CS 5410 - Computer and Network Security: Cellular Network Security - PowerPoint PPT Presentation
CS 5410 - Computer and Network Security: Cellular Network Security Professor Kevin Butler Fall 2015 Southeastern Security for Enterprise and Infrastructure (SENSEI) Center Reminders Poster showcase next Monday For final project: turn
CS 5410 - Computer and Network Security: Cellular Network Security Professor Kevin Butler Fall 2015 Southeastern Security for Enterprise and Infrastructure (SENSEI) Center
Reminders • Poster showcase next Monday • For final project: turn in all of your code, plus a makefile and instructions on how to run it Southeastern Security for Enterprise and Infrastructure (SENSEI) Center 2
Unintended Consequences • The law of unintended consequences states that most human actions have at least one unintended consequence. • Rigidity in networks: how would you characterize the rigidity of: • The Internet? • The telephone network? Southeastern Security for Enterprise and Infrastructure (SENSEI) Center 3
Low Rate DoS Attacks • While recent attacks on cellular networks seem unrelated, there is a common factor that catalyzes them all. • Comparing multiple attacks uncovers causality: ‣ SMS Attack (JCS’09, CCS’05) ‣ Network Characterization and Clash of Design Partial Mitigations (TON’10, MobiCom’06) Philosophies ‣ Data Teardown/Setup Attacks (USENIX Security’07) • The architecture of cellular networks inherently makes them susceptible to denial of service attacks. Southeastern Security for Enterprise and Infrastructure (SENSEI) Center 4
SMS Delivery (simplified) CCH MSC PSTN HLR VLR VLR Network SMSC MSC Internet ESME Southeastern Security for Enterprise and Infrastructure (SENSEI) Center 5
Control Channels • Control channels are used for a handful of infrequently used functions. ‣ Call setup, SMS delivery, mobility management, etc... • The SDCCH allows the network to perform most of these functions. • The number of SDCCHs typically depends on the expected use in an area. PCH ‣ 4/8/12... RACH AGCH SDCCH Southeastern Security for Enterprise and Infrastructure (SENSEI) Center 6
GSM TDMA Frames • TDMA Frame: Frame: 4.615 msec Slot 0 Slot 1 Slot 2 Slot 3 Slot 4 Slot 5 Slot 6 Slot 7 51 Multiframe: Frame 0 Frame 1 Frame 2 ... Frame 50 235.365 msec Southeastern Security for Enterprise and Infrastructure (SENSEI) Center 7
From Frames to Channels 26 Multiframe: 120.00 ms 7 } 0 1 2 3 Frame: 4.615ms 4 5 6 Southeastern Security for Enterprise and Infrastructure (SENSEI) Center 8
Recognition • Once you fill the SDCCH channels with SMS traffic, call setup is blocked Voice X SMS SMS SMS SMS SMS SMS SMS SMS • The goal of an adversary is therefore to fill SDCCHs with SMS traffic. ‣ Not as simple as you might think... Southeastern Security for Enterprise and Infrastructure (SENSEI) Center 9
Reconnaissance • Can such an attack be launched by targeting a single phone? ‣ Low end phones: 30-50 msgs ‣ High end phones: 500+ msgs (battery dies) • How do you get messages into the network? ‣ Email, IM, provider websites, bulk senders, etc... • Don’t the networks have protections? ‣ IP Address blocking, Spam filtering Southeastern Security for Enterprise and Infrastructure (SENSEI) Center 10
Finding Phones • North American Numbering Plan (NANP) NPA-NXX-XXXX Numbering Plan Exchange Numbering Plan Area (Area code) ‣ Mappings between providers and exchanges publicly documented and available on the web • Implication : An adversary can identify the prefixes used in a target area. Southeastern Security for Enterprise and Infrastructure (SENSEI) Center 11
Web-Scraping • Googling for phone numbers gives us better results: 7,300 in NYC 6,184 in D.C. in 5 seconds... Southeastern Security for Enterprise and Infrastructure (SENSEI) Center 12
Provider Interfaces • Almost all provider interfaces indicate whether or not a number is good. ‣ Some sites even tell you a target phone’s availability. • This interface is an “oracle” for available phones. Southeastern Security for Enterprise and Infrastructure (SENSEI) Center 13
Exploit (Metro) Sectors in SDCCHs per Messages per Manhattan sector SDCCH per hour „ 12 SDCCH « „ 900 msg/hr « (55 sectors ) C � 1 sector 1 SDCCH 594 , 000 msg/hr � 165 msg/sec � • 165 msgs/sec * 1500 bytes = 1933.6 kb/sec • 193.36 kb/sec on multi-send interface... • Comparison: Cable modem ~= 768 kb/sec Southeastern Security for Enterprise and Infrastructure (SENSEI) Center 14
Attack Profile 1.2 SDCCH Utilization TCH Utilization 1 0.8 SDCCH Utilization Utilization 0.6 TCH Utilization 0.4 0.2 0 0 500 1000 1500 2000 2500 3000 3500 4000 Time (seconds) • Applied simulation and analysis to better characterize the attacks. • Examined call blocking under multiple arrival patterns with exponentially distributed service times. • Using 495 msgs/sec, a blocking probability of 71% is possible with the bandwidth of a cable modem. Southeastern Security for Enterprise and Infrastructure (SENSEI) Center 15
Security Goals • Goal: To preserve the fidelity of both voice services and legitimate text messages during targeted SMS attacks. • Security Model: ‣ We must trust equipment in the network core. ‣ We can not trust Internet users or customer devices. Southeastern Security for Enterprise and Infrastructure (SENSEI) Center 16
Placing Mitigations MSC PSTN HLR VLR VLR Network SMSC MSC Internet ESME Southeastern Security for Enterprise and Infrastructure (SENSEI) Center 17
Solution Classifications • Scheduling/Shaping/Regulation ‣ WFQ, Leaky Bucket, Priority Queues ‣ AQM (WRED, REM, AVQ) • Resource Provisioning 1 1 Service Queue (SMS) SDCCH (SMS) Service Queue (Voice) SDCCH (Voice) TCH (Voice) TCH (Voice) ‣ SRP 0.8 0.8 Percent of Attempts Blocked Percent of Attempts Blocked 0.6 0.6 0.4 0.4 ‣ DRP 0.2 0.2 0 0 0 500 1000 1500 2000 2500 3000 3500 4000 0 500 1000 1500 2000 2500 3000 3500 4000 Time (seconds) Time (seconds) 1 1 SDCCH (SMS) SDCCH SDCCH (Voice) ‣ DCA TCH TCH (Voice) Service Queue 0.8 0.8 Percent of Attempts Blocked 0.6 0.6 Utilization 0.4 0.4 0.2 0.2 0 0 0 500 1000 1500 2000 2500 3000 3500 4000 0 500 1000 1500 2000 2500 3000 3500 4000 Time (seconds) Time (seconds) Southeastern Security for Enterprise and Infrastructure (SENSEI) Center 18
WRED - Overview High Med Low t med,max t med,min t low,min t low,max Southeastern Security for Enterprise and Infrastructure (SENSEI) Center 19
WRED - Overview High Med Low t med,max t med,min t low,min t low,max ρ N Q = P Q 1 − ρ ρ target = ρ actual (1 − P drop ) P drop = P drop,high · λ high + P drop,med · λ med + P drop,low · λ low λ SMS P drop = P drop,max · ( Q avg − t min ) ( t max − t min ) Southeastern Security for Enterprise and Infrastructure (SENSEI) Center 20
WRED - Results 1 1 Service Queue (SMS - Priority 1) SDCCH Service Queue (SMS - Priority 2) TCH Service Queue (SMS - Priority 3) Service Queue 0.8 0.8 Percent of Attempts Blocked 0.6 0.6 Average Queue Utilization Occupancy Low Priority 0.4 0.4 SMS Blocking 0.2 0.2 0 0 0 500 1000 1500 2000 2500 3000 3500 4000 0 500 1000 1500 2000 2500 3000 3500 4000 Time (seconds) Time (seconds) • Messages of high and medium-priority experience no blocking, but increased delay. • An average of 77% of low-priority messages are blocked. • This is a nice solution, assuming meaningful partitioning of flows. Southeastern Security for Enterprise and Infrastructure (SENSEI) Center 21
...and yet... • Performance improvements come from one of two changes: speedup or parallelization. • As diverse as our solutions appear, they all attempt to maximize performance through the latter. ‣ In many senses, we are not solving the problem - we are pushing food around on our plate. • Adding bandwidth should logically address this problem. Southeastern Security for Enterprise and Infrastructure (SENSEI) Center 22
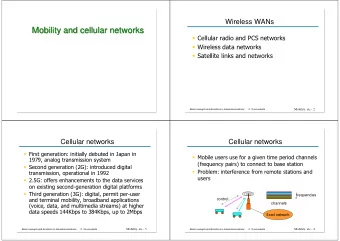
Cellular Data Networks • GPRS/EDGE provide much higher bandwidth service. • Packet-switched data services are attractive to providers and users for a number of reasons. • User devices operate in one of three states: IDLE, STANDBY and READY. STANDBY ‣ IDLE: The device is unavailable. READY Paging Timer Request Expires ‣ STANDBY: Available, but not STANDBY Timer READY exchanging packets. Expires GPRS GPRS ‣ READY: Actively listening for packets. Detach Attach IDLE Southeastern Security for Enterprise and Infrastructure (SENSEI) Center 23
Data Architecture HLR Internet GGSN SGSN IP Address SGSN 192.168.100.1 192.168.1.2 192.168.100.2 192.168.1.2 Southeastern Security for Enterprise and Infrastructure (SENSEI) Center 24
Real Network Configs • To make these simulations represent reality, we use a Samsung Blackjack in Field Test Mode to discover settings of an operational network. • Field Test Mode tells us that control channels for voice and data are shared in real networks. ‣ Voice and data traffic may be able to interfere with each other. Southeastern Security for Enterprise and Infrastructure (SENSEI) Center 25
Recommend
More recommend
Explore More Topics
Stay informed with curated content and fresh updates.



















![A Curious Case of Consent Button [... neither do I want to accept, nor decline ...] Nurul](https://c.sambuz.com/844513/a-curious-case-of-consent-button-s.webp)