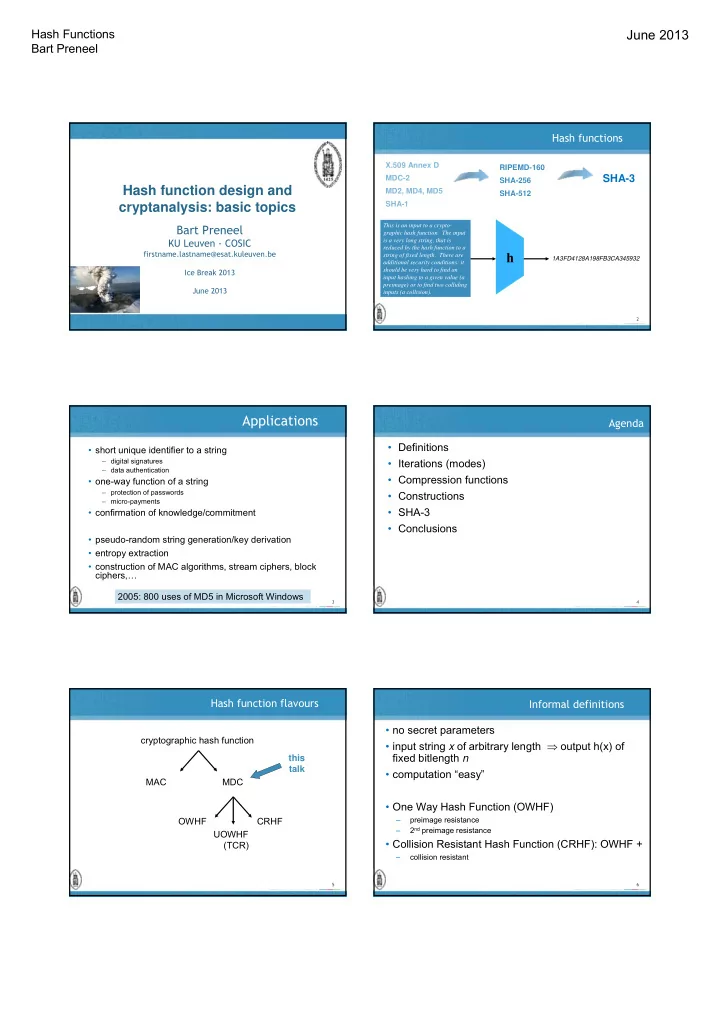

Hash Functions June 2013 Bart Preneel Hash functions X.509 Annex D RIPEMD-160 SHA-3 MDC-2 SHA-256 Hash function design and MD2, MD4, MD5 Title of Presentation SHA-512 SHA-1 cryptanalysis: basic topics Bart Preneel This is an input to a crypto- graphic hash function. The input KU Leuven - COSIC is a very long string, that is reduced by the hash function to a firstname.lastname@esat.kuleuven.be h string of fixed length. There are 1A3FD4128A198FB3CA345932 additional security conditions: it Ice Break 2013 should be very hard to find an input hashing to a given value (a preimage) or to find two colliding June 2013 inputs (a collision). Insert presenter logo here on slide master 2 Applications Agenda • Definitions • short unique identifier to a string – digital signatures • Iterations (modes) – data authentication • Compression functions • one-way function of a string – protection of passwords • Constructions – micro-payments • SHA-3 • confirmation of knowledge/commitment • Conclusions • pseudo-random string generation/key derivation • entropy extraction • construction of MAC algorithms, stream ciphers, block ciphers,… 2005: 800 uses of MD5 in Microsoft Windows 3 4 Hash function flavours Informal definitions • no secret parameters cryptographic hash function • input string x of arbitrary length ⇒ output h(x) of fixed bitlength n this talk • computation “easy” MAC MDC • One Way Hash Function (OWHF) – preimage resistance OWHF CRHF 2 nd preimage resistance – UOWHF • Collision Resistant Hash Function (CRHF): OWHF + (TCR) – collision resistant 5 6
Hash Functions June 2013 Bart Preneel Security requirements (n-bit result) Preimage resistance 2 nd preimage preimage collision • in a password file, one does not store preimage – (username, password) ≠ ≠ ? x ? ? ? ? • but – (username,hash(password)) • this is sufficient to verify a password h h h h h h • an attacker with access to the password file has to find a preimage = = h(x’) h(x) h(x) h(x’) h(x) h(x) 2 n/2 2 n 2 n 2 n 7 8 Second preimage resistance Collision resistance (1/2) 2 nd preimage • hacker Alice prepares two versions collision of a software driver for the O/S x company Bob ≠ ≠ x’ x ? Channel 1: high capacity and insecure x – x is correct code h(x) – x’ contains a backdoor that gives Alice access to the machine Channel 2: low capacity but secure • Alice submits x for inspection to Bob h h (= authenticated – cannot be modified) h h • if Bob is satisfied, he digitally signs h(x) with his private key • an attacker can modify x but not h(x) • Alice now distributes x’ to users of • he can only fool the recipient if he = h(x) = h(x’) h(x’) h(x) the O/S; these users verify the finds a second preimage of x signature with Bob’s public key 2 n/2 2 n • this signature works for x and for x’, since h(x) = h(x’) 9 10 Collision resistance (2/2) Pseudo-random function computationally indistinguishable from a random function collision • in many cryptographic protocols, Alice wants to commit to a value x K : A hK(.) ⇒ 1] - Pr [ f ← RAND(m,n : A f ⇒ 1] prf = Pr [ K ← K $ $ Adv h ) : RAND(m,n) without revealing it ≠ x’ x RAND(m,n): set of all functions from m-bit to n-bit strings • Alice picks a secret random string r and sends y = h(x || r) to Bob • in a later phase of the protocol, Alice h h K h reveals x and r to Bob and he f checks that y is correct • if Alice can find a collision, that is = h(x) h(x’) (x,r) and (x’,r’) with x’ ≠ x she can ? or ? cheat This concept makes only 2 n/2 D sense for a function with a • if Bob can find a preimage, he can secret key learn x and cheat 11 12
Hash Functions June 2013 Bart Preneel Indifferentiability from a random oracle Brute force (2 nd ) preimage or PRO property [Maurer+04] variant of indistinguishability appropriate when distinguisher • multiple target second preimage (1 out of many): has access to inner component (e.g. building block of a – if one can attack 2 t simultaneous targets, the effort to find a single hash function) preimage is 2 n-t ∃ Simulator S, ∀ distinguisher D, Adv PRO (H,S) is small • multiple target second preimage (many out of many): – time-memory trade-off with Θ (2 n ) precomputation and FIL H storage Θ (2 2n/3 ) time per (2 nd ) preimage: Θ (2 2n/3 ) VIL RO S [Hellman’80] RO (hash function) • answer: randomize hash function with a parameter S ? or ? (salt, key, spice,…) D 13 14 The birthday paradox The birthday paradox (2) how many people r do I need to have in a room to • given a set with S elements have a probability of p=50% to have at least 2 • choose r elements at random (with replacements) with r « S people with the same birthday? • the probability p that there are at least 2 equal elements (a answer: 23 collision) ≅ 1 - exp ( - r(r-1)/2S) • more precisely, it can be shown that what is the probability that the birthdays of r people are distinct? – p ≥ 1 - exp ( - r(r-1)/2S) r terms – if r < √ 2S then p ≥ 0.6 r (r-1)/2S q = 1 - p = 1 . 364/365 . 363/365 . 362/365 … (365-(r-1))/365 ⇒ for a hash function with an n-bit result, a collision can be q = 1-p ≈ 0.5 for r = 23 found in time 2 n/2 and memory 2 n/2 • the number of collisions follows a Poisson distribution with λ intuition: number of distinct pairs of people is 23.22/2 = 253; each pair has = r(r-1)/2S probability 1/365 to have the same birthday – the expected number of collisions is equal to λ – the probability to have c collision is e - λ λ c / c! exercise: how many people do you need in a room to have a probability of 0.50 to have 3 people with the same birthday? 15 16 16 Functional graph of f(x) = x 3 + 3 mod 11 The birthday paradox - proof r terms q = 1-p = 1 . ((S-1)/S) . ((S-2)/S) …. ((S-(r-1))/S) 0 r-1 (S-k/S) or q = Π k=1 1 5 3 2 r-1 ln (1-k/S) ≅ Σ k=1 r-1 -k/S = -r(r-1)/2S ln q = Σ k=1 8 10 4 7 Taylor: if x « 1: ln (1-x) ≅ x 6 9 summation: Σ k=1r-1 k = r (r-1)/2 Exercise: find the functional graph of f(x) = x 3 + 7 mod 11 hence p = 1 – q = 1 - exp ( - r(r-1)/2S) 17 18
Hash Functions June 2013 Bart Preneel Functional graph of f(x) = x 2 + 7 mod 11 Functional graph of a permutation π permutation π 9 2 every permutation of π 2 (x) π (x) x π (x) π a finite set can be 4 written as a product of 0 7 disjoint cycles π (x) 1 π 2 (x) x expected length of 8 3 6 largest cycle: 0.62 2 n Done! expected number 5 10 of cycles of length at most m ≈ ln m • Exercise: why is the indegree of 5 nodes equal to 0 resp. 2? 19 20 Brute force collision search Functional graph of a random function f random function f Expected length of largest cycle: • low memory and parallel x ( π /8) 2 n/2 h(x) h implementation of the birthday attack f(x) f 2 (x) x f(x) Expected length from a point to f the cycle:( π /8) 2 n/2 [Pollard’78][Quisquater’89][Wiener-van Oorschot’94] c [Odlyzko-Flajolet’89] • distinguished point (d bits) f(x i )=f(x j ) collision – Θ (e2 n/2 + e 2 d+1 ) steps with e the cost of one function evaluation l a point of the form – Θ (n2 n/2-d ) memory 000 … 000 || x d f 2 (x) l = c = ( π /8) 2 n/ 2 – full cost: Θ (e n2 n/2 ) x f 2 (x) f(x) M. Wiener: The Full Cost of Cryptanalytic Attacks, J. of Cryptology, 2002 x f(x) 21 22 Collision resistance Relation between properties • hard to achieve in practice [Rogaway-Shrimpton’04] – many attacks – requires double output length 2 n/2 versus 2 n [Stinson’06] • hard to achieve in theory [Reyhanitabar-Susilo-Mu’10] – [Simon’98] one cannot derive collision resistance from “general” [Andreeva-Stam’10] preimage resistance (there exists no black box reduction) • hard to formalize: requires – family of functions: key, parameter, salt, spice,… – “human ignorance” trick [Stinson’06], [Rogaway’06] Even if Coll ⇒ xSEC/Pre: bound always 2 n/2 << 2 n 23 24 23
Recommend
More recommend