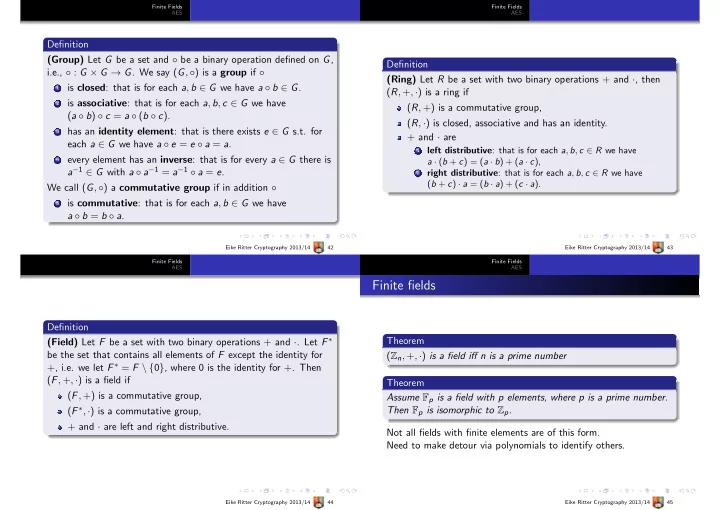

Finite Fields Finite Fields AES AES Definition (Group) Let G be a set and ◦ be a binary operation defined on G , Definition i.e., ◦ : G × G → G . We say ( G , ◦ ) is a group if ◦ (Ring) Let R be a set with two binary operations + and · , then 1 is closed : that is for each a , b ∈ G we have a ◦ b ∈ G . ( R , + , · ) is a ring if 2 is associative : that is for each a , b , c ∈ G we have ( R , +) is a commutative group, ( a ◦ b ) ◦ c = a ◦ ( b ◦ c ). ( R , · ) is closed, associative and has an identity. 3 has an identity element : that is there exists e ∈ G s.t. for + and · are each a ∈ G we have a ◦ e = e ◦ a = a . left distributive : that is for each a , b , c ∈ R we have 1 4 every element has an inverse : that is for every a ∈ G there is a · ( b + c ) = ( a · b ) + ( a · c ), a − 1 ∈ G with a ◦ a − 1 = a − 1 ◦ a = e . right distributive : that is for each a , b , c ∈ R we have 2 ( b + c ) · a = ( b · a ) + ( c · a ). We call ( G , ◦ ) a commutative group if in addition ◦ 5 is commutative : that is for each a , b ∈ G we have a ◦ b = b ◦ a . Eike Ritter Cryptography 2013/14 42 Eike Ritter Cryptography 2013/14 43 Finite Fields Finite Fields AES AES Finite fields Definition Theorem (Field) Let F be a set with two binary operations + and · . Let F ∗ be the set that contains all elements of F except the identity for ( Z n , + , · ) is a field iff n is a prime number +, i.e. we let F ∗ = F \ { 0 } , where 0 is the identity for +. Then ( F , + , · ) is a field if Theorem ( F , +) is a commutative group, Assume F p is a field with p elements, where p is a prime number. Then F p is isomorphic to Z p . ( F ∗ , · ) is a commutative group, + and · are left and right distributive. Not all fields with finite elements are of this form. Need to make detour via polynomials to identify others. Eike Ritter Cryptography 2013/14 44 Eike Ritter Cryptography 2013/14 45
Finite Fields Finite Fields AES AES Division with remainder Definition (Polynomial) We call an expression of the form Theorem a n x n + . . . + a 2 x 2 + a 1 x + a 0 a polynomial in the variable x over For every a , b ∈ Z with a ≥ b there exist s , r ∈ Z with | s | < | a | Z , if all a i ∈ Z , i = 0 , . . . , n and all exponents 0 , . . . , n are and | r | < | b | such that a = s · b + r. non-negative integers. Same holds also for polynomials: We denote the set of all polynomials in one variable over Z as Z [ x ]. We call a summand a i x i of a polynomial a monomial of degree i Theorem with coefficient a i . For every p ( x ) , q ( x ) ∈ Z [ x ] with deg ( p ) ≥ deg ( q ) there exist We say a polynomial p ∈ Z [ x ] is of degree n if its greatest s ( x ) , r ( x ) ∈ Z [ x ] with deg ( s ) < deg ( p ) and deg ( r ) < deg ( q ) such non-zero monomial is of degree n . We generally write deg ( p ) = n . that k · p ( x ) = s ( x ) · q ( x ) + r ( x ) , with k ∈ Z . Eike Ritter Cryptography 2013/14 46 Eike Ritter Cryptography 2013/14 47 Finite Fields Finite Fields AES AES Residue classes Irreducible polynomials For Z , have for each integer n residue classes Definition { [0] n , [1] n , . . . , [ n − 1] n } obtained by divison with remainder An integer n is called prime if its only divisors are 1 and n The same notion for polynomials is called irreducible: In the same way, in Z [ x ] have for each polynomial p ( x ) residue Definition classes obtained by division with remainder Note that there are infinitely many residue classes for each A polynomial p ( x ) ∈ Z [ x ] is called irreducible if its only divisors are polynomial p ( x ) of degree ≤ 2 p ( x ) and the constant polynomial a 0 ∈ Z [ x ] for any a 0 ∈ Z . We will write Z [ x ] / p ( x ) for the set of all residue classes Eike Ritter Cryptography 2013/14 48 Eike Ritter Cryptography 2013/14 49
Finite Fields Finite Fields AES AES Polynomials over finite fields The Advanced Encryption Standard Instead of Z can use arbitrary ring to obtain polyonmials. Interesting case: Ring is finite field F p . Theorem Let q ( x ) be an irreducible polynomial of degree n over F p , where p Successor of DES is a prime number. Then F p [ x ] / q ( x ) is a field with p n elements. Adopted in 2001 Still believed to be secure Theorem For every prime number p and every n there exists (up to isomorphism) exactly one field with p n elements. Will use often case of F 2 , ie polynomials with coefficients 0 or 1 only. Eike Ritter Cryptography 2013/14 50 Eike Ritter Cryptography 2013/14 51 Finite Fields Finite Fields AES AES Operations take place in F 2 8 = F 2 [ x ] / ( x 8 + x 4 + x 3 + x + 1) Start by arranging the message in 4 × 4 matrix of 8-bit elements, AES parametrisable: filling it downwards and then right Bock sizes of 128, 192 and 256 bits Each round has following operations: key sizes of 128, 192 and 256 bits Substitution: Operating on every single byte 10, 12 or 14 rounds of encryption Byte permutation ShiftRows column manipulation MixColumns xor with round key Eike Ritter Cryptography 2013/14 52 Eike Ritter Cryptography 2013/14 53
Finite Fields Finite Fields AES AES Substitution Shift Rows ShiftRows performs cyclic shift on the state matrix Corresponds to algebraic operation in the field F 2 8 Consider byte as polynomial in the field Compute its multiplicative inverse (non-linear step) Compute new bitvector by applying certain linear function to it (strengthening against algebraic attacks) Source: Wikipedia Eike Ritter Cryptography 2013/14 54 Eike Ritter Cryptography 2013/14 55 Finite Fields Finite Fields AES AES MixColumns Adding Round Key Mixing each column separately Achieved by multiplying with matrix Key, including all round keys is 128 bits. b 0 , i 0 x 02 0 x 03 0 x 01 0 x 01 a 0 , i Can be therefore represented as 4 × 4 matrix. b 1 , i 0 x 01 0 x 02 0 x 03 0 x 01 a 1 , i Simply added to state matrix. = · b 2 , i 0 x 01 0 x 01 0 x 02 0 x 03 a 2 , i b 3 , i 0 x 03 0 x 01 0 x 01 0 x 02 a 3 , i Each hex-number represents polynomial. Multiplication is in F 2 8 . Eike Ritter Cryptography 2013/14 56 Eike Ritter Cryptography 2013/14 57
Finite Fields Finite Fields AES AES Key schedule Advanced Access Content System Derive round keys K i as follows: Digital rights management system for HD-DVD and Blu-Ray Disc K 0 is the original key K To obtain K i +1 , first split key k into four words W 0 , W 1 , W 2 and W 3 of 32 bit each for i := 1 to 10 do T := W 4 i − 1 ≪ 8 T := SubBytes( T ) T := T ⊕ RC i W 4 i := W 4 i − 4 ⊕ T W 4 i +1 := W 4 i − 3 ⊕ W 4 i W 4 i +2 := W 4 i − 2 ⊕ W 4 i +1 W 4 i +3 := W 4 i − 1 ⊕ W 4 i +2 end where RC i = x i ( modx 8 + x 4 + x 3 + x + 1) Source: arstechnica.com Eike Ritter Cryptography 2013/14 58 Eike Ritter Cryptography 2013/14 59
Recommend
More recommend