Province) : Isère Subject Name Subject Name O (Organisation) : UdG Public Key Algorithm : SO (Organizational Unit) : LJK Subjet Public Key Info : Subjet Public Key Info : rsaEncryption CN (Common Name) : Jean−Guillaume Dumas − Algorithm ID − Algorithm ID RSA Public Key (1024bit) STREET (Adress): 51, av des Mathématiques − Public Key Value − Public Key Value Modulus (1024 bits) : E (Email) : Jean−Guillaume.Dumas@imag.fr 00:b3:e4:4f:....... Issuer Unique ID Issuer Unique ID Exponent : 65537 (0x10001) Subject Unique ID Subject Unique ID Extension Extension Signature − Algorithm ID CA private key − Signature Value Signature
7°) Key : OK Signed Certificate Certificate Alice Subject : Alice Subject : Alice Hash Pub. Key : KpubA Pub. Key : KpubA Public key 1°) Recovery Issuer : Ivan 2°) Extraction Issuer : Ivan Function Signature Signature : s 6°) Signature verification s algorithm Bob Issuer == Ivan Ivan Public key Root Certificate Certificate Subject: Ivan Subject : Ivan Hash Pub. key : KpubI Pub. Key : KpubI 3°) Recovery Issuer : Ivan 4°) Extraction Issuer : Ivan Function Signature Signature : r 5°) Signature verification r algorithm Ivan Public key
Alg. Hash. OID Identificator 3DES-CBC 1.2.840.113549.3.7 DES-EDE3-CBC RSA 1.2.840.113549.1.1.1 RSAEncryption RSA MD5 1.2.840.113549.1.1.4 md5withRSAEncryption RSA SHA-1 1.2.840.113549.1.1.5 sha1withRSAEncryption DSA 1.2.840.10040.4.1 id-dsa DSA SHA-1 1.2.840.10040.4.3 id-dsawithSha1 DSA SHA-1.320 1.3.14.3.2 id-dsawithSha1.320 ECDSA SHA-1 1.2.840.10045.1 ecdsawithSha1 Reasons to revoke a certificate [RFC 5280] • unspecified (0) • keyCompromise (1) • CACompromise (2) • affiliationChanged (3) • superseded (4) • cessationOfOperation (5) • certificateHold (6) • removeFromCRL (8) • privilegeWithdrawn (9) • AACompromise (10) Obs.: Value 7 is not used.
Certificate signed with NEW priv Certificate signed with OLD priv Repository contains OLD and NEW NEW pub Recover OLDwNEW within DIRECT verification Verify OLDwNEW PSE with NEW pub Verify certificate with OLD pub OLD pub Recover NEWwOLD within Verify NEWwOLD DIRECT verification PSE with OLD pub Verify certificate with NEW pub Repository contains only OLD NEW pub DIRECT verification FAILURE (Repository’s fault) within PSE (without the Repository) OLD pub FAILURE (Repository’s fault) DIRECT verification within PSE Bob Alice (C) C=E (r) r=D Kpriv−Bob Kpub−Bob C K =H(r) s K =H(r) s
[FIPS−196 Authentification Request] 1°) [ Token ID ] || Token BA 1 2°) Alice Bob [ Token ID ] || [ Cert A ] || Token AB || SIGN privA ( Token AB ) 3°) [ Token ID ] || [ Cert B ] || Token BA 2 || SIGN privB ( Token BA 2 ) 4°)
Recommend
More recommend