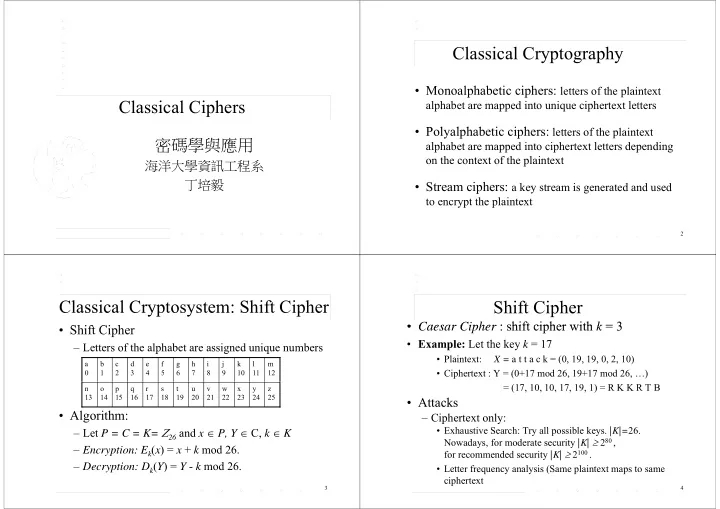

Classical Cryptography • Monoalphabetic ciphers: letters of the plaintext Classical Ciphers alphabet are mapped into unique ciphertext letters • Polyalphabetic ciphers: letters of the plaintext P l l h b i i h 密碼學與應用 alphabet are mapped into ciphertext letters depending on the context of the plaintext 海洋大學資訊工程系 丁培毅 丁培毅 • Stream ciphers: a key stream is generated and used St i h k i d d d to encrypt the plaintext 2 Classical Cryptosystem: Shift Cipher Shift Cipher • Caesar Cipher : shift cipher with k = 3 • Caesar Cipher : shift cipher with k = 3 • Shift Cipher Shif Ci h • Example: Let the key k = 17 – Letters of the alphabet are assigned unique numbers p g q • Plaintext: X = a t t a c k = (0, 19, 19, 0, 2, 10) a b c d e f g h i j k l m 0 1 2 3 4 5 6 7 8 9 10 11 12 • Ciphertext : Y = (0+17 mod 26, 19+17 mod 26, …) = (17, 10, 10, 17, 19, 1) = R K K R T B n o p q r s t u v w x y z 13 14 15 16 17 18 19 20 21 22 23 24 25 • Attacks • Algorithm: – Ciphertext only: – Let P = C = K= 26 and x P, Y C, k K • Exhaustive Search: Try all possible keys. |K|= 26. , , 26 Nowadays, for moderate security |K| 2 80 , – Encryption: E k ( x ) = x + k mod 26. for recommended security |K| 2 100 . – Decryption: D k ( Y ) = Y - k mod 26. Decryption: D ( Y ) = Y k mod 26 • Letter frequency analysis (Same plaintext maps to same f l i ( l i ciphertext 3 4
Frequency Analysis Letter Frequency Analysis • Method 1: Find the most frequent cipher character, make a guess • Method 1: Find the most frequent cipher character make a guess • In most languages, letters occur in texts as E k (‘e’), solves k. Use this k to decrypt ciphertext and see if it with different frequencies with different frequencies is a reasonable guess. Otherwise, find the second frequent is a reasonable guess. Otherwise, find the second frequent cipher character, make a guess as E k (‘e’). • single, double, triple letter frequencies • Method 2: correlation Single Frequency Double Triple Si l F D bl T i l A 0 =[.082 .015 .028 .043 .127 .022 .020 .061 .070 .002 E .127 TH THE .008 .040 .024 .067 .075 .019 .001 .060 .063 .091 T T .091 091 HE HE ING ING .028 .010 .023 .001 .020 .001] 028 010 023 001 020 001] A .082 IN AND A i is obtained by circularly shift right A 0 i elements O .075 ER HER e.g. A 2 =[.020 .001 .082 .015 .028 .043 ... e g A 2 =[ 020 001 082 015 028 043 I I .070 070 AN AN ERE ERE N .067 RE ENT • correlation = A i ꞏ A j is the usual dot product between A i and A j S .063 ED THA • let A be the frequency of the ciphertext paragraph • let A be the frequency of the ciphertext paragraph H H .061 061 ON ON NTH NTH • calculate correlation between A and A i , choose the maximum 5 6 Shift Cipher Shift Cipher – Known plaintext :You can deduce the key if you • One time pad can be considered as a shift know one letter of the plaintext along with its know one letter of the plaintext along with its cipher with modulus 2 and a changing key i h i h d l 2 d h i k corresponding ciphertext. Ex. t(=19) encrypts to sequence, in which each key is used only D( 3), then the key is D(=3) then the key is for one plaintext character and never k 3 - 19 -16 10 (mod 26) repeated. epeated. – Chosen plaintext : choose the letter ‘a’ as the Ch l i t t h th l tt ‘ ’ th • A shift cipher as defined is therefore plaintext, the ciphertext is the key perfectly secure if the key keeps changing f tl if th k k h i – Chosen ciphertext : choose the letter ‘A’ as and is used for one character only. ciphertext, the plaintext is the negative of the key p p g y 7 8
Matlab Example Matlab letter frequency analysis • dir, cd, help di d h l • sci= i ['themethodusedforthepreparationandreadingofcodemessagesissimplei', … • path(path, 'c:\lcwMatlabCode') 'ntheextremeandatthesametimeimpossibleoftranslationunlessthekeyi', … p y , • k = 20 'sknowntheeasewithwhichthekeymaybechangedisanotherpointinfavorof', … 'theadoptionofthiscodebythosedesiringtotransmitimportantmessages', … plain = 'hellothisisashiftcipherexample' 'withouttheslightestdangeroftheirmessagesbeingreadbypoliticalorb' withouttheslightestdangeroftheirmessagesbeingreadbypoliticalorb , … plain_i = text2int(plain) 'usinessrivalsetc']; cipher i = mod(plain i + k, 26) p _ (p _ , ) • cipher=shift(sci, 15); cipher shift(sci, 15); cipher = int2text(cipher_i) • freq=frequency(cipher); recovered_i mod(cipher_i k, 26) recovered i = mod(cipher i - k 26) • correlation=corr(freq); correlation corr(freq); recovered = int2text(recovered_i) • plot(0:25,correlation,'bd:') • cipher = shift(plain k) • cipher = shift(plain, k) recovered = shift(cipher, -k) 9 10 Affine Cipher Affine Cipher • Key Space: K S • Algorithm: Let P = C = 26 and x P, Y C Al ith – can be any number in 26 . 26 possibilities – Encryption: E k ( x ) = Y = ꞏ x + mod 26 k – Since -1 is required to exist, we can only select – The key k = ( , ) and , 26 integers in 26 s.t. gcd( , 26) = 1. Candidates are {1, 3, integers in 26 s.t. gcd( , 26) 1. Candidates are {1, 3, – ex . =13, =4 5, 7, 9, 11, 15, 17, 19, 21, 23, 25} input = (8, 13, 15, 20, 19) (4, 17, 17, 4, 17) = ERRER – Therefore, the key space has 12 ꞏ 26 = 312 candidates. Therefore the key space has 12 ꞏ 26 = 312 candidates alter = (0, 11, 19, 4, 17) l (0 11 19 4 17) (4, 17, 17, 4, 17) = ERRER (4 17 17 4 17) ERRER – There is no one-to-one mapping between plaintext • Attack types: and ciphertext. d i h t t What’s wrong? Wh t’ ? – Ciphertext only: exhaustive search or frequency – Decryption: D k (Y) = x = -1 ꞏ ( Y - ) analysis y = ' ꞏ Y + ' mod 26 11 12
Letter Frequency Analysis Letter Frequency Analysis • Make a guess: choose two potential candidate letters • Consider the ciphertext e.g. 1st guess R e and D t g g FMNVEDKAPHFERBNDKRX RSREFMORUDSDKDVSHVU • Try to show the guess make sense by solving FEDKAPRKDLYEVLRHHRH ( , ) from E k ( x ) Y ( , ) from E k ( x ) = Y = ꞏ x + mod 26 x mod 26 • Letter frequency of the ciphertext: e.g. 4 + =17 mod 26 and 19 + =5 mod 26 Letter # of Occurrences = 6, =19, which is illegal since gcd(6,26)>1 6, 19, which is illegal since gcd(6,26) 1 R 8 • 2nd guess: R e and E t ….. = 13, still illegal D 6 E 5 • 3rd guess: R e and H t ….. = 3, =5 3 3 d R d H t 5 H 5 i.e. E k ( x ) = 3 ꞏ x + 5 mod 26 K 5 V V 4 4 D k ( x ) = 9 ꞏ x - 19 mod 26 D ( ) 9 19 d 26 F 4 13 14 Affine Cipher Letter Frequency Analysis • Better Solution: correlation S l i l i • Attack types: – Enumerate 312 possible keys, ex. (3,2) p y ( ) – Known plaintext: two letters in the plaintext and Known plaintext: two letters in the plaintext and – Let A 0 = [.082, .015, .028, .043, .127, .022, .020, .061, .070, corresponding ciphertext letters would suffice to .002, .008, .040, .024, .067, .075, .019, .001, .060, , , , , , , , , , find the key. find the key .063, .091, 028, .010, .023, .001, .020, .001] Ex. plaintext ‘if’=(8, 5) and ciphertext ‘PQ’=(15, 16) – Let the i-th key be (3,2), which maps plaintexts [0, 1, 2, y ( , ), p p 8 ꞏ + 15 mod 26 [ , , , 5 ꞏ + 16 mod 26 = 17 and = 9 3, 4 …, 25] to ciphertexts [2, 5, 8, 11, 14, 17, 20, 23, …] – Calculate a vector A i with the k-th element being Calculate a vector A i with the k th element being What happens if we have only one letter of h h if h l l f A 0 (E 3,2 (k)), ex. A i = [A 0 (2), A 0 (5), A 0 (8), A 0 (11), A 0 known plaintext? (14) A 0 (17) A 0 (20) A 0 (23) A 0 (0) (14), A 0 (17), A 0 (20), A 0 (23), A 0 (0), …] ] still have great reduction in candidates ill h d i i did – Perform correlation AꞏA i and find the maximum 15 16
Recommend
More recommend