CS70: Lecture 8. Outline. Extended GCD Algorithm. Correctness. - PowerPoint PPT Presentation
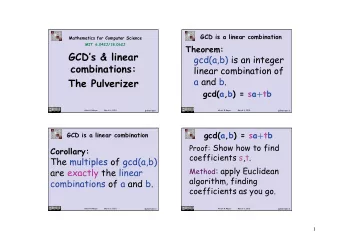
CS70: Lecture 8. Outline. Extended GCD Algorithm. Correctness. Proof: Strong Induction. 1 Base: ext-gcd ( x , 0 ) returns ( d = x , 1 , 0 ) with x = ( 1 ) x +( 0 ) y . 1. Finish Up Extended Euclid. Induction Step: Returns ( d , A , B ) with d =
CS70: Lecture 8. Outline. Extended GCD Algorithm. Correctness. Proof: Strong Induction. 1 Base: ext-gcd ( x , 0 ) returns ( d = x , 1 , 0 ) with x = ( 1 ) x +( 0 ) y . 1. Finish Up Extended Euclid. Induction Step: Returns ( d , A , B ) with d = Ax + By ext-gcd(x,y) Ind hyp: ext-gcd ( y , mod ( x , y )) returns ( d , a , b ) with 2. Cryptography if y = 0 then return(x, 1, 0) d = ay + b ( mod ( x , y )) else 3. Public Key Cryptography ext-gcd ( x , y ) calls ext-gcd ( y , mod ( x , y )) so (d, a, b) := ext-gcd(y, mod(x,y)) 4. RSA system return (d, b, a - floor(x/y) * b) d = ay + b · ( mod ( x , y )) 4.1 Efficiency: Repeated Squaring. ay + b · ( x −⌊ x = y ⌋ y ) 4.2 Correctness: Fermat’s Theorem. Theorem: Returns ( d , a , b ) , where d = gcd ( a , b ) and 4.3 Construction. bx +( a −⌊ x = y ⌋· b ) y d = ax + by . 5. Warnings. And ext-gcd returns ( d , b , ( a −⌊ x y ⌋· b )) so theorem holds! 1 Assume d is gcd ( x , y ) by previous proof. Review Proof: step. Wrap-up Xor Computer Science: 1 - True 0 - False Conclusion: Can find multiplicative inverses in O ( n ) time! 1 ∨ 1 = 1 ext-gcd(x,y) Very different from elementary school: try 1, try 2, try 3... 1 ∨ 0 = 1 if y = 0 then return(x, 1, 0) 2 n / 2 0 ∨ 1 = 1 else 0 ∨ 0 = 0 (d, a, b) := ext-gcd(y, mod(x,y)) Inverse of 500 , 000 , 357 modulo 1 , 000 , 000 , 000 , 000? ≤ 80 divisions. return (d, b, a - floor(x/y) * b) A ⊕ B - Exclusive or. versus 1 , 000 , 000 1 ∨ 1 = 0 Recursively: d = ay + b ( x −⌊ x ⇒ d = bx − ( a −⌊ x y ⌋· y ) = y ⌋ b ) y Internet Security. 1 ∨ 0 = 1 0 ∨ 1 = 1 Public Key Cryptography: 512 digits. Returns ( d , b , ( a −⌊ x y ⌋· b )) . 512 divisions vs. 0 ∨ 0 = 0 ( 10000000000000000000000000000000000000000000 ) 5 divisions. Iterative Algorithm? A bit easier. Later. Note: Also modular addition modulo 2! { 0 , 1 } is set. Take remainder for 2. Property: A ⊕ B ⊕ B = A . By cases: 1 ⊕ 1 ⊕ 1 = 1. ...
Cryptography ... Public key crypography. Is public key crypto possible? Secret s m = D ( E ( m , s ) , s ) m = D ( E ( m , K ) , k ) We don’t really know. Message m ...but we do it every day!!! E ( m , s ) E ( m , s ) Alice Bob Eve Private: k Public: K Message m RSA (Rivest, Shamir, and Adleman) E ( m , K ) E ( m , K ) Pick two large primes p and q . Let N = pq . Example: Choose e relatively prime to ( p − 1 )( q − 1 ) . 2 Alice Bob One-time Pad: secret s is string of length | m | . Compute d = e − 1 mod ( p − 1 )( q − 1 ) . E ( m , s ) – bitwise m ⊕ s . Announce N (= p · q ) and e : K = ( N , e ) is my public key! D ( x , s ) – bitwise x ⊕ s . Eve mod ( x e , N ) . Works because m ⊕ s ⊕ s = m ! Encoding: Everyone knows key K ! ...and totally secure! mod ( y d , N ) . Decoding: Bob (and Eve and me and you and you ...) can encode. ...given E ( m , s ) any message m is equally likely. Only Alice knows the secret key k for public key K . Does D ( E ( m )) = m ed = m mod N ? Disadvantages: (Only?) Alice can decode with k . Yes! Shared secret! Is this even possible? Uses up one time pad..or less and less secure. 2 Typically small, say e = 3. Iterative Extended GCD. Encryption/Decryption Techniques. Repeated squaring. Example: p = 7, q = 11. Notice: 43 = 32 + 8 + 2 + 1. 51 43 = 51 32 + 8 + 2 + 1 = 51 32 · 51 8 · 51 2 · 51 1 N = 77 . ( mod 77 ) . ( p − 1 )( q − 1 ) = 60 4 multiplications sort of... Choose e = 7, since gcd ( 7 , 60 ) = 1. Public Key: ( 77 , 7 ) Need to compute 51 32 ... 51 1 . ? egcd(7,60). Message Choices: { 0 ,..., 76 } . 51 1 ≡ 51 ( mod 77 ) 51 2 = ( 51 ) ∗ ( 51 ) = 2601 ≡ 60 ( mod 77 ) Message: 2! 51 4 = ( 51 2 ) ∗ ( 51 2 ) = 60 ∗ 60 = 3600 ≡ 58 ( mod 77 ) E ( 2 ) = 2 e = 2 7 ≡ 128 ( mod 77 ) = 51 ( mod 77 ) 7 ( 0 )+ 60 ( 1 ) = 60 51 8 = ( 51 4 ) ∗ ( 51 4 ) = 58 ∗ 58 = 3364 ≡ 53 ( mod 77 ) D ( 51 ) = 51 43 ( mod 77 ) 7 ( 1 )+ 60 ( 0 ) = 7 51 16 = ( 51 8 ) ∗ ( 51 8 ) = 53 ∗ 53 = 2809 ≡ 37 ( mod 77 ) uh oh! 51 32 = ( 51 16 ) ∗ ( 51 16 ) = 37 ∗ 37 = 1369 ≡ 60 ( mod 77 ) 7 ( − 8 )+ 60 ( 1 ) = 4 Obvious way: 43 multiplcations. Ouch. 7 ( 9 )+ 60 ( − 1 ) = 3 5 more multiplications. In general, O ( N ) multiplications! 7 ( − 17 )+ 60 ( 2 ) = 1 51 32 · 51 8 · 51 2 · 51 1 = ( 60 ) ∗ ( 53 ) ∗ ( 60 ) ∗ ( 51 ) ≡ 2 ( mod 77 ) . Decoding got the message back! Repeated Squaring took 9 multiplications versus 43. Confirm: − 119 + 120 = 1 d = e − 1 = − 17 = 43 = ( mod 60 )
Repeated Squaring: x y RSA is pretty fast. Always decode correctly? E ( m , ( N , e )) = m e ( mod N ) . D ( m , ( N , d )) = m d ( mod N ) . Repeated squaring O ( log y ) multiplications versus y !!! N = pq and d = e − 1 ( mod ( p − 1 )( q − 1 )) . 1. x y : Compute x 1 , x 2 , x 4 , ..., x 2 ⌊ log y ⌋ . Modular Exponentiation: x y mod N . All n -bit numbers. Want: ( m e ) d = m ed = m ( mod N ) . O ( n 3 ) time. 2. Multiply together x i where the ( log ( i )) th bit of y (in binary) is 1. Another view: Example: 43 = 101011 in binary. Remember RSA encoding/decoding! d = e − 1 ( mod ( p − 1 )( q − 1 )) ⇐ ⇒ ed = k ( p − 1 )( q − 1 )+ 1. x 43 = x 32 ∗ x 8 ∗ x 2 ∗ x 1 . E ( m , ( N , e )) = m e ( mod N ) . Consider... D ( m , ( N , d )) = m d ( mod N ) . Modular Exponentiation: x y mod N . All n -bit numbers. Repeated Fermat’s Little Theorem: For prime p , and a �≡ 0 ( mod p ) , Squaring: For 512 bits, a few hundred million operations. a p − 1 ≡ 1 ( mod p ) . O ( n ) multiplications. Easy, peasey. O ( n 2 ) time per multiplication. ⇒ O ( n 3 ) time. ⇒ a k ( p − 1 ) ≡ 1 ( mod p ) = ⇒ a k ( p − 1 )+ 1 = a ( mod p ) = = Conclusion: x y mod N takes O ( n 3 ) time. a k ( p − 1 )( q − 1 )+ 1 = a ( mod pq ) . versus Similar, not same, but useful. Correct decoding... Always decode correctly? (cont.) ...Decoding correctness... Lemma 1: For any prime p and any a , b , Fermat’s Little Theorem: For prime p , and a �≡ 0 ( mod p ) , a 1 + b ( p − 1 ) ≡ a ( mod p ) a p − 1 ≡ 1 ( mod p ) . Lemma 2: For any two different primes p , q and any x , k , Fermat’s Little Theorem: For prime p , and a �≡ 0 ( mod p ) , x 1 + k ( p − 1 )( q − 1 ) ≡ x ( mod pq ) Proof: Consider S = { a · 1 ,..., a · ( p − 1 ) } . a p − 1 ≡ 1 Let a = x , b = k ( p − 1 ) and apply Lemma 1 with modulus q . All different modulo p since a has an inverse modulo p . ( mod p ) . S contains representative of { 1 ,..., p − 1 } modulo p . x 1 + k ( p − 1 )( q − 1 ) ≡ x ( mod q ) Lemma 1: For any prime p and any a , b , ( a · 1 ) · ( a · 2 ) ··· ( a · ( p − 1 )) ≡ 1 · 2 ··· ( p − 1 ) mod p , a 1 + b ( p − 1 ) ≡ a ( mod p ) Let a = x , b = k ( q − 1 ) and apply Lemma 1 with modulus p . Since multiplication is commutative. Proof: If a ≡ 0 ( mod p ) , of course. x 1 + k ( p − 1 )( q − 1 ) ≡ x ( mod p ) Otherwise a ( p − 1 ) ( 1 ··· ( p − 1 )) ≡ ( 1 ··· ( p − 1 )) mod p . x 1 + k ( q − 1 )( p − 1 ) − x is multiple of p and q . a 1 + b ( p − 1 ) ≡ a 1 ∗ ( a p − 1 ) b ≡ a ∗ ( 1 ) b ≡ a ( mod p ) Each of 2 ,... ( p − 1 ) has an inverse modulo p , solve to get... x 1 + k ( q − 1 )( p − 1 ) − x ≡ 0 ⇒ x 1 + k ( q − 1 )( p − 1 ) = x a ( p − 1 ) ≡ 1 mod ( pq ) = mod pq . mod p .
RSA decodes correctly.. Construction of keys.. .. Security of RSA. 1. Find large (100 digit) primes p and q ? Prime Number Theorem: π ( N ) number of primes less than Lemma 2: For any two different primes p , q and any x , k , x 1 + k ( p − 1 )( q − 1 ) ≡ x ( mod pq ) N .For all N ≥ 17 Security? Theorem: RSA correctly decodes! 1. Alice knows p and q . π ( N ) ≥ N / ln N . Recall 2. Bob only knows, N (= pq ) , and e . Choosing randomly gives approximately 1 / ( ln N ) chance of D ( E ( x )) = ( x e ) d = x ed ≡ x ( mod pq ) , number being a prime. (How do you tell if it is prime? ... Does not know, for example, d or factorization of N . cs170..Miller-Rabin test.. Primes in P ). 3. I don’t know how to break this scheme without factoring N . where ed ≡ 1 mod ( p − 1 )( q − 1 ) = ⇒ ed = 1 + k ( p − 1 )( q − 1 ) For 1024 bit number, 1 in 710 is prime. No one I know or have heard of admits to knowing how to factor N . x ed ≡ x k ( p − 1 )( q − 1 )+ 1 ≡ x ( mod pq ) . 2. Choose e with gcd ( e , ( p − 1 )( q − 1 )) = 1. Breaking in general sense = ⇒ factoring algorithm. Use gcd algorithm to test. 3. Find inverse d of e modulo ( p − 1 )( q − 1 ) . Use extended gcd algorithm. All steps are polynomial in O ( log N ) , the number of bits. Much more to it..... Signatures using RSA. RSA Verisign: k v , K v If Bobs sends a message (Credit Card Number) to Alice, [ C , S v ( C )] C = E ( S V ( C ) , k V )? [ C , S v ( C )] [ C , S v ( C )] Eve sees it. Browser. K v Amazon Eve can send credit card again!! Public Key Cryptography: Certificate Authority: Verisign, GoDaddy, DigiNotar,... The protocols are built on RSA but more complicated; D ( E ( m , K ) , k ) = ( m e ) d mod N = m . Verisign’s key: K V = ( N , e ) and k V = d ( N = pq .) For example, several rounds of challenge/response. Browser “knows” Verisign’s public key: K V . Signature scheme: One trick: Amazon Certificate: C = “I am Amazon. My public Key is K A .” E ( D ( C , k ) , K ) = ( C d ) e mod N = C Bob encodes credit card number, c , Versign signature of C : S v ( C ) : D ( C , k V ) = C d mod N . concatenated with random k -bit number r . Browser receives: [ C , y ] Never sends just c . Checks E ( y , K V ) = C ? Again, more work to do to get entire system. E ( S v ( C ) , K V ) = ( S v ( C )) e = ( C d ) e = C de = C ( mod N ) CS161... Valid signature of Amazon certificate C ! Security: Eve can’t forge unless she “breaks” RSA scheme.
Recommend
More recommend
Explore More Topics
Stay informed with curated content and fresh updates.