Efficient and Reliable Lock-Free Memory Introduction The Problem - PDF document
Outline Efficient and Reliable Lock-Free Memory Introduction The Problem Reclamation Lock-free synchronization Based on Reference Counting Our solution Anders Gidenstam, Marina Papatriantafilou, Idea Hkan Sundell and
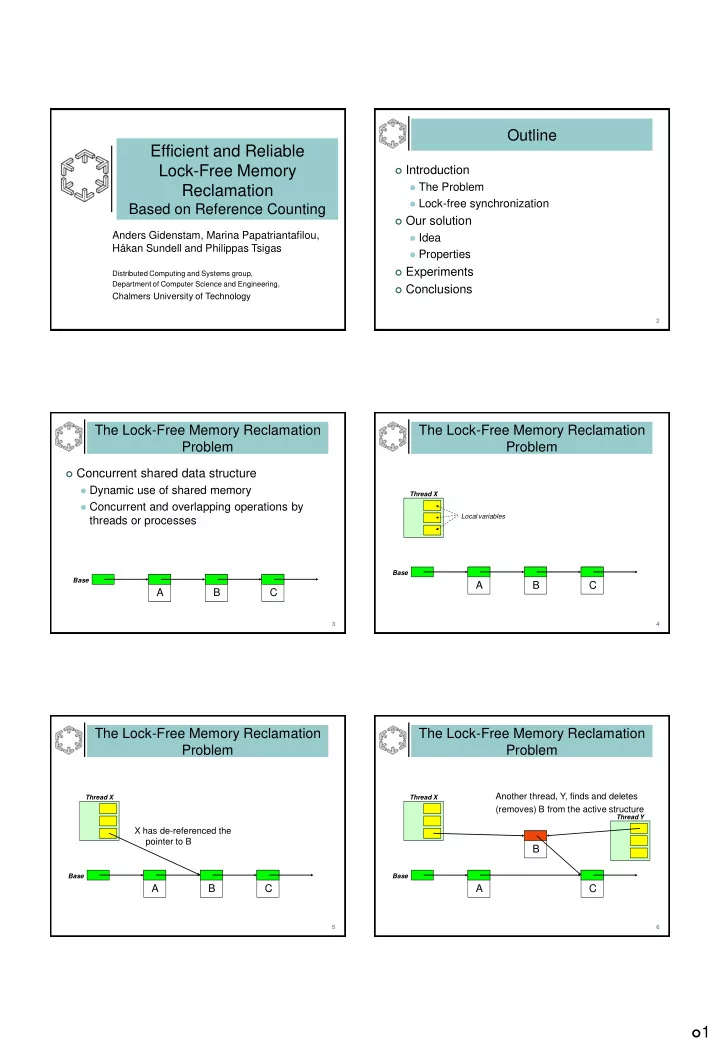
Outline Efficient and Reliable Lock-Free Memory Introduction The Problem Reclamation Lock-free synchronization Based on Reference Counting Our solution Anders Gidenstam, Marina Papatriantafilou, Idea Håkan Sundell and Philippas Tsigas Properties Experiments Distributed Computing and Systems group, Department of Computer Science and Engineering, Conclusions Chalmers University of Technology 2 The Lock-Free Memory Reclamation The Lock-Free Memory Reclamation Problem Problem Concurrent shared data structure Dynamic use of shared memory Thread X Concurrent and overlapping operations by Local variables threads or processes Base Base A B C A B C 3 4 The Lock-Free Memory Reclamation The Lock-Free Memory Reclamation Problem Problem Another thread, Y, finds and deletes Thread X Thread X (removes) B from the active structure Thread Y X has de-referenced the pointer to B B Base Base A B C A C 5 6 1
The Lock-Free Memory Reclamation The Lock-Free Memory Reclamation Problem Problem Property I: A (de-)referenced node is not reclaimed Property II: Links in a (de-)referenced node should always be de-referencable. Thread X Thread X Thread Y wants to reclaim(/free) B The nodes B and C ? ? are deleted from the Thread Y active structure. B B C Base Base A C A D 7 8 The Lock-Free Memory Reclamation Lock-free synchronization Problem A lock-free shared data structure Solutions? Allows concurrent operations without enforcing Garbage collection? mutual exclusion (i.e. no locks) Reference counting? Guarantees that at least one operation always Needs to be lock-free! makes progress Thread X Avoids: • Blocking, deadlock and priority inversion Hardware synchronization primitives 1 1 B C Built into CPU and memory system • Typically: atomic read-modify-write instructions Examples Base 1 2 • Test-and-set, Compare-and-Swap, Load-Linked / Store-Conditional A D 9 10 Previous solutions Previous solutions Hazard Pointers Hazard Pointers Michael 2002 Michael 2002 Thread X Thread X “Secure your foothold” “Secure your foothold” Thread X Thread X Base Base A B C A B C 11 12 2
Previous solutions Previous solutions Hazard Pointers Hazard Pointers Michael 2002 Michael 2002 Thread X Thread X “Secure your foothold” “Secure your foothold” Thread X Thread X ? Thread Y removes A from the structure A A Base Base B C B C 13 14 Previous solutions Previous solutions Lock-free Reference Counters Hazard Pointers Valois + Michael & Scott 1995 Michael 2002 Detlefs et al. 2001 Thread X “Secure your foothold” Herlihy et al. 2002 Thread X Thread X ?! Thread Z removes B from the structure and deletes B. A B Base Base 1 1 1 C A B C 15 16 Previous solutions Previous solutions Lock-free Reference Counters Lock-free Reference Counters Valois + Michael & Scott 1995 Valois + Michael & Scott 1995 Detlefs et al. 2001 Detlefs et al. 2001 Herlihy et al. 2002 Herlihy et al. 2002 Thread X Thread X Thread Y removes B from the structure 1 B 1 2 1 1 2 Base Base A B C A C 17 18 3
Previous solutions Previous solutions Lock-free Reference Counters Lock-free Reference Counters Valois + Michael & Scott 1995 Valois + Michael & Scott 1995 Detlefs et al. 2001 Detlefs et al. 2001 Herlihy et al. 2002 Herlihy et al. 2002 Thread Z removes C from the structure. ? ? Thread X Thread X 1 1 1 B B C 1 2 1 Base Base A C A 19 20 Our approach – The basic idea Previous solutions Lock-free Reference Counting Combine the best of Valois + Michael & Scott 1995 Hazard pointers (Michael 2002) Detlefs et al. 2001 • Tracks references from threads Slow 1 1 1 Herlihy et al. 2002 • Fast de-reference B C A • Upper bound on the amount of unreclaimed deleted nodes Remaining issues • Compatible with standard memory allocators A slow thread might prevent reclamation Reference counting Cyclic garbage • Tracks references from links in shared memory Implementation practicality issues • Manages links within dynamic nodes Reference-count field MUST remain forever (Valois + Michael & • Safe to traverse links (also) in deleted nodes Scott) Practical Needs double word CAS (Detlefs et al.) Uses only single-word Compare-And-Swap Needs double width CAS (Herlihy, 2002) Large overhead 21 22 The basic idea The basic idea Thread X Thread X API API Hazard pointers Hazard pointers DeRefLink DeRefLink ReleaseRef ReleaseRef Deletion list Deletion list CompareAndSwapRef CompareAndSwapRef Thread X Thread X StoreRef StoreRef NewNode NewNode DeleteNode DeleteNode 1 1 1 1 1 1 Base Base A B C A B C 23 24 4
The basic idea The basic idea Thread X Thread X API API Hazard pointers Hazard pointers DeRefLink DeRefLink ReleaseRef ReleaseRef Deletion list Deletion list CompareAndSwapRef CompareAndSwapRef Thread X Thread X StoreRef StoreRef NewNode NewNode 0 DeleteNode DeleteNode D 1 1 1 1 1 1 Base Base A B C A B C 25 26 The basic idea The basic idea Thread X Thread X API API Hazard pointers Hazard pointers DeRefLink DeRefLink C C A B ReleaseRef ReleaseRef Deletion list Deletion list CompareAndSwapRef CompareAndSwapRef Thread X Thread X StoreRef StoreRef NewNode NewNode 0 1 C C DeleteNode DeleteNode D D A B Base 1 1 2 Base 1 0 2 A B C A B C 27 28 The basic idea Breaking chains of garbage Thread X Thread X API Clean-up deleted nodes Hazard pointers Hazard pointers DeRefLink Update links to point to ReleaseRef live nodes Deletion list Deletion list CompareAndSwapRef Performed on nodes in Thread X Thread X StoreRef • Own deletion list NewNode • All deletion lists 1 0 1 DeleteNode D C D 1 0 2 1 1 2 Base Base A B C A B E 29 30 5
Breaking chains of garbage Bound on unreclaimed nodes Thread X Clean-up deleted nodes Hazard pointers A deleted node can be reclaimed when Update links to point to The reference count is zero and live nodes No hazard pointer is pointing to it and Deletion list Performed on nodes in There is no ongoing clean-up of this node Thread X • Own deletion list • All deletion lists With a rate relative to the number of threads of 0 0 Scanning hazard pointers C D Cleaning up nodes as needed Then the maximum size of each deletion list depends on 1 1 3 The number of hazard pointers Base A B E The number of links per node The number of threads 31 32 Experimental evaluation Experimental evaluation Lock-free deque (Sundell and Tsigas 2004) (deque – double-ended queue) The algorithm needs traversal of deleted nodes 10000 random operations/thread Tested memory reclamation schemes Reference counting, Valois et al. The new algorithm Systems 4 processor Xeon PC / Linux (UMA) 8 processor SGI Origin 2000 / IRIX (NUMA) 33 34 Experimental evaluation Conclusions First lock-free memory reclamation scheme that Only uses atomic primitives available in contemporary architectures Guarantees safety of • Local and • Global references Has an upper bound on the amount of deleted but unreclaimed nodes Allows arbitrary reuse of memory 35 36 6
Recommend
More recommend
Explore More Topics
Stay informed with curated content and fresh updates.





![Decoupling Lock-Free Data Structures from Memory Reclamation for Static Analysis [POPL'19]](https://c.sambuz.com/795309/decoupling-lock-free-data-structures-from-memory-s.webp)