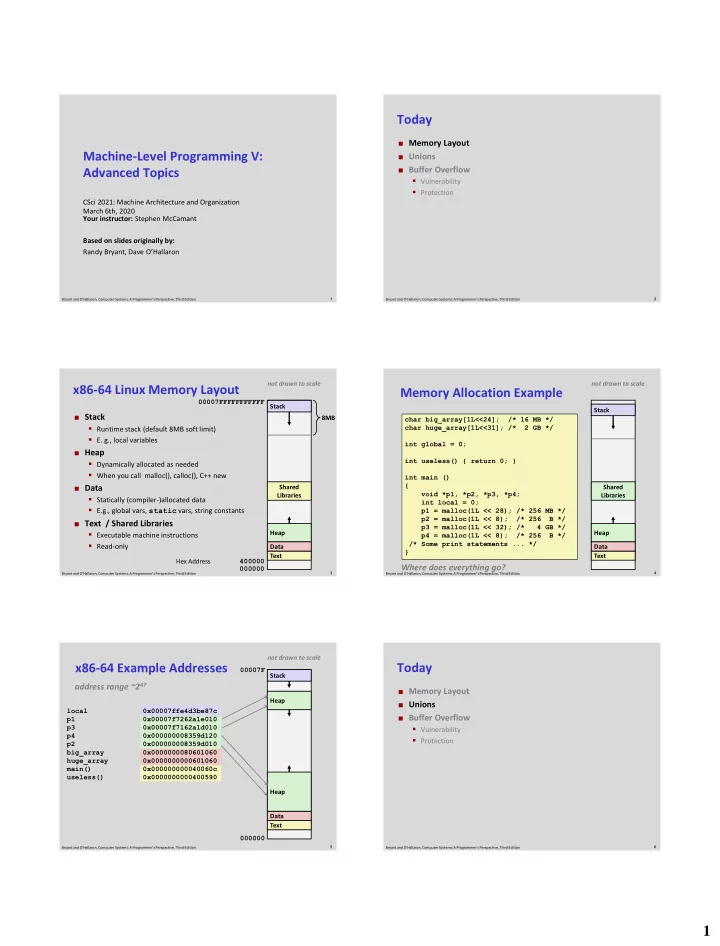

Today Memory Layout Machine-Level Programming V: Unions Buffer Overflow Advanced Topics Vulnerability Protection CSci 2021: Machine Architecture and Organization March 6th, 2020 Your instructor: Stephen McCamant Based on slides originally by: Randy Bryant, Dave O’Hallaron 1 2 Bryant and O’Hallaron, Computer Systems: A Programmer’s Perspective, Third Edition Bryant and O’Hallaron, Computer Systems: A Programmer’s Perspective, Third Edition not drawn to scale not drawn to scale x86-64 Linux Memory Layout Memory Allocation Example 00007FFFFFFFFFFF Stack Stack Stack 8MB char big_array[1L<<24]; /* 16 MB */ Runtime stack (default 8MB soft limit) char huge_array[1L<<31]; /* 2 GB */ E. g., local variables int global = 0; Heap int useless() { return 0; } Dynamically allocated as needed When you call malloc(), calloc(), C++ new int main () { Data Shared Shared void *p1, *p2, *p3, *p4; Libraries Libraries Statically (compiler-)allocated data int local = 0; E.g., global vars, static vars, string constants p1 = malloc(1L << 28); /* 256 MB */ p2 = malloc(1L << 8); /* 256 B */ Text / Shared Libraries p3 = malloc(1L << 32); /* 4 GB */ Executable machine instructions Heap Heap p4 = malloc(1L << 8); /* 256 B */ /* Some print statements ... */ Read-only Data Data } Text Text Hex Address 400000 Where does everything go? 000000 3 4 Bryant and O’Hallaron, Computer Systems: A Programmer’s Perspective, Third Edition Bryant and O’Hallaron, Computer Systems: A Programmer’s Perspective, Third Edition not drawn to scale x86-64 Example Addresses Today 00007F Stack address range ~2 47 Memory Layout Heap Unions local 0x00007ffe4d3be87c Buffer Overflow p1 0x00007f7262a1e010 p3 0x00007f7162a1d010 Vulnerability p4 0x000000008359d120 Protection p2 0x000000008359d010 big_array 0x0000000080601060 huge_array 0x0000000000601060 main() 0x000000000040060c useless() 0x0000000000400590 Heap Data Text 000000 5 6 Bryant and O’Hallaron, Computer Systems: A Programmer’s Perspective, Third Edition Bryant and O’Hallaron, Computer Systems: A Programmer’s Perspective, Third Edition 1
Union Allocation Using Union to Access Bit Patterns Allocate according to largest element typedef union { u Can only use one field at a time float f; f unsigned u; union U1 { 0 4 } bit_float_t; char c; c int i[2]; double v; i[0] i[1] float bit2float(unsigned u) unsigned float2bit(float f) } *up; v { { up+0 up+4 up+8 bit_float_t arg; bit_float_t arg; struct S1 { arg.u = u; arg.f = f; char c; return arg.f; return arg.u; int i[2]; } } double v; } *sp; Same as (float) u ? Same as (unsigned) f ? c i[0] i[1] v 3 bytes 4 bytes sp+0 sp+4 sp+8 sp+16 sp+24 7 8 Bryant and O’Hallaron, Computer Systems: A Programmer’s Perspective, Third Edition Bryant and O’Hallaron, Computer Systems: A Programmer’s Perspective, Third Edition Byte Ordering Revisited Byte Ordering Example union { unsigned char c[8]; Idea unsigned short s[4]; Short/long/quad words stored in memory as 2/4/8 consecutive bytes unsigned int i[2]; Which byte is most (least) significant? unsigned long l[1]; } dw; Can cause problems when exchanging binary data between machines Big Endian Most significant byte has lowest address c[0] c[1] c[2] c[3] c[4] c[5] c[6] c[7] 32-bit Sparc s[0] s[1] s[2] s[3] Little Endian i[0] i[1] Least significant byte has lowest address l[0] Intel x86, ARM Android and IOS c[0] c[1] c[2] c[3] c[4] c[5] c[6] c[7] 64-bit Bi Endian s[0] s[1] s[2] s[3] Can be configured either way i[0] i[1] ARM l[0] 9 10 Bryant and O’Hallaron, Computer Systems: A Programmer’s Perspective, Third Edition Bryant and O’Hallaron, Computer Systems: A Programmer’s Perspective, Third Edition Byte Ordering on IA32 Byte Ordering Example (Cont). int j; Little Endian for (j = 0; j < 8; j++) dw.c[j] = 0xf0 + j; f0 f1 f2 f3 f4 f5 f6 f7 printf("Characters 0-7 == c[0] c[1] c[2] c[3] c[4] c[5] c[6] c[7] [0x%x,0x%x,0x%x,0x%x,0x%x,0x%x,0x%x,0x%x]\n", dw.c[0], dw.c[1], dw.c[2], dw.c[3], s[0] s[1] s[2] s[3] dw.c[4], dw.c[5], dw.c[6], dw.c[7]); i[0] i[1] l[0] printf("Shorts 0-3 == [0x%x,0x%x,0x%x,0x%x]\n", dw.s[0], dw.s[1], dw.s[2], dw.s[3]); LSB MSB LSB MSB Print printf("Ints 0-1 == [0x%x,0x%x]\n", Output: dw.i[0], dw.i[1]); Characters 0-7 == [0xf0,0xf1,0xf2,0xf3,0xf4,0xf5,0xf6,0xf7] printf("Long 0 == [0x%lx]\n", Shorts 0-3 == [0xf1f0,0xf3f2,0xf5f4,0xf7f6] dw.l[0]); Ints 0-1 == [0xf3f2f1f0,0xf7f6f5f4] Long 0 == [0xf3f2f1f0] 11 12 Bryant and O’Hallaron, Computer Systems: A Programmer’s Perspective, Third Edition Bryant and O’Hallaron, Computer Systems: A Programmer’s Perspective, Third Edition 2
Byte Ordering on Sun Byte Ordering on x86-64 Little Endian Big Endian f0 f1 f2 f3 f4 f5 f6 f7 f0 f1 f2 f3 f4 f5 f6 f7 c[0] c[1] c[2] c[3] c[4] c[5] c[6] c[7] c[0] c[1] c[2] c[3] c[4] c[5] c[6] c[7] s[0] s[1] s[2] s[3] s[0] s[1] s[2] s[3] i[0] i[1] i[0] i[1] l[0] l[0] MSB LSB MSB LSB LSB MSB Print Print Output on x86-64: Output on Sun: Characters 0-7 == [0xf0,0xf1,0xf2,0xf3,0xf4,0xf5,0xf6,0xf7] Characters 0-7 == [0xf0,0xf1,0xf2,0xf3,0xf4,0xf5,0xf6,0xf7] Shorts 0-3 == [0xf1f0,0xf3f2,0xf5f4,0xf7f6] Shorts 0-3 == [0xf0f1,0xf2f3,0xf4f5,0xf6f7] Ints 0-1 == [0xf3f2f1f0,0xf7f6f5f4] Ints 0-1 == [0xf0f1f2f3,0xf4f5f6f7] Long 0 == [0xf7f6f5f4f3f2f1f0] Long 0 == [0xf0f1f2f3] 13 14 Bryant and O’Hallaron, Computer Systems: A Programmer’s Perspective, Third Edition Bryant and O’Hallaron, Computer Systems: A Programmer’s Perspective, Third Edition Summary of Compound Types in C Today Arrays Memory Layout Contiguous allocation of memory Unions Aligned to satisfy every element’s alignment requirement Buffer Overflow Pointer to first element Vulnerability No bounds checking Protection Structures Allocate bytes in order declared Pad in middle and at end to satisfy alignment Unions Overlay declarations Way to circumvent type system 15 16 Bryant and O’Hallaron, Computer Systems: A Programmer’s Perspective, Third Edition Bryant and O’Hallaron, Computer Systems: A Programmer’s Perspective, Third Edition Recall: Memory Referencing Bug Example Memory Referencing Bug Example typedef struct { typedef struct { fun(0) → 3.14 int a[2]; int a[2]; fun(1) → 3.14 double d; double d; fun(2) → 3.1399998664856 } struct_t; } struct_t; fun(3) → 2.00000061035156 fun(4) → 3.14 double fun(int i) { fun(6) → Segmentation fault volatile struct_t s; s.d = 3.14; Explanation: s.a[i] = 1073741824; /* Possibly out of bounds */ return s.d; } Critical State 6 ? 5 fun(0) → 3.14 fun(1) → 3.14 ? 4 fun(2) → 3.1399998664856 Location accessed by d7 ... d4 3 fun(3) → 2.00000061035156 fun(i) d3 ... d0 2 fun(4) → 3.14 struct_t fun(6) → Segmentation fault a[1] 1 a[0] 0 Result is system specific 17 18 Bryant and O’Hallaron, Computer Systems: A Programmer’s Perspective, Third Edition Bryant and O’Hallaron, Computer Systems: A Programmer’s Perspective, Third Edition 3
Recommend
More recommend